VPN is a mechanism of employing encryption, authentication, and integrity protection so that we can use a public network as if it is a private network. It offers a high amount of security and allows users to remotely access private networks. In this article, we will cover every point about virtual private networks.
What is a VPN?
A virtual private network (VPN) is a technology that creates a safe and encrypted connection over a less secure network, such as the Internet. A Virtual Private Network is a way to extend a private network using a public network such as the Internet. The name only suggests that it is a “Virtual Private Network”, i.e. user can be part of a local network sitting at a remote location. It makes use of tuneling protocols to establish a secure connection.
History of VPNs
ARPANET introduced the idea of connecting distant computers in the 1960s. The foundation for current internet connectivity was established by ensuring the development of protocols like TCP/IP in the 1980s. Particular VPN technologies first appeared in the 1990s in response to the growing concerns about online privacy and security.
Need for VPN
It could easily be said that VPNs are a necessity since privacy, security, and free internet access should be everybody’s right. First, they establish secure access to the corporate networks for remote users; then, they secure the data during the transmission and, finally, they help users to avoid geo-blocking and censorship. VPNs are highly useful for protecting data on open Wi-Fi, for privacy, and preventing one’s ISP from throttling one’s internet connection.
How Does a VPN Work?
Let us understand VPN with an example think of a situation where the corporate office of a bank is situated in Washington, USA. This office has a local network consisting of say 100 computers. Suppose other branches of the bank are in Mumbai, India, and Tokyo, Japan. The traditional method of establishing a secure connection between the head office and the branch was to have a leased line between the branches and head office which was a very costly as well as troublesome job. VPN lets us effectively overcome this issue.
The situation is described below
- All 100 hundred computers of the corporate office in Washington are connected to the VPN server(which is a well-configured server containing a public IP address and a switch to connect all computers present in the local network i.e. in the US head office).
- The person sitting in the Mumbai office connects to The VPN server using a dial-up window and the VPN server returns an IP address that belongs to the series of IP addresses belonging to a local network of the corporate office.
- Thus person from the Mumbai branch becomes local to the head office and information can be shared securely over the public internet.
- So this is the intuitive way of extending the local network even across the geographical borders of the country.
VPN is well Exploited all Across the Globe
We will explain to you with an example. Suppose we are using smartphones regularly. Spotify Swedish music app that is not active in India But we are making full use of it sitting in India. So how ?? VPN can be used to camouflage our geolocation.
- Suppose the IP address is 101.22.23.3 which belongs to India. That’s why our device is not able to access the Spotify music app.
- But the magic began when we used the Psiphon app which is an Android app used to change the device IP address to the IP address of the location we want(say US where Spotify works seamlessly).
- The IP address is changed using VPN technology. Basically what happens is that your device will connect to a VPN server of the respective country that you have entered in your location textbox of the Psiphon app and now you will inherit a new IP from this server.
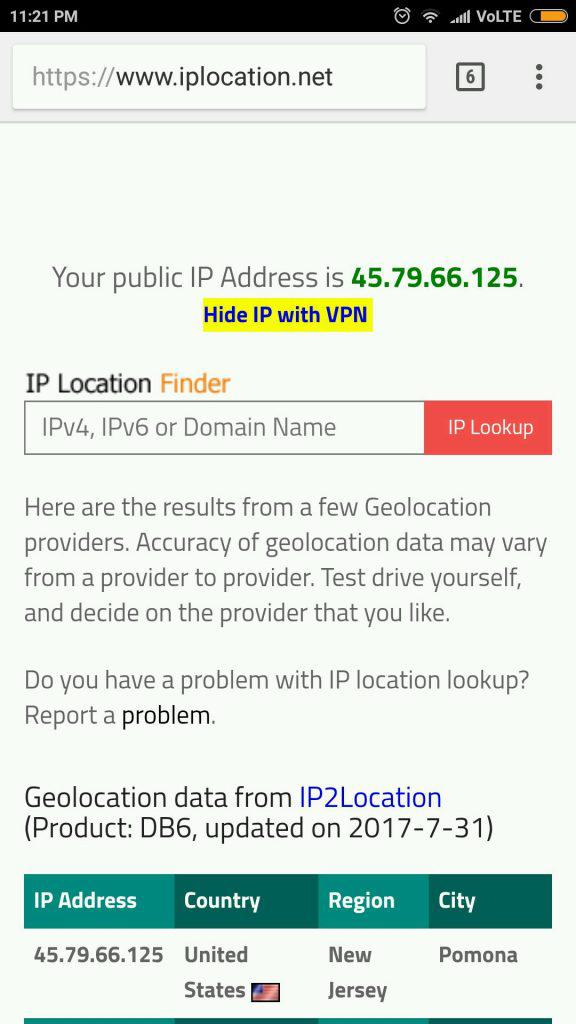
Now we typed “What is my IP address”? Amazingly the IP address changed to 45.79.66.125 which belongs to the USA And since Spotify works well in the US, we can use it now being in India (virtually in the USA). Is not that good? obviously, it is very useful.
- VPN also ensures security by providing an encrypted tunnel between the client and the VPN server.
- VPN is used to bypass many blocked sites.
- VPN facilitates Anonymous browsing by hiding your IP address.
- Also, the most appropriate Search engine optimization (SEO) is done by analyzing the data from VPN providers which provide country-wise statics of browsing a particular product.
- VPNs encrypt your internet traffic, safeguarding your online activities from potential eavesdropping and cyber threats, thereby enhancing your privacy and data protection.
Characteristics of VPN
- Encryption: VPNs employ several encryption standards to maintain the confidentiality of the transmitted data and, even if intercepted, can’t be understood.
- Anonymity: Thus, VPN effectively hides the users IP address, thus offering anonymity and making tracking by websites or other third parties impossible.
- Remote Access: VPNs provide the means for secure remote connection to business’ networks thus fostering employee productivity through remote working.
- Geo-Spoofing: The user can also change the IP address to another country using the VPN hence breaking the regional restrictions of some sites.
- Data Integrity: VPNs make sure that the data communicated in the network in the exact form and not manipulated in any way.
Types of VPN
There are several types of VPN and these are vary from specific requirement in computer network. Some of the VPN are as follows:
- Remote Access VPN
- Site to Site VPN
- Cloud VPN
- Mobile VPN
- SSL VPN
For more details you can refer Types of VPN published article.
VPN Protocols
- OpenVPN: A cryptographic protocol that prioritises security is called OpenVPN. OpenVPN is compatible protocol that provides a variety of setup choices.
- Point-To-Point Tunneling Protocol(PPTP): PPTP is not utilized because there are many other secure choices with higher and more advanced encryption that protect data.
- WireGuard: Wireguard is a good choice that indicates capability in terms of performance.
- Secure Socket Tunneling Protocol(SSTP): SSTP is developed for Windows users by Microsoft. It is not widely used due to the lack of connectivity.
- Layer 2 Tunneling Protocol(L2TP) It connects a user to the VPN server but lacks encryption hence it is frequently used with IPSec to offer connection, encryption, and security simultaneously.
Why Should Use VPN?
- For Unlimited Streaming: Love streaming your favourite shows and sports games? A VPN is your ultimate companion for unlocking streaming services.
- For elevating your Gaming Experience: Unleash your gaming potential with the added layer of security and convenience provided by a VPN. Defend yourself against vengeful competitors aiming to disrupt your gameplay while improving your ping for smoother, lag-free sessions. Additionally, gain access to exclusive games that may be restricted in your region, opening up a world of endless gaming possibilities.
- For Anonymous Torrenting: When it comes to downloading copyrighted content through torrenting, it’s essential to keep your IP address hidden. A VPN can mask your identity and avoid potential exposure, ensuring a safe and private torrenting experience.
- For supercharging your Internet Speed: Are you tired of your Internet speed slowing down when downloading large files? Your Internet Service Provider (ISP) might be intentionally throttling your bandwidth. Thankfully, a VPN can rescue you by keeping your online activities anonymous, effectively preventing ISP throttling. Say goodbye to sluggish connections and embrace blazing-fast speeds.
- Securing Public Wi-Fi: VPNs are essential for maintaining security when using public Wi-Fi networks, such as those in coffee shops, airports, or hotels. These networks are often vulnerable to cyberattacks, and using a VPN encrypts your internet connection, protecting your data from potential hackers and eavesdroppers when you connect to untrusted Wi-Fi hotspots.
Tunnelling Protocols for VPN
- OpenVPN: An open source protocol with very good security and the ability to set up the functionality to use. Secure Sockets Layer / Transport Layer Security is for the key exchange; it can go through firewalls and network address translators (NATs).
- Point-To-Point Tunneling Protocol (PPTP): Another outdated VPN protocol is PPTP as it is one of the oldest VPN protocols that are quite easy to configure but provides the weaker security than most contemporary VPN protocols.
- WireGuard: A relatively new protocol that has been widely recommended because of its relative ease of use and high performance. It incorporates modern techniques of encryption and it is perhaps easier to implement and to audit.
- Secure Socket Tunnelling Protocol (SSTP): SSTP is a Microsoft developed protocol; it is compatible with the Windows operating systems and uses SSL/TLS for encryption which is rather secure.
- Layer 2 Tunnelling Protocol (L2TP): L2TP is frequently combined with IPsec for encryption; however, L2TP does not have encryption integrated into it but does build a secure tunnel for data.
Authentication Mechanisms in VPN
- Pre-Shared Key (PSK): Is a secret key that is used for authenticating the two parties, that is, the client and the VPN server. It is easy to integrate but is also considered insecure when not administered properly.
- Digital Certificates: Based on certificates given by a reliable certificate authority, it is effective in identifying the identity of users and devices with a sense of security.
- Username and Password: Usually known in user authentication in which users submit their credentials for them to access the VPNs. This method is sometimes supported by other security measures such as MFA (multi-factor authentication).
- Two-Factor Authentication (2FA): Provides another level of protection by including a second factor of identification in the manner of a number received via one’s cellular telephone along with a user identification and password.
Security Concerns in VPN
- Data Leakage: VPNs also can some time not hide IP address and thus cause leakages of data collected. This can happen via DNS leaks or when the VPN connection is severed prematurely or when switches between servers.
- Weak Encryption: Even the security of a VPN can be affected by weak encryption standards as well as outdated encryption algorithms. In this case, it is essential to implement sound encryption/decryption methods.
- Trust in VPN Providers: VPN provider can only guarantee that they will secure the user’s data and refrain from abusing it if the user themselves trusts their service provider. Some providers may keep records of the use of the resource by a user and this can infringe on the privacy of a consumer.
- Man-in-the-Middle Attacks (MitM): If VPN setting is not safe, the attacker gets the chance to intervene and modify information exchanged between client and server.
- Performance Trade-offs: VPN security often affects internet connection since the encryption and routing through VPN servers cause slower connection. For security and performance are always equally important for the choice of the measures.
Are VPNs legal or illegal?
Using a VPN is legal in most countries, The legality of using a VPN service depends on the country and its geopolitical relations with another country as well. A reliable and secure VPN is always legal if you do not intend to use it for any illegal activities like committing fraud online, cyber theft, or in some countries downloading copyrighted content. China has decided to block all VPNs (Virtual private network) by next year, as per the report of Bloomberg. Many Chinese Internet users use VPNs to privately access websites that are blocked under China’s so-called “great firewall”. This is done to avoid any information leakage to rival countries and to tighten the information security.
What to Look for When Choosing a VPN?
- Be sure the VPN has appropriate speed, a lot of providers have trouble keeping up with Netflix viewing or downloading.
- Read both user and expert evaluations to gain a good idea of how well the VPN operates.
- Select a VPN provider that provides shared IP addresses.
- More servers translate into faster browsing because there will be less traffic on each one.
Benefits of VPN
- When you use VPN it is possible to switch IP.
- The internet connection is safe and encrypted with VPN
- Sharing files is confidential and secure.
- Your privacy is protected when using the internet.
- There is no longer a bandwidth restriction.
- It facilitates cost savings for internet shopping.
Limitations of VPN
- VPN may decrease your internet speed.
- Premium VPNs are not cheap.
- VPN usage may be banned in some nations.]
Conclusion
In conclusion, a VPN (Virtual Private Network) is a powerful tool that enhances your online privacy and security by encrypting your internet connection and masking your IP address. Whether you’re accessing public Wi-Fi, wanting to browse the web more securely, or bypassing geographical restrictions, a VPN offers a layer of protection that keeps your data safe. As the digital landscape continues to evolve, understanding and using a VPN can be an essential step in safeguarding your online presence.
Frequently Asked Question on VPN – FAQs
Can a VPN Be Traced?
While VPNs enhance privacy, it’s not entirely foolproof. In some cases, determined adversaries, such as government agencies, may employ advanced techniques to trace VPN usage. However, for typical online privacy needs, a VPN provides a high level of protection.
Do VPNs Slow Down Internet Speed?
VPNs can introduce some degree of latency due to the encryption and routing processes. The extent of the speed reduction depends on various factors, including the VPN provider’s infrastructure, server location, and your internet connection. In many cases, the impact on speed is minimal, and modern VPN services strive to provide fast connections.
Are There Free VPNs?
Yes, there are free VPN services available. However, they often come with limitations such as data caps, slower speeds, and less robust security features. Paid VPN services generally offer more reliable performance and better security.
Where are VPNs illegal?
Despite being heavily used in major parts of the worlds, VPNs are strictly prohibited in few countries that includes:
- Russia
- China
- Belarus
- North Korea
- Iraq, etc.





















 388
388

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








