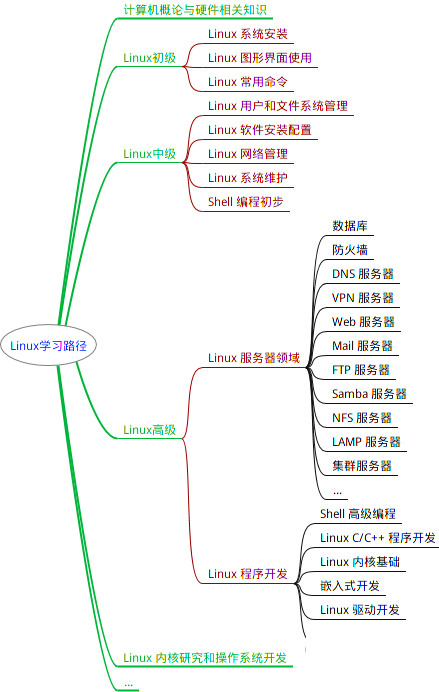
最全的Linux教程,Linux从入门到精通
======================
-
linux从入门到精通(第2版)
-
Linux系统移植
-
Linux驱动开发入门与实战
-
LINUX 系统移植 第2版
-
Linux开源网络全栈详解 从DPDK到OpenFlow

第一份《Linux从入门到精通》466页
====================
内容简介
====
本书是获得了很多读者好评的Linux经典畅销书**《Linux从入门到精通》的第2版**。本书第1版出版后曾经多次印刷,并被51CTO读书频道评为“最受读者喜爱的原创IT技术图书奖”。本书第﹖版以最新的Ubuntu 12.04为版本,循序渐进地向读者介绍了Linux 的基础应用、系统管理、网络应用、娱乐和办公、程序开发、服务器配置、系统安全等。本书附带1张光盘,内容为本书配套多媒体教学视频。另外,本书还为读者提供了大量的Linux学习资料和Ubuntu安装镜像文件,供读者免费下载。

本书适合广大Linux初中级用户、开源软件爱好者和大专院校的学生阅读,同时也非常适合准备从事Linux平台开发的各类人员。
需要《Linux入门到精通》、《linux系统移植》、《Linux驱动开发入门实战》、《Linux开源网络全栈》电子书籍及教程的工程师朋友们劳烦您转发+评论
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: Set /proc/self/oom_score_adj to 0
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: rexec start in 5 out 5 newsock 5 pipe 7 sock 8
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: inetd sockets after dupping: 3, 3
Sep 18 19:22:18 pam-dev21 sshd[9223]: Connection from 10...100 port 42510 on 10...21 port 22
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: Client protocol version 2.0; client software version OpenSSH_7.4
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: match: OpenSSH_7.4 pat OpenSSH* compat 0x04000000
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: Local version string SSH-2.0-OpenSSH_7.4
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: Enabling compatibility mode for protocol 2.0
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: SELinux support enabled [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: permanently_set_uid: 74/74 [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: list_hostkey_types: ssh-rsa,rsa-sha2-512,rsa-sha2-256,ecdsa-sha2-nistp256,ssh-ed25519 [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: SSH2_MSG_KEXINIT sent [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: SSH2_MSG_KEXINIT received [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: kex: algorithm: diffie-hellman-group-exchange-sha256 [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: kex: host key algorithm: ecdsa-sha2-nistp256 [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: compression: none [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: compression: none [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: kex: diffie-hellman-group-exchange-sha256 need=64 dh_need=64 [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: kex: diffie-hellman-group-exchange-sha256 need=64 dh_need=64 [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: expecting SSH2_MSG_KEX_DH_GEX_REQUEST [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: SSH2_MSG_KEX_DH_GEX_REQUEST received [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: SSH2_MSG_KEX_DH_GEX_GROUP sent [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: expecting SSH2_MSG_KEX_DH_GEX_INIT [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: rekey after 134217728 blocks [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: SSH2_MSG_NEWKEYS sent [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: expecting SSH2_MSG_NEWKEYS [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: SSH2_MSG_NEWKEYS received [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: rekey after 134217728 blocks [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: KEX done [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: userauth-request for user root service ssh-connection method none [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: attempt 0 failures 0 [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: PAM: initializing for “root”
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: PAM: setting PAM_RHOST to “pam-server01.com”
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: PAM: setting PAM_TTY to “ssh”
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: userauth-request for user root service ssh-connection method publickey [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: attempt 1 failures 0 [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: userauth_pubkey: test whether pkalg/pkblob are acceptable for RSA SHA256:z2sV4X/ioEmUAMluJM2QB0JMSzwqIA26wpHBZ3O0Yuk [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: temporarily_use_uid: 0/0 (e=0/0)
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: trying public key file /root/.ssh/authorized_keys
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: fd 4 clearing O_NONBLOCK
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: matching key found: file /root/.ssh/authorized_keys, line 2 RSA SHA256:z2sV4X/ioEmUAMluJM2QB0JMSzwqIA26wpHBZ3O0Yuk
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: restore_uid: 0/0
Sep 18 19:22:18 pam-dev21 sshd[9223]: Postponed publickey for root from 10...100 port 42510 ssh2 [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: userauth-request for user root service ssh-connection method publickey [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: attempt 2 failures 0 [preauth]
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: temporarily_use_uid: 0/0 (e=0/0)
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: trying public key file /root/.ssh/authorized_keys
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: fd 4 clearing O_NONBLOCK
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: matching key found: file /root/.ssh/authorized_keys, line 2 RSA SHA256:z2sV4X/ioEmUAMluJM2QB0JMSzwqIA26wpHBZ3O0Yuk
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: restore_uid: 0/0
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: do_pam_account: called
Sep 18 19:22:18 pam-dev21 sshd[9223]: Accepted publickey for root from 10...100 port 42510 ssh2: RSA SHA256:z2sV4X/ioEmUAMluJM2QB0JMSzwqIA26wpHBZ3O0Yuk
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: monitor_child_preauth: root has been authenticated by privileged process
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: monitor_read_log: child log fd closed
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: temporarily_use_uid: 0/0 (e=0/0)
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: ssh_gssapi_storecreds: Not a GSSAPI mechanism
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: restore_uid: 0/0
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: SELinux support enabled
Sep 18 19:22:18 pam-dev21 sshd[9223]: debug1: PAM: establishing credentials
### 日志概览
日志来源于名为`pam-dev21`的服务器,该服务器使用了OpenSSH 7.4版本。客户端连接来自IP地址`10.76.77.100`,端口`42510`。
### 关键步骤解析
#### 进程和资源准备
* **Forked child 9223**: SSHD(SSH Daemon)进程fork了一个子进程(PID为9223)来处理新的SSH连接。
#### 连接和版本匹配
* **Connection from 10.\*.\*.100**: 记录了客户端的IP地址和端口。
* **Client protocol version 2.0**: 客户端使用SSH协议版本2.0。
* **Local version string SSH-2.0-OpenSSH\_7.4**: 服务器端的SSH版本信息。
#### 密钥交换(Key Exchange)
* **SSH2\_MSG\_KEXINIT sent/received**: 密钥交换初始化信息已发送和接收。
* **kex: algorithm: diffie-hellman-group-exchange-sha256**: 使用Diffie-Hellman算法和SHA-256进行密钥交换。
* **kex: host key algorithm: ecdsa-sha2-nistp256**: 主机密钥使用ECDSA和SHA-256。
**网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。**
**[需要这份系统化的资料的朋友,可以点击这里获取!](https://bbs.csdn.net/forums/4f45ff00ff254613a03fab5e56a57acb)**
**一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!**























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








