一.实验拓扑

二.实验要求
1.R5为ISP,只能进行IP地址的配置;其所有地址均配为公有IP地址
2.R1和R5之间使用ppp的pap认证,R5为主认证方;
R2和R5之间使用ppp的chap认证,R5为主认证方;
R3和R5之间使用HDLC封装;
3.R1/R2/R3构建一个MGRE环境,R1为中心站点;R1,R4间为点到点的GRE。
4.整个私有网络基于RIP全网可达;
5.所有PC设置私有IP为源IP,可以访问R5环回。
三.路由器配置
R1配置
[V200R003C00]
#
sysname R1
#
board add 0/4 2SA
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
acl number 2000
rule 5 permit source 192.168.1.0 0.0.0.255
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface Serial4/0/0
link-protocol ppp
ppp pap local-user admin password cipher %$%$\S*J:s)ZI64G'1MC4]\=,&ls%$%$
ip address 10.1.1.1 255.255.255.0
nat outbound 2000
#
interface Serial4/0/1
link-protocol ppp
#
interface GigabitEthernet0/0/0
ip address 192.168.1.1 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface Tunnel0/0/0
ip address 192.168.5.1 255.255.255.0
undo rip split-horizon
tunnel-protocol gre p2mp
source 10.1.1.1
nhrp entry multicast dynamic
nhrp network-id 100
#
interface Tunnel0/0/1
description 40.1.1.1
ip address 192.168.6.1 255.255.255.0
tunnel-protocol gre
source 10.1.1.1
#
rip 1
version 2
network 192.168.1.0
network 192.168.5.0
network 192.168.6.0
#
ip route-static 0.0.0.0 0.0.0.0 10.1.1.2
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
ReturnR2配置
[V200R003C00]
#
sysname R2
#
board add 0/4 2SA
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
acl number 2000
rule 5 permit source 192.168.2.0 0.0.0.255
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface Serial4/0/0
link-protocol ppp
ppp chap user admin1
ppp chap password cipher %$%$|.<3AWl2=CXS3eO,psVN,&FU%$%$
ip address 20.1.1.1 255.255.255.0
nat outbound 2000
#
interface Serial4/0/1
link-protocol ppp
#
interface GigabitEthernet0/0/0
ip address 192.168.2.1 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface Tunnel0/0/0
ip address 192.168.5.2 255.255.255.0
tunnel-protocol gre p2mp
source Serial4/0/0
nhrp network-id 100
nhrp entry 192.168.5.1 10.1.1.1 register
#
rip 1
version 2
network 192.168.2.0
network 192.168.5.0
#
ip route-static 0.0.0.0 0.0.0.0 20.1.1.2
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
ReturnR3配置
[V200R003C00]
#
sysname R3
#
board add 0/4 2SA
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
acl number 2000
rule 5 permit source 192.168.3.0 0.0.0.255
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface Serial4/0/0
link-protocol hdlc
ip address 30.1.1.1 255.255.255.0
nat outbound 2000
#
interface Serial4/0/1
link-protocol ppp
#
interface GigabitEthernet0/0/0
ip address 192.168.3.1 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface Tunnel0/0/0
ip address 192.168.5.3 255.255.255.0
tunnel-protocol gre p2mp
source Serial4/0/0
nhrp network-id 100
nhrp entry 192.168.5.1 10.1.1.1 register
#
rip 1
version 2
network 192.168.3.0
network 192.168.5.0
#
ip route-static 0.0.0.0 0.0.0.0 30.1.1.2
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
ReturnR4配置
[V200R003C00]
#
sysname R4
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
acl number 2000
rule 5 permit source 192.168.4.0 0.0.0.255
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 40.1.1.1 255.255.255.0
nat outbound 2000
#
interface GigabitEthernet0/0/1
ip address 192.168.4.1 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface Tunnel0/0/1
description 10.1.1.1
ip address 192.168.6.2 255.255.255.0
tunnel-protocol gre
source 40.1.1.1
#
rip 1
version 2
network 192.168.4.0
network 192.168.6.0
#
ip route-static 0.0.0.0 0.0.0.0 40.1.1.2
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
ReturnR5配置
[V200R003C00]
#
sysname R5
#
board add 0/3 2SA
board add 0/4 2SA
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$6Y9U.B~X916("|%MH>{Kf[d1%$%$
local-user admin service-type ppp
local-user admin1 password cipher %$%$-L@4@mK=1$"U.3-HpuW~f^DD%$%$
local-user admin1 service-type ppp
#
firewall zone Local
priority 15
#
interface Serial3/0/0
link-protocol ppp
ppp authentication-mode pap
ip address 10.1.1.2 255.255.255.0
#
interface Serial3/0/1
link-protocol ppp
ppp authentication-mode chap
ip address 20.1.1.2 255.255.255.0
#
interface Serial4/0/0
link-protocol hdlc
ip address 30.1.1.2 255.255.255.0
#
interface Serial4/0/1
link-protocol ppp
#
interface GigabitEthernet0/0/0
ip address 40.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 5.5.5.5 255.255.255.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
Return四.实验结果
1.R1和R5之间利用ppp的pap认证
重启R1的Serial4/0/0接口,通过抓包清晰的看到Authenticate-Request报文和Authenticate-Ack报文故而认证成功。

2.R2和R5之间利用ppp的chap认证
重启R2的Serial4/0/0接口,通过抓包清晰的看到R5发送了一个challenge报文,带了随机数c,R2回复Response,通过哈希算法把密钥和c计算并且返回,然后R5回复Success报文通过比较认证,最终通过了认证。

3.R3和R5之间使用HDLC封装
使用R3 ping R5通过抓包很明显R3和R5间使用HDLC封装成功。
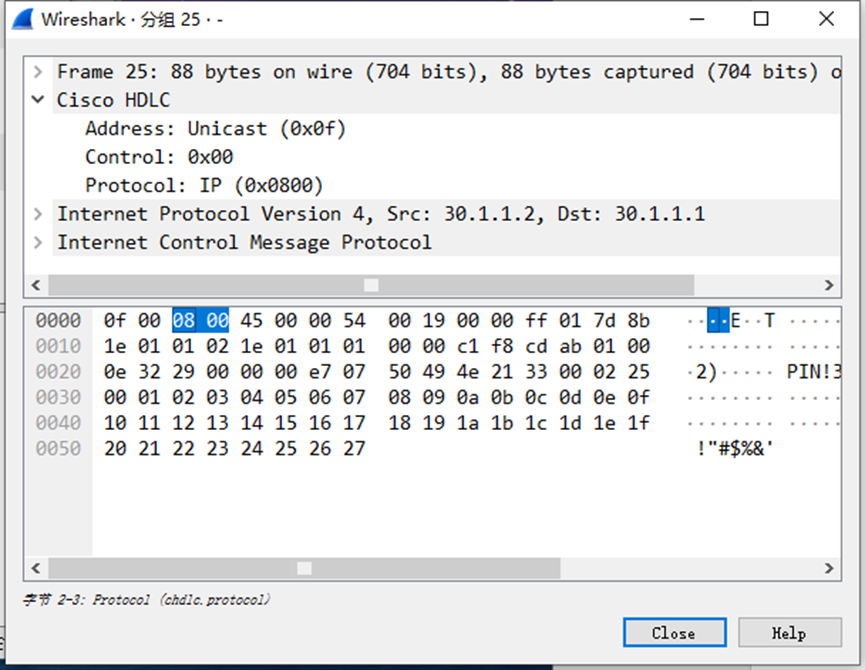
3.nhrp邻居结果
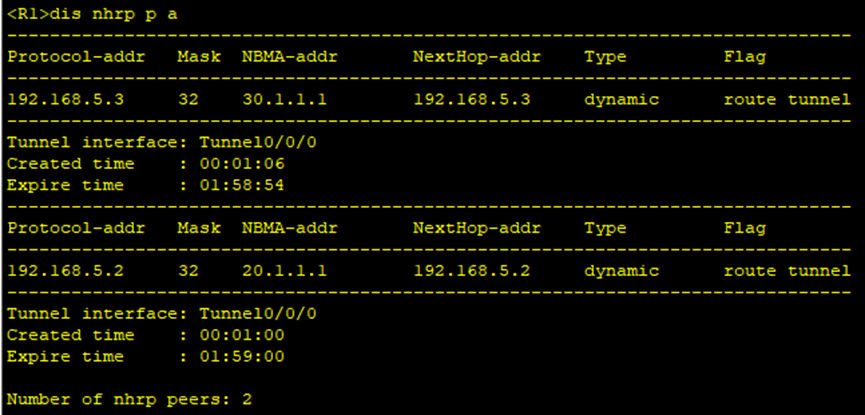
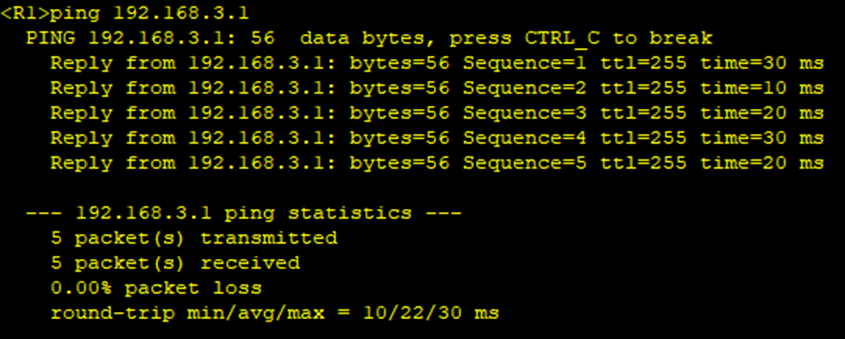
4.rip配置
Rip配置后,通过R1,R2,R3和R4之间互相ping其私网,测试结果如下,明显都是通的。
5.PC可以访问R5环回
在R1,R2,R3,R4上配置nat,然后给PC上配置IPV4,如下图所示,ping 5.5.5.5都是通的。

























 156
156











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








