
3.IP规划
为了不断壮大集团业务经营范围,集团计划在上海成立办事处。通过调研,计
划在上海办事处设立与Internet连接的4个业务部门,每个业务部门的最大所需主
机数如下表所示,要求从10.1.10.100/19主机地址所在网络第一个网段开始进行
IP地址规划,IP地址按照下表依次往后顺延规划,网关地址取每个网段最后一个可
用地址,请完成下表IP地址规划。

营销 网络地址 10.1.10.0/25 网关地址 10.1.10.126
产品 网络地址 10.1.10.128/22 网关地址 10.1.13.254
法务 网络地址 10.1.14.0/25 网关地址 10.1.14.126
财务 网络地址 10.1.14.128/28 网关地址 10.1.14.142
二、交换配置
1.配置vlan,SW1、SW2、SW3、AC1的二层链路只允许相应vlan通过。

2-4.SW1和SW2之间利用三条双绞线实现互通,其中一条双绞线承载三层IP业务、一条双绞线承载VPN业务、一条双绞线承载二层业务。用相关技术分别实现财务1段、财务2段业务路由表与其它业务路由表隔离,财务业务VPN实例名称为Finance。承载二层业务的只有一条双绞线通道,配置相关技术,方便后续链路扩容与冗余备份,编号为1,用LACP协议,SW1为active,SW2为passive;采用源、目的IP进行实现流量负载分担。SW3针对每个业务VLAN的第一个接口配置Loopback命令,模拟接口UP,方便后续业务验证与测试。将SW3模拟为Internet交换机,实现与集团其它业务路由表隔离,Internet路由表VPN实例名称为Internet。将SW3模拟办事处交换机,实现与集团其它业务路由表隔离,办事处路由表VPN实例名称为Office。
SW1:
port-group 1
!
vlan 1;11-15;2019-2020;2022-2023
!
load-balance dst-src-ip
!
Interface Ethernet1/0/1
switchport access vlan 11
!
Interface Ethernet1/0/2
switchport access vlan 12
!
Interface Ethernet1/0/3
switchport access vlan 13
!
Interface Ethernet1/0/4
switchport access vlan 14
!
Interface Ethernet1/0/5
switchport access vlan 15
!
Interface Ethernet1/0/6
!
Interface Ethernet1/0/7
!
Interface Ethernet1/0/8
!
Interface Ethernet1/0/9
!
Interface Ethernet1/0/10
!
Interface Ethernet1/0/11
!
Interface Ethernet1/0/12
!
Interface Ethernet1/0/13
!
Interface Ethernet1/0/14
!
Interface Ethernet1/0/15
!
Interface Ethernet1/0/16
!
Interface Ethernet1/0/17
!
Interface Ethernet1/0/18
!
Interface Ethernet1/0/19
switchport access vlan 2019
!
Interface Ethernet1/0/20
switchport access vlan 2020
!
Interface Ethernet1/0/21
!
Interface Ethernet1/0/22
switchport access vlan 2022
!
Interface Ethernet1/0/23
switchport access vlan 2023
!
Interface Ethernet1/0/24
switchport mode trunk
switchport trunk allowed vlan 11-15;3000
//这里vlan3000是因为后面端口镜像要用到
port-group 1 mode active
!
Interface Ethernet1/0/25
!
Interface Ethernet1/0/26
!
Interface Ethernet1/0/27
!
Interface Ethernet1/0/28
!
Interface Port-Channel1
!
ip vrf Finance
!
interface Vlan11
ipv6 address 2001:10:1:11::1/64
ip address 10.1.11.1 255.255.255.0
!
interface Vlan12
ipv6 address 2001:10:1:12::1/64
ip address 10.1.12.1 255.255.255.0
!
interface Vlan13
ipv6 address 2001:10:1:13::1/64
ip address 10.1.13.1 255.255.255.0
!
interface Vlan14
ip vrf forwarding Finance
ipv6 address 2001:10:1:14::1/64
ip address 10.1.14.1 255.255.255.0
!
interface Vlan15
ipv6 address 2001:10:1:15::1/64
ip address 10.1.15.1 255.255.255.0
!
interface Vlan2019
ip address 10.1.255.14 255.255.255.252
!
interface Vlan2020
ip address 10.1.255.5 255.255.255.252
!
interface Vlan2022
ip address 10.1.255.1 255.255.255.252
!
interface Vlan2023
ip vrf forwarding Finance
ip address 10.1.255.1 255.255.255.252
!
interface Loopback1
ipv6 address 2001:10:1:1::1/128
ip address 10.1.1.1 255.255.255.255
!
interface Loopback2
ipv6 address 2001:10:1:1::2/128
ip address 10.1.1.2 255.255.255.255
!
SW2:
port-group 1
!
vlan 1;21-25;2019-2020;2022-2023
!
load-balance dst-src-ip
!
Interface Ethernet1/0/1
switchport access vlan 21
!
Interface Ethernet1/0/2
switchport access vlan 22
!
Interface Ethernet1/0/3
switchport access vlan 23
!
Interface Ethernet1/0/4
switchport access vlan 24
!
Interface Ethernet1/0/5
switchport access vlan 25
!
Interface Ethernet1/0/6
!
Interface Ethernet1/0/7
!
Interface Ethernet1/0/8
!
Interface Ethernet1/0/9
!
Interface Ethernet1/0/10
!
Interface Ethernet1/0/11
!
Interface Ethernet1/0/12
!
Interface Ethernet1/0/13
!
Interface Ethernet1/0/14
!
Interface Ethernet1/0/15
!
Interface Ethernet1/0/16
!
Interface Ethernet1/0/17
!
Interface Ethernet1/0/18
!
Interface Ethernet1/0/19
switchport access vlan 2019
!
Interface Ethernet1/0/20
switchport access vlan 2020
!
Interface Ethernet1/0/21
!
Interface Ethernet1/0/22
switchport access vlan 2022
!
Interface Ethernet1/0/23
switchport access vlan 2023
!
Interface Ethernet1/0/24
switchport mode trunk
switchport trunk allowed vlan 21-25;3000
port-group 1 mode passive
!
Interface Ethernet1/0/25
!
Interface Ethernet1/0/26
!
Interface Ethernet1/0/27
!
Interface Ethernet1/0/28
!
Interface Port-Channel1
!
ip vrf Finance
!
interface Vlan21
ipv6 address 2001:10:1:21::1/64
ip address 10.1.21.1 255.255.255.0
!
interface Vlan22
ipv6 address 2001:10:1:22::1/64
ip address 10.1.22.1 255.255.255.0
!
interface Vlan23
ipv6 address 2001:10:1:23::1/64
ip address 10.1.23.1 255.255.255.0
!
interface Vlan24
ip vrf forwarding Finance
ipv6 address 2001:10:1:24::1/64
ip address 10.1.24.1 255.255.255.0
!
interface Vlan25
ipv6 address 2001:10:1:25::1/64
ip address 10.1.25.1 255.255.255.0
!
interface Vlan2019
ip address 10.1.255.22 255.255.255.252
!
interface Vlan2020
ip address 10.1.255.9 255.255.255.252
!
interface Vlan2022
ip address 10.1.255.2 255.255.255.252
!
interface Vlan2023
ip vrf forwarding Finance
ip address 10.1.255.2 255.255.255.252
!
interface Loopback1
ipv6 address 2001:10:1:2::1/128
ip address 10.1.2.1 255.255.255.255
!
interface Loopback2
ipv6 address 2001:10:1:2::2/128
ip address 10.1.2.2 255.255.255.255
!
SW3:
vlan 1;31-33;35;110;120;1015;2017-2020
!
Interface Ethernet1/0/1
loopback
switchport access vlan 31
!
Interface Ethernet1/0/2
loopback
switchport access vlan 32
!
Interface Ethernet1/0/3
loopback
switchport access vlan 33
!
Interface Ethernet1/0/4
!
Interface Ethernet1/0/5
loopback
switchport access vlan 35
!
Interface Ethernet1/0/6
!
Interface Ethernet1/0/7
!
Interface Ethernet1/0/8
!
Interface Ethernet1/0/9
!
Interface Ethernet1/0/10
!
Interface Ethernet1/0/11
!
Interface Ethernet1/0/12
!
Interface Ethernet1/0/13
!
Interface Ethernet1/0/14
!
Interface Ethernet1/0/15
switchport access vlan 1015
!
Interface Ethernet1/0/16
!
Interface Ethernet1/0/17
switchport access vlan 2017
!
Interface Ethernet1/0/18
switchport access vlan 2018
!
Interface Ethernet1/0/19
switchport access vlan 2019
!
Interface Ethernet1/0/20
switchport access vlan 2020
!
Interface Ethernet1/0/21
!
Interface Ethernet1/0/22
!
Interface Ethernet1/0/23
!
Interface Ethernet1/0/24
switchport mode trunk
switchport trunk allowed vlan 31-35;110;120
!
Interface Ethernet1/0/25
!
Interface Ethernet1/0/26
!
Interface Ethernet1/0/27
!
Interface Ethernet1/0/28
!
ip vrf Office
!
ip vrf Internet
!
interface Vlan31
ipv6 address 2001:10:1:31::1/64
ip address 10.1.31.1 255.255.255.0
!
interface Vlan32
ipv6 address 2001:10:1:32::1/64
ip address 10.1.32.1 255.255.255.0
!
interface Vlan33
ipv6 address 2001:10:1:33::1/64
ip address 10.1.33.1 255.255.255.0
!
interface Vlan35
ipv6 address 2001:10:1:35::1/64
ip address 10.1.35.1 255.255.255.0
!
interface Vlan110
ip vrf forwarding Office
ipv6 address 2001:10:1:110::1/64
ip address 10.1.110.1 255.255.255.0
!
interface Vlan120
ip vrf forwarding Office
ipv6 address 2001:10:1:120::1/64
ip address 10.1.120.1 255.255.255.0
!
interface Vlan1015
ip vrf forwarding Office
ip address 10.1.255.46 255.255.255.252
!
interface Vlan2017
ip vrf forwarding Internet
ip address 200.200.200.1 255.255.255.252
!
interface Vlan2018
ip vrf forwarding Internet
ip address 200.200.200.5 255.255.255.252
!
interface Vlan2019
ip address 10.1.255.6 255.255.255.252
!
interface Vlan2020
ip address 10.1.255.10 255.255.255.252
!
interface Loopback1
ipv6 address 2001:10:1:3::1/128
ip address 10.1.3.1 255.255.255.255
!
interface Loopback2
ip vrf forwarding Office
ipv6 address 2001:10:1:3::2/128
ip address 10.1.3.2 255.255.255.255
!
interface Loopback3
ip vrf forwarding Internet
ipv6 address 2001:200:200:3::3/128
ip address 200.200.3.3 255.255.255.255
!
!
no login
!
captive-portal
!
end
AC1:
vlan 1;130;140;150;2001
!
Interface Ethernet1/0/1
switchport access vlan 2001
!
Interface Ethernet1/0/2
switchport mode trunk
switchport trunk allowed vlan 140;150
switchport trunk native vlan 130
!
Interface Ethernet1/0/3
!
Interface Ethernet1/0/4
!
Interface Ethernet1/0/5
!
Interface Ethernet1/0/6
!
Interface Ethernet1/0/7
!
Interface Ethernet1/0/8
!
Interface Ethernet1/0/9
!
Interface Ethernet1/0/10
!
Interface Ethernet1/0/11
!
Interface Ethernet1/0/12
!
Interface Ethernet1/0/13
!
Interface Ethernet1/0/14
!
Interface Ethernet1/0/15
!
Interface Ethernet1/0/16
!
Interface Ethernet1/0/17
!
Interface Ethernet1/0/18
!
Interface Ethernet1/0/19
!
Interface Ethernet1/0/20
!
Interface Ethernet1/0/21
!
Interface Ethernet1/0/22
!
Interface Ethernet1/0/23
!
Interface Ethernet1/0/24
!
Interface Ethernet1/0/25
!
Interface Ethernet1/0/26
!
Interface Ethernet1/0/27
!
Interface Ethernet1/0/28
!
interface Vlan130
ipv6 address 2001:10:1:130::1/64
ip address 10.1.130.1 255.255.255.0
!
interface Vlan140
ipv6 address 2001:10:1:140::1/64
ip address 10.1.140.1 255.255.255.0
!
interface Vlan150
ipv6 address 2001:10:1:150::1/64
ip address 10.1.150.1 255.255.255.0
!
interface Vlan2001
ip address 10.1.255.42 255.255.255.252
!
interface Loopback1
ipv6 address 2001:10:1:4::1/128
ip address 10.1.4.1 255.255.255.255
!
interface Loopback2
ipv6 address 2001:10:1:4::2/128
ip address 10.1.4.2 255.255.255.255
!
interface Loopback3
ipv6 address 2001:10:1:4::3/128
ip address 10.1.4.3 255.255.255.255
!5.勒索蠕虫病毒席卷全球,爆发了堪称史上最大规模的网络攻击,通过对总部核心交换机SW1和SW2所有业务VLAN下配置访问控制策略实现双向安全防护。
SW1:
注:135-138;139;445等都是常用勒索病毒端口号
ip access-list extended fh
deny tcp any-source any-destination d-port 135
deny tcp any-source any-destination d-port 137
deny tcp any-source any-destination d-port 138
deny tcp any-source any-destination d-port 139
deny tcp any-source any-destination d-port 445
exit
!
ipv6 access-list extended fh6
deny tcp any-source any-destination d-port 135
deny tcp any-source any-destination d-port 137
deny tcp any-source any-destination d-port 138
deny tcp any-source any-destination d-port 139
deny tcp any-source any-destination d-port 445
exit
!
vacl ip access-group fh in vlan 11-15
vacl ip access-group fh out vlan 11-15
vacl ipv6 access-group fh6 in vlan 11-15
vacl ipv6 access-group fh6 out vlan 11-15
SW2:
ip access-list extended fh
deny tcp any-source any-destination d-port 135
deny tcp any-source any-destination d-port 137
deny tcp any-source any-destination d-port 138
deny tcp any-source any-destination d-port 139
deny tcp any-source any-destination d-port 445
exit
!
ipv6 access-list extended fh6
deny tcp any-source any-destination d-port 135
deny tcp any-source any-destination d-port 137
deny tcp any-source any-destination d-port 138
deny tcp any-source any-destination d-port 139
deny tcp any-source any-destination d-port 445
exit
!
vacl ip access-group fh in vlan 21-25
vacl ip access-group fh out vlan 21-25
vacl ipv6 access-group fh6 in vlan 21-25
vacl ipv6 access-group fh6 out vlan 21-256.总部预采购多个厂商网流分析平台对集团整体流量进行监控、审计,连接在
SW1的E1/0/10-E1/0/13接 口 测 试 ,VLAN3000作 为 远 程 端 口 镜 像VLAN,
Ethernet10/14作为反射端口,将核心交换机与灾备交换机、路由器互连流量提供给多个厂商网流分析平台。
SW1:
vlan 3000
remote-span
!
Interface Ethernet1/0/10-13
switchport access vlan 3000
!
Interface Ethernet1/0/24
switchport mode trunk
switchport trunk allowed vlan 11-15;3000
port-group 1 mode active
!
monitor session 1 remote vlan 3000
Sw2:
vlan 3000
remote-span
!
Interface Ethernet1/0/14
switchport access vlan 3000
!
Interface Ethernet1/0/24
switchport mode trunk
switchport trunk allowed vlan 21-25;3000
port-group 1 mode passive
!
monitor session 1 source interface Ethernet1/0/19-20 tx
monitor session 1 source interface Ethernet1/0/19-20 rx
monitor session 1 reflector-port interface Ethernet1/0/14
monitor session 1 remote vlan 3000
!7.营销1段的组长因业务需求,其笔记本电脑的mac地址为01-01-01-01-01-01经常在办公室移动有线办公,为解决营销组的移动有线办公问题,现要求经过设置,当该设备接入到SW2的E1/0/17-18时,会自动收到来自营销1段的数据包。
SW2:
vlan 11
!
Interface Ethernet1/0/17
switchport access vlan 11
!
Interface Ethernet1/0/18
switchport access vlan 11
!
mac-address-table static-multicast address 01-01-01-01-01-01 vlan 11 interface Ethernet1/0/17
mac-address-table static-multicast address 01-01-01-01-01-01 vlan 11 interface Ethernet1/0/188.SW1和SW2所有端口启用链路层发现协议,更新报文发送时间间隔为20s,老化时间乘法器值为5,Trap报文发送间隔为10s,配置三条双绞线端口使能Trap功能。
SW1-SW2:
lldp enable
lldp msgTxHold 5
lldp tx-interval 20
lldp notification interval 10
Interface Ethernet1/0/1-28
lldp enable
!
Interface Ethernet1/0/22-24
lldp trap enable
!9.对SW1上VLAN40开启以下安全机制:业务内部终端相互二层隔离,启用环路检测,环路检测的时间间隔为10s,发现环路以后关闭该端口,恢复时间为30分钟;配置防止ARP欺骗攻击。
SW1:
这里应该是vlan14,题目弄错了应该
ip dhcp snooping enable
ip dhcp snooping binding enable
ip dhcp snooping binding arp
loopback-detection interval-time 10 10
!
loopback-detection control-recovery timeout 1800
!
isolate-port apply l
isolate-port group 1 switchport interface ethernet 1/0/4
vlan 14
arp-guard ip 10.1.14.1
isolate-port group 1 switchport interface ethernet 1/0/4
!
Interface Ethernet1/0/4
switchport access vlan 14
loopback-detection specified-vlan 14
arp-guard ip 10.1.14.1
!
10.集团SW1使用相关技术配置产品业务VLAN每个物理端口最多允许每秒钟通过640kbit的广播数据包;营销业务VLAN每个物理端口最多允许每秒钟通过1280kbit的单播数据包。
SW1:
Interface Ethernet1/0/1
storm-control broadcast 640
switchport access vlan 11
!
Interface Ethernet1/0/2
storm-control unicast 1280
switchport access vlan 12
!三、路由调试
1.在路由器R1上通过SSH服务管理设备,,仅允许账号为skills01密码为skills01;密码全部设置为明文,允许用户最多6次验证,最多同时运行2台设备登录,验证超时为120秒,RT2配置使用telnet方式登录终端界面前显示如下授权信息:"WARNING!!! Authorised access only, all of your donewill be recorded! Disconnected IMMEDIATELY if you arenot an authorised user! Otherwise, we retain the rightto pursue the legal responsibility"。
SW1:
username skills01 password 0 skills
ip sshd enable
ip sshd auth-method password
ip sshd timeout 540
ip sshd max-user 2
ip sshd enable
SW2:
banner message
text WARNING!!! Authorised access only, all of your donewill be recorded! Disconnected IMMEDIATELY if you arenot an authorised user! Otherwise, we retain the rightto pursue the legal responsibility
!2.在SW1配置法务1段报文带宽限制为10M比特/秒,突发值设为4M字节,超过带宽的该网段内的报文一律丢弃。
SW1:
ip access-list standard cl
permit any-source
exit
!
class-map cl
match access-group cl
!
policy-map cl
class cl
policy 10000 4000 exceed-action drop
exit
!
Interface Ethernet1/0/3
service-policy input cl
service-policy output cl
switchport access vlan 13
!
3.配置接口ipv4地址和ipv6地址,互联接口ipv6地址用本地链路地址。
根据ip地址表配置,很基础这里不过多阐述了
4.SW2配置DHCPv4和DHCPv6,分别为总公司产品1段、总公司产品2段、分公
司Vlan130、分公司Vlan140和分公司Vlan150分配地址。IPv4地址池名称分别为Poolv4-Vlan11、Poolv4-Vlan21、Poolv4-Vlan130、Poolv4-Vlan140、Poolv4-Vlan150,排除网关,DNS为10.1.210.101和10.1.220.101。IPv6地址池名称分别为Poolv6-Vlan11、Poolv6-Vlan21、Poolv6-Vlan130、Poolv6-Vlan140、Poolv6-Vlan150,IPv6地址池用网络前缀表示,排除网关,DNS为2400:3200::1。PC1保 留 地 址10.1.21.9和2001:10:1:21::9,PC2保 留 地 址10.1.31.9和2001:10:1:31::9,AP1保留地址10.1.130.9和2001:10:1:130::9。开启路由公告功能,路由器公告的生存期为2小时,确保IPv6终端可以获得IPv6无状态地址;SW1、AC1中继地址为SW2Loopback1地址,SW1启用DHCPv4和DHCPv6 snooping,如果E1/0/1连接dhcpv4服务器,则关闭该端口,恢复时间为10分钟。
SW2:
service dhcp
!
ip dhcp excluded-address 10.1.11.1
ip dhcp excluded-address 10.1.21.1
ip dhcp excluded-address 10.1.130.1
ip dhcp excluded-address 10.1.140.1
ip dhcp excluded-address 10.1.150.1
!
ip dhcp pool poolv4-vlan11
network-address 10.1.11.0 255.255.255.0
default-router 10.1.11.1
dns-server 10.1.210.101 10.1.220.101
!
ip dhcp pool poolv4-vlan21
network-address 10.1.21.0 255.255.255.0
default-router 10.1.21.1
dns-server 10.1.210.101 10.1.220.101
!
ip dhcp pool poolv4-vlan130
network-address 10.1.130.0 255.255.255.0
default-router 10.1.130.1
dns-server 10.1.210.101 10.1.220.101
!
ip dhcp pool poolv4-vlan140
network-address 10.1.140.0 255.255.255.0
default-router 10.1.140.1
dns-server 10.1.210.101 10.1.220.101
!
ip dhcp pool poolv4-vlan150
network-address 10.1.150.0 255.255.255.0
default-router 10.1.150.1
dns-server 10.1.210.101 10.1.220.101
!
ip dhcp pool AP1
host 10.1.130.9 255.255.255.0
hardware-address 00-03-0F-EA-5B-C0
!
ip dhcp pool PC1
host 10.1.11.9 255.255.255.0
hardware-address 64-5D-86-C6-6D-D5
!
ip dhcp pool PC2
host 10.1.21.9 255.255.255.0
hardware-address 8C-EC-4B-9B-16-FD
!
!
!
!
!
service dhcpv6
!
ipv6 dhcp pool poolv6-vlan150
network-address 2001:10:1:150::1 64
excluded-address 2001:10:1:150::1
dns-server 2400:3200::1
!
ipv6 dhcp pool poolv6-vlan140
network-address 2001:10:1:140::1 64
excluded-address 2001:10:1:140::1
dns-server 2400:3200::1
!
ipv6 dhcp pool poolv6-vlan130
network-address 2001:10:1:130::1 64
static-binding 2001:10:1:130::9 00-03-0f-ea-5b-c0
excluded-address 2001:10:1:130::1
dns-server 2400:3200::1
!
ipv6 dhcp pool poolv6-vlan21
network-address 2001:10:1:21::1 64
static-binding 2001:10:1:21::9 8c-ec-4b-9b-16-fd
excluded-address 2001:10:1:21::1
dns-server 2400:3200::1
!
ipv6 dhcp pool poolv6-vlan11
network-address 2001:10:1:11::1 64
static-binding 2001:10:1:11::9 64-5d-86-c6-6d-d5
excluded-address 2001:10:1:11::1
dns-server 2400:3200::1
!
SW1:
service dhcp
service dhcpv6
ip forward-protocol udp bootps
ip dhcp snooping enable
ip dhcp snooping binding enable
savi enable
savi ipv6 dhcp-only enable
interface Vlan11
no ipv6 nd suppress-ra
ipv6 nd managed-config-flag
ipv6 nd other-config-flag
ip helper-address 10.1.2.1
ipv6 dhcp relay destination 2001:10:1:2::1
!
AC1:
service dhcp
service dhcpv6
ip forward-protocol udp bootps
interface Vlan130
no ipv6 nd suppress-ra
ipv6 nd managed-config-flag
ipv6 nd other-config-flag
ip helper-address 10.1.2.1
ipv6 dhcp relay destination 2001:10:1:2::1
!
interface Vlan140
no ipv6 nd suppress-ra
ipv6 nd managed-config-flag
ipv6 nd other-config-flag
ip helper-address 10.1.2.1
ipv6 dhcp relay destination 2001:10:1:2::1
!
interface Vlan150
no ipv6 nd suppress-ra
ipv6 nd managed-config-flag
ipv6 nd other-config-flag
ip helper-address 10.1.2.1
ipv6 dhcp relay destination 2001:10:1:2::1
!
5.SW1、SW2、SW3、RT1以太链路、RT2以太链路、FW1、FW2、AC1之间运行OSPFv2和OSPFv3协议(路由模式发布网络用接口地址,BGP协议除外)。
(1)SW1、SW2、SW3、FW1之间OSPFv2进程1,区域0,RT1和RT2之间OSPFv2进程1,区域1,SW1、SW2、SW3、RT1、RT2、FW 1之间OSP Fv3协议,进程1,区域0; 分别发布loopback1地址路由和产品路由,FW1通告type1默认路由。
SW1:
router ospf 1
ospf router-id 10.1.1.1
network 10.1.1.1/32 area 0
network 10.1.11.0/24 area 0
network 10.1.255.0/30 area 0
network 10.1.255.4/30 area 0
network 10.1.255.12/30 area 0
!
router ipv6 ospf 1
router-id 10.1.1.1
!
nterface Loopback1
ipv6 router ospf area 0 tag 1
!
interface Vlan11
ipv6 router ospf area 0 tag 1
!
interface Vlan2019
ipv6 router ospf area 0 tag 1
ip address 10.1.255.14 255.255.255.252
!
interface Vlan2020
ipv6 router ospf area 0 tag 1
ip address 10.1.255.5 255.255.255.252
!
interface Vlan2022
ipv6 router ospf area 0 tag 1
ip address 10.1.255.1 255.255.255.252
!
SW2:
router ospf 1
ospf router-id 10.1.2.1
network 10.1.2.1/32 area 0
network 10.1.21.1/24 area 0
network 10.1.255.22/30 area 0
network 10.1.255.9/30 area 0
network 10.1.255.2/30 area 0
!
router ipv6 ospf 1
router-id 10.1.2.1
!
interface Loopback1
ipv6 router ospf area 0 tag 1
!
interface Vlan21
ipv6 router ospf area 0 tag 1
!
interface Vlan2019
ipv6 router ospf area 0 tag 1
!
interface Vlan2020
ipv6 router ospf area 0 tag 1
!
interface Vlan2022
ipv6 router ospf area 0 tag 1
!
SW3:
router ospf 1
ospf router-id 10.1.3.1
network 10.1.3.1/32 area 0
network 10.1.31.0/24 area 0
network 10.1.255.4/30 area 0
network 10.1.255.8/30 area 0
!
router ipv6 ospf 1
router-id 10.1.3.1
!
interface Loopback1
ipv6 router ospf area 0 tag 1
!
interface Vlan31
ipv6 router ospf area 0 tag 1
!
interface Vlan2019
ipv6 router ospf area 0 tag 1
!
interface Vlan2020
ipv6 router ospf area 0 tag 1
!
RT1:
router ospf 1
router-id 10.1.5.1
network 10.1.5.1 255.255.255.255 area 1
network 10.1.255.28 255.255.255.252 area 1
network 10.1.255.20 255.255.255.252 area 0
network 10.1.255.16 255.255.255.252 area 0
area 1 virtual-link 10.1.6.1
//这里做虚链接是因为让后面ac获取到ospfv4的路由
!
router ospfv3 1
router-id 10.1.5.1
!
interface GigaEthernet0/0
ip address 10.1.255.29 255.255.255.252
ipv6 enable
ipv6 ospf 1 area 0
!
interface GigaEthernet0/1
ip address 10.1.255.21 255.255.255.252
ipv6 enable
ipv6 ospf 1 area 0
!
interface GigaEthernet0/2
ip address 10.1.255.18 255.255.255.252
ipv6 enable
ipv6 ospf 1 area 0
!
interface Loopback1
ip address 10.1.5.1 255.255.255.255
ipv6 enable
ipv6 address 2001:10:1:5::1/128
ipv6 ospf 1 area 0
!
RT2:
router ospf 1
router-id 10.1.6.1
network 10.1.6.1 255.255.255.255 area 1
network 10.1.255.28 255.255.255.252 area 1
area 1 virtual-link 10.1.5.1
!
router ospfv3 1
router-id 10.1.6.1
!
interface GigaEthernet0/0
ip address 10.1.255.30 255.255.255.252
ipv6 enable
ipv6 ospf 1 area 0
!
interface Loopback1
ip address 10.1.6.1 255.255.255.255
ipv6 enable
ipv6 address 2001:10:1:6::1/128
ipv6 ospf 1 area 0
!
FW1:
router ospf 1
router-id 10.1.7.1
default-information originate type 1
network 10.1.7.1/32 area 0
network 10.1.255.12/30 area 0
network 10.1.255.16/30 area 0
exit
ipv6 router ospf 1
router-id 10.1.7.1
default-information originate type 1
exit
interface loopback1
zone "trust"
ip address 10.1.7.1 255.255.255.255
ipv6 enable
ipv6 address 2001:10:1:7::1/128
manage ping
manage ssh
ipv6 ospf 1 area 0
nterface ethernet0/1
zone "trust"
ip address 10.1.255.13 255.255.255.252
ipv6 enable
manage ping
manage ssh
ipv6 ospf 1 area 0
exit
interface ethernet0/2
zone "trust"
ip address 10.1.255.17 255.255.255.252
ipv6 enable
manage ping
manage ssh
ipv6 ospf 1 area 0
(2-3)RT2与AC1之间运行OSPFv2协议,进程1,区域2;AC1发布loopback1地址路由、产品和营销路由。RT2与AC1之间运行OSPFv3协议,进程1,stub no-summary区域1;AC1发布loopback1地址路由、产品和营销。
RT2:
router ospf 1
router-id 10.1.6.1
network 10.1.6.1 255.255.255.255 area 1
network 10.1.255.28 255.255.255.252 area 1
network 10.1.255.40 255.255.255.252 area 2
area 1 virtual-link 10.1.5.1
default-information originate always
//这里做默认路由是为后面ac访问外网做准备
!
router ospfv3 1
router-id 10.1.6.1
area 1 stub no-summary
!
interface GigaEthernet0/1
ip address 10.1.255.41 255.255.255.252
ipv6 enable
ipv6 ospf 1 area 1
!
AC1:
router ospf 1
ospf router-id 10.1.4.1
network 10.1.4.1/32 area 2
network 10.1.130.0/24 area 2
network 10.1.140.0/24 area 2
network 10.1.150.0/24 area 2
network 10.1.255.40/30 area 2
!
router ipv6 ospf 1
router-id 10.1.4.1
area 1 stub no-summary
!
interface Loopback1
ipv6 router ospf area 1 tag 1
!
interface Vlan130
ipv6 router ospf area 1 tag 1
!
interface Vlan140
ipv6 router ospf area 1 tag 1
!
interface Vlan150
ipv6 router ospf area 1 tag 1
!
interface Vlan2001
ipv6 router ospf area 1 tag 1
!
(4-5)SW3模拟办事处产品和营销接口配置为loopback,模拟接口up。SW3模拟办事处与FW2之间运行OSPFv2协议,进程2,区域2,SW3模拟办事处发布loopback2、产品和营销。SW3模拟办事处配置ipv6默认路由;FW2分别配置到SW3模拟办事处loopback2、产品和营销的ipv6明细静态路由,FW2重发布静态路由到OSPFv3协议。RT1、FW2之间OSPFv2协议,进程2,区域2;RT1发布loopback4路由,向该区域通告type1默认路由;FW2发布loopback1路由,FW2禁止学习到集团和分公司的所有路由。RT1用prefix-list匹配FW2 loopback1路由、SW3模拟办事loopback2和产品路由、RT1与FW2直连ipv4路由,将这些路由重发布到区域0。
SW3:
Interface Ethernet1/0/11
loopback
switchport access vlan 110
!
Interface Ethernet1/0/12
loopback
switchport access vlan 120
!
router ospf 2 vrf Office
ospf router-id 10.1.3.2
network 10.1.3.2/32 area 2
network 10.1.110.0/24 area 2
network 10.1.120.0/24 area 2
network 10.1.255.44/30 area 2
!
ipv6 route vrf Office ::/0 fe80::203:fff:fe2d:6e1 Vlan1015
FW2:
access-list route 1 deny any
router ospf 2
router-id 10.1.8.1
network 10.1.8.1/32 area 2
network 10.1.255.44/30 area 2
network 10.1.255.24/30 area 2
redistribute static
distribute-list 1 in ethernet0/1
exit
ip vrouter "trust-vr"
ipv6 route 2001:10:1:3::2/128 "ethernet0/1" FE80::203:FFF:FE3F:C694
ipv6 route 2001:10:1:110::/64 "ethernet0/1" FE80::203:FFF:FE3F:C694
ipv6 route 2001:10:1:120::/64 "ethernet0/1" FE80::203:FFF:FE3F:C694
ipv6 router ospf 2
redistribute static
exit
RT1:
route-map pp 10 permit
match ip address prefix-list pp
!
route-map ppc 10 permit
match ip address prefix-list ppc
!
ip prefix-list pp seq 5 permit 10.1.8.1/32
ip prefix-list pp seq 10 permit 10.1.3.2/32
ip prefix-list pp seq 15 permit 10.1.110.0/24
ip prefix-list pp seq 20 permit 10.1.120.0/24
ip prefix-list ppc seq 5 permit 10.1.255.24/30
!
router ospf 1
router-id 10.1.5.1
network 10.1.5.1 255.255.255.255 area 1
network 10.1.255.28 255.255.255.252 area 1
network 10.1.255.20 255.255.255.252 area 0
network 10.1.255.16 255.255.255.252 area 0
area 1 virtual-link 10.1.6.1
redistribute ospf 2 route-map pp
redistribute connect route-map ppc
router ospf 2
router-id 10.1.5.4
network 10.1.5.4 255.255.255.255 area 2
network 10.1.255.24 255.255.255.252 area 2
default-information originate always metric-type 1
!
(6)修改ospf cost为100,实现SW1分别与RT2、FW2之间ipv4互访流量优先通过SW1_SW2_RT1链路转发,SW2访问Internet ipv4流量优先通过SW2_SW1_FW1链路转发。
RT1:
interface GigaEthernet0/2
ip address 10.1.255.18 255.255.255.252
ipv6 enable
ip ospf cost 100
ipv6 ospf 1 area 0
!
FW1:
interface ethernet0/2
zone "trust"
ip address 10.1.255.17 255.255.255.252
ipv6 enable
manage ping
manage ssh
ip ospf cost 100
ipv6 ospf cost 100
ipv6 ospf 1 area 0
exit6.RT1串行链路、RT2串行链路、FW1、AC1之间分别运行RIP和RIPng、OSPFv2和OSPFv3协议,FW1、RT1、RT2的RIP和RIPng、OSPFv2和OSPFv3发布loopback2地址路由,保证loopback2数据优先走RIP和RIPng。RT1配置offset值为3的路由策略,实现RT1-S1/0_RT2-S1/1为主链路,RT1-S1/1_RT2-S1/0为备份链路,ipv4的ACL名称为AclRIP,ipv6的ACL名称为AclRIPng。RT1的S1/0与RT2的S1/1之间采用chap双向认证,用户名为对端设备名称,密码为skills01。
FW1:
router rip
network 10.1.7.2/32
network 10.1.255.16/30
exit
ipv6 router ospf 1
router-id 10.1.7.1
default-information originate type 1
exit
RT1:
aaa authentication ppp default local
!
username RT2 password 0 skills01
interface Serial1/0
ip address 10.1.255.33 255.255.255.252
encapsulation ppp
ppp authentication chap
ppp chap hostname RT1
ppp chap password 0 skills01
physical-layer speed 2048000
ipv6 enable
ip rip 1 enable
ipv6 rip 1 enable
!
interface Serial1/1
ip address 10.1.255.37 255.255.255.252
encapsulation ppp
physical-layer speed 2048000
ipv6 enable
ip rip 1 enable
ipv6 rip 1 enable
!
ip access-list standard AclRIP
permit any sequence 10
!
ipv6 access-list AclRIPng
permit ipv6 any any sequence 10
!
router ripng 1
offset Serial1/1 in AclRIPng 3
offset Serial1/1 out AclRIPng 3
!
router rip 1
version 2
offset Serial1/1 in AclRIP 3
offset Serial1/1 out AclRIP 3
!
interface Loopback2
ip address 10.1.5.2 255.255.255.255
ipv6 enable
ipv6 address 2001:10:1:5::2/128
ip rip 1 enable
ipv6 rip 1 enable
!
interface GigaEthernet0/2
ip address 10.1.255.18 255.255.255.252
ipv6 enable
ip rip 1 enable
ip ospf cost 100
ipv6 rip 1 enable
ipv6 ospf 1 area 0
ipv6 ospf cost 100
!
RT2:
router rip 1
version 2
!
router ripng 1
!
aaa authentication ppp default local
!
username RT1 password 0 skills01
interface Serial1/0
ip address 10.1.255.38 255.255.255.252
encapsulation ppp
physical-layer speed 2048000
ipv6 enable
ip rip 1 enable
ipv6 rip 1 enable
!
interface Serial1/1
ip address 10.1.255.34 255.255.255.252
encapsulation ppp
ppp authentication chap
ppp chap hostname RT2
ppp chap password 0 skills01
physical-layer speed 2048000
ipv6 enable
ip rip 1 enable
ipv6 rip 1 enable
!
interface Loopback2
ip address 10.1.6.2 255.255.255.255
ipv6 enable
ipv6 address 2001:10:1:6::2/128
ip rip 1 enable
ipv6 rip 1 enable
!
interface GigaEthernet0/1
ip address 10.1.255.41 255.255.255.252
ipv6 enable
ip rip 1 enable
ipv6 ospf 1 area 1
ipv6 rip 1 enable
!
AC1:
router rip
network 10.1.4.2/32
network 10.1.255.40/30
!
router ipv6 rip
!
interface Loopback2
ipv6 address 2001:10:1:4::2/128
ipv6 router rip
ip address 10.1.4.2 255.255.255.255
!
interface Vlan2001
ipv6 router rip
ipv6 router ospf area 1 tag 1
ip address 10.1.255.42 255.255.255.252
!7.RT1以太链路、RT2以太链路之间运行ISIS协议,进程1,分别实现loopback3之间ipv4互通和ipv6互通。RT1、RT2的NET分别为10.0000.0000.0001.00、10.0000.0000.0002.00,路由器类型是Level-2,接口网络类型为点到点。配置域md5认证和接口md5认证,密码均为skills01。
RT1:
router isis 1
is-type level-2
authentication mode md5 level-2
authentication key 0 skills level-2
net 10.0000.0000.0001.00
!
interface Loopback3
ip address 10.1.5.3 255.255.255.255
ipv6 enable
ipv6 address 2001:10:1:5::3/128
ip router isis 1
ipv6 router isis 1
isis network point-to-point
isis circuit-type level-2
isis authentication mode md5 level-2
isis authentication key 0 skills01
!
interface GigaEthernet0/0
ip address 10.1.255.29 255.255.255.252
ipv6 enable
ip router isis 1
ipv6 router isis 1
isis network point-to-point
isis circuit-type level-2
isis authentication mode md5 level-2
isis authentication key 0 skills01
ipv6 ospf 1 area 0
!
RT2:
router isis 1
is-type level-2
authentication mode md5 level-2
authentication key 0 skills level-2
net 10.0000.0000.0002.00
!
interface Loopback3
ip address 10.1.6.3 255.255.255.255
ipv6 enable
ipv6 address 2001:10:1:6::3/128
ip router isis 1
ipv6 router isis 1
isis network point-to-point
isis circuit-type level-2
isis authentication mode md5 level-2
isis authentication key 0 skills01
!
interface GigaEthernet0/0
ip address 10.1.255.30 255.255.255.252
ipv6 enable
ip router isis 1
ipv6 router isis 1
isis network point-to-point
isis circuit-type level-2
isis authentication mode md5 level-2
isis authentication key 0 skills01
ipv6 ospf 1 area 0
!
8.RT2配置ipv4 nat,实现AC1 ipv4产品用RT2外网接口ipv4地址访问Internet。RT2配置nat64,实现AC1 ipv6产品用RT2外网接口ipv4地址访问Internet,ipv4地址转ipv6地址前缀为64:ff9b::/96。
RT2:
ip route default 200.200.200.5
ip access-list standard nat4
permit 10.1.140.1 255.255.255.0 sequence 10
!
ip nat inside source list nat4 interface GigaEthernet0/3
!
ipv6 access-list nat6
permit ipv6 2001:10:1:140::/64 64:FF9B::/96 sequence 10
!
ipv6 nat v6v4 source list nat6 interface GigaEthernet0/3
ipv6 nat prefix 64:FF9B::/96 v4-mapped nat6
interface GigaEthernet0/3
ip address 200.200.200.6 255.255.255.252
ipv6 enable
ip nat outside
ipv6 nat
!
interface GigaEthernet0/1
ip address 10.1.255.41 255.255.255.252
ipv6 enable
ip rip 1 enable
ip nat inside
ipv6 nat
ipv6 ospf 1 area 1
ipv6 rip 1 enable
!9.SW1、SW2、SW3、RT1、RT2之间运行BGP协议,SW1、SW 2、RT1 AS号65001、RT2 AS号65002、SW3 AS号65003。
(1-2)SW1、SW2、SW3、RT1、RT2之间通过loopback1建立ipv4和ipv6 BGP邻居。SW1和SW2之间财务通过loopback2建立ipv4 BGP邻居,SW1和SW2的loopback2互通采用静态路由。SW1、SW2、SW3、RT2分别只发布营销、法务、财务、人力等ipv4和ipv6路由;RT1发布办事处营销ipv4和ipv6路由到BGP。
SW1:
router ipv6 ospf 2 vrf Finance
router-id 10.1.1.2
!
interface Loopback2
ip vrf forwarding Finance
ipv6 address 2001:10:1:1::2/128
ipv6 router ospf area 2 tag 2
ip address 10.1.1.2 255.255.255.255
!
interface Vlan2023
ip vrf forwarding Finance
ipv6 router ospf area 2 tag 2
ip address 10.1.255.1 255.255.255.252
!
//此处做ospf路由是为了使财务ipv6路由互通
ip route vrf Finance 10.1.2.2/32 10.1.255.2
router bgp 65001
network 10.1.12.0/24
network 10.1.13.0/24
network 10.1.15.0/24
neighbor 10.1.2.1 remote-as 65001
neighbor 10.1.2.1 update-source Loopback1
neighbor 10.1.2.1 next-hop-self
neighbor 10.1.3.1 remote-as 65003
neighbor 10.1.3.1 ebgp-multihop 255
neighbor 10.1.3.1 update-source Loopback1
neighbor 2001:10:1:2::1 remote-as 65001
neighbor 2001:10:1:2::1 update-source Loopback1
no neighbor 2001:10:1:2::1 activate
neighbor 2001:10:1:3::1 remote-as 65003
neighbor 2001:10:1:3::1 ebgp-multihop 255
neighbor 2001:10:1:3::1 update-source Loopback1
no neighbor 2001:10:1:3::1 activate
address-family ipv6 unicast
network 2001:10:1:12::/64
network 2001:10:1:13::/64
network 2001:10:1:15::/64
neighbor 2001:10:1:2::1 activate
neighbor 2001:10:1:3::1 activate
exit-address-family
address-family ipv4 vrf Finance
network 10.1.14.0/24
neighbor 10.1.2.2 remote-as 65001
neighbor 10.1.2.2 update-source Loopback2
exit-address-family
address-family ipv6 vrf Finance
network 2001:10:1:14::/64
neighbor 2001:10:1:2::2 remote-as 65001
neighbor 2001:10:1:2::2 update-source Loopback2
exit-address-family
!
SW2:
router ipv6 ospf 2 vrf Finance
router-id 10.1.2.2
!
interface Loopback2
ip vrf forwarding Finance
ipv6 address 2001:10:1:2::2/128
ipv6 router ospf area 2 tag 2
ip address 10.1.2.2 255.255.255.255
!
interface Vlan2023
ip vrf forwarding Finance
ipv6 router ospf area 2 tag 2
ip address 10.1.255.2 255.255.255.252
!
//此处做ospf路由是为了使财务ipv6路由互通
ip route vrf Finance 10.1.1.2/32 10.1.255.1
router bgp 65001
network 10.1.22.0/24
network 10.1.23.0/24
network 10.1.25.0/24
neighbor 10.1.1.1 remote-as 65001
neighbor 10.1.1.1 update-source Loopback1
neighbor 10.1.1.1 next-hop-self
neighbor 10.1.3.1 remote-as 65003
neighbor 10.1.3.1 ebgp-multihop 255
neighbor 10.1.3.1 update-source Loopback1
neighbor 2001:10:1:1::1 remote-as 65001
neighbor 2001:10:1:1::1 update-source Loopback1
no neighbor 2001:10:1:1::1 activate
neighbor 2001:10:1:3::1 remote-as 65003
neighbor 2001:10:1:3::1 ebgp-multihop 255
neighbor 2001:10:1:3::1 update-source Loopback1
no neighbor 2001:10:1:3::1 activate
neighbor 10.1.5.1 remote-as 65001
neighbor 10.1.5.1 update-source Loopback1
neighbor 10.1.5.1 next-hop-self
neighbor 2001:10:1:5::1 remote-as 65001
neighbor 2001:10:1:5::1 update-source Loopback1
no neighbor 2001:10:1:5::1 activate
address-family ipv6 unicast
network 2001:10:1:22::/64
network 2001:10:1:23::/64
network 2001:10:1:25::/64
neighbor 2001:10:1:1::1 activate
neighbor 2001:10:1:3::1 activate
neighbor 2001:10:1:3::1 activate
exit-address-family
address-family ipv4 vrf Finance
network 10.1.24.0/24
neighbor 10.1.1.2 remote-as 65001
neighbor 10.1.1.2 update-source Loopback2
exit-address-family
address-family ipv6 vrf Finance
network 2001:10:1:24::/64
neighbor 2001:10:1:1::2 remote-as 65001
neighbor 2001:10:1:1::2 update-source Loopback2
exit-address-family
!
SW3:
router bgp 65003
network 10.1.32.0/24
network 10.1.33.0/24
network 10.1.35.0/24
neighbor 10.1.1.1 remote-as 65001
neighbor 10.1.1.1 ebgp-multihop 255
neighbor 10.1.1.1 update-source Loopback1
neighbor 10.1.2.1 remote-as 65001
neighbor 10.1.2.1 ebgp-multihop 255
neighbor 10.1.2.1 update-source Loopback1
neighbor 2001:10:1:1::1 remote-as 65001
neighbor 2001:10:1:1::1 ebgp-multihop 255
neighbor 2001:10:1:1::1 update-source Loopback1
no neighbor 2001:10:1:1::1 activate
neighbor 2001:10:1:2::1 remote-as 65001
neighbor 2001:10:1:2::1 ebgp-multihop 255
neighbor 2001:10:1:2::1 update-source Loopback1
no neighbor 2001:10:1:2::1 activate
address-family ipv6 unicast
network 2001:10:1:32::/64
network 2001:10:1:33::/64
network 2001:10:1:35::/64
neighbor 2001:10:1:1::1 activate
neighbor 2001:10:1:2::1 activate
exit-address-family
!
RT1:
router bgp 65001
no synchronization
bgp log-neighbor-changes
network 10.1.120.0/24
neighbor 10.1.2.1 remote-as 65001
neighbor 10.1.2.1 update-source Loopback1
neighbor 10.1.2.1 next-hop-self
neighbor 10.1.6.1 remote-as 65002
neighbor 10.1.6.1 ebgp-multihop 255
neighbor 10.1.6.1 update-source Loopback1
neighbor 2001:10:1:2::1 remote-as 65001
neighbor 2001:10:1:2::1 update-source Loopback1
no neighbor 2001:10:1:2::1 activate
neighbor 2001:10:1:6::1 remote-as 65002
neighbor 2001:10:1:6::1 ebgp-multihop 255
neighbor 2001:10:1:6::1 update-source Loopback1
no neighbor 2001:10:1:6::1 activate
address-family ipv6
no synchronization
network 2001:10:1:120::/64
neighbor 2001:10:1:2::1 activate
neighbor 2001:10:1:6::1 activate
exit-address-family
!
RT2:
router bgp 65002
no synchronization
bgp log-neighbor-changes
network 10.1.150.0/24
neighbor 10.1.5.1 remote-as 65001
neighbor 10.1.5.1 ebgp-multihop 255
neighbor 10.1.5.1 update-source Loopback1
neighbor 2001:10:1:5::1 remote-as 65001
neighbor 2001:10:1:5::1 ebgp-multihop 255
neighbor 2001:10:1:5::1 update-source Loopback1
no neighbor 2001:10:1:5::1 activate
address-family ipv6
no synchronization
network 2001:10:1:150::/64
neighbor 2001:10:1:5::1 activate
exit-address-family
!财务v4与v6互通验证:

(3)SW3营销分别与SW1和SW2营销ipv4和ipv6互访优先在SW3_SW1链路转发;SW3法务及人力分别与SW1和SW2法务及人力ipv4和ipv6互访优先在SW3_SW2链路转发,主备链路相互备份;用prefix-list、route-map和BGP路径属性进行选路,新增AS 65000。
SW3:
ip prefix-list SW1-SW2-FWRL-IPv4 seq 5 permit 10.1.13.1/24
ip prefix-list SW1-SW2-FWRL-IPv4 seq 10 permit 10.1.15.1/24
ip prefix-list SW1-SW2-FWRL-IPv4 seq 15 permit 10.1.23.1/24
ip prefix-list SW1-SW2-FWRL-IPv4 seq 20 permit 10.1.25.1/24
ip prefix-list SW1-SW2-YX-IPv4 seq 5 permit 10.1.12.1/24
ip prefix-list SW1-SW2-YX-IPv4 seq 10 permit 10.1.22.1/24
ip prefix-list SW3-FWRL-IPv4 seq 5 permit 10.1.33.1/24
ip prefix-list SW3-FWRL-IPv4 seq 10 permit 10.1.35.1/24
ip prefix-list SW3-IPv4 seq 5 permit 10.1.32.1/24
ipv6 prefix-list SW1-SW2-FWRL-IPv6 seq 5 permit 2001:10:1:13::1/64
ipv6 prefix-list SW1-SW2-FWRL-IPv6 seq 10 permit 2001:10:1:23::1/64
ipv6 prefix-list SW1-SW2-FWRL-IPv6 seq 15 permit 2001:10:1:15::1/64
ipv6 prefix-list SW1-SW2-FWRL-IPv6 seq 20 permit 2001:10:1:25::1/64
ipv6 prefix-list SW1-SW2-YX-IPv6 seq 5 permit 2001:10:1:12::1/64
ipv6 prefix-list SW1-SW2-YX-IPv6 seq 10 permit 2001:10:1:22::1/64
ipv6 prefix-list SW3-FWRL-IPv6 seq 5 permit 2001:10:1:33::1/64
ipv6 prefix-list SW3-FWRL-IPv6 seq 10 permit 2001:10:1:35::1/64
ipv6 prefix-list SW3-IPv6 seq 5 permit 2001:10:1:32::1/64
route-map SW1-SW2-YX-IPv4 permit 10
match ip address prefix-list SW1-SW2-YX-IPv4
set as-path prepend 65000
set ip next-hop 10.1.1.1
!
route-map SW1-SW2-YX-IPv4 permit 20
!
route-map SW1-SW2-YX-IPv6 permit 10
match ipv6 address prefix-list SW1-SW2-YX-IPv6
set as-path prepend 65000
set ipv6 next-hop 2001:10:1:1::1
!
route-map SW1-SW2-YX-IPv6 permit 20
!
route-map SW1-SW2-FWRL-IPv4 permit 10
match ip address prefix-list SW1-SW2-FWRL-IPv4
set as-path prepend 65000
set ip next-hop 10.1.2.1
!
route-map SW1-SW2-FWRL-IPv4 permit 20
!
route-map SW1-SW2-FWRL-IPv6 permit 10
match ipv6 address prefix-list SW1-SW2-FWRL-IPv6
set as-path prepend 65000
set ipv6 next-hop 2001:10:1:2::1
!
route-map SW1-SW2-FWRL-IPv6 permit 20
!
route-map SW3-FWRL-IPv6 permit 10
match ipv6 address prefix-list SW3-FWRL-IPv6
set as-path prepend 65000
set ipv6 next-hop 2001:10:1:2::1
!
route-map SW3-FWRL-IPv6 permit 20
!
route-map SW3-YX-IPv6 permit 10
match ipv6 address prefix-list SW3-YX-IPv6
set as-path prepend 65000
set ipv6 next-hop 2001:10:1:1::1
!
route-map SW3-YX-IPv6 permit 20
!
route-map SW3-FWRL-IPv4 permit 10
match ip address prefix-list SW3-FWRL-IPv4
set as-path prepend 65000
set ip next-hop 10.1.2.1
!
route-map SW3-FWRL-IPv4 permit 20
!
route-map SW3-YX-IPv4 permit 10
match ip address prefix-list SW3-YX-IPv4
set as-path prepend 65000
set ip next-hop 10.1.1.1
!
route-map SW3-YX-IPv4 permit 20
!
router bgp 65003
neighbor 10.1.1.1 route-map SW1-SW2-FWRL-IPv4 in
neighbor 10.1.1.1 route-map SW3-FWRL-IPv4 out
neighbor 10.1.2.1 route-map SW1-SW2-YX-IPv4 in
neighbor 10.1.2.1 route-map SW3-YX-IPv4 out
address-family ipv6 unicast
neighbor 2001:10:1:1::1 route-map SW1-SW2-FWRL-IPv6 in
neighbor 2001:10:1:1::1 route-map SW3-FWRL-IPV6 out
neighbor 2001:10:1:2::1 route-map SW1-SW2-YX-IPv6 in
neighbor 2001:10:1:2::1 route-map SW3-YX-IPv6 out
exit-address-family
!
比较麻烦多,看看自己做的有没有错可以验证一下:

可以看到vlan2019有sw1和sw2的营销路由,走SW1-SW3,验证成功
10.利用BGP MPLS VPN技术,RT1与RT2以太链路间运行多协议标签交换、标
签分发协议。RT1与RT2间创建财务VPN实例,名称为Finance,RT1的RD值为1:1,export rt值为1:2,import rt值为2:1;RT2的RD值为2:2。通过两端loopback1建立VPN邻居,分别实现两端loopback5 ipv4互通和ipv6互通。
RT1:
ipv6 vrf Finance
rd 1:1
route-target import 2:1
route-target export 1:2
!
!
!
mpls ip
mpls ldp router-id 10.1.5.1
!
!
ip vrf Finance
rd 1:1
route-target export 1:2
route-target import 2:1
interface GigaEthernet0/0
mpls ip
mpls ip encapsulate
mpls ldp enable
!
router bgp 65001
address-family vpnv4
neighbor 10.1.6.1 activate
neighbor 10.1.6.1 send-community both
exit-address-family
address-family vpnv6
neighbor 2001:10:1:6::1 activate
neighbor 2001:10:1:6::1 send-community both
exit-address-family
address-family ipv4 vrf Finance
no synchronization
network 10.1.5.5/32
exit-address-family
address-family ipv6 vrf Finance
no synchronization
network 2001:10:1:5::5/128
exit-address-family
interface Loopback5
ip vrf forwarding Finance
ip address 10.1.5.5 255.255.255.255
ipv6 enable
ipv6 address 2001:10:1:5::5/128
ipv6 vrf forwarding Finance
mpls ip encapsulate
interface GigaEthernet0/0
mpls ip
mpls ip encapsulate
mpls ldp enable
RT2:
ipv6 vrf Finance
rd 2:2
route-target import 1:2
route-target export 2:1
!
!
!
mpls ip
mpls ldp router-id 10.1.6.1
!
!
ip vrf Finance
rd 2:2
route-target export 2:1
route-target import 1:2
interface GigaEthernet0/0
mpls ip
mpls ip encapsulate
ipv6 ospf 1 area 0
!
router bgp 65002
address-family vpnv4
neighbor 10.1.5.1 activate
neighbor 10.1.5.1 send-community both
exit-address-family
address-family vpnv6
neighbor 2001:10:1:5::1 activate
neighbor 2001:10:1:5::1 send-community both
exit-address-family
address-family ipv4 vrf Finance
no synchronization
network 10.1.6.5/32
exit-address-family
address-family ipv6 vrf Finance
no synchronization
network 2001:10:1:6::5/128
exit-address-family
interface Loopback5
ip vrf forwarding Finance
ip address 10.1.6.5 255.255.255.255
ipv6 enable
ipv6 address 2001:10:1:6::5/128
ipv6 vrf forwarding Finance
mpls ip encapsulate
interface GigaEthernet0/0
mpls ip
mpls ip encapsulate
mpls ldp enable
可以验证一下,注意,一定要loopback5直接ping,不要原ping

验证成功!
四、无线部署
1.AC1 loopback1 ipv4和ipv6地址分别作为AC1的ipv4和ipv6管理地址。AP二层自动注册,AP采用序列号认证。配置2个ssid,分别为skills-2.4G和skills-5G。skills-2.4G对应vlan140,用network 140和radio1(模式为n-only-g),用户接入无线网络时需要采用基于WPA-personal加密方式,密码为skills2023。skills-5G对应vlan150,用network 150和radio2(模式为n-only-a),不需要认证,隐藏ssid,skills-5G用倒数第一个可用VAP发送5G信号。
AC1:
wireless
ap authentication mac
discovery vlan-list 130
static-ip 10.1.4.1
static-ipv6 2001:10:1:4::1
network 140
security mode wpa-personal
ssid skills-2.4G
vlan 140
wpa key encrypted 40a969b568f4229e3f9adfbb383055d332c1a42ade6bb7e6ddab6051064fbd819de3f7d325509f4244e0b6517a6b2155fca049fe5cb12b2322da0b9bee397d24
//这里密码是skills2023,被加密过
!
network 150
hide-ssid
ssid skills-5G
vlan 150
!
ap profile 1
channel-plan an time 05:00
channel-plan bgn time 05:00
air-match template 1
radio 1
mode n-only-g
vap 0
network 140
!
!
radio 2
mode n-only-a
vap 0
!
vap 15
enable
network 150
!
!
!
!
ap database 00-03-0f-ea-5b-c0
查看ap上线状态:

2.当AP上线,如果AC中储存的Image版本和AP的Image版本号不同时,会触发AP自动升级。AP失败状态超时时间及探测到的客户端状态超时时间都为2小时。
AC1:
wireless
ap auto-upgrade
agetime ap-failure 2
agetime detected-clients 2
!3.MAC认证模式为黑名单,MAC地址为80-45-DD-77-CC-48的无线终端采用全局配置MAC认证。
AC1:
wireless
known-client 80-45-dd-77-cc-48 action global-action
network 140
mac authentication local
!
network 150
mac authentication local
!4.网络管理员的专属IP地址为10.10.10.10,为了保障网络管理的安全性,若发现的设备接入无线路由器并使用SSH功能时,在不对其信号强度进行过滤的前提下,在全频道内每隔15秒进行一次定位。
AC1:
wireless
ap profile 1
device-location fingerprint ipv4 10.10.10.10 port 23 interval 15 rssi-filter enable scan-type full-channel
5.配置vlan140无线接入用户最大可连接人数为100人, 周一至周三17点至19点禁止用户连接。
AC1:
wireless
network 140
max-clients 100
time-limit from 17:00 to 19:00 weekday monday
time-limit from 17:00 to 19:00 weekday tuesday
time-limit from 17:00 to 19:00 weekday wednesday 6.开启Radio的自动信道调整,每天上午10:00触发信道调整功能。
AC1:
wireless
ap profile 1
channel-plan an time 10:00
channel-plan bgn time 10:00
7.开启AP组播广播突发限制功能;AP收到错误帧时,将不再发送ACK帧;AP发送向无线终端表明AP存在的帧时间间隔为1秒。
AC1:
wireless
ap profile 1
radio 1
rate-limit
beacon-interval 1000
incorrect-frame-no-ack
radio 2
rate-limit
beacon-interval 1000
incorrect-frame-no-ack8.该公司AC1想按照法国2.4GHz频段信道标准进行设置,做一个信道测试对比,需要根据国外情况进行修正。
AC1:
wireless
country-code FR tx-power-unlimited enable 五、安全维护
说明:ip地址按照题目给定的顺序用"ip/mask"表示,ipv4 any地址用0.0.0.0/0,ipv6 any地址用::/0,禁止用地址条目,否则按零分处理。
1.FW1配置ipv4 nat,实现集团产品1段ipv4访问Internet ipv4,转换ip/mask为200.200.200.16/28,保证每一个源ip产生的所有会话将被映射到同一个固定的IP地址;当有流量匹配本地址转换规则时产生日志信息,将匹配的日志发送至10.1.11.120的UDP 514端口,记录主机名,用明文轮询方式分发日志;开启相关特性,实现扩展nat转换后的网络地址端口资源。



2.FW1配置L2TP VPN,名称为VPN,满足远程办公用户通过拨号登陆访问内网,创建隧道接口为tunnel 1、并加入vpnhub安全域,地址池名称为AddressPool,地址池为172.30.253.1/24-10172.30.253.100/24,网关为最大可用地址,认证账号skills01,密码skills01。



3.FW1和FW2策略默认动作为拒绝,FW1允许集团产品1段ipv4和ipv6访问Internet任意服务。


4.FW2允许办事处产品ipv4访问集团产品1段https服务,允许集团产品1段访问办事处产品ipv4、FW2 loopback1 ipv4、SW3模拟办事处loopback2 ipv4。


5.FW1与RT2之间用Internet互联地址建立GRE Over IPSec VPN,实现loopback4之间的加密访问。




RT2:
ip route default 200.200.200.5
ip route 10.1.7.4 255.255.255.255 Tunnel4
crypto isakmp key 0 123456 address 200.200.200.2 255.255.255.255
crypto isakmp policy 1
authentication pre-share
encryption 3des
group 2
hash md5
lifetime 86400
!
crypto ipsec transform-set SET-1 esp-3des esp-md5-hmac
mode transport
!
crypto map map 1 ipsec-isakmp
match address acl
set peer 200.200.200.2
set transform-set SET-1
!
ip access-list extended acl
permit gre 200.200.200.6 255.255.255.252 200.200.200.2 255.255.255.252 sequence 10
!
interface GigaEthernet0/3
ip address 200.200.200.6 255.255.255.252
ipv6 enable
ip nat outside
ipv6 nat
crypto map map
FW1:
ip vrouter "trust-vr"
ip route 10.1.6.4/32 "tunnel4"
ip route 0.0.0.0/0 200.200.200.1
tunnel gre "GRE-1"
source 200.200.200.2
destination 200.200.200.6
interface ethernet0/3
next-tunnel ipsec b
interface tunnel4
zone "VPNHub"
ip address 10.1.255.49 255.255.255.252
ipv6 enable
manage ping
manage ssh
tunnel gre "GRE-1" gw 10.1.255.50
exit
SW3:
ip route vrf Internet 0.0.0.0/0 200.200.200.2
ip route vrf Internet 0.0.0.0/0 200.200.200.6
//做完后记得FW1开放行策略,不然loopback4直接通不了,这里不再演示了6.FW1配置邮件内容过滤,规则名称和类别名称均为"赌博",过滤含有"游戏"字样的邮件。
7.FW1通过ping监控外网网关地址,监控对象名称为Track1,每隔5S发送探测报文,连续10次收不到监测报文,就认为线路故障,关闭外网接口。
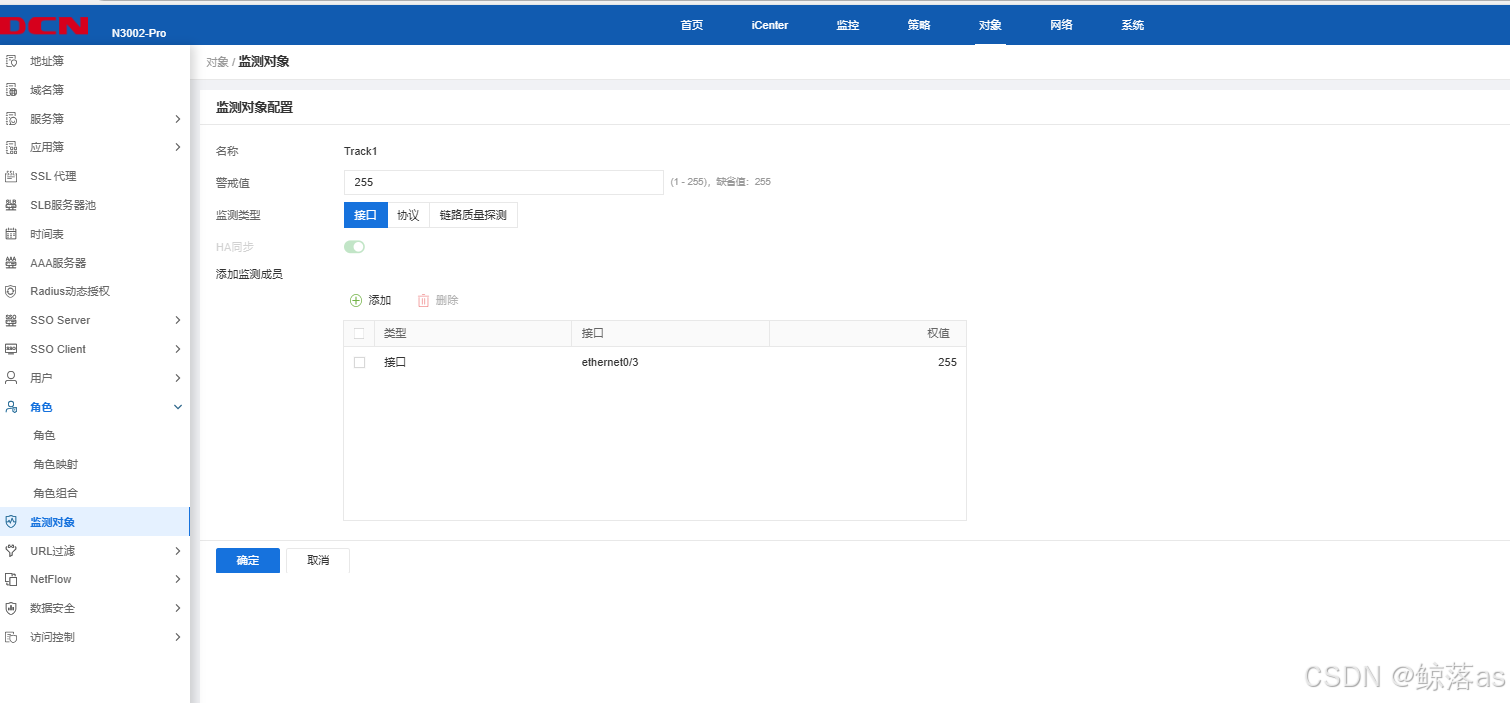

FW1:
//补充,代码做法
track Track1
icmp 200.200.200.1 interface ethernet0/3 interval 5 threshold 10 src-interface ethernet0/3
interface ethernet0/3
shutdown track Track1

























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








