SharePoint 2013+ Sqlserver 2014 Kerberos 配置图例。
1,安装数据库,安装方法我就不说了,账户一定要注意。 我下面会有参考实例和账户。
2,建立DNS,如果没有DNS服务器 在本地修改hosts吧。
3,Configure Claims to Windows Token Service Account.(呵呵 中文 是声明为windows令牌服务)
Create an AD account to be used by the Claims to Windows Token Service Account e.g. SP_C2WTS
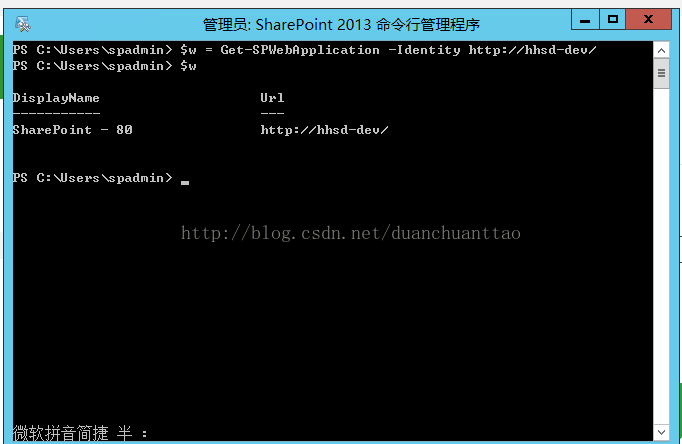
Open a SharePoint PowerShell prompt as Administrator and run the following command:
$w = Get-SPWebApplication -Identity http://bi.blue.com (Put the URL of your web application)
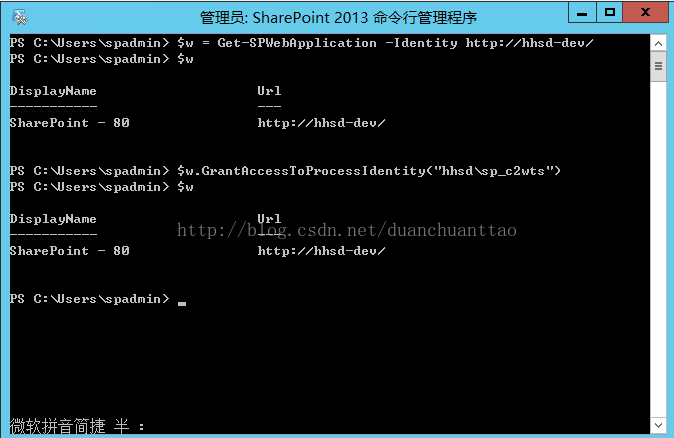
$w.GrantAccessToProcessIdentity("blue\sp_c2wts") (Put your service account name)
2,建立DNS,如果没有DNS服务器 在本地修改hosts吧。
3,Configure Claims to Windows Token Service Account.(呵呵 中文 是声明为windows令牌服务)
Create an AD account to be used by the Claims to Windows Token Service Account e.g. SP_C2WTS
Open a SharePoint PowerShell prompt as Administrator and run the following command:
$w = Get-SPWebApplication -Identity http://bi.blue.com (Put the URL of your web application)
$w.GrantAccessToProcessIdentity("blue\sp_c2wts") (Put your service account name)
验证一下啊
图例告诉我们OK
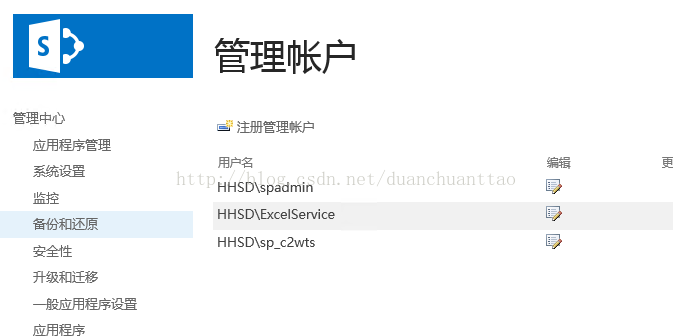
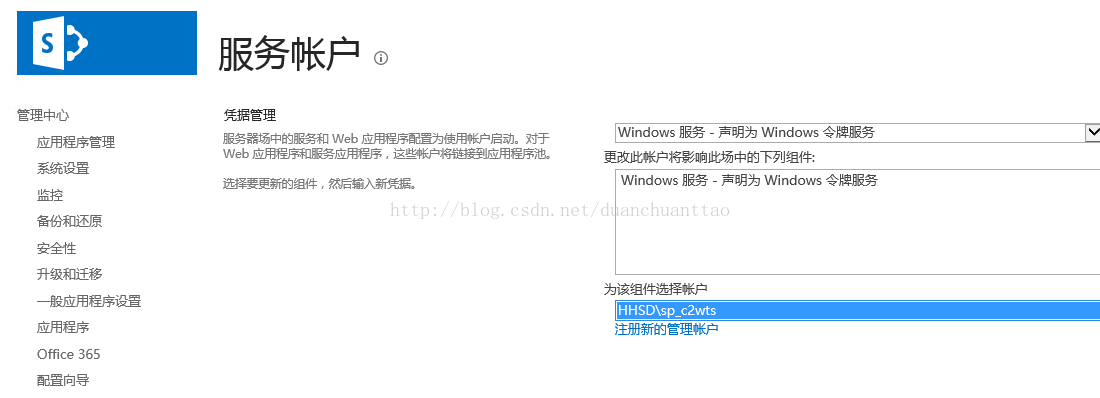
Change the account in the SharePoint UI running the Claims to Windows token Service
- Navigate to Security in Central Admin,
- Click on managed Accounts and add the new C2WTS account as a Managed Account,
- Click Security again and Click on Service Accounts,
- Click the Drop Down and Select Claims to Windows Token Service,
- Select the new Managed Account SP_C2WTS and click OK. (Wait a few minutes for it to complete)
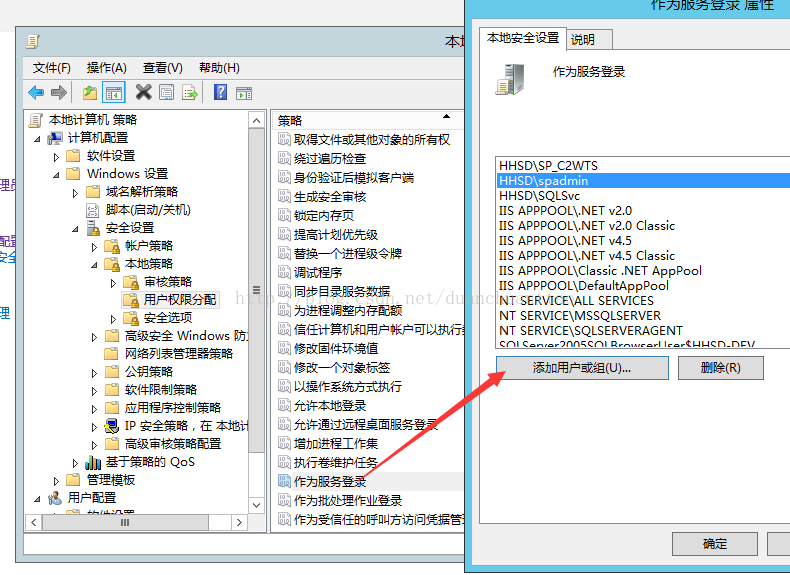
- Set the following permissions on all SharePoint servers in the farm (All must be done) – this is completed under Local Security Policy on each server
下一步是到SPfarm 服务器上配置,
- Grant Log on as a service (this should have happened automatically)
- Impersonate a User (this should have happened automatically)
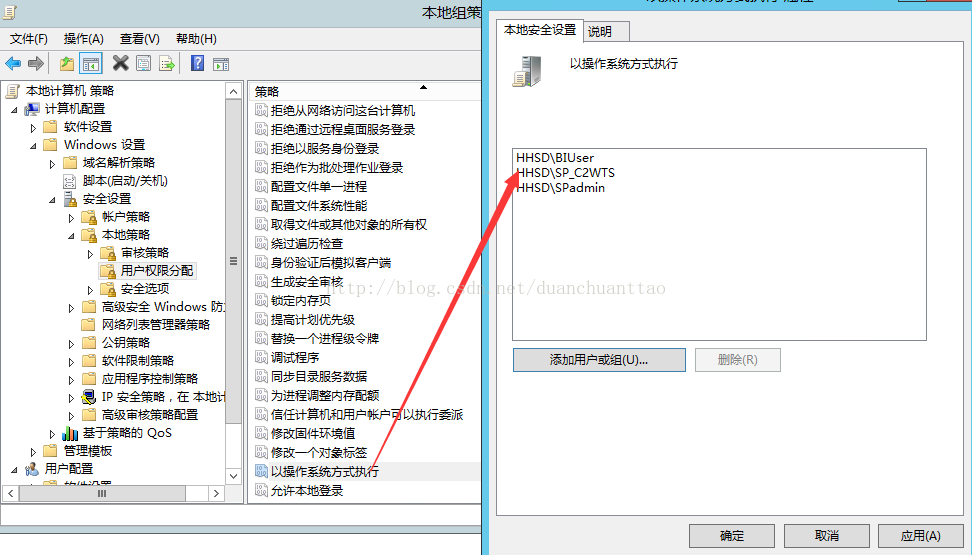
- Act as part of the operating system (If its greyed out then your domain admin will need to update the group policy to allow it)
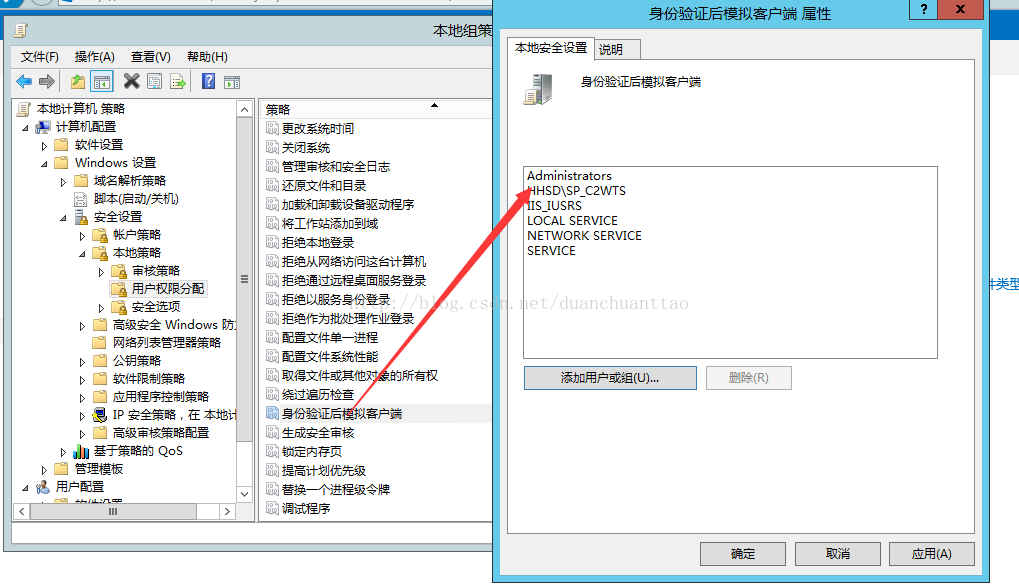
既然配置到这里了 把其他几个也配置了吧。 如图 单击身份验证后模拟客户端--添加用户或组 把kerberos 账号加进去。
以操作系统方式运行,添加kerberos 账号。
- Local admin on all SharePoint servers
- STOP and START the Claims to Windows Token Service (From SharePoint UI) on all servers in the Farm. Simply navigate to Services in Farm and select each server from the link in the top right corner and Stop and Start each one individually waiting for them to finish
也可以完全按照步骤来做。如下;
Grant permission for the account running the application pool for the Service Application
e.g. Excel Services Service Application, Reporting Services Service Application, etc.
- For Analysis services this User must be Granted SQL Analysis Services Administrator access (Unfortunately this is required as Read permission is insufficient for the delegation of credentials)
- Check which account is being used by navigating to Central Admin Security and then select Service Accounts and from the drop down list validate each service or application pool.
- In my example I have an account SP_Services and that account is granted Admin permissions on Analysis Services and granted “SP_DataAccess” on SQL to the SharePoint web application content database(s).
- Validate that the account has the following permissions on each SharePoint server
(This should be completed automatically but should be validated under the Local Security Policy)- Grant Log on as a service
- Impersonate a User
- Grant process identity access to the Service account








 本文档详细介绍了SharePoint 2013和Sqlserver 2014环境中Kerberos身份验证的配置步骤,包括在SharePoint UI中更改Claims to Windows Token Service的账户、设置服务器权限、配置SQL Server Analysis Services的SPN,以及设置受约束的委派等关键操作。通过遵循这些步骤,可以确保Kerberos配置正确并适用于BI解决方案。
本文档详细介绍了SharePoint 2013和Sqlserver 2014环境中Kerberos身份验证的配置步骤,包括在SharePoint UI中更改Claims to Windows Token Service的账户、设置服务器权限、配置SQL Server Analysis Services的SPN,以及设置受约束的委派等关键操作。通过遵循这些步骤,可以确保Kerberos配置正确并适用于BI解决方案。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章















 1503
1503

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








