
Do you want to encrypt important files, but not your Linux system’s entire hard drive? If so, we recommend gocryptfs. You’ll get a directory that, essentially, encrypts and decrypts everything you store.
您要加密重要文件,而不是Linux系统的整个硬盘驱动器吗? 如果是这样,我们建议使用gocryptfs 。 您将获得一个目录,从本质上讲,该目录将加密和解密您存储的所有内容。
gocryptfs提供防止数据泄露的保护 (gocryptfs Offers Protection From Data Breaches)
Privacy is big news. Hardly a week goes by without the announcement of a breach at one organization or another. Companies either report recent incidents or disclose breaches that happened some time ago. In both cases, it’s bad news for those whose data has been exposed.
隐私是个大新闻。 没有一个组织或另一个组织宣布违规的情况,几乎没有一周的时间。 公司要么报告最近的事件,要么披露前一段时间发生的违规事件。 在这两种情况下,对于那些暴露了数据的人来说都是个坏消息。
Because millions of people use services like Dropbox, Google Drive, and Microsoft OneDrive, a seemingly never-ending stream of data is pushed to the cloud every day. If you store some (or all) of your data on the cloud, what can you do to protect classified information and private documents should a breach occur?
由于数以百万计的人使用Dropbox , Google Drive和Microsoft OneDrive之类的服务 ,因此看似永无止境的数据流每天都被推送到云中。 如果您将部分(或全部)数据存储在云中,那么一旦发生违规,您将如何保护机密信息和私人文档?
Data breaches come in all shapes and sizes, of course, and they’re not limited to the cloud. A lost memory stick or stolen laptop is just a data breach on a smaller scale. But the scale isn’t the critical factor. If the data is sensitive or confidential, someone else having it could be disastrous.
当然,数据泄露有各种各样的形式和规模,而且不仅限于云。 记忆棒丢失或笔记本电脑失窃只是小规模的数据泄露。 但是规模并不是关键因素。 如果数据敏感或机密,则拥有该数据的其他人可能会造成灾难性的后果。
One solution is to encrypt your documents. Traditionally, this is done by encrypting your hard drive in its entirety. This is secure, but it also slightly slows down your computer. Plus, if you suffer a catastrophic failure, it can complicate the process of restoring your system from backups.
一种解决方案是对文档进行加密。 传统上,这是通过对硬盘整体进行加密来完成的。 这是安全的,但也会稍微降低计算机的速度。 另外,如果您遭受灾难性的故障,它会使从备份还原系统的过程变得复杂。
The gocryptfs system allows you to encrypt only the directories that need protection and avoid the system-wide overhead of encryption and decryption. It’s fast, lightweight, and easy to use. It’s also easy to move encrypted directories to other computers. As long as you have the password to access that data, it leaves no trace of your files on the other computer.
gocryptfs系统允许您仅加密需要保护的目录,并避免系统范围内的加密和解密开销。 它快速,轻巧且易于使用。 将加密目录移动到其他计算机也很容易。 只要您具有访问该数据的密码,它就不会在另一台计算机上留下文件的痕迹。
The gocryptfs system is constructed as a lightweight, encrypted file system. It’s also mountable by regular, non-root accounts because it uses the Filesystem in Userspace (FUSE) package. This acts as a bridge between gocryptfs and the kernel file-system routines it needs to access.
gocryptfs系统构造为轻量级的加密文件系统。 它也可以由常规的非root用户帐户挂载,因为它使用了用户空间 (FUSE)包中的文件系统 。 它充当gocryptfs和它需要访问的内核文件系统例程之间的桥梁。
安装gocryptfs (Installing gocryptfs)
To install gocryptfs on ubuntu, type this command:
要在ubuntu上安装gocryptfs ,请键入以下命令:
sudo apt-get install gocryptfs

To install it on Fedora type:
要将其安装在Fedora上,请输入:
sudo dnf install gocryptfs
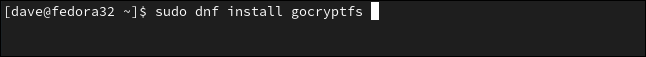
On Manjaro, the command is:
在Manjaro上,命令是:
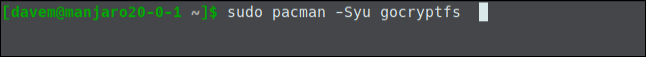
sudo pacman -Syu gocryptfs
创建一个加密目录 (Creating an Encrypted Directory)
Part of the glory of gocryptfs is how simple it is to use. The principles are:
gocryptfs部分荣耀在于它的使用非常简单。 原则是:
- Create a directory to contain the files and subdirectories you’re protecting. 创建一个目录以包含您要保护的文件和子目录。
Use
gocryptrfsto initialize that directory.使用
gocryptrfs初始化该目录。- Create an empty directory as a mount point, and then mount the encrypted directory onto it. 创建一个空目录作为安装点,然后将加密目录安装到该目录上。
- In the mount point, you can see and use the decrypted files and create new ones. 在安装点,您可以查看和使用解密的文件并创建新文件。
- Unmount the encrypted folder when you’re done. 完成后,卸载加密的文件夹。
We’re going to create a directory called “vault” to hold the encrypted data. To do so, we type the following:
我们将创建一个名为“ vault”的目录来保存加密数据。 为此,我们键入以下内容:
mkdir vault

We need to initialize our new directory. This step creates the gocryptfs file system within the directory:
我们需要初始化新目录。 此步骤在目录中创建gocryptfs文件系统:
gocryptfs -init vault
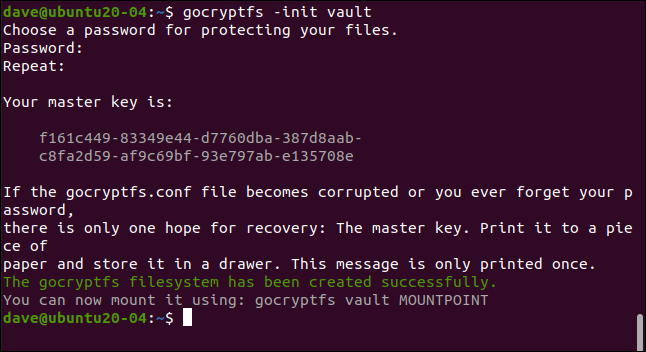
Type a password when you’re prompted; you’ll type it twice to ensure it’s correct. Choose a strong one: three unrelated words that include punctuation, digits, or symbols is a good template.
提示时输入密码; 您将输入两次以确保正确无误。 选择一个强词:三个不相关的单词(包括标点符号,数字或符号)是一个很好的模板。
Your master key is generated and displayed. Copy and save this somewhere safe and private. In our example, we’re creating a gocryptfs directory on a research machine that’s wiped after each article is written.
您的主密钥已生成并显示。 复制并保存在安全私密的地方。 在我们的示例中,我们正在研究机器上创建gocryptfs目录,该目录在撰写每篇文章后都会被擦除。
As it’s necessary for an example, you can see the master key for this directory. You’ll definitely want to be much more secretive with yours. If someone obtains your master key, they can access al of your encrypted data.
由于有必要提供示例,因此您可以看到此目录的主密钥。 您绝对希望对自己的内容更加保密。 如果有人获得了您的主密钥,则他们可以访问您的所有加密数据。
If you change into the new directory, you’ll see two files have been created. Type the following:
如果转到新目录,将看到已创建两个文件。 输入以下内容:
cd vault
ls -ahl
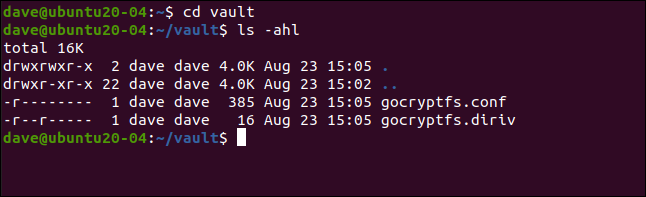
The “gocryptfs.diriv” is a short binary file, while “gocryptfs.conf” contains settings and information you should keep safe.
“ gocryptfs.diriv”是一个简短的二进制文件,而“ gocryptfs.conf”包含您应确保安全的设置和信息。
If you upload your encrypted data to the cloud or back it up to small, transportable media, don’t include this file. If, however, you back up to local media that remains under your control, you can include this file.
如果将加密数据上传到云或备份到小型可移动媒体,请不要包含此文件。 但是,如果您备份到受您控制的本地媒体,则可以包含此文件。
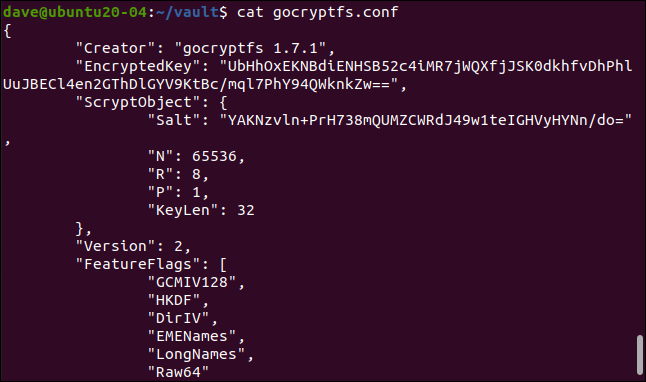
With sufficient time and effort, it might be possible to extract your password from the “encrypted key” and “salt” entries, as shown below:
花费足够的时间和精力,可能可以从“加密密钥”和“盐”项中提取密码,如下所示:
cat gocryptfs.conf
挂载加密目录 (Mounting the Encrypted Directory)
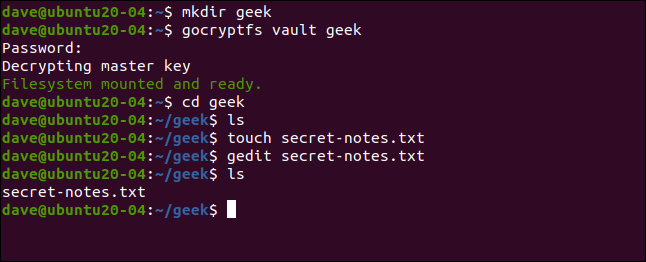
The encrypted directory is mounted on a mount point, which is simply an empty directory. We’re going to create one called “geek”:
加密目录被挂载在挂载点上,该挂载点只是一个空目录。 我们将创建一个称为“怪胎”的东西:
mkdir geek
We can now mount the encrypted directory on the mount point. Strictly speaking, what’s actually mounted is the gocryptfs file system inside the encrypted directory. We’re prompted for the password:
现在,我们可以将加密目录安装在安装点上。 严格来说,实际安装的是加密目录内的gocryptfs文件系统。 系统提示您输入密码:
gocryptfs vault geek
When the encrypted directory is mounted, we can use the mount point directory the same as we would any other. Anything we edit and create in this directory is actually written to the mounted, encrypted directory.
挂载加密目录时,我们可以像使用其他目录一样使用挂载点目录。 我们在此目录中编辑和创建的所有内容实际上都会写入已安装的加密目录。
We can create a simple text file, like the following:
我们可以创建一个简单的文本文件,如下所示:
touch secret-notes.txt
We can edit it, add some content to it, and then save the file:
我们可以对其进行编辑,向其中添加一些内容,然后保存文件:
gedit secret-notes.txt
Our new file has been created:
我们的新文件已创建:
ls
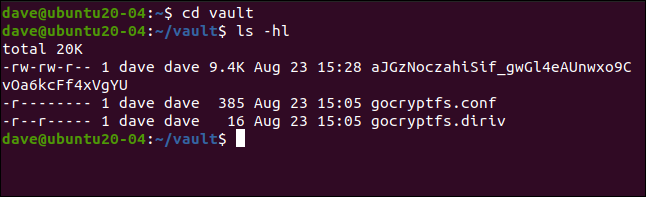
If we switch into our encrypted directory, as shown below, we see a new file has been created with an encrypted name. You can’t even tell which file type it is from the name:
如果我们切换到加密目录,如下所示,我们将看到已创建一个具有加密名称的新文件。 您甚至无法从名称中分辨出它是哪种文件类型:
cd vault
ls -hl
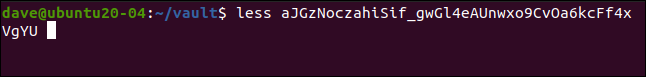
If we try to view the contents of the encrypted file, we can see it’s truly scrambled:
如果我们尝试查看加密文件的内容,我们可以看到它是真正被加密的:
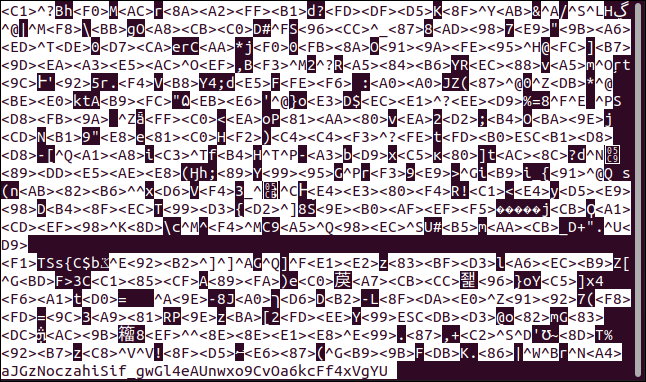
less aJGzNoczahiSif_gwGl4eAUnwxo9CvOa6kcFf4xVgYU
Our simple text file, shown below, is now anything but simple to decipher.
现在,我们的简单文本文件(如下所示)几乎无法解密。
卸载加密目录 (Unmounting the Encrypted Directory)
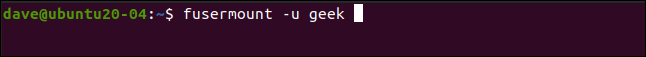
When you’re finished with your encrypted directory, you can unmount it with the fusermount command. Part of the FUSE package, the following command unmounts the gocryptfs file system inside the encrypted directory from the mount point:
完成加密目录后,可以使用fusermount命令将其卸载。 以下命令是FUSE软件包的一部分,从安装点卸载加密目录内的gocryptfs文件系统:
fusermount -u geek
If you type the following to check your mount point directory, you’ll see it’s still empty:
如果键入以下命令检查安装点目录,则会看到它仍然为空:
ls

Everything you did is safely stored in the encrypted directory.
您所做的一切都安全地存储在加密目录中。
简单安全 (Simple and Secure)
Simple systems have the advantage of being used more often, while more complicated processes tend to fall by the wayside. Using gocryptfs is not only simple, it’s also secure. Simplicity without security wouldn’t be worthwhile.
简单的系统的优点是可以更频繁地使用,而更复杂的过程往往会被淘汰。 使用gocryptfs不仅简单,而且很安全。 没有安全性的简单性将不值得。
You can create as many encrypted directories as you need or just one to hold all of your sensitive data. You might also want to create a few aliases to mount and unmount your encrypted file system and simplify the process even more.
您可以根据需要创建任意数量的加密目录,也可以只创建一个目录来保存所有敏感数据。 您可能还想创建一些别名来挂载和卸载加密的文件系统,从而进一步简化该过程。
翻译自: https://www.howtogeek.com/686779/how-to-encrypt-files-with-gocryptfs-on-linux/







 gocryptfs是一款轻量级加密文件系统,可在Linux系统中为指定目录提供加密保护,无需加密整个硬盘,避免了系统级加密带来的额外开销。通过简单的几步配置即可实现对敏感文件的安全防护。
gocryptfs是一款轻量级加密文件系统,可在Linux系统中为指定目录提供加密保护,无需加密整个硬盘,避免了系统级加密带来的额外开销。通过简单的几步配置即可实现对敏感文件的安全防护。
















 873
873

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








