H3C IPsec+IKE 预共享密钥方法配置实验
实验拓扑
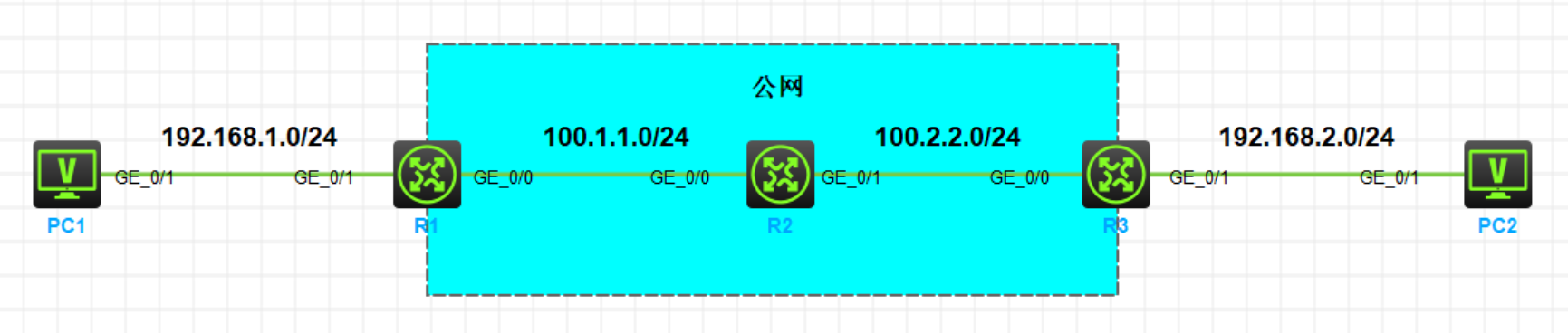
实验需求
- 按照图示配置 IP 地址
- 在 R1 和 R3 上配置默认路由连通公网
- 在 R1 和 R3 上配置 IPsec VPN,使两端私网可以互相访问
实验步骤
按照图示配置IP地址
[R1]display ip interface brief
*down: administratively down
(s): spoofing (l): loopback
Interface Physical Protocol IP address/Mask VPN instance Description
GE0/0 up up 100.1.1.1/24 -- --
GE0/1 up up 192.168.1.254/24 -- --
[R2]display ip interface brief
*down: administratively down
(s): spoofing (l): loopback
Interface Physical Protocol IP address/Mask VPN instance Description
GE0/0 up up 100.1.1.2/24 -- --
GE0/1 up up 100.2.2.2/24 -- --
[R3]display ip interface brief
*down: administratively down
(s): spoofing (l): loopback
Interface Physical Protocol IP address/Mask VPN instance Description
GE0/0 up up 100.2.2.3/24 -- --
GE0/1 up up 192.168.2.254/24 -- --
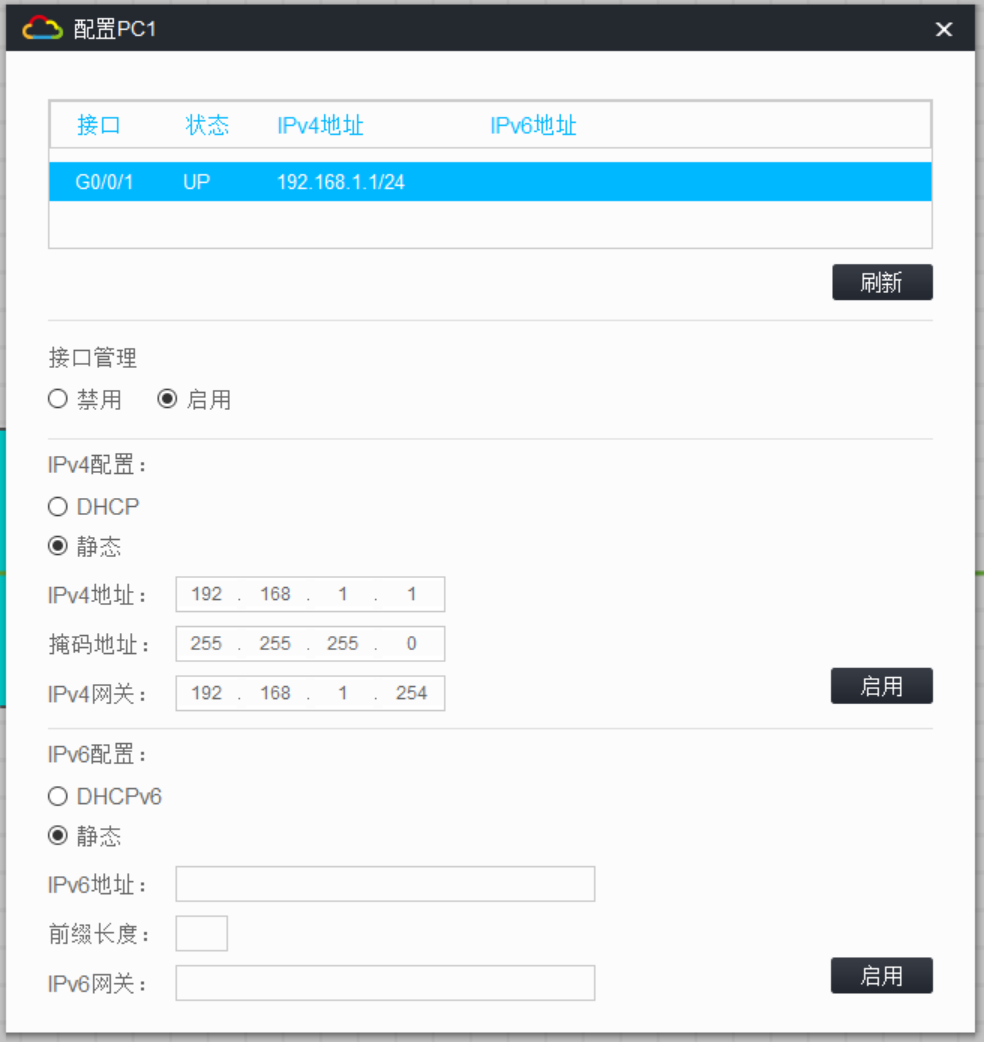
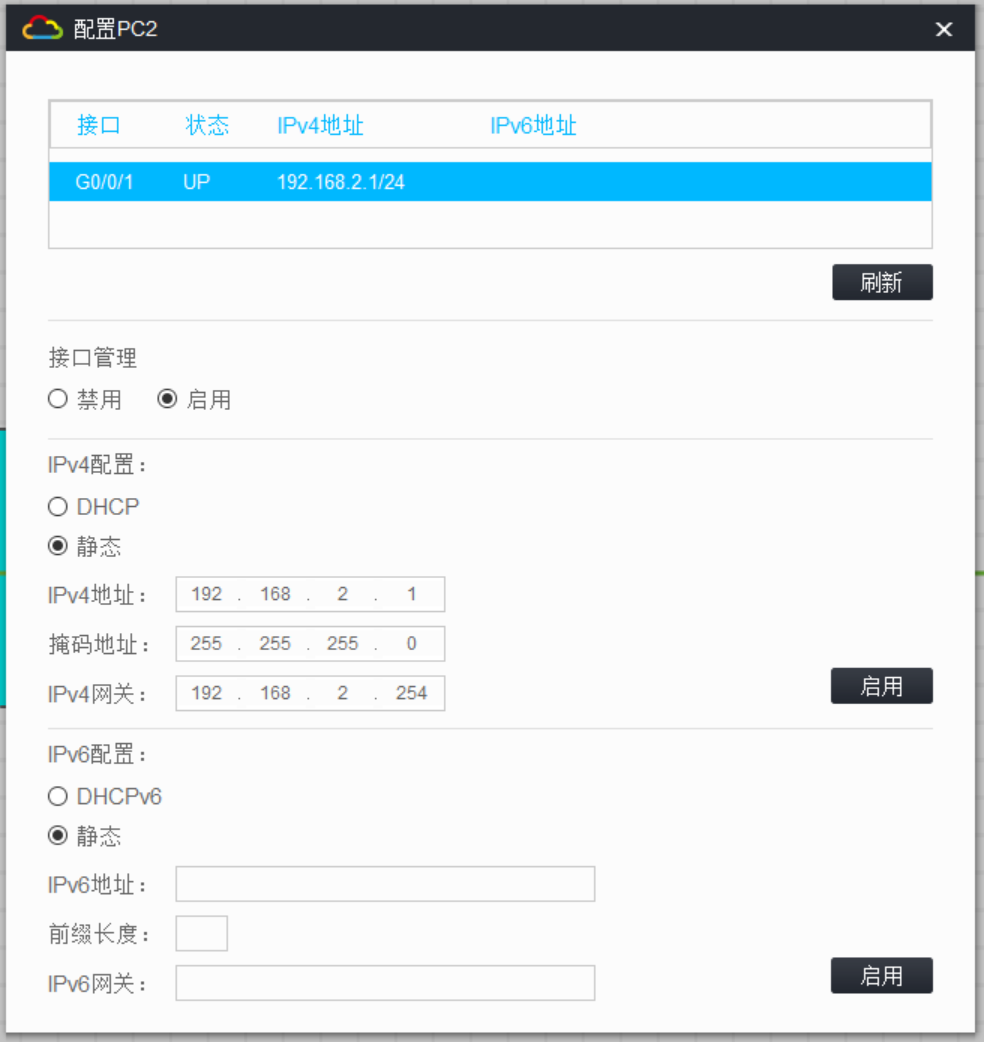
在 R1 和 R3 上配置默认路由连通公网
[R1]ip route-static 0.0.0.0 0 100.1.1.2
[R3]ip route-static 0.0.0.0 0 100.2.2.2
在 R1 和 R3 上配置 IPsec VPN,使两端私网可以互相访问
R1配置IPsec VPN
在R1上配置IKE提议
[R1]ike proposal 1 //创建IKE提议1
[R1-ike-proposal-1]encryption-algorithm aes-cbc-128 //加密算法为”aes-cbc-128“(默认”des-cbc“)
[R1-ike-proposal-1]authentication-method pre-share //验证方法为”预共享密钥“(默认)
[R1-ike-proposal-1]authentication-algorithm md5 //认证算法为”md5“(默认”sha“)
[R1-ike-proposal-1]sa duration 86400 //sa存活时间24小时(默认)
[R1-ike-proposal-1]dh group1 //密钥协商时采用768位的DH组(默认“group1”)
在R1上配置IKE预共享密钥
[R1]ike keychain R1-R3 //创建IKE钥匙
[R1-ike-keychain-R1-R3]pre-shared-key address 100.2.2.3 key simple admin@123 //与100.2.2.3使用密钥”admin@123“建立连接
在R1上配置IKE协议框架
[R1]ike profile R1-R3 //创建IKE协议框架R1-R3
[R1-ike-profile-R1-R3]exchange-mode main //配置协商模式为主模式(默认)
[R1-ike-profile-R1-R3]keychain R1-R3 //调用”ike keychain R1-R3“
[R1-ike-profile-R1-R3]proposal 1 //调用”IKE提议1“
[R1-ike-profile-R1-R3]local-identity address 100.1.1.1 //配置本地身份信息
[R1-ike-profile-R1-R3]match remote identity address 100.2.2.3 //配置匹配对端身份信息
在R1上配置IPsec安全提议
[R1]ipsec transform-set R1-R3 //创建IPsec安全提议(转换集)R1-R3
[R1-ipsec-transform-set-R1-R3]protocol esp //安全协议为”esp“(默认)
[R1-ipsec-transform-set-R1-R3]esp encryption-algorithm aes-cbc-128 //配置esp协议采用”aes-cbc-128“加密算法
[R1-ipsec-transform-set-R1-R3]esp authentication-algorithm md5 //配置esp协议采用”md5“认证算法
[R1-ipsec-transform-set-R1-R3]encapsulation-mode tunnel //IPsec工作模式为”隧道模式“(默认)
在R1上配置安全ACL
[R1]acl advanced 3000
[R1-acl-ipv4-adv-3000]rule permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
在R1上配置IPsec安全策略
[R1]ipsec policy R1-R3 1 isakmp //创建IKE协商参数的安全策略R1-R3,编号1
[R1-ipsec-policy-isakmp-R1-R3-1]security acl 3000 //调用ACL3000
[R1-ipsec-policy-isakmp-R1-R3-1]transform-set R1-R3 //调用IPsec安全提议R1-R3
[R1-ipsec-policy-isakmp-R1-R3-1]local-address 100.1.1.1 //配置IPsec隧道本地地址100.1.1.1
[R1-ipsec-policy-isakmp-R1-R3-1]remote-address 100.2.2.3 //配置IPsec隧道对端地址100.2.2.3
默认情况下IPsec SA基于时间的生存周期为3600s,基于流量的生存周期为1843200KB
在R1出接口上应用IPsec安全策略
[R1]interface GigabitEthernet 0/0
[R1-GigabitEthernet0/0]ipsec apply policy R1-R3
R3配置IPsec VPN
在R3上配置IKE提议
[R3]ike proposal 1
[R3-ike-proposal-1]encryption-algorithm aes-cbc-128 //加密算法为”aes-cbc-128“(默认”des-cbc“)
[R3-ike-proposal-1]authentication-method pre-share //验证方法为”预共享密钥“(默认)
[R3-ike-proposal-1]authentication-algorithm md5 //认证算法为”md5“(默认”sha“)
[R3-ike-proposal-1]sa duration 86400 //sa存活时间24小时(默认)
[R3-ike-proposal-1]dh group1 //密钥协商时采用768位的DH组(默认“group1”)
在R3上配置IKE预共享密钥
[R3]ike keychain R3-R1 //创建IKE钥匙
[R3-ike-keychain-R3-R1]pre-shared-key address 100.1.1.1 key simple admin@123 //与100.1.1.1使用密钥”admin@123“建立连接
在R3上配置IKE协议框架
[R3]ike profile R3-R1 //创建IKE协议框架R3-R1
[R3-ike-profile-R3-R1]exchange-mode main //配置协商模式为主模式(默认)
[R3-ike-profile-R3-R1]keychain R3-R1 //调用”ike keychain R3-R1“
[R3-ike-profile-R3-R1]proposal 1 //调用”IKE提议1“
[R3-ike-profile-R3-R1]local-identity address 100.2.2.3 //配置本地身份信息
[R3-ike-profile-R3-R1]match remote identity address 100.1.1.1 //配置匹配对端身份信息
在R3上配置IPsec安全提议
[R3]ipsec transform-set R3-R1 //创建IPsec安全提议(转换集)R3-R1
[R3-ipsec-transform-set-R3-R1]protocol esp //安全协议为”esp“(默认)
[R3-ipsec-transform-set-R3-R1]esp encryption-algorithm aes-cbc-128 //配置esp协议采用”aes-cbc-128“加密算法
[R3-ipsec-transform-set-R3-R1]esp authentication-algorithm md5 //配置esp协议采用”md5“认证算法
[R3-ipsec-transform-set-R3-R1]encapsulation-mode tunnel //IPsec工作模式为”隧道模式“(默认)v
在R3上配置安全ACL
[R3]acl advanced 3000
[R3-acl-ipv4-adv-3000]rule permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
在R3上配置IPsec安全策略
[R3]ipsec policy R3-R1 1 isakmp //创建IKE协商参数的安全策略R3-R1,编号1
[R3-ipsec-policy-isakmp-R3-R1-1]security acl 3000 //调用ACL3000
[R3-ipsec-policy-isakmp-R3-R1-1]transform-set R3-R1 //调用IPsec安全提议R3-R1
[R3-ipsec-policy-isakmp-R3-R1-1]local-address 100.2.2.3 //配置IPsec隧道本地地址100.2.2.3
[R3-ipsec-policy-isakmp-R3-R1-1]remote-address 100.1.1.1 //配置IPsec隧道对端地址100.1.1.1
默认情况下IPsec SA基于时间的生存周期为3600s,基于流量的生存周期为1843200KB
在R3出接口上应用IPsec安全策略
[R3]interface GigabitEthernet 0/0
[R3-GigabitEthernet0/0]ipsec apply policy R3-R1
实验验证
<H3C>ping 192.168.2.1
Ping 192.168.2.1 (192.168.2.1): 56 data bytes, press CTRL_C to break
Request time out
56 bytes from 192.168.2.1: icmp_seq=1 ttl=253 time=1.000 ms
56 bytes from 192.168.2.1: icmp_seq=2 ttl=253 time=2.000 ms
56 bytes from 192.168.2.1: icmp_seq=3 ttl=253 time=2.000 ms
56 bytes from 192.168.2.1: icmp_seq=4 ttl=253 time=2.000 ms
--- Ping statistics for 192.168.2.1 ---
5 packet(s) transmitted, 4 packet(s) received, 20.0% packet loss
round-trip min/avg/max/std-dev = 1.000/1.750/2.000/0.433 ms
通过抓包发现第一个数据包丢包原因为IPsec隧道处于协商状态
实验附件
通过百度网盘分享的文件:H3C IPsec+IKE 预共享密钥方法配置实验
链接:https://pan.baidu.com/s/19SwXdW9KK8LjCkftqIG78g?pwd=6ek4

























 1593
1593

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










