
安全 lynis
If you perform a security audit on your Linux computer with Lynis, it will ensure your machine is as protected as it can be. Security is everything for internet-connected devices, so here’s how to make sure yours are safely locked down.
如果您使用Lynis在Linux计算机上执行安全审核,它将确保您的计算机受到尽可能多的保护。 安全性是连接互联网的设备的全部要素,因此,这是确保安全锁定您的方法。
您Linux计算机的安全性如何? (How Secure Is Your Linux Computer?)
Lynis performs a suite of automated tests that thoroughly inspect many system components and settings of your Linux operating system. It presents its findings in a color-coded ASCII report as a list of graded warnings, suggestions, and actions that should be taken.
Lynis执行一套自动化测试,以彻底检查Linux操作系统的许多系统组件和设置。 它在以彩色编码的ASCII报告中显示其发现结果,作为分级的警告,建议和应采取的措施的列表。
Cybersecurity is a balancing act. Outright paranoia isn’t useful to anyone, so how concerned should you be? If you only visit reputable web sites, don’t open attachments or follow links in unsolicited emails, and use different, robust, passwords for all the systems you log in to, what danger remains? Especially when you’re using Linux?
网络安全是一种平衡行为。 彻底的妄想症对任何人都没有用,那么您应该如何关注? 如果您仅访问信誉良好的网站,请勿打开附件或跟踪未经请求的电子邮件中的链接,并为登录的所有系统使用不同的功能强大的密码,那么仍然存在危险吗? 特别是在使用Linux时?
Let’s address those in reverse. Linux isn’t immune to malware. In fact, the very first computer worm was designed to target Unix computers in 1988. Rootkits were named after the Unix superuser (root) and the collection of software (kits) with which they install themselves to evade detection. This gives the superuser access to the threat actor (i.e., the bad guy).
让我们反向解决这些问题。 Linux无法幸免于恶意软件。 实际上,第一个计算机蠕虫是在1988年针对Unix计算机设计的。Rootkit以Unix超级用户(root)和用于安装其自身的软件(套件)的集合来命名,以逃避检测。 这使超级用户可以访问威胁参与者(即坏人)。
Why are they named after root? Because the first rootkit was released in 1990 and targeted at Sun Microsystems running the SunOS Unix.
他们为什么以根命名? 因为第一个rootkit于1990年发布,并且针对运行SunOS Unix的Sun Microsystems 。
So, malware got its start on Unix. It jumped the fence when Windows took off and hogged the limelight. But now that Linux runs the world, it’s back. Linux and Unix-like operating systems, like macOS, are getting the full attention of threat actors.
因此,恶意软件始于Unix。 Windows起飞时,它跳出篱笆,成为众人瞩目的焦点。 但是现在Linux运转了,它又回来了。 像macOS这样Linux和Unix之类的操作系统正受到威胁参与者的充分关注。
What danger remains if you’re careful, sensible, and mindful when you use your computer? The answer is long and detailed. To condense it somewhat, cyberattacks are many and varied. They’re capable of doing things that, just a short while ago, were considered impossible.
如果您在使用计算机时谨慎,明智和专心,仍然会有什么危险? 答案是冗长而详尽的。 为了进行某种程度的压缩,网络攻击是多种多样的。 他们有能力做不久前被认为是不可能的事情。
Rootkits, like Ryuk, can infect computers when they’re turned off by compromising the wake-on-LAN monitoring functions. Proof-of-concept code has also been developed. A successful “attack” was demonstrated by researchers at Ben-Gurion University of the Negev that would allow threat actors to exfiltrate data from an air-gapped computer.
像Ryuk一样,Rootkit在关闭计算机时也可以通过损害局域网唤醒监控功能来感染计算机。 还开发了概念验证代码。 内盖夫本古里安大学的研究人员证明了一次成功的“攻击”,它将使威胁者能够从一台气隙不堪的计算机中窃取数据。
It’s impossible to predict what cyberthreats will be capable of in the future. However, we do understand which points in a computer’s defenses are vulnerable. Regardless of the nature of present or future attacks, it only makes sense to plug those gaps in advance.
无法预测未来的网络威胁将具有什么样的能力。 但是,我们确实了解计算机防御中的哪一点是易受攻击的。 无论当前或将来的攻击的性质如何,只有事先填补这些空白才有意义。
Of the total number of cyberattacks, only a small percentage are consciously targeted at specific organizations or individuals. Most threats are indiscriminate because malware doesn’t care who you are. Automated port-scanning and other techniques just seek out vulnerable systems and attack them. You nominate yourself as a victim by being vulnerable.
在网络攻击的总数中,只有一小部分有意识地针对特定组织或个人。 大多数威胁是不加区分的,因为恶意软件并不关心您是谁。 自动化的端口扫描和其他技术只是找出易受攻击的系统并对其进行攻击。 您因脆弱而提名自己为受害者。
And that’s where Lynis comes in.
这就是Lynis的用武之地。
安装Lynis (Installing Lynis)
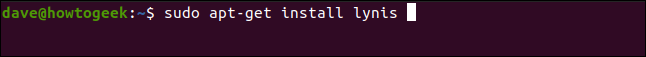
To install Lynis on Ubuntu, run the following command:
要在Ubuntu上安装Lynis,请运行以下命令:
sudo apt-get install lynis
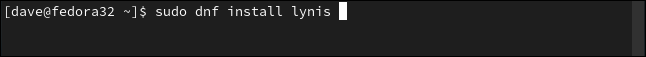
On Fedora, type:
在Fedora上,输入:
sudo dnf install lynis
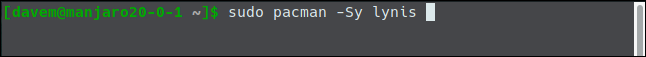
On Manjaro, you use pacman:
在Manjaro上,您使用pacman :
sudo pacman -Sy lynis
进行审核 (Conducting an Audit)
Lynis is terminal-based, so there’s no GUI. To start an audit, open a terminal window. Click and drag it to the edge of your monitor to make it snap to full height or stretch it as tall as it can go. There’s a lot of output from Lynis, so the taller the terminal window is, the easier it will be to review.
Lynis是基于终端的,因此没有GUI。 要开始审核,请打开一个终端窗口。 单击并将其拖动到显示器的边缘,使其捕捉到最大高度或将其拉伸到可能的高度。 Lynis的输出很多,因此终端窗口越高,审查起来就越容易。
It’s also more convenient if you open a terminal window specifically for Lynis. You’ll be scrolling up and down a lot, so not having to deal with the clutter of previous commands will make navigating the Lynis output easier.
如果打开专门用于Lynis的终端窗口,也将更加方便。 您将上下滚动很多,因此不必处理先前命令的混乱情况,将使Lynis输出的导航更加容易。
To start the audit, type this refreshingly straightforward command:
要开始审核,请键入以下令人耳目一新的简单命令:
sudo lynis audit system
Category names, test titles, and results will scroll in the terminal window as each category of tests is completed. An audit only takes a few minutes at most. When it’s finished, you’ll be returned to the command prompt. To review the findings, just scroll the terminal window.
每个测试类别完成后,类别名称,测试标题和结果将在终端窗口中滚动。 审核最多只需要几分钟。 完成后,您将返回到命令提示符。 要查看结果,只需滚动终端窗口。
The first section of the audit detects the version of Linux, kernel release, and other system details.
审核的第一部分将检测Linux的版本,内核发行版和其他系统详细信息。

Areas that need to be looked at are highlighted in amber (suggestions) and red (warnings that should be addressed).
琥珀色(建议)和红色(需要注意的警告)以黄色突出显示需要检查的区域。
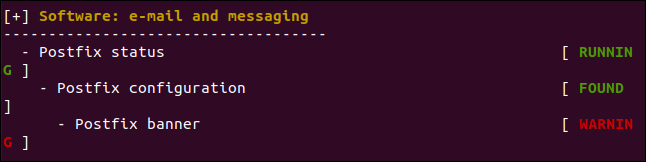
Below is an example of a warning. Lynis has analyzed the postfix mail server configuration and flagged something to do with the banner. We can get more details of exactly what it found and why it might be an issue later.
以下是警告示例。 Lynis分析了postfix邮件服务器的配置,并标记了与横幅有关的内容。 我们将获得更多有关其发现内容的详细信息,以及以后可能会引起问题的原因。
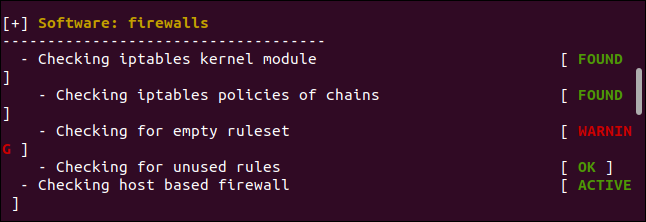
Below, Lynis warns us that the firewall isn’t configured on the Ubuntu virtual machine we’re using.
下面,Lynis警告我们在使用的Ubuntu虚拟机上未配置防火墙。
Scroll through your results to see what Lynis flagged. At the bottom of the audit report, you’ll see a summary screen.
滚动浏览结果以查看Lynis标记的内容。 在审核报告的底部,您将看到一个摘要屏幕。
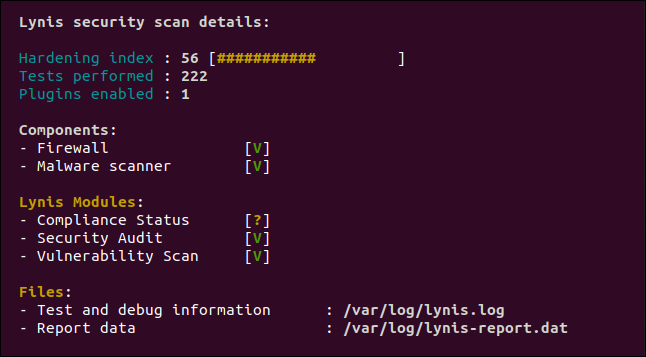
The “Hardening Index” is your exam score. We got 56 out of 100, which isn’t great. There were 222 tests performed and one Lynis plugin is enabled. If you go to the Lynis Community Edition plugin download page and subscribe to the newsletter, you’ll get links to more plugins.
“强化指数”是您的考试成绩。 我们的100分中有56分,这不是很好。 进行了222个测试,并且启用了一个Lynis插件。 如果您转到Lynis Community Edition插件下载页面并订阅新闻通讯,则将获得指向更多插件的链接。
There are many plugins, including some for auditing against standards, such as GDPR, ISO27001, and PCI-DSS.
有许多插件,其中包括一些用于根据标准审核的插件,例如GDPR , ISO27001和PCI-DSS 。
A green V represents a check mark. You might also see amber question marks and red X’s.
绿色的V表示复选标记。 您可能还会看到琥珀色的问号和红色的X。
We have green check marks because we have a firewall and malware scanner. For test purposes, we also installed rkhunter, a rootkit detector, to see whether Lynis would discover it. As you can see above, it did; we got a green check mark next to “Malware Scanner.”
我们有绿色的复选标记,因为我们有防火墙和恶意软件扫描程序。 为了进行测试,我们还安装了rootkit检测器rkhunter ,以查看Lynis是否会发现它。 正如您在上面看到的,它确实做到了; 我们在“恶意软件扫描程序”旁边显示了一个绿色的复选标记。
The compliance status is unknown because the audit didn’t use a compliance plugin. The security and vulnerability modules were used in this test.
由于审核未使用合规性插件,因此合规性状态未知。 此测试中使用了安全性和漏洞模块。
Two files are generated: a log and data file. The data file, located at “/var/log/lynis-report.dat,” is the one we’re interested in. It will contain a copy of the results (without the color highlighting) that we can see in the terminal window. These come in handy to see how your hardening index improves over time.
生成两个文件:日志文件和数据文件。 数据文件位于“ /var/log/lynis-report.dat”,是我们感兴趣的文件。它将包含结果的副本(不突出显示颜色),可以在终端窗口中查看。 这些将很方便地查看您的硬化指数如何随时间提高。
If you scroll backward in the terminal window, you’ll see a list of suggestions and another of warnings. The warnings are the “big ticket” items, so we’ll look at those.
如果在终端窗口中向后滚动,则会看到建议列表和其他警告。 警告是“大问题”项,因此我们将对其进行研究。
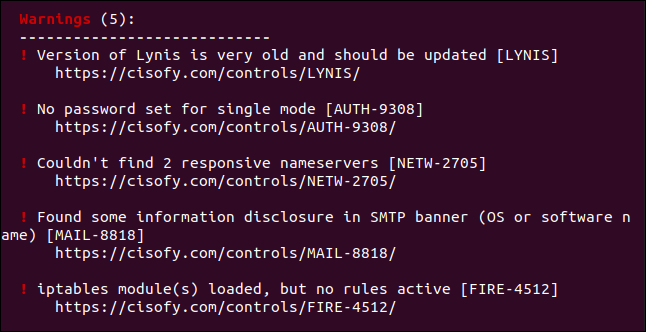
These are the five warnings:
以下是五个警告:
“Version of Lynis is very old and should be updated”: This is actually the newest version of Lynis in the Ubuntu repositories. Although it’s only 4 months old, Lynis considers this very old. The versions in the Manjaro and Fedora packages were newer. Updates in package managers are always likely to be slightly behind. If you really want the latest version you can clone the project from GitHub and keep it synchronized.
“ Lynis的版本非常旧,应该进行更新”:实际上,这是Ubuntu存储库中Lynis的最新版本。 虽然只有4个月大,但Lynis认为这很老。 Manjaro和Fedora软件包中的版本较新。 程序包管理器中的更新总是可能会稍微落后。 如果您确实想要最新版本,则可以从GitHub克隆项目并使其保持同步。
“No password set for single mode”: Single is a recovery and maintenance mode in which only the root user is operational. No password is set for this mode by default.
“未为单一模式设置密码”:单一是一种恢复和维护模式,其中只有root用户可以操作。 默认情况下,没有为该模式设置密码。
“Couldn’t find 2 responsive nameservers”: Lynis tried to communicate with two DNS servers, but was unsuccessful. This is a warning that if the current DNS server failed, there’d be no automatic roll-over to another.
“找不到2个响应性名称服务器”: Lynis尝试与两个DNS服务器通信,但未成功。 这是一个警告,如果当前的DNS服务器出现故障,则不会自动将其移到另一台。
“Found some information disclosure in SMTP banner”: Information disclosure happens when applications or network equipment give away their make and model numbers (or other info) in standard replies. This can give threat actors or automated malware insight into the types of vulnerability to check for. Once they’ve identified the software or device they’ve connected to, a simple lookup will find the vulnerabilities they can try to exploit.
“在SMTP标语中找到了一些信息泄漏”:当应用程序或网络设备在标准答复中放弃其制造商和型号(或其他信息)时,就会发生信息泄漏。 这可以使威胁参与者或自动恶意软件洞悉要检查的漏洞类型。 一旦他们确定了已连接的软件或设备,就可以通过简单的查找找到可以尝试利用的漏洞。
“iptables module(s) loaded, but no rules active”: The Linux firewall is up and running, but there are no rules set for it.
“已加载iptables模块,但未激活任何规则”: Linux防火墙已启动并正在运行,但未为其设置任何规则。
清除警告 (Clearing Warnings)
Each warning has a link to a webpage that describes the issue and what you can do to remedy it. Just hover your mouse pointer over one of the links, and then press Ctrl and click it. Your default browser will open on the webpage for that message or warning.
每个警告都有指向该问题的网页以及描述该问题的解决方法的链接。 只需将鼠标指针悬停在链接之一上,然后按Ctrl并单击它。 您的默认浏览器将在网页上打开该消息或警告。
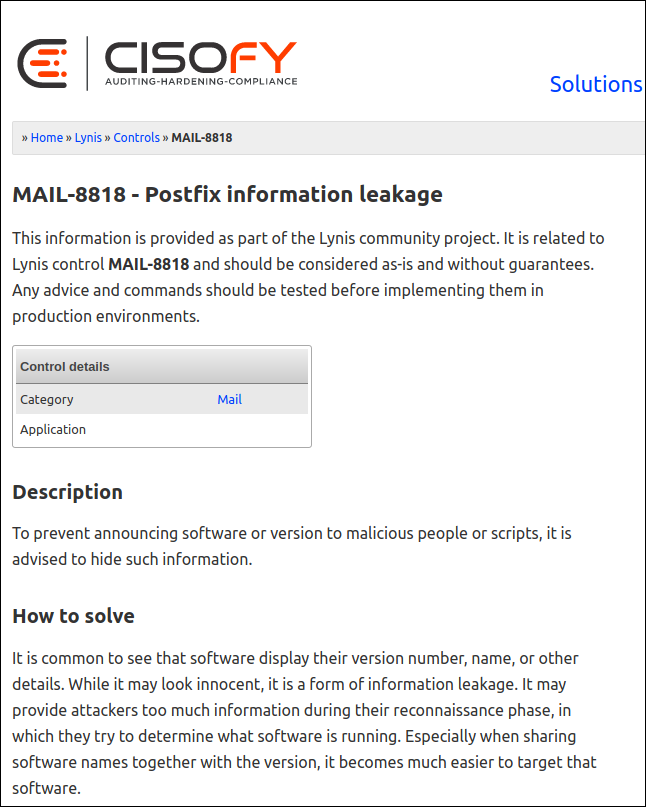
The page below opened for us when we Ctrl+clicked on the link for the fourth warning we covered in the previous section.
当我们Ctrl +单击上一节中涉及的第四个警告的链接时,下面的页面为我们打开了。
You can review each of these and decide which warnings to address.
您可以查看所有这些警告并确定要解决的警告。
The web page above explains that the default snippet of information (the “banner”) sent to a remote system when it connects to the postfix mail server configured on our Ubuntu computer is too verbose. There’s no benefit to offering too much information—in fact, that’s often used against you.
上面的网页说明,当连接到我们的Ubuntu计算机上配置的postfix邮件服务器时,发送到远程系统的默认信息片段(“横幅”)太冗长。 提供过多的信息没有任何好处-实际上,这种信息经常对您不利。
The web page also tells us the banner resides in “/etc/postfix/main.cf.” It advises us that it should be trimmed back to only show “$myhostname ESMTP.”
该网页还告诉我们标语位于“ /etc/postfix/main.cf”中。 它建议我们将其修剪为仅显示“ $ myhostname ESMTP”。
We type the following to edit the file as Lynis recommends:
我们按照Lynis的建议键入以下内容来编辑文件:
sudo gedit /etc/postfix/main.cf
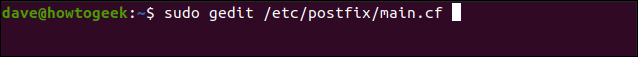
We locate the line in the file that defines the banner.
我们在定义横幅的文件中找到该行。
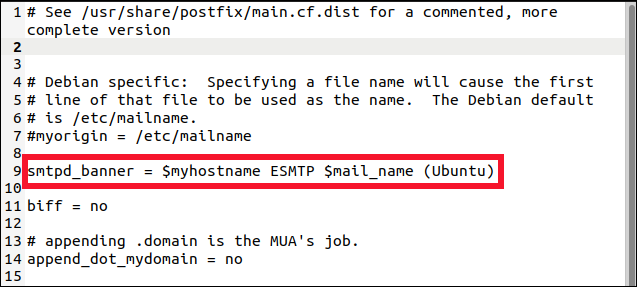
We edit it to show only the text Lynis recommended.
我们对其进行编辑以仅显示Lynis建议的文本。
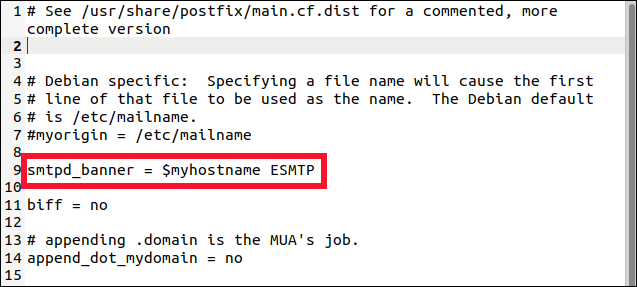
We save our changes and close gedit. We now need to restart the postfix mail server for the changes to take effect:
我们保存更改并关闭gedit 。 现在,我们需要重新启动postfix邮件服务器,以使更改生效:
sudo systemctl restart postfix
Now, let’s run Lynis once more and see if our changes have had an effect.
现在,让我们再次运行Lynis,看看我们的更改是否生效。

The “Warnings” section now only shows four. The one referring to postfix is gone.
现在,“警告”部分仅显示四个。 提到postfix那个不见了。
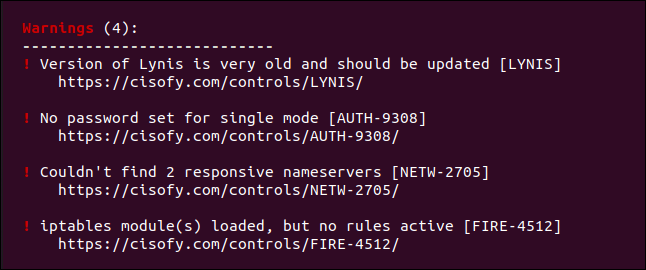
One down, and just four more warnings and 50 suggestions to go!
一击下来,只有四个警告和50条建议可以解决!
你应该走多远? (How Far Should You Go?)
If you’ve never done any system hardening on your computer, you’ll likely have roughly the same number of warnings and suggestions. You should review them all and, guided by the Lynis webpages for each, make a judgment call about whether to address it.
如果您从未在计算机上进行过任何系统强化,则警告和建议的数量可能大致相同。 您应该查看所有内容,并在Lynis网页的指导下,对是否解决进行判断。
The textbook method, of course, would be to try to clear them all. That might be easier said than done, though. Plus, some of the suggestions might be overkill for the average home computer.
当然,教科书的方法是尝试清除所有内容。 不过,说起来容易做起来难。 此外,对于一般的家用计算机,某些建议可能会显得过分杀伤力。
Blacklist the USB kernel drivers to disable USB access when you’re not using it? For a mission-critical computer that provides a sensitive business service, this might be necessary. But for an Ubuntu home PC? Probably not.
在不使用USB内核驱动程序时将其列入黑名单以禁用USB访问? 对于提供敏感业务服务的关键任务计算机,这可能是必需的。 但是对于Ubuntu家用PC? 可能不是。
翻译自: https://www.howtogeek.com/674288/how-to-audit-your-linux-systems-security-with-lynis/
安全 lynis





















 3843
3843











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








