Please indicate the source: http://blog.csdn.net/gaoxiangnumber1
Welcome to my github: https://github.com/gaoxiangnumber1
17.1 Introduction
17.2 TCP Services
- TCP provides a connection-oriented, reliable, byte stream service. Connection-oriented means that the two applications using TCP must establish a TCP connection with each other before they can exchange data.
- TCP provides reliability by doing the following:
- The application data is broken into what TCP considers the best sized chunks to send. This is different from UDP where each write by the application generates a UDP datagram of that size. The unit of information passed by TCP to IP is called a segment. Section 18.4.
- When TCP sends a segment it maintains a timer, waiting for the other end to acknowledge reception of the segment. If an acknowledgment isn’t received in time, the segment is retransmitted. Chapter 21.
- When TCP receives data from the other end of the connection, it sends an acknowledgment. This acknowledgment is not sent immediately, but delayed a fraction of a second. Section 19.3.
- TCP maintains a checksum on its header and data. This is an end-to-end checksum whose purpose is to detect any modification of the data in transit. If a segment arrives with an invalid checksum, TCP discards it and doesn’t acknowledge receiving it. It expects the sender to time out and retransmit.
- Since TCP segments are transmitted as IP datagrams, and since IP datagrams can arrive out of order, TCP segments can arrive out of order. A receiving TCP re-sequences the data if necessary, passing the received data in the correct order to the application.
- Since IP datagrams can get duplicated, a receiving TCP must discard duplicate data.
- TCP provides flow control. Each end of a TCP connection has a finite amount of buffer space. A receiving TCP only allows the other end to send as much data as the receiver has buffers for. This prevents a fast host from taking all the buffers on a slower host.
- A stream of 8-bit bytes is exchanged across the TCP connection between the two applications. There are no record markers inserted by TCP, i.e., a byte stream service. One end puts a stream of bytes into TCP and the same, identical stream of bytes appears at the other end.
- TCP does not interpret the contents of the bytes. The interpretation of this byte stream is up to the applications on each end of the connection.
17.3 TCP Header
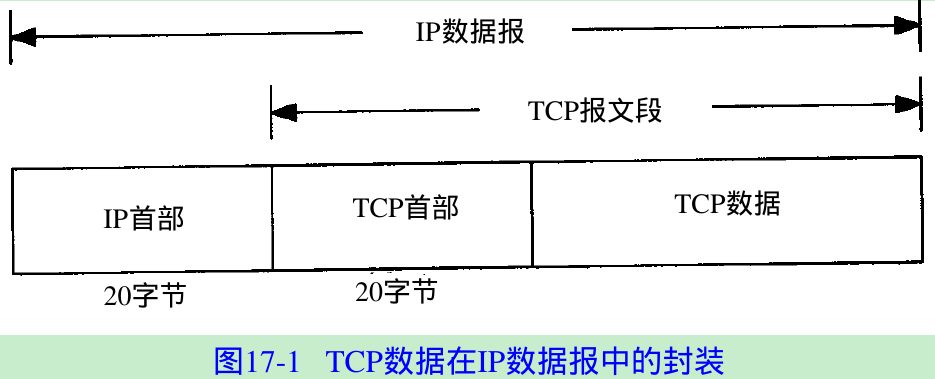
- TCP data is encapsulated in an IP datagram, as shown in Figure 17.1.
- Figure 17.2 shows the format of the TCP header. Its normal size is 20 bytes, unless options are present.
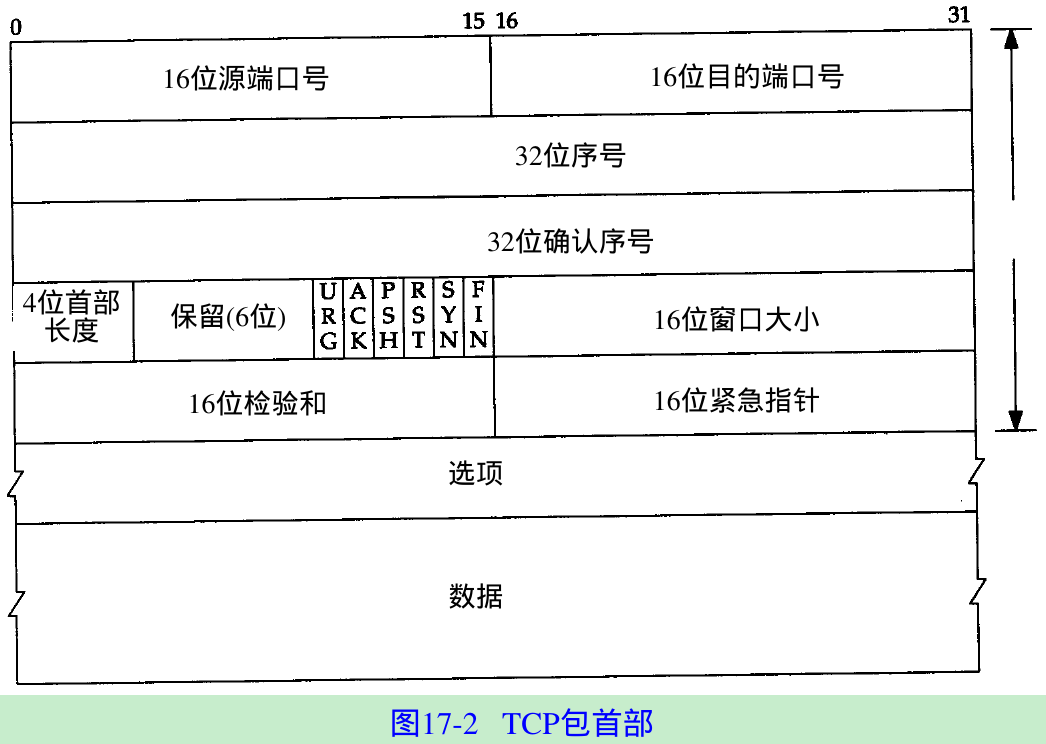
- The combination of an IP address and a port number is called a socket. The socket pair(the 4-tuple consisting of the client IP address, client port number, server IP address, and server port number) specifies the two end points that uniquely identifies each TCP connection in an internet.
- The sequence number identifies the byte in the stream of data from the sending TCP to the receiving TCP that the first byte of data in this segment represents. If we consider the stream of bytes flowing in one direction between two applications, TCP numbers each byte with a sequence number. This sequence number is a 32-bit unsigned number that wraps back around to 0 after reaching 232 - 1.
- When a new connection is being established, the SYN flag is turned on. The sequence number field contains the initial sequence number(ISN) chosen by this host for this connection. The sequence number of the first byte of data sent by this host will be the ISN + 1 because the SYN flag consumes a sequence number.
- The acknowledgment number contains the next sequence number that the sender of the acknowledgment expects to receive. This is the sequence number plus 1 of the last successfully received byte of data. This field is valid only if the ACK flag is on.
- TCP provides a full-duplex service to the application layer that data can be flowing in each direction, independent of the other direction. Therefore, each end of a connection must maintain a sequence number of the data flowing in each direction.
- TCP can be described as a sliding-window protocol without selective or negative acknowledgments.
- TCP lacks selective acknowledgments because the acknowledgment number in the TCP header means that the sender has successfully received up through but not including that byte. There is no way to acknowledge selected pieces of the data stream. For example, if bytes 1-1024 are received OK, and the next segment contains bytes 2049-3072, the receiver cannot acknowledge this new segment. All it can send is an ACK with 1025 as the acknowledgment number.
- There is no means for negatively acknowledging a segment. For example, if the segment with bytes 1025-2048 did arrive, but had a checksum error, all the receiving TCP can send is an ACK with 1025 as the acknowledgment number.
- The header length gives the length of the header in 32-bit words. This is required because the length of the options field is variable. With a 4-bit field, TCP is limited to a 60-byte header. Without options, the normal size is 20 bytes.
- There are six flag bits in the TCP header. One or more of them can be turned on at the same time.
URG The urgent pointer is valid(Section 20.8).
ACK The acknowledgment number is valid.
PSH The receiver should pass this data to the application as soon as possible
(Section 20.5).
RST Reset the connection(Section 18.7).
SYN Synchronize sequence numbers to initiate a connection. This flag and the
next are described in Chapter 18.
FIN The sender is finished sending data. - TCP’s flow control is provided by each end advertising a window size. This is the number of bytes, starting with the one specified by the acknowledgment number field, that the receiver is willing to accept. This is a 16-bit field, limiting the window to 65535 bytes.
- The checksum covers the TCP segment(TCP header and TCP data). This is a mandatory field that must be calculated and stored by the sender and then verified by the receiver. The TCP checksum is calculated using a pseudo-header as described in Section 11.3.
- The urgent pointer is valid only if the URG flag is set. This pointer is a positive offset that must be added to the sequence number field of the segment to yield the sequence number of the last byte of urgent data. TCP’s urgent mode is a way for the sender to transmit emergency data to the other end. Section 20.8.
- The most common option field is the maximum segment size option, called the MSS. Each end of a connection specifies this option on the first segment exchanged(the one with the SYN flag set to establish the connection). It specifies the maximum sized segment that the sender wants to receive. Section 18.4.
- The data portion of the TCP segment is optional. When a connection is established and when a connection is terminated, segments are exchanged that contain only the TCP header with possible options. A header without any data is also used to acknowledge received data, if there is no data to be transmitted in that direction.
17.4 Summary
Exercise 17.1
We’ve covered the following packet formats, each of which has a checksum in its corresponding header: IP, ICMP, IGMP, UDP, and TCP. For each one, describe what portion of an IP datagram the checksum covers and whether the checksum is mandatory or optional.
- All are mandatory except the UDP checksum. The IP checksum covers only the IP header, while the others start immediately after the IP header.
Exercise 17.2
Why do all the Internet protocols that we’ve discussed(IP, ICMP, IGMP, UDP, TCP) quietly discard a packet that arrives with a checksum error?
- The source IP address, source port number, or protocol field might have been corrupted.
Exercise 17.3
TCP provides a byte-stream service where record boundaries are not maintained between the sender and receiver. How can applications provide their own record markers?
- Many Internet applications use a carriage return and linefeed to mark the end of each application record. This is NVT ASCII coding(Section 26.4).
- An alternative technique is to prefix each record with a byte count, which is used by the DNS(Exercise 14.4) and Sun RPC(Section 29.2).
Exercise 17.4
Why are the source and destination port numbers at the beginning of the TCP header?
- Section 6.5: an ICMP error must return at least the first 8 bytes beyond the IP header of the IP datagram that caused the error. When TCP receives an ICMP error it needs to examine the two port numbers to determine which connection the error corresponds to, so the port numbers must be in the first 8 bytes of the TCP header.
Exercise 17.5
Why does the TCP header have a header length field while the UDP header(Figure 11.2) does not?
- There are options at the end of the TCP header, but there are no options in the UDP header.
Please indicate the source: http://blog.csdn.net/gaoxiangnumber1
Welcome to my github: https://github.com/gaoxiangnumber1






















 421
421

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








