Wireshark is the Swiss Army knife of network analysis tools. Whether you’re looking for peer-to-peer traffic on your network or just want to see what websites a specific IP address is accessing, Wireshark can work for you.
Wireshark是瑞士军刀的网络分析工具。 无论您是在网络上寻找对等流量,还是只想查看特定IP地址正在访问哪些网站,Wireshark都能为您服务。
We’ve previously given an introduction to Wireshark. and this post builds on our previous posts. Bear in mind that you must be capturing at a location on the network where you can see enough network traffic. If you do a capture on your local workstation, you’re likely to not see the majority of traffic on the network. Wireshark can do captures from a remote location — check out our Wireshark tricks post for more information on that.
我们之前已经对Wireshark进行了介绍 。 这篇文章建立在我们以前的文章的基础上。 请记住,您必须在网络上可以看到足够网络流量的位置进行捕获。 如果在本地工作站上进行捕获,则很可能看不到网络上的大部分流量。 Wireshark可以从远程位置进行捕获-请查看我们的Wireshark技巧文章以获取有关此信息的更多信息。
识别对等流量 (Identifying Peer-to-Peer Traffic)
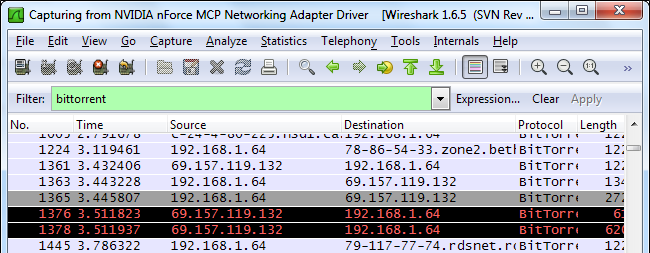
Wireshark’s protocol column displays the protocol type of each packet. If you’re looking at a Wireshark capture, you might see BitTorrent or other peer-to-peer traffic lurking in it.
Wireshark的协议列显示每个数据包的协议类型。 如果您正在查看Wireshark捕获,则可能会看到BitTorrent或其他对等流量潜伏其中。
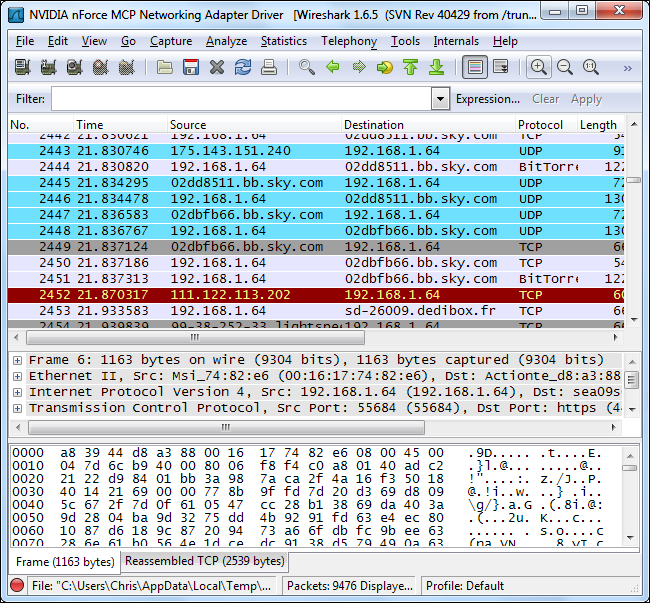
You can see just what protocols are being used on your network from the Protocol Hierarchy tool, located under the Statistics menu.
您可以从“ 统计”菜单下的“协议层次结构”工具查看网络上正在使用的协议 。

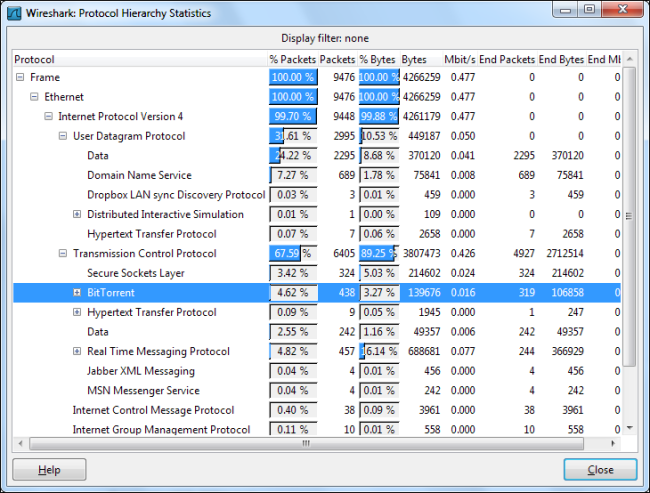
This window shows a breakdown of network usage by protocol. From here, we can see that nearly 5 percent of packets on the network are BitTorrent packets. That doesn’t sound like much, but BitTorrent also uses UDP packets. The nearly 25 percent of packets classified as UDP Data packets are also BitTorrent traffic here.
该窗口按协议显示网络使用情况的细分。 从这里,我们可以看到网络上近5%的数据包是BitTorrent数据包。 听起来并不多,但是BitTorrent也使用UDP数据包。 在这里,将近25%的分类为UDP数据包的数据包也是BitTorrent流量。
We can view only the BitTorrent packets by right-clicking the protocol and applying it as a filter. You can do the same for other types of peer-to-peer traffic that may be present, such as Gnutella, eDonkey, or Soulseek.
通过右键单击协议并将其用作过滤器,我们只能查看BitTorrent数据包。 您可以对可能存在的其他类型的对等流量执行相同的操作,例如Gnutella,eDonkey或Soulseek。
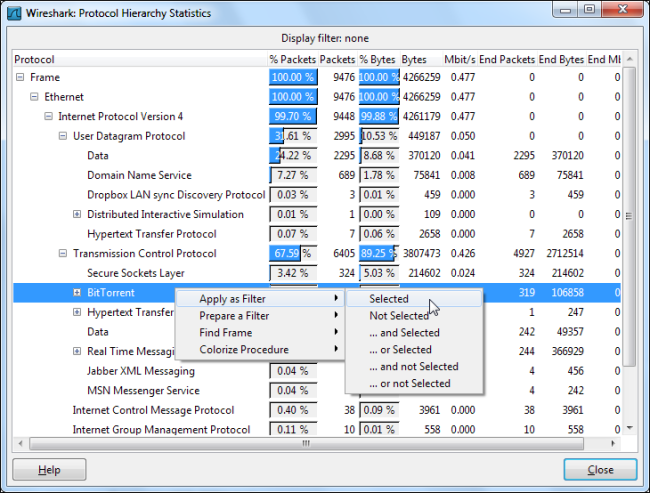
Using the Apply Filter option applies the filter “bittorrent.” You can skip the right-click menu and view a protocol’s traffic by typing its name directly into the Filter box.
使用“应用过滤器”选项将应用过滤器“ bittorrent。 您可以跳过右键单击菜单,直接在“过滤器”框中键入协议的名称来查看协议的流量。
From the filtered traffic, we can see that the local IP address of 192.168.1.64 is using BitTorrent.
从经过过滤的流量中,我们可以看到192.168.1.64的本地IP地址正在使用BitTorrent。
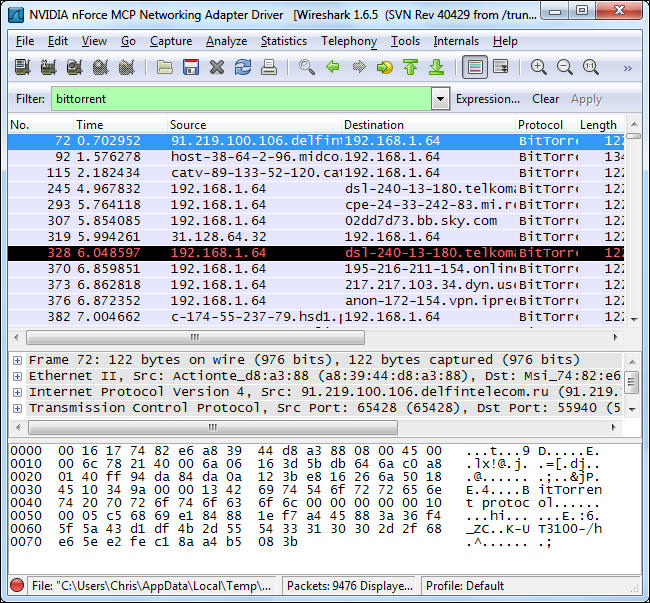
To view all the IP addresses using BitTorrent, we can select Endpoints in the Statistics menu.
要使用BitTorrent查看所有IP地址,我们可以在“ 统计”菜单中选择“ 端点 ”。
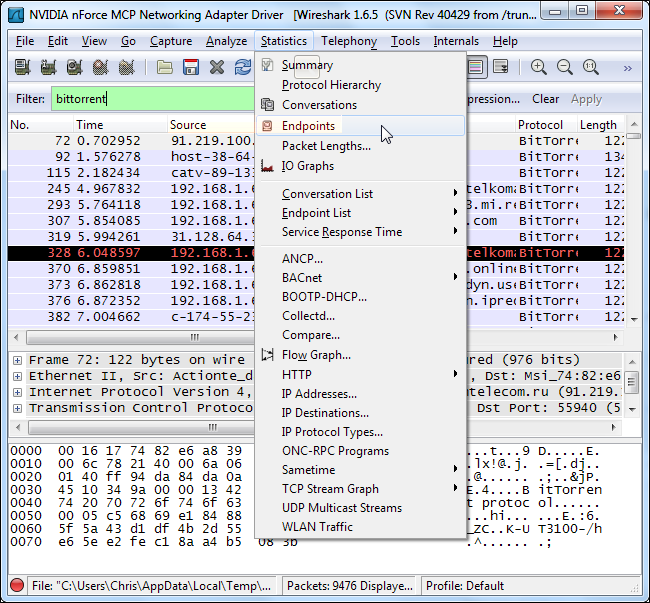
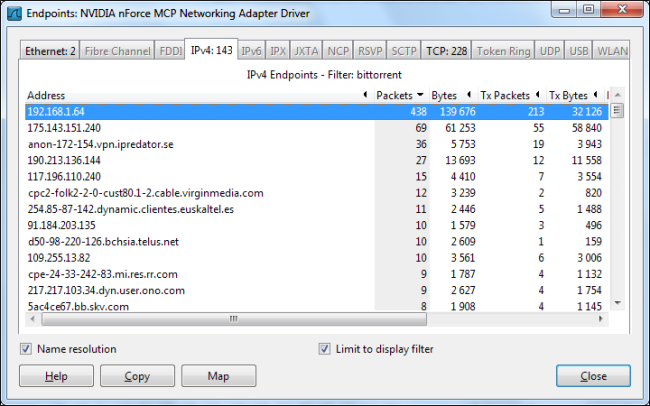
Click over to the IPv4 tab and enable the “Limit to display filter” check box. You’ll see both the remote and local IP addresses associated with the BitTorrent traffic. The local IP addresses should appear at the top of the list.
单击“ IPv4”选项卡,然后启用“ 限制显示过滤器 ”复选框。 您将看到与BitTorrent流量关联的远程和本地IP地址。 本地IP地址应显示在列表的顶部。
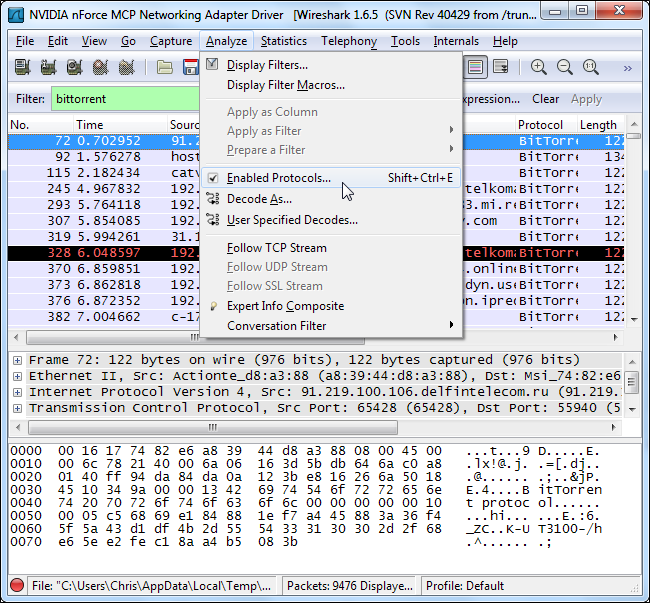
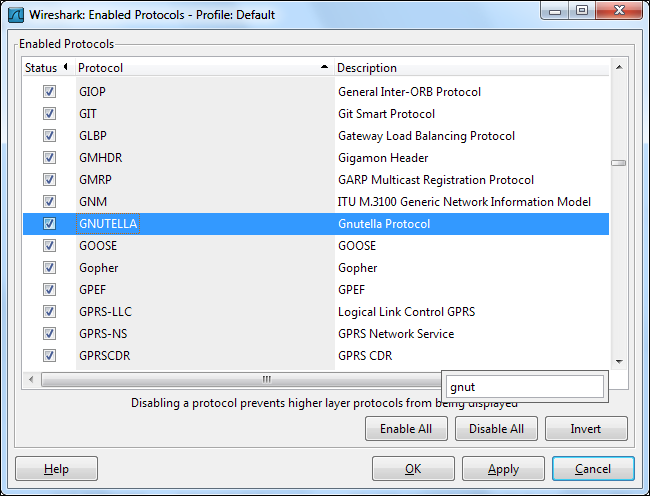
If you want to see the different types of protocols Wireshark supports and their filter names, select Enabled Protocols under the Analyze menu.
如果要查看Wireshark支持的不同类型的协议及其过滤器名称,请在“ 分析”菜单下选择“ 启用的协议” 。
You can start typing a protocol to search for it in the Enabled Protocols window.
您可以在“启用的协议”窗口中开始键入协议以进行搜索。
监控网站访问 (Monitoring Website Access)
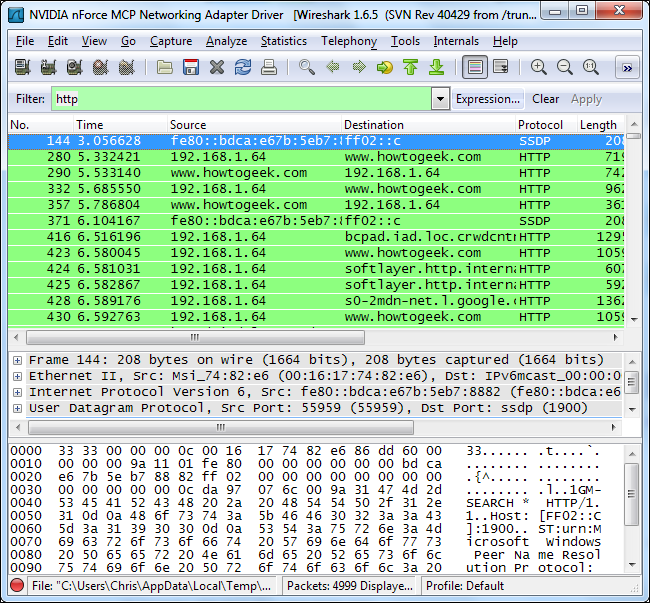
Now that we know how to break traffic down by protocol, we can type “http” into the Filter box to see only HTTP traffic. With the “Enable network name resolution” option checked, we’ll see the names of the websites being accessed on the network.
现在我们知道如何按协议分解流量,我们可以在“过滤器”框中键入“ http ”以仅查看HTTP流量。 选中“启用网络名称解析”选项 ,我们将看到网络上正在访问的网站的名称。
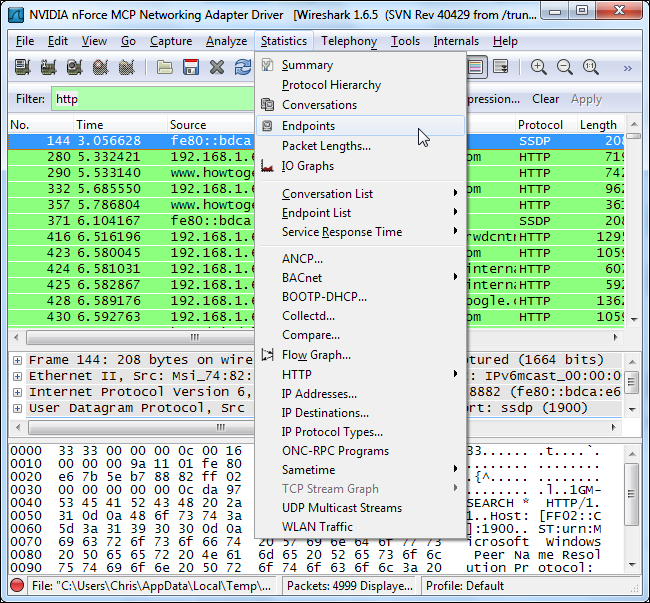
Once again, we can use the Endpoints option in the Statistics menu.
再一次,我们可以使用“ 统计”菜单中的“ 端点”选项。
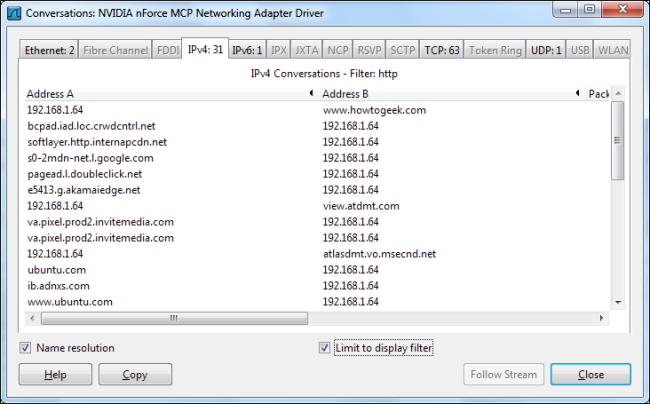
Click over to the IPv4 tab and enable the “Limit to display filter” check box again. You should also ensure that the “Name resolution” check box is enabled or you’ll only see IP addresses.
单击“ IPv4”选项卡,然后再次启用“ 限制以显示过滤器 ”复选框。 您还应该确保启用“ 名称解析 ”复选框,否则您只会看到IP地址。
From here we, can see the websites being accessed. Advertising networks and third-party websites that host scripts used on other websites will also appear in the list.
从这里,我们可以看到正在访问的网站。 承载其他网站上使用的脚本的广告网络和第三方网站也将出现在列表中。
If we want to break this down by a specific IP address to see what a single IP address is browsing, we can do that too. Use the combined filter http and ip.addr == [IP address] to see HTTP traffic associated with a specific IP address.
如果我们想通过一个特定的IP地址来细分它,以查看单个IP地址正在浏览什么,我们也可以这样做。 使用组合的过滤器http和ip.addr == [IP地址]查看与特定IP地址关联的HTTP通信。
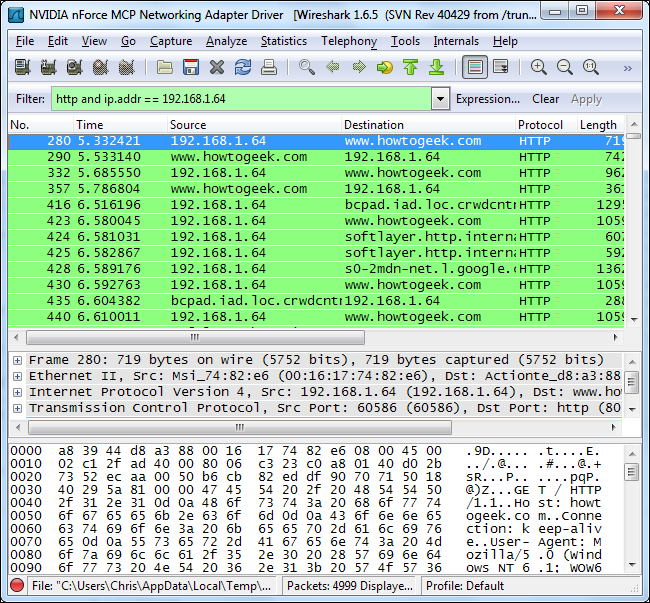
Open the Endpoints dialog again and you’ll see a list of websites being accessed by that specific IP address.
再次打开“端点”对话框,您将看到该特定IP地址正在访问的网站的列表。
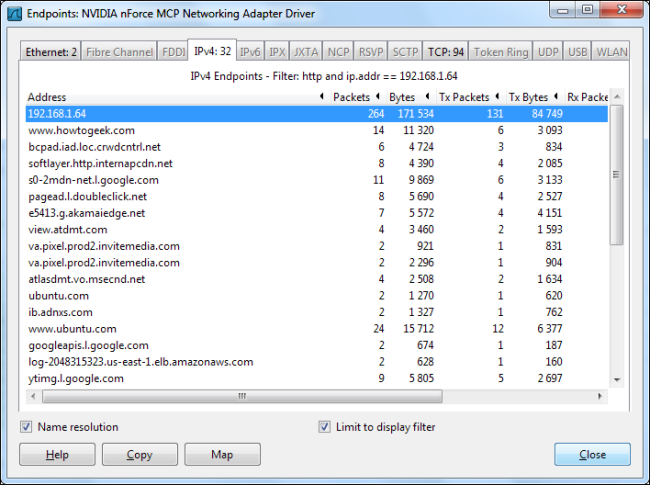
This is all just scratching the surface of what you can do with Wireshark. You could build much more advanced filters, or even use the Firewall ACL Rules tool from our Wireshark tricks post to easily block the types of traffic you’ll find here.
这一切都只是从头开始了解Wireshark的功能。 您可以构建更高级的过滤器,甚至可以使用我们Wireshark技巧文章中的Firewall ACL Rules工具轻松阻止在此处找到的流量类型。
翻译自: https://www.howtogeek.com/107945/how-to-identify-network-abuse-with-wireshark/





















 2748
2748

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








