wordpress攻击思路
A ‘brute force’ login attack is a type of attack against a website to gain access to the site by guessing the username and password, over and over again. Other kinds of hacks rely on website vulnerabilities whereas a brute force attack is a simple hit and miss method and can be tried on any site.
“暴力破解”登录攻击是一种针对网站的攻击,它通过一遍又一遍地猜测用户名和密码来获得对该网站的访问权限。 其他类型的黑客攻击都依赖于网站漏洞,而蛮力攻击是一种简单的命中注定的方法,可以在任何网站上进行尝试。
In this tutorial, we will cover some methods and plugins we can use to prevent brute force attacks against WordPress sites. WordPress is the most popular CMS and therefore it’s a frequent target of these type of attacks.
在本教程中,我们将介绍一些可用于防止对WordPress网站进行暴力攻击的方法和插件。 WordPress是最流行的CMS,因此,它经常成为此类攻击的目标。
蛮力攻击和DDoS攻击有什么区别? (What’s the Difference Between a Brute Force Attack and a DDoS Attack?)
A brute force attack is performed to gain access to someone else’s account on the site, whereas a DDoS attack is usually launched to take a site down (typically by consuming resources). That said, a large scale brute force attack can also take a site down.
进行暴力攻击以获得对站点上其他人帐户的访问权限,而DDoS攻击通常是为了使站点瘫痪而发起的(通常是通过消耗资源)。 也就是说,大规模的蛮力攻击也会使站点瘫痪。
A DDoS attack is usually performed using a bot, whereas a brute force attack can be made using a bot or by a human. Humans can launch more targeted attacks, especially if they know usernames or have other intelligence to narrow down possible credentials.
DDoS攻击通常使用机器人来执行,而蛮力攻击可以使用机器人或人来进行。 人类可以发起更具针对性的攻击,尤其是当他们知道用户名或具有其他情报来缩小可能的凭证时。
Neither of these kinds of attacks rely on the website vulnerabilities and can be applied to any website.
这两种攻击都不依赖于网站漏洞,并且可以应用于任何网站。
WordPress doesn’t have any built in feature to prevent these two types of attacks. Therefore, it’s your responsibility to prevent them on your own sites.
WordPress没有任何内置功能可防止这两种类型的攻击。 因此,您有责任防止它们出现在您自己的网站上。
This tutorial will show you how you can prevent brute force attacks.
本教程将向您展示如何防止暴力攻击。
如何对WordPress网站发动蛮力攻击? (How is a Brute Force Attack Launched Against a WordPress Site?)
Launching a brute force attack on a site is relatively easier than any other kinds of attack. To launch a brute force attack on a site that logs into a user account, you just need to send the login form POST requests with the guessed username and password.
与任何其他类型的攻击相比,在站点上发起暴力攻击相对容易。 要在登录用户帐户的网站上发起暴力攻击,您只需要发送带有猜测的用户名和密码的登录表单POST请求即可。
In case of WordPress, the POST request with the guessed username and password is made to wp-login.php file again and again.
在WordPress的情况下,带有猜测的用户名和密码的POST请求将一次又一次地发送到wp-login.php文件。
Let’s see some of the ways to prevent brute force attacks.
让我们看看一些防止暴力攻击的方法。
验证你是人 (Verifying You Are Human)
Most of the time, brute force attacks are made using bots. We can simply verify if a form has been submitted by a human or not. If it’s submitted by a bot then we simply don’t process it.
在大多数情况下,暴力攻击都是使用漫游器进行的。 我们可以简单地验证一个人是否提交了表格。 如果它是由机器人提交的,那么我们根本就不处理它。
Agbonghama Collins has written an article here at SitePoint on how to integrate Google’s No CAPTCHA reCAPTCHA in WordPress login form. No CAPTCHA reCAPTCHA is a simple and user friendly way of asking the site visitor to verify if they are human or not when submitting a form.
Agbonghama Collins在SitePoint上写了一篇文章,介绍如何将Google的No CAPTCHA reCAPTCHA集成到WordPress登录表单中 。 没有CAPTCHA reCAPTCHA是一种简单且用户友好的方式,它要求站点访问者在提交表单时验证他们是否为人。
Here are the following problems using this method:
使用此方法存在以下问题:
- WordPress processes the request anyway, therefore if the brute force attack is made on large scale by bots then resources are still consumed that can kill the site. WordPress无论如何都会处理该请求,因此,如果僵尸程序通过机器人进行大规模的暴力攻击,那么仍然会消耗资源,这可能会杀死该网站。
- This method prevents access to bots but not humans. 这种方法可以防止访问机器人,但不能访问人类。
密码保护wp-login.php (Password Protecting wp-login.php)
You can protect access to your wp-login.php file using HTTP Basic Authentication. This simply adds a extra security layer. Although a brute force attack can be launched against HTTP basic authentication but it’s difficult and time intensive to crack down both layers.
您可以使用HTTP基本身份验证来保护对wp-login.php文件的访问。 这只是增加了一个额外的安全层。 尽管可以针对HTTP基本身份验证发起蛮力攻击,但要破解这两个层既困难又费时。
To password protect access to the wp-login.php file in Apache, follow the below steps:
要使用密码保护对Apache中wp-login.php文件的访问,请执行以下步骤:
Generate a
.htpasswdfile using htpasswd generator.使用htpasswd generator生成
.htpasswd文件。Place this file in the same location as your
.htaccessfile.将此文件放置在与
.htaccess文件相同的位置。Assuming your
.htpasswdfile includes the usernamenarayanprusty, place the code below in your.htaccessfile假设您的
.htpasswd文件包含用户名narayanprusty,请将下面的代码放入.htaccess文件中
## Stop Apache from serving .htpasswd files
<Files ~ "^\.ht"> Order allow,deny Deny from all </Files>
<Files wp-login.php>
AuthUserFile ~/.htpasswd
AuthName "Private access"
AuthType Basic
require user narayanprusty
</Files>Here are the following problems using this method:
使用此方法存在以下问题:
- If your WordPress site has multiple authors then you may not want to share the username and password of basic authentication. 如果您的WordPress网站有多个作者,那么您可能不想共享基本身份验证的用户名和密码。
- It’s possible that a bot or human can successfully guess both passwords. 机器人或人类可以成功猜出两个密码。
- Although WordPress is not loaded during basic authentication, a web server initiates a process to verify the credentials therefore consuming memory and CPU which can kill a site if requests are made in large scale. 尽管在基本身份验证期间未加载WordPress,但Web服务器会启动一个过程来验证凭据,因此会消耗内存和CPU,如果大规模进行请求,这可能会杀死站点。
蛮力登录保护插件 (Brute Force Login Protection Plugin)
Brute Force Login Protection is a WordPress plugin which protects brute force login attempts by taking several factors into account.
蛮力登录保护是一个WordPress插件,它通过考虑多个因素来保护蛮力登录尝试。
This is how the plugin works:
插件的工作方式如下:
- Limits the number of allowed login attempts for an IP Address. 限制允许的IP地址登录尝试次数。
- It allows you to manually block an IP address from logging into WordPress 它允许您手动阻止IP地址登录WordPress
- It delays execution after a failed login attempt to slow down the brute force attack. This can prevent the site being killed. 登录尝试失败后,它将延迟执行,以减慢蛮力攻击的速度。 这样可以防止该站点被杀死。
- It also informs the users about the number of login attempts remaining before getting blocked. 它还会告知用户有关被阻止之前剩余的登录尝试次数。
This is how the settings page of the plugin looks:
插件的设置页面如下所示:
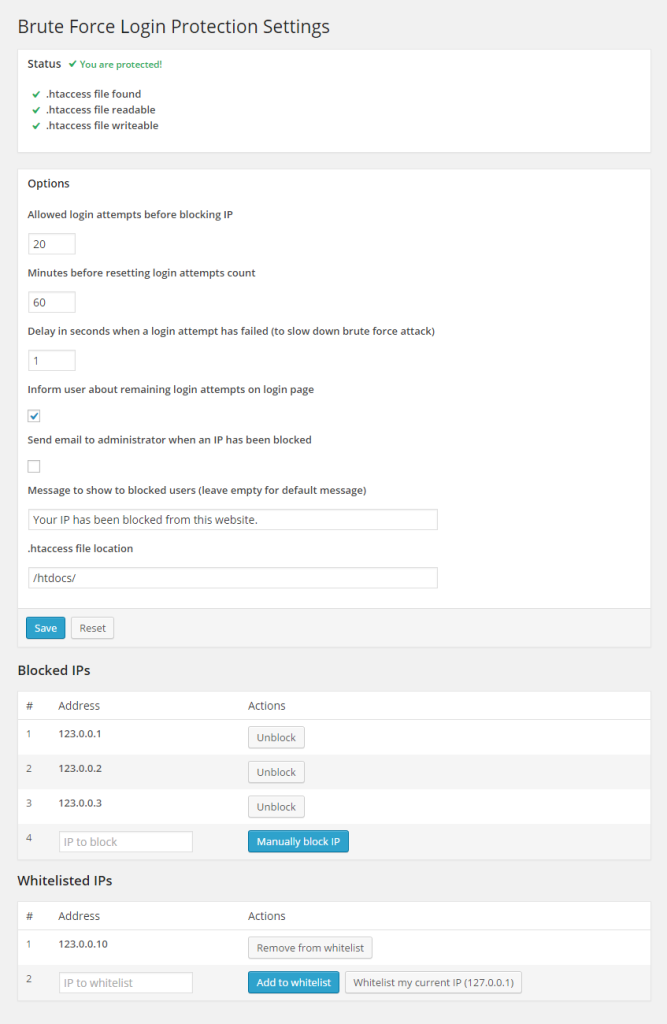
Here are the following problems using this plugin:
使用此插件存在以下问题:
- It will not be able to deal well with a distributed brute force attack because this plugin completely relays on IP address. A distributed brute force attack is one made from many different computers i.e. different IP addresses. 由于此插件完全依赖IP地址,因此无法很好地应对分布式暴力攻击。 分布式暴力攻击是由许多不同的计算机(即不同的IP地址)构成的攻击。
- It delays script execution for an IP address if a login has failed previously. While this saves computational time, memory is still used as the process is created in memory. 如果先前登录失败,则会延迟IP地址的脚本执行。 尽管这样可以节省计算时间,但由于在内存中创建了进程,因此仍使用内存。
暴力保护 (BruteProtect)
BruteProtect is a cloud-powered Brute Force attack prevention plugin and aims to provide the best protection against botnet attacks.
BruteProtect是一款基于云的蛮力攻击防御插件,旨在为抵御僵尸网络攻击提供最佳保护。
Every WordPress site which has BruteProtect installed will become a part of BruteProtect network. When an IP address is blocked due to malicious activity (such as a some number of failed login attempts) it’s shared among all the sites so that they all can block it before it begins to harm any sites.
每个安装了BruteProtect的WordPress网站都将成为BruteProtect网络的一部分。 当IP地址由于恶意活动(例如,多次失败的登录尝试)而被阻止时,它将在所有站点之间共享,以便他们可以在开始损害任何站点之前将其阻止。
You can think of BruteProtect as an advanced version of the above Brute Force Login Protection plugin as it has a bigger list of bad bots therefore probably doing well in the case of a distributed brute force attack.
您可以将BruteProtect视为上述“ Brute Force登录保护”插件的高级版本,因为它具有更多的不良机器人,因此在分布式蛮力攻击的情况下可能表现良好。
One feature that the BruteProtect plugin doesn’t have that the Brute Force Login Protection plugin does is a slow down script execution for failed login attempts. However, it doesn’t matter that much, as it takes up memory for the extra time.
BruteProtect插件不具备Brute Force Login Protection插件所具有的一项功能是,针对失败的登录尝试降低了脚本执行速度。 但是,没关系,因为它会占用额外的时间。
The problem using this plugin is that WordPress is loaded on every request for the IP address verification to be done. Therefore, if a brute force attack is done on a large enough scale then the site can still become overwhelmed and fall over.
使用此插件的问题是,在每次要进行IP地址验证的请求上都加载了WordPress。 因此,如果以足够大的规模进行暴力攻击,则该站点仍会不堪重负并倒下。
CloudFlare (CloudFlare)
CloudFlare protects and accelerates any website online. Once your website is a part of CloudFlare, its web traffic is routed through their intelligent global network. They automatically optimize the delivery of your web pages so your visitors get the fastest page load times and best performance.
CloudFlare保护和加速任何在线网站。 一旦您的网站成为CloudFlare的一部分,其Web流量便会通过其智能全球网络进行路由。 它们会自动优化您的网页的投放,从而使访问者获得最快的页面加载时间和最佳性能。
What’s important is it can prevent brute force attacks. Its has free and premium plans. Free plan is enough to get a decent amount of brute force protection. All the methods we’ve seen above were making our web server do the work to prevent brute force attack, which as we’ve mentioned, can still consumes memory and CPU. But CloudFlare on the other hand, can prevent malicious requests, before they even hit your server.
重要的是它可以防止暴力攻击。 它有免费和高级计划。 免费计划足以获得相当数量的暴力保护。 我们上面看到的所有方法都使我们的Web服务器完成了防止蛮力攻击的工作,正如我们已经提到的那样,蛮力攻击仍然会消耗内存和CPU。 但另一方面,CloudFlare可以阻止恶意请求,甚至不会将它们发送到您的服务器。
This image below shows how CloudFlare stops malicious requests:
下图显示了CloudFlare如何阻止恶意请求:
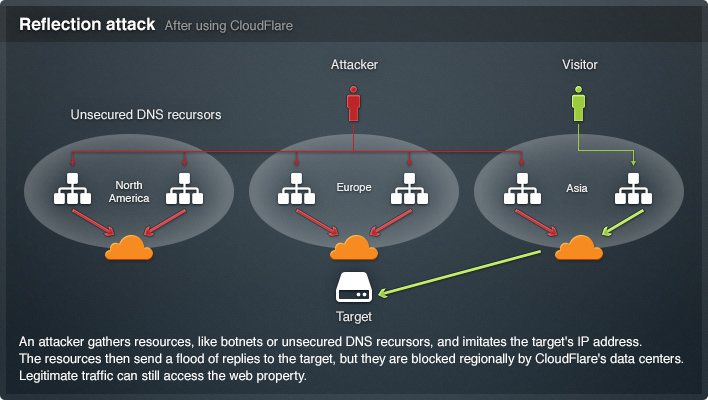
Here are the following problems using this service: 1. You need to make DNS changes to integrate CloudFlare with your site. This can be difficult if you’re not overly technical. 2. It fails to stop brute force attacks made by humans. It’s good at identifying malicious bots, but not malicious humans.
使用此服务存在以下问题:1.您需要进行DNS更改以将CloudFlare与您的站点集成。 如果您不太熟练,可能会很难。 2.它无法阻止人类进行的暴力攻击。 它擅长识别恶意机器人,但不能识别恶意人类。
结论 (Conclusion)
You must be wondering which is the best solution? It really depends on which one you think is the best for your needs. For me personally, I use both CloudFlare and BruteProtect to stops brute force attacks on my site.
您一定想知道哪个是最佳解决方案? 这实际上取决于您认为哪一种最适合您的需求。 就我个人而言,我同时使用CloudFlare和BruteProtect来阻止网站上的暴力攻击。
Let me know which one you think is the best solution for protecting against brute force attacks. Leave your thoughts and suggestions below.
让我知道您认为哪一种是防止暴力攻击的最佳解决方案。 在下面留下您的想法和建议。
翻译自: https://www.sitepoint.com/preventing-brute-force-attacks-against-wordpress-websites/
wordpress攻击思路




















 1258
1258











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








