本博客只针对自己的学习spring security过程记录,根据所学情况会继续更新
Spring Security入门案例
1.创建springboot项目,导入依赖
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
2.创建控制器类
@RestController
public class HelloController {
@GetMapping("/hello")
public String hello(){
return "hello security";
}
}
3.测试,启动springboot应用,访问http://localhost:8080/hello,弹出一个登录界面,
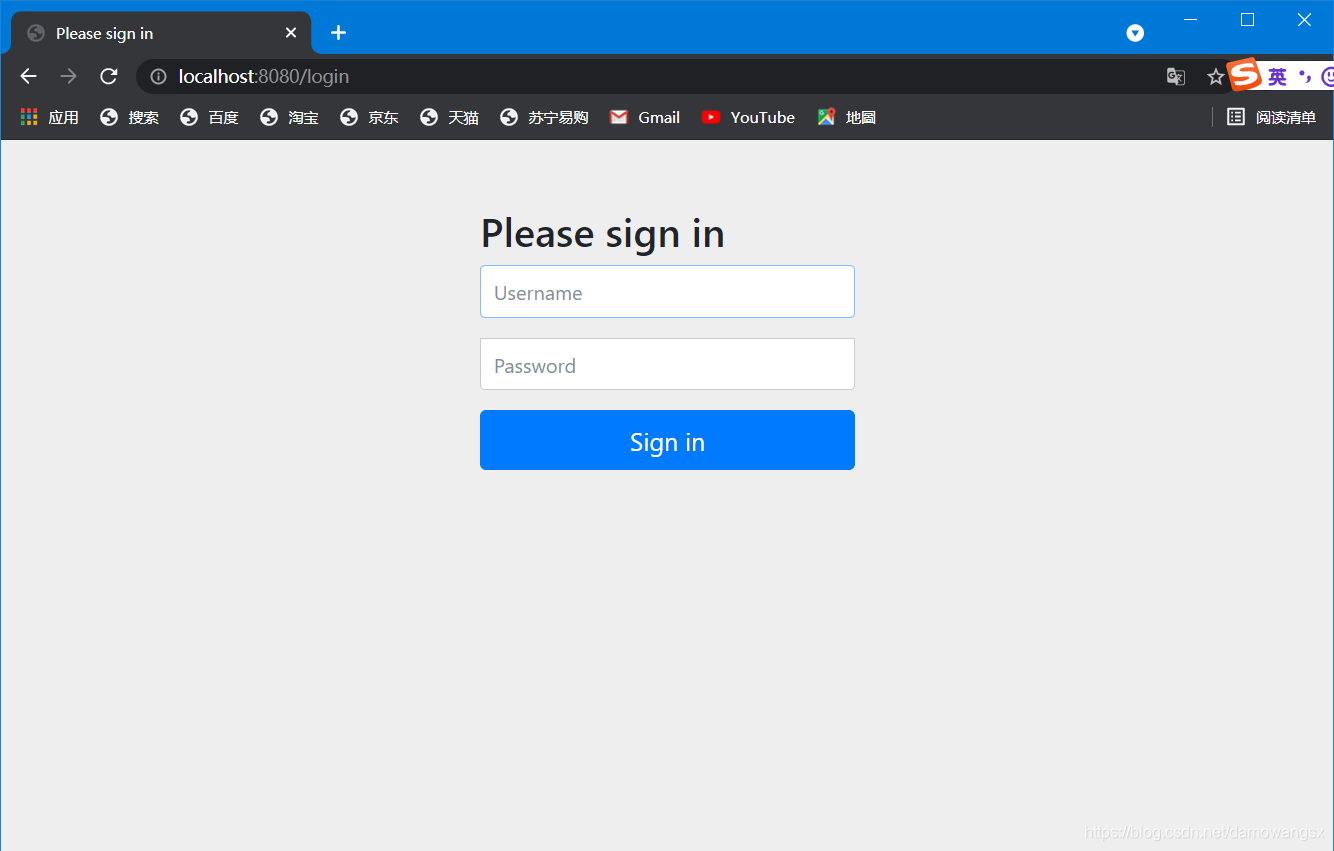
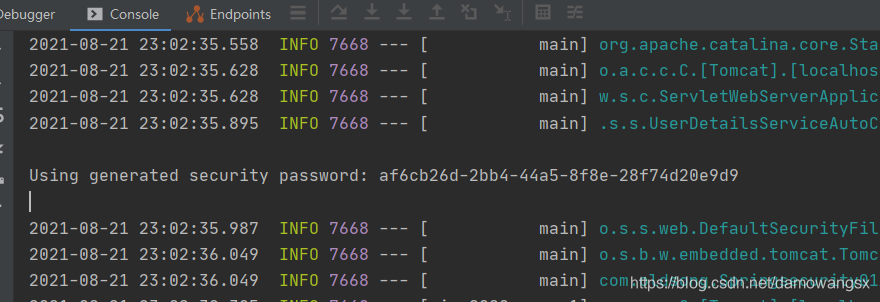
在控制台中会给一个默认的密码,用户名为user,
进行登录
SpirngSecurity的核心过滤器
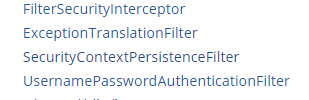
FilterSecurityInterceptor负责处理HTTP资源的安全性.。
ExceptionTranslationFilter在FilterSecurityInterceptor安全过滤器堆栈的上面。它没有做任何实际的安全执法本身,而是处理由安全拦截器抛出的异常,并提供合适的HTTP响应。
SecurityContextPersistenceFilter
请求开始时从对应的SecurityContextRepository获取securityContext存入SecurityContextHolder中,请求结束时清除SecurityContextHolder中的securityContext,将本次请求执行后新的SecurityContext存入到对应的SecurityContextRepository中。
UsernamePasswordAuthenticationFilter是身份认证过滤器。
SpringSecurity基于数据库的认证
1.创建数据库表
CREATE DATABASE `springsecurity` DEFAULT CHARACTER SET utf8;
USE `springsecurity`;
DROP TABLE IF EXISTS `user`;
CREATE TABLE `user`(
`id` INT(11) NOT NULL AUTO_INCREMENT,
`username` VARCHAR(32) DEFAULT NULL,
`password` VARCHAR(255) DEFAULT NULL,
`enabled` TINYINT(1) DEFAULT NULL,
`locked` TINYINT(1) DEFAULT NULL,
PRIMARY KEY(`id`)
)ENGINE=INNODB DEFAULT CHARSET=utf8;
DROP TABLE IF EXISTS `role`;
CREATE TABLE `role`(
`id` INT(11) NOT NULL AUTO_INCREMENT,
`name` VARCHAR(32) DEFAULT NULL,
`nameZh` VARCHAR(32) DEFAULT NULL,
PRIMARY KEY(`id`)
)ENGINE=INNODB DEFAULT CHARSET=utf8;
DROP TABLE IF EXISTS `user_role`;
CREATE TABLE `user_role`(
`id` INT(11) NOT NULL AUTO_INCREMENT,
`uid` INT(11) DEFAULT NULL,
`rid` INT(11) DEFAULT NULL,
PRIMARY KEY(`id`)
)ENGINE=INNODB DEFAULT CHARSET=utf8;
INSERT INTO `user`(`id`,`username`,`password`,`enabled`,`locked`)
VALUES
(1,'root','$2a$10$RmuFXGQ5AtH4wOvkUqyvuecpqUSeoxZYqi1Xzbz50dceRsga.WYiq',1,0),
(2,'admin','$2a$10$RmuFXGQ5AtH4wOvkUqyvuecpqUSeoxZYqi1Xzbz50dceRsga.WYiq',1,0),
(3,'sang','$2a$10$RmuFXGQ5AtH4wOvkUqyvuecpqUSeoxZYqi1Xzbz50dceRsga.WYiq',1,0);
INSERT INTO `role`(`id`,`name`,`nameZh`)
VALUES
(1,'ROLE_dba','数据库管理员'),
(2,'ROLE_admin','系统管理员'),
(3,'ROLE_user','用户');
INSERT INTO `user_role`(`id`,`uid`,`rid`)
VALUES
(1,1,1),
(2,1,2),
(3,2,2),
(4,3,3);
2.创建spirngboot项目,导入依赖
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
<dependency>
<groupId>org.mybatis.spring.boot</groupId>
<artifactId>mybatis-spring-boot-starter</artifactId>
<version>1.3.2</version>
</dependency>
<dependency>
<groupId>mysql</groupId>
<artifactId>mysql-connector-java</artifactId>
<scope>runtime</scope>
</dependency>
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>druid</artifactId>
<version>1.1.10</version>
</dependency>
3.配置数据库在properties中进行数据库连接配置
spring.datasource.password=root
spring.datasource.username=root
spring.datasource.url=jdbc:mysql:///springsecurity
spring.datasource.type=com.alibaba.druid.pool.DruidDataSource
4.创建实体类
public class Role {
private Integer id;
private String name;
private String nameZh;
@Override
public String toString() {
return "Role{" +
"id=" + id +
", name='" + name + '\'' +
", nameZh='" + nameZh + '\'' +
'}';
}
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
public String getName() {
return name;
}
public void setName(String name) {
this.name = name;
}
public String getNameZh() {
return nameZh;
}
public void setNameZh(String nameZh) {
this.nameZh = nameZh;
}
}
import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.authority.SimpleGrantedAuthority;
import org.springframework.security.core.userdetails.UserDetails;
import java.util.ArrayList;
import java.util.Collection;
import java.util.List;
public class User implements UserDetails {
private Integer id;
private String username;
private String password;
private Boolean enabled;
private Boolean locked;
private List<Role> roles;
@Override
public Collection<? extends GrantedAuthority> getAuthorities() {
List<SimpleGrantedAuthority> authorities=new ArrayList<>();
for(Role role:roles){
authorities.add(new SimpleGrantedAuthority(role.getName()));
}
return authorities;
}
@Override
public String getPassword() {
return password;
}
@Override
public String getUsername() {
return username;
}
@Override
public boolean isAccountNonExpired() {
return true;
}
@Override
public boolean isAccountNonLocked() {
return !locked;
}
@Override
public boolean isCredentialsNonExpired() {
return true;
}
@Override
public boolean isEnabled() {
return enabled;
}
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
public void setUsername(String username) {
this.username = username;
}
public void setPassword(String password) {
this.password = password;
}
public Boolean getEnabled() {
return enabled;
}
public void setEnabled(Boolean enabled) {
this.enabled = enabled;
}
public Boolean getLocked() {
return locked;
}
public void setLocked(Boolean locked) {
this.locked = locked;
}
public List<Role> getRoles() {
return roles;
}
public void setRoles(List<Role> roles) {
this.roles = roles;
}
@Override
public String toString() {
return "User{" +
"id=" + id +
", username='" + username + '\'' +
", password='" + password + '\'' +
", enabled=" + enabled +
", locked=" + locked +
", roles=" + roles +
'}';
}
}
UserDetails接口的七个方法的用法
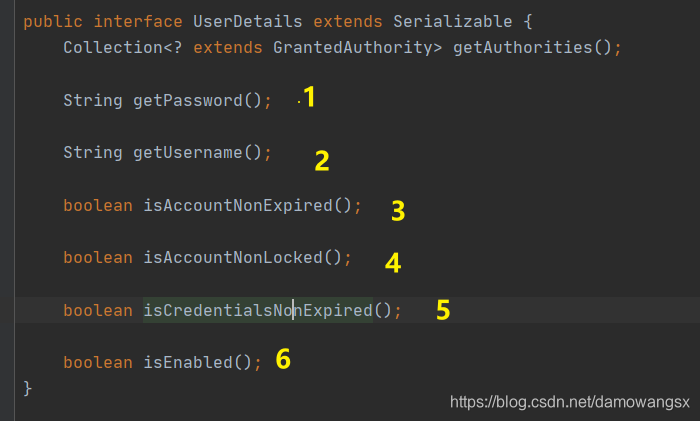
1.获取当前用户对象的密码
2.获取当前用户对象的用户名
3.当前用户是否未过期
4.当前账户是否未锁定
5.当前账户密码是否未过期
6.当前账户是否可用
5.创建UserService 、UserMapper、UserMapper.xml
定义UserService实现UserDetailsService接口,并实现该接口中的loadUserByUsername方法,该方法的参数就是用户登录时输入的用户名,通过用户名去数据库中查找用户,如果没有查到用户,就抛出一个用户不存在的异常,如果查找到用户,就继续查找该用户所具有的角色信息,并将获取到的user对象返回,再由系统提供的DaoAuthenticationProvider类去比对密码是否正确。
loadUserByUsername方法将在用户登录时自动调用
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.core.userdetails.UsernameNotFoundException;
import org.springframework.stereotype.Service;
@Service
public class UserService implements UserDetailsService {
@Autowired
UserMapper userMapper;
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
User user=userMapper.loadUserByUsername(username);
if(user==null){
throw new UsernameNotFoundException("账户不存在");
}
user.setRoles(userMapper.getUserRolesByUid(user.getId()));
return user;
}
}
import org.apache.ibatis.annotations.Mapper;
import java.util.List;
@Mapper
public interface UserMapper {
User loadUserByUsername(String username);
List<Role> getUserRolesByUid(Integer id);
}
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE mapper
PUBLIC "-//mybatis.org//DTD Mapper 3.0//EN"
"http://mybatis.org/dtd/mybatis-3-mapper.dtd">
<mapper namespace="com.oldsong.UserMapper">
<select id="loadUserByUsername" resultType="com.oldsong.User">
select * from user where username=#{username};
</select>
<select id="getUserRolesByUid" resultType="com.oldsong.Role">
select * from role r,user_role ur where r.id=ur.rid and ur.uid=#{id}
</select>
</mapper>
6.配置SpringSecurity
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.crypto.password.PasswordEncoder;
@Configuration
public class WebSecurityConfig extends WebSecurityConfigurerAdapter {
@Autowired
UserService userService;
@Bean
PasswordEncoder passwordEncoder(){
return new BCryptPasswordEncoder(10);
}
@Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.userDetailsService(userService);
}
@Override
protected void configure(HttpSecurity http) throws Exception {
http.authorizeRequests()
.antMatchers("/admin/**").hasRole("admin")
.antMatchers("/db/**").hasRole("dba")
.antMatchers("/user/**").hasRole("user")
.anyRequest().authenticated()
.and()
.formLogin()
.loginProcessingUrl("/login").permitAll()
.and()
.csrf().disable();
}
}
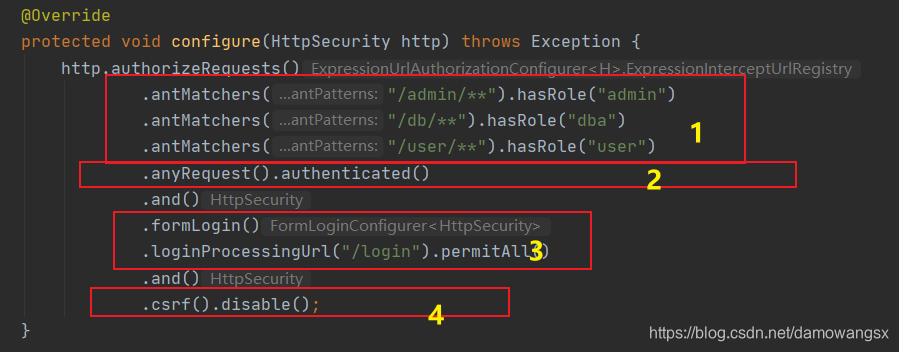
authorizeRequests()方法开启HttpSecurity的配置
1.表示用户方法“/admin/**”模式的URL必须具备ADMIN角色
2.表示除了前面定义的URL模式之外,用户方法其他的URL都必须认证后访问
3.配置登录接口为“/login”即可以直接调用“/login"接口,发起一个POST的请求进行登录,登录参数中用户名必须为username,密码必须命名为password,配置loginProcessingUrl接口主要是方便Ajax或者移动端调用登录接口。最后还配置了permitAll,表示与登录相关的接口都不需要认证即可访问
4.关闭csrf
本人测试过了 测试过程我就不写了 我自己看太多余,如果你想的话可以自己定义一个Controller来访问各个路径
动态配置权限
创建数据库表
CREATE TABLE `menu`(
`id` INT(11) NOT NULL AUTO_INCREMENT,
`pattern` VARCHAR(128) DEFAULT NULL,
PRIMARY KEY(`id`)
)ENGINE=INNODB DEFAULT CHARSET=utf8;
DROP TABLE IF EXISTS `menu_role`;
CREATE TABLE `menu_role`(
`id` INT(11) NOT NULL AUTO_INCREMENT,
`mid` INT(11) DEFAULT NULL,
`rid` INT(11) DEFAULT NULL,
PRIMARY KEY(`id`)
)ENGINE=INNODB DEFAULT CHARSET=utf8;
INSERT INTO `menu_role`(`id`,`mid`,`rid`)
VALUES
(1,1,1),
(2,2,2),
(3,3,3);
INSERT INTO `menu`(`id`,`pattern`)
VALUES
(1,'/db/**'),
(2,'/admin/**'),
(3,'/user/**');
2.自定义FilterInvocationSecurityMetadataSource、MenuMapper、MenuMapper.xml
要实现动态配置权限,首先要定义FilterInvocationSecurityMetadataSource,SpringSecurity中通过FilterInvocationSecurityMetadataSource接口中的getAttributes方法来确定一个请求需要哪些角色,
FilterInvocationSecurityMetadataSource接口的默认实现类是DefaultFilterInvocationSecurityMetadataSource,参考DefaultFilterInvocationSecurityMetadataSource开发者可以自定义FilterInvocationSecurityMetadataSource
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.access.ConfigAttribute;
import org.springframework.security.access.SecurityConfig;
import org.springframework.security.web.FilterInvocation;
import org.springframework.security.web.access.intercept.FilterInvocationSecurityMetadataSource;
import org.springframework.util.AntPathMatcher;
import java.util.Collection;
import java.util.List;
public class CustomFilterInvocationSecurityMetadataSource
implements FilterInvocationSecurityMetadataSource {
AntPathMatcher antPathMatcher=new AntPathMatcher();
@Autowired
MenuMapper menuMapper;
@Override
public Collection<ConfigAttribute> getAttributes(Object object) throws IllegalArgumentException {
String requestUrl=((FilterInvocation)object).getRequestUrl();
List<Menu> allMenus=menuMapper.getAllMenus();
for(Menu menu:allMenus){
if(antPathMatcher.match(menu.getPattern(),requestUrl)){
List<Role> roles=menu.getRoles();
String[] roleArr=new String[roles.size()];
for (int i = 0; i <roleArr.length ; i++) {
roleArr[i]=roles.get(i).getName();
}
return SecurityConfig.createList(roleArr);
}
}
return SecurityConfig.createList("ROLE_LOGIN");
}
@Override
public Collection<ConfigAttribute> getAllConfigAttributes() {
return null;
}
@Override
public boolean supports(Class<?> aClass) {
return FilterInvocation.class.isAssignableFrom(aClass);
}
}
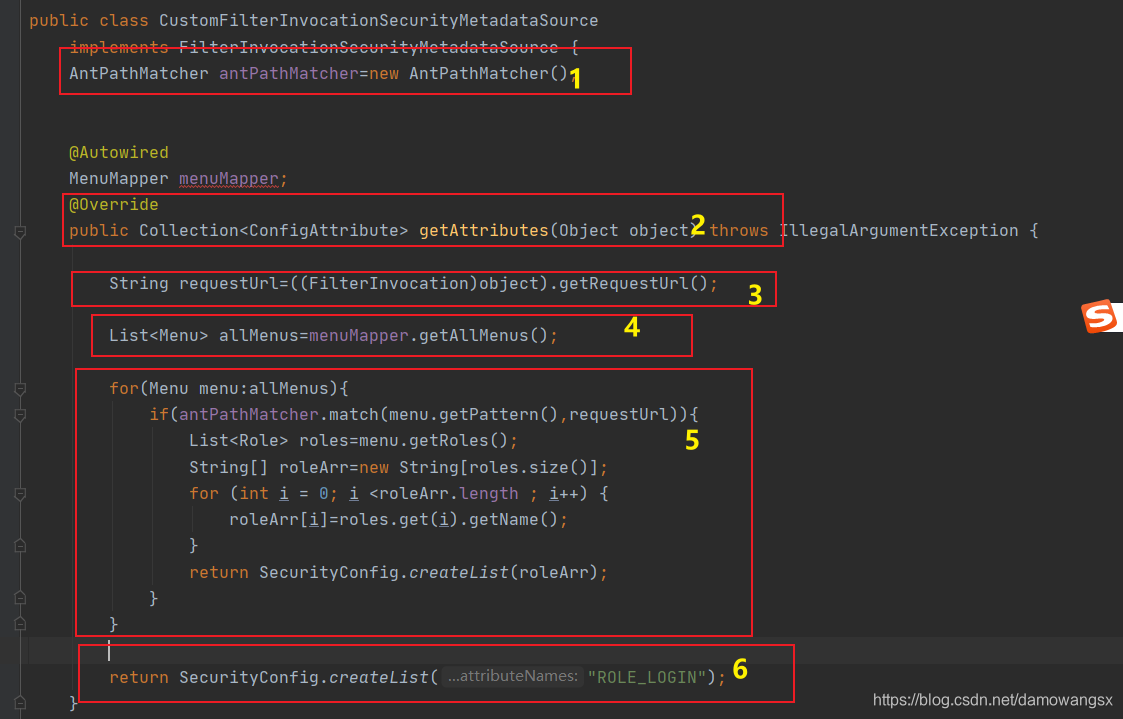
1.AntPathMatcher,主要用来实现ant风格的URL匹配
2.开发者自定义FilterInvocationSecurityMetadataSource主要实现该接口中getAttributes方法,该方法的参数是一个FilterInvocation,开发者可以从FilterInvocation中提取当前请求中的URL返回值是Collection,表示当前请求URL所需要的的角色
3.提取当前的URL
4.从数据库中获取所有的资源信息
5.遍历过程中过去当前请求的URL所需要的角色信息并返回。
6.如果当前请求的URL在资源表中不存在相应的模式,就假设该请求登录后即可访问。返回ROLE_LOGIN
import org.apache.ibatis.annotations.Mapper;
import java.util.List;
@Mapper
public interface MenuMapper {
List<Menu> getAllMenus();
}
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE mapper
PUBLIC "-//mybatis.org//DTD Mapper 3.0//EN"
"http://mybatis.org/dtd/mybatis-3-mapper.dtd">
<mapper namespace="com.oldsong.MenuMapper">
<resultMap id="BaseResultMap" type="com.oldsong.Menu">
<id property="id" column="id"/>
<result property="pattern" column="pattern"/>
<collection property="roles" ofType="com.oldsong.Role">
<id property="id" column="rid"/>
<result property="name" column="rname"/>
<result property="nameZh" column="rnameZh"/>
</collection>
</resultMap>
<select id="getAllMenus" resultMap="BaseResultMap">
select m.*,r.id AS rid,r.name AS rname,r.nameZh AS rnameZh FROm menu m
LEFT JOIN menu_role mr ON m.`id`=mr.`mid` LEFT JOIN role r ON mr.`rid`=r.`id`
</select>
</mapper>
3.自定义AccessDecisionManager
当一个请求走完FilterInvocationSecurityMetadataSource中的getAttributes方法后,接下来就会来到AccessDecisionManager类中进行角色对比
import org.springframework.security.access.AccessDecisionManager;
import org.springframework.security.access.AccessDeniedException;
import org.springframework.security.access.ConfigAttribute;
import org.springframework.security.authentication.InsufficientAuthenticationException;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.GrantedAuthority;
import java.util.Collection;
public class CustomAccessDecisionManager implements AccessDecisionManager {
@Override
public void decide(Authentication auth, Object object, Collection<ConfigAttribute> ca) throws AccessDeniedException, InsufficientAuthenticationException {
Collection<? extends GrantedAuthority> auths = auth.getAuthorities();
for(ConfigAttribute configAttribute:ca){
if("ROLE_LOGIN".equals(configAttribute.getAttribute())&&auth instanceof UsernamePasswordAuthenticationToken){
return ;
}
for(GrantedAuthority authority:auths){
if(configAttribute.getAttribute().equals(authority.getAuthority())){
return ;
}
}
}
throw new AccessDeniedException("权限不足");
}
@Override
public boolean supports(ConfigAttribute configAttribute) {
return true;
}
@Override
public boolean supports(Class<?> aClass) {
return true;
}
}
decide 方法有三个参数 第一个参数包含当前登录用户的信息;第二个参数则是一个FilterInvocatiion对象,可以获取当前请求对象;第三个参数就是FilterInvocationSecurityMetadataSource中的getAttributes方法的返回值,即当前请求URL所需要的的角色
如果角色是ROLE_LOGIN,说明当前请求的URL用户登录后即可访问,如何auth是UsernamePasswordAuthenticationToken的实例,那么说明当前用户已登录,方法到此结束,否则进入正常的判断流程,如果当前用户具备当前请求需要的角色,那么方法结束
4.配置
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.ObjectPostProcessor;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.security.web.access.intercept.FilterSecurityInterceptor;
@Configuration
public class WebSecurityConfig2 extends WebSecurityConfigurerAdapter {
@Bean
PasswordEncoder passwordEncoder(){
return new BCryptPasswordEncoder(10);
}
@Bean
CustomFilterInvocationSecurityMetadataSource cfisms(){
return new CustomFilterInvocationSecurityMetadataSource();
}
@Bean
CustomAccessDecisionManager cadm(){
return new CustomAccessDecisionManager();
}
@Override
protected void configure(HttpSecurity http) throws Exception {
http.authorizeRequests()
.withObjectPostProcessor(new ObjectPostProcessor<FilterSecurityInterceptor>() {
@Override
public <O extends FilterSecurityInterceptor> O postProcess(O o) {
o.setSecurityMetadataSource(cfisms());
o.setAccessDecisionManager(cadm());
return o;
}
})
.and()
.formLogin()
.loginProcessingUrl("/login").permitAll()
.and()
.csrf().disable();
}
}
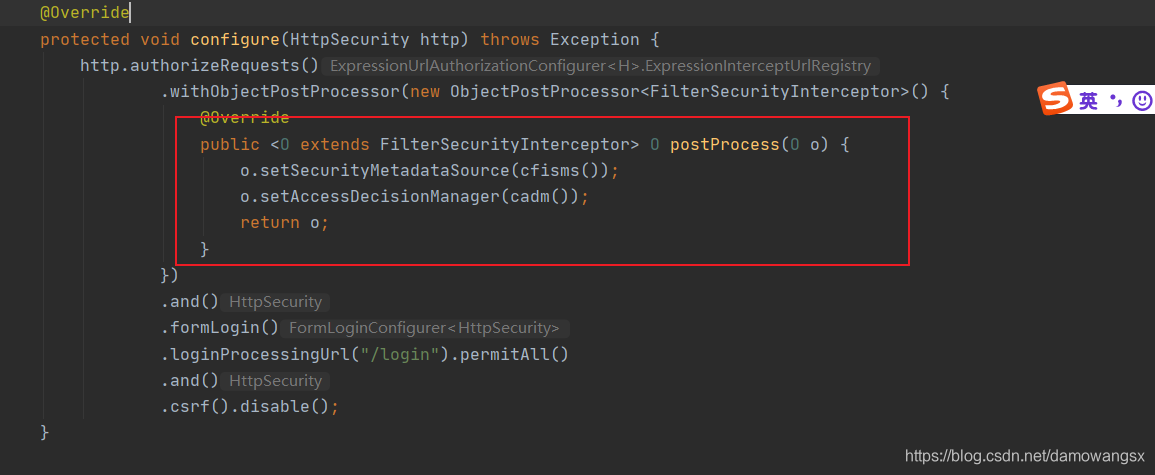
这里作者说的也不是很清楚,但是可以知道如何你想实现自定义的动态配置权限,你就需要将你自定义的两个类的实例加入到认证流程中才会生效。
本人测试过了 测试过程我就不写了 我自己看太多余,如果你想的话可以自己定义一个Controller来访问各个路径





















 1344
1344











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








