传统蓝牙(BE/EDR)的设备发现
Bluetooth Spec v5.2 中关于设备发现的内容
3.3.1.3 Inquiry scan channel
3.3.1.3.1 Overview
In order for a device to be discovered, an inquiry scan channel is used. A discoverable device listens for inquiry requests on its inquiry scan channel and then sends a response to that request. In order for a device to discover other devices, it iterates (hops) through all possible inquiry scan channel frequencies in a pseudo-random fashion, sending an inquiry request on each frequency and listening for any response
3.3.1.3.2 Characteristics
Inquiry scan channels follow a slower hopping pattern and use an access code to distinguish between occasional occupancy of the same radio frequency by two co-located devices using different physical channels.
The access code used on the inquiry scan channel is taken from a reserved set of inquiry access codes that are shared by all Bluetooth devices. One access code is used for general inquiries, and a number of additional access codes are reserved for limited inquiries. Each device has access to a number of different inquiry scan channels. As all of these channels share an identical hopping pattern, a device may concurrently occupy more than one inquiry scan channel if it is capable of concurrently correlating more than one access code.
A device using one of its inquiry scan channels remains passive on that channel until it receives an inquiry message on this channel from another Bluetooth device. This is identified by the appropriate inquiry access code. The inquiry scanning device will then follow the inquiry response procedure to return a response to the inquiring device. In order for a device to discover other Bluetooth devices it uses the inquiry scan channel to send inquiry requests. As it has no prior knowledge of the devices to discover, it cannot know the exact characteristics of the inquiry scan channel.
The device takes advantage of the fact that inquiry scan channels have a reduced number of hop frequencies and a slower rate of hopping. The inquiring device transmits inquiry requests on each of the inquiry scan hop frequencies and listens for an inquiry response. Transmissions are done at a faster rate, allowing the inquiring device to cover all inquiry scan frequencies in a easonably short time period.
3.3.1.3.3 Topology
Inquiring and discoverable devices use a simple exchange of packets to fulfill the inquiring function. The topology formed during this transaction is a simple and transient point-to-point connection.
3.3.1.3.4 Supported layers
During the exchange of packets between an inquiring and discoverable device it may be considered that a temporary physical link exists between these devices. However, the concept is quite irrelevant as it has no physical representation but is only implied by the brief transaction between the devices. No further architectural layers are considered to be supported
4.2.1 BR/EDR procedures
4.2.1.1 Inquiry (discovering) procedure
Bluetooth devices use the inquiry procedure to discover nearby devices, or to be discovered by devices in their locality.
The inquiry procedure is asymmetrical. A Bluetooth device that tries to find other nearby devices is known as an inquiring device and actively sends inquiry requests. Bluetooth devices that are available to be found are known as discoverable devices and listen for these inquiry requests and send responses. The inquiry procedure uses a special physical channel for the inquiry requests and responses.
Both inquiring and discoverable devices may already be connected to other Bluetooth devices in a piconet. Any time spent inquiring or occupying the inquiry scan physical channel needs to be balanced with the demands of the QoS commitments on existing logical transports.
The inquiry procedure does not make use of any of the architectural layers above the physical channel, although a transient physical link may be considered to be present during the exchange of inquiry and inquiry response information.
4.2.1.1.1 Extended Inquiry response
An Extended Inquiry Response can be used to provide miscellaneous information during the inquiry response procedure. Data types are defined for such things as local name and supported services, information that otherwise would have to be obtained by establishing a connection. A device that receives a local name and a list of supported services in an extended inquiry response does not have to connect to do a remote name request and an SDP service search, thereby shortening the time to useful information. It is recommended that a device includes all supported services and a significant portion of its local name, if that name is too long to be sent in its entirety, in the extended inquiry response.
The extended inquiry response procedure is backwards compatible with the
standard inquiry response procedure.
手机端蓝牙设置列表蓝牙设备的发现

如上图所示,在我点击"与新设备配对"的图标时,会进入如下设备发现的界面:

在上面截图中,代表手机蓝牙正在进行蓝牙扫描(发现)的动作,按照Bluetooth Spec的定义, 此时手机蓝牙时处于"Inquiring"的状态. 在手机蓝牙处于这个状态时,手机蓝牙会在特定的"Inquiry scan channel"发起"inquiry requests", 而此刻处于"discoverable"的蓝牙音箱正在监听着"Inquiry scan channel"的"inquiry requests"并发送对应的"respond", 这时候的蓝牙手机在收到对应的"respond"后,就发现了该蓝牙设备.
如下图所示,在手机蓝牙界面中出现了我的蓝牙音箱设备"小爱触屏音箱-0017".

而这个过程"手机发现小米小爱蓝牙音箱"在Bluetooth Spec v5.2 也有对应的规范说明.
在Vol2 -> Part F: Message Sequence Charts -> 2 Service without connection request -> 2.2 ONE-TIME INQUIRY中:
Inquiry is used to detect and collect nearby devices.
Step 1: The Host sends an HCI_Inquiry command. (See Figure 2.4.)

Step 2: The Controller will start the Baseband Inquiry procedure with the
specified Inquiry Access Code and Inquiry Length. When inquiry responses are
received, the Controller extracts the required information and returns the
information related to the found devices using one or more HCI_Inquiry_Result
events to the Host. (See Figure 2.5.)

Step 3a: If the Host wishes to terminate an Inquiry, the HCI_Inquiry_Cancel
command is used to immediately stop the inquiry procedure.
(See Figure 2.6.)

Step 3b: If the Inquiry procedure is completed due to the number of results
obtained, or the Inquiry Length has expired, an HCI_Inquiry_Complete event is
returned to the Host. (See Figure 2.7.)

上述的内容是来源于"Bluetooth Spec v5.2", 关于更详细的内容请下载对应的pdf进行学习.
补充说明:
之前一直把BE/EDR发现设备的过程理解成了和BLE设备发现过程是类似的,但经过这次的学习理解到了: 手机发现周围的传统蓝牙设备是手机端蓝牙主动发起的"inquiry requests"
基于空包的设备发现过程分析
未完待续!!! 待抓包后输出
传统蓝牙(BE/EDR)的设备连接
Bluetooth Spec v5.2 中关于设备发现的内容
3.3.1.4 Page scan channel
3.3.1.4.1 Overview
A connectable device (one that is prepared to accept connections) does so using a page scan channel. A connectable device listens for a page request on its page scan channel and, once received, enters into a sequence of exchanges with this device. In order for a device to connect to another device, it iterates (hops) through all page scan channel frequencies in a pseudorandom fashion, sending a page request on each frequency and listening for a response.
3.3.1.4.2 Characteristics
The page scan channel uses an access code derived from the scanning device’s Bluetooth device address to identify communications on the channel. The page scan channel uses a slower hopping rate than the hop rate of the basic and adapted piconet channels. The hop selection algorithm uses the Bluetooth device clock of the scanning device as an input.
A device using its page scan channel remains passive until it receives a page request from another Bluetooth device. This is identified by the page scan channel access code. The two devices will then follow the page procedure to form a connection. Following a successful conclusion of the page procedure both devices switch to the basic piconet channel that is characterized by having the paging device as master.
In order for a device to connect to another Bluetooth device it uses the page scan channel of the target device in order to send page requests. If the paging device does not know the phase of the target device’s page scan channel it therefore does not know the current hop frequency of the target device. The paging device transmits page requests on each of the page scan hop frequencies and listens for a page response. This is done at a faster hop rate,allowing the paging device to cover all page scan frequencies in a reasonably short time period.
The paging device may have some knowledge of the target device’s Bluetooth clock (indicated during a previous inquiry transaction between the two devices, or as a result of a previous involvement in a piconet with the device), in this case it is able to predict the phase of the target device’s page scan channel. It may use this information to optimize the synchronization of the paging and page scanning process and speed up the formation of the connection.
4.2.1.2 Paging (connecting) procedure
The procedure for forming connections is asymmetrical and requires that one Bluetooth device carries out the page (connection) procedure while the other Bluetooth device is connectable (page scanning). The procedure is targeted, so that the page procedure is only responded to by one specified Bluetooth device.
The connectable device uses a special physical channel to listen for connection request packets from the paging (connecting) device. This physical channel has attributes that are specific to the connectable device, hence only a paging device with knowledge of the connectable device is able to communicate on this channel.
Both paging and connectable devices may already be connected to other Bluetooth devices. Any time spent paging or occupying the page scan physical channel needs to be balanced with the demands of the QoS commitments on existing logical transports.
手机端蓝牙设置列表发起的蓝牙设备连接
这部分主要是分析下手机蓝牙在发现小米小爱蓝牙设备后主动发起对于其的连接过程:
如下图所示, 在手机蓝牙"与新设备配对"的界面扫描(发现)到"小爱触屏音箱-0017"后,点击连接.

连接成功后会出现如下界面: 蓝牙连接成功.

在这个连接过程,“小米小爱音箱"是处于"connectable”; 而手机蓝牙发起对于"小米小爱音箱"的连接流程在Bluetooth Spec中被定义为"Paging (Connecting) procedure".
在这个过程中"Connectable device - 小米小爱音箱" 通过特定的physical channel(Page scan channel)进行"connection request packet"的监听,而我们在手机蓝牙触发连接的动作实际就是在特定的physical channel进行"connection request packet"的发送(这里需要注意的是和设备发现类似,这里特定的"physical channal"进行对应包的发送也是调频进行发的),当"小米小爱音箱"接收到对应的request后会回复特定的respond. 这时候可以理解为"手机蓝牙"和"小米小爱音箱"在physical channel这一层面是成功建立了连接. 然后才是ACL的连接连接建立, 详细的行为在Bleutooth Spec中有如下定义:
3 ACL CONNECTION ESTABLISHMENT AND DETACHMENT
A flow diagram of the establishment and detachment of a connection between two devices is shown in Figure 3.1. The process is illustrated in 9 distinct steps. A number of these steps may be optionally performed, such as authentication and encryption. Some steps are required, such as the Connection Request and Setup Complete steps. The steps in the overview diagram directly relate to the steps in the following message sequence charts

3.1 CONNECTION SETUP
Step 1: The Host sends an HCI_Create_Connection command to the Controller. The Controller then performs a Baseband Paging procedure with the specified BD_ADDR. (See Figure 3.2.)
Step 1 指的就是我们前面讲到的"Paging (Connecting) procedure"

Step 2: Optionally, the LM may decide to exchange features.
(See Figure 3.3.)

Step 3: The LM on the master will request an LMP_HOST_CONNECTION_-REQ PDU. The LM on the slave will then confirm that a connection is OK, and if so, what role is preferred. (See Figure 3.4)

Step 4a: The remote Host rejects this connection, and the link is terminated.
(See Figure 3.5.)

Step 4b: The remote Host accepts this connection. (See Figure 3.6.)

Step 4c: The remote Host accepts this connection but with the preference of being a master. This will cause a role switch to occur before the LMP_-ACCEPTED for the LMP_HOST_CONNECTION_REQ PDU is sent. (See Figure 3.7.)
这里涉及到Master 和 Slave的理解, Spec中的定义如下:
One device provides the synchronization reference and is known as the master. All other devices synchronized to a master’s clock and frequency hopping pattern are known as slaves.

Step 5: After the features have been exchanged and AFH support is determined to be available, the master may at any time send an LMP_SET_AFH and LMP_CHANNEL_CLASSIFICATION_REQ PDU. (See Figure 3.8.)

Step 6: The LM will request if authentication is required. It does this by requesting the Link Key for this connection from the Host. (See Figure 3.9.)

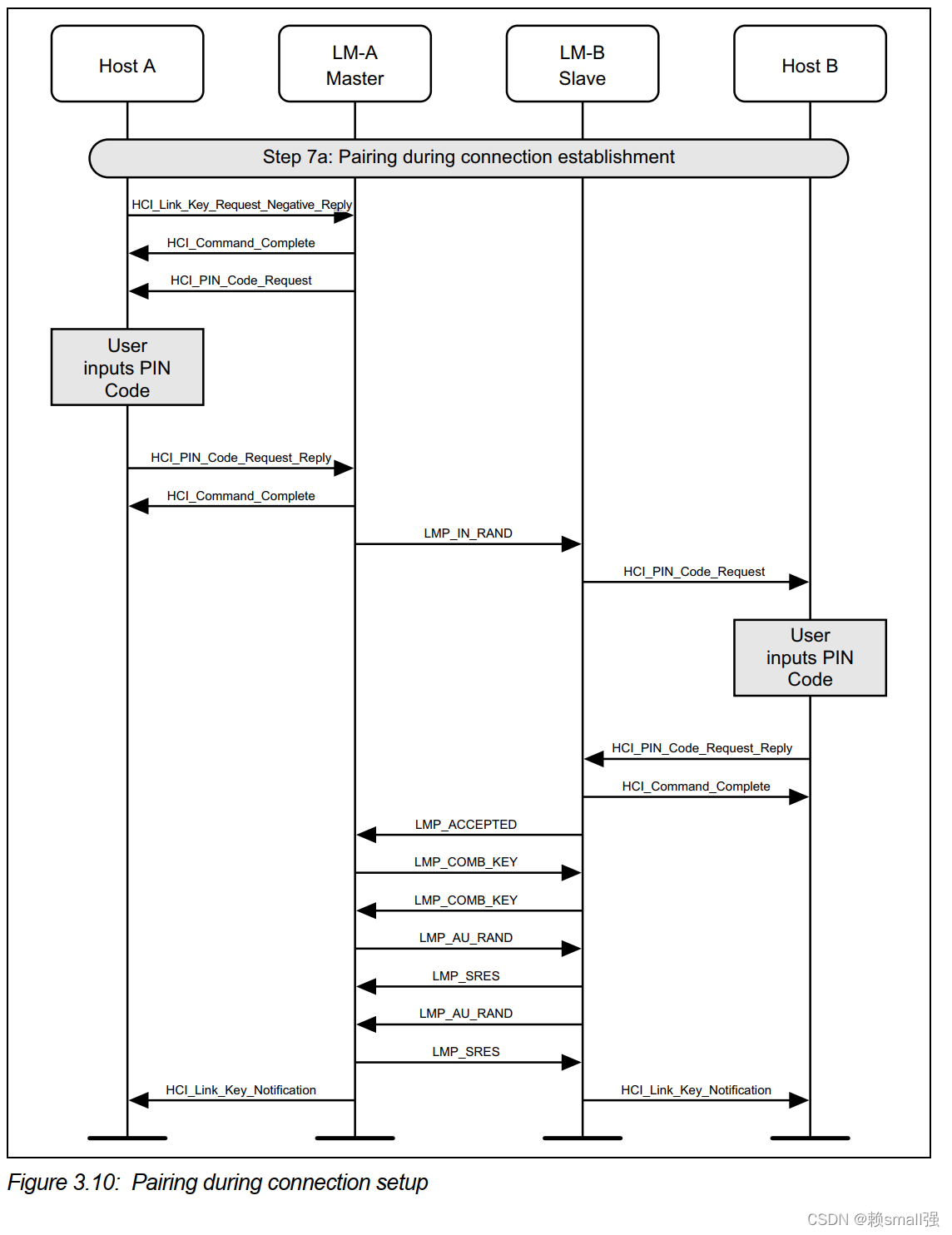
Step 7a: If authentication is required by the higher layers and the devices to be connected do not have a common link key, a pairing procedure will be used. The LM will have requested a link key from the Host for this connection. If there is a negative reply, then a PIN code will be requested. This PIN code will be requested on both sides of the connection, and authentication performed based on this PIN code. The last step is for the new link key for this connection to be passed to the Host so that it may store it for future connections.
(See Figure 3.10.)
Step 7b: If a common link key exists between the devices, then pairing is not needed. The LM will have asked for a link key from the Host for this connection. If this is a positive reply, then the link key is used for authentication. If the configuration parameter Authentication_Enable is set, then the authentication procedure must be executed. This MSC only shows the case when Authentication_Enable is set on both sides. (See Figure 3.11.)

Step 8: Once the pairing or authentication procedure is successful, the encryption procedure may be started. This MSC only shows the set up of an encrypted point-to-point connection. (See Figure 3.12.)
 Step 9: The LMs indicate that the connection is setup by sending LMP_-SETUP_COMPLETE PDU. This will cause the Host to be notified of the new Connection_Handle, and this connection may be used to send higher layer data such as L2CAP information. (See Figure 3.13.)
Step 9: The LMs indicate that the connection is setup by sending LMP_-SETUP_COMPLETE PDU. This will cause the Host to be notified of the new Connection_Handle, and this connection may be used to send higher layer data such as L2CAP information. (See Figure 3.13.)

Step 10: Once the connection is no longer needed, either device may terminate the connection using the HCI_Disconnect command and
LMP_DETACH message PDU. The disconnection procedure is one-sided and does not need an explicit acknowledgment from the remote LM. The use of ARQ Acknowledgment from the Baseband is needed to ensure that the remote LM has received the LMP_DETACH PDU. (See Figure 3.14.)

这里补充说明下,传统蓝牙中安全相关的概念:
5.1 Security architecture
The Bluetooth security model includes five distinct security features: pairing,
bonding, device authentication, encryption and message integrity.
- Pairing: the process for creating one or more shared secret keys
- Bonding: the act of storing the keys created during pairing for use in subsequent connections in order to form a trusted device pair.
- Device authentication: verification that the two devices have the same keys
- Encryption: message confidentiality.
- Message integrity: protects against message forgeries.
基于空包的设备连接过程分析
未完待续!!! 待抓包后输出
























 2万+
2万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








