1. 背景知识
1)2003年,[MRK] S. Micali,M.-O. Rabin和J. Kilian的论文《Zero-Knowledge Sets》中首次提出了zero-knowledge sets(ZKS) primitive:
允许prover commit to a secret finite set
S
S
S so as to be able to prove statements such as
x
∈
S
x\in S
x∈S or
x
∉
S
x\notin S
x∈/S without revealing anything else on
S
S
S, not even its size。同时指出,zero-knowledge elementary databases(ZK-EDB)可概括为:zero-knowledge sets in that each element
x
x
x has an associated value
D
(
x
)
D(x)
D(x) in the committed database。Micali在该论文中构建了一个ZK-EDB based on the discrete logarithm assumption 和 use an extension of Pedersen’s trapdoor commitment[23],有trusted setup 需构建CRS。
2)2005年,Chase等人的论文《Mercurial Commitments with Applications to Zero-Knowledge Sets》中指出,ZKS protocol可由mercurial commitment构成。[MRK]的构建是由mercurial commitments和a Merkle tree组成,Merkle tree的每个internal node 包含a mercurial commitment to its two children。
博客 水银承诺mercurial commitment 中有介绍mercurial commitment知识。
mercurial commitment是binding 属性更灵活的commitment,分为:
- hard commitment:可hard/soft-opened to only one message。可支持软打开和硬打开,且软打开的值应与硬打开的值一致。
- soft commitment:可soft-opened to any arbitrary message without committing the sender to a specific one。仅支持软打开,不支持硬打开。
hard commitment和soft commitment应是computationally indistinguishable。
3)2008年,Catalano等人[CFM]论文《Zero-Knowledge Sets with Short Proofs》中指出:
之前构建的zero-knowledge database[21,10] 都是基于a binary Merkle tree of height
O
(
λ
)
O(\lambda)
O(λ),其中
λ
\lambda
λ为security parameter。Each internal node contains a mercurial commitment to (a hash value of) its two children whereas each leaf node is a mercurial commitment to a database entry. A proof of membership for the entry x consists of a sequence of hard openings for commitments appearing in nodes on the path from leaf x to the root. Proofs of non-membership proceed similarly but rather use soft openings along the path. 这种方式生成的proof经常是过长的。
将binary扩展为
q
q
q,2008年 Catalano等人[CFM]论文《Zero-Knowledge Sets with Short Proofs》 提出了trapdoor
q
q
q-mercurial commitment(qTMC)的概念,允许一次commit to a vector of
q
q
q messages at once,且open时可open指定位置的message,不需要将
q
q
q个message全部reveal。该方式构建的soft commitment openings仅需一个group element,从而大幅缩短了non-membership proof的长度;但是hard openings为
O
(
q
)
O(q)
O(q) elements,从而membership proof的长度
O
(
λ
⋅
q
/
log
(
q
)
)
O(\lambda\cdot q/\log(q))
O(λ⋅q/log(q))比non-membership proof的长度要长很多。
4)本论文,2010年,Benoît Libert和Moti Yung 的论文《Concise Mercurial Vector Commitments and Independent Zero-Knowledge Sets with Short Proofs》在[CFM] qTMC的基础上,提出:
-
a concise mercurial vector commitment,具有如下特性:
(1)hard and soft position-wise openings both have constant size(independent of q q q)。
(2)the committer can hard-open the commitment at position i ∈ { 1 , ⋯ , q } i\in\{1,\cdots,q\} i∈{1,⋯,q} without revealing anything on messages at other positions in the vector。
(3)membership proof和non-membership proof的长度均较短, O ( λ / log ( q ) ) O(\lambda/\log(q)) O(λ/log(q))。取 q = 128 q=128 q=128,proof可不超过2KB。 -
可转化为concise multi-trapdoor qTMC scheme,以支持构建independent zero-knowledge databases,从而实现ZK-EDB的independence和short proof。
1.1 Complexity assumption
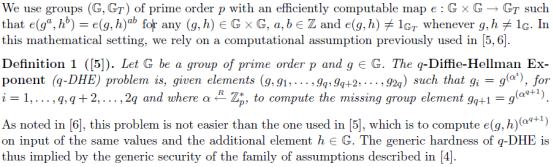
基于的假设为
q
q
q-Diffie-Hellman Exponent (q-DHE):已知
(
g
,
g
α
,
⋯
,
g
α
q
,
g
α
q
+
2
,
⋯
,
g
α
2
q
)
(g,g^{\alpha},\cdots,g^{\alpha^q},g^{\alpha^{q+2}},\cdots,g^{\alpha^{2q}})
(g,gα,⋯,gαq,gαq+2,⋯,gα2q),计算
g
α
q
+
1
g^{\alpha^{q+1}}
gαq+1的难度很高。
1.2 Trapdoor q q q-Mercurial Commitment
Trapdoor q q q-Mercurial Commitment 由一系列算法组成(qKeygen, qHCom, qHOpen, qHVer, qSCom, qSOpen, qSVer, qFake, qHEquiv, qSEquiv)。
-
qKeygen( λ , q \lambda, q λ,q):基于security参数 λ \lambda λ和单次commit支持的消息数 q q q,输出为public/private keys ( p k , t k ) (pk,tk) (pk,tk)。
-
qHCom p k _{pk} pk( m 1 , ⋯ , m q m_1,\cdots,m_q m1,⋯,mq):基于public key p k pk pk,输出hard commitment C C C 和 辅助状态state信息 a u x aux aux。
-
qHOpen p k _{pk} pk( m , i , a u x m,i,aux m,i,aux):为hard opening 算法。Given a pair ( C , a u x ) = (C,aux)= (C,aux)=qHCom p k _{pk} pk( m q , ⋯ , m q m_q,\cdots,m_q mq,⋯,mq),it outputs a hard de-commitment π \pi π of C C C w.r.t. position i i i if m = m i m=m_i m=mi. If m ≠ m i m\neq m_i m=mi, it returns ⊥ \perp ⊥.
-
qHVer p k _{pk} pk( m , i , C , π m,i,C,\pi m,i,C,π):为hard verification算法。若 π \pi π gives evidence that C C C is a commitment to a sequence ( m 1 , ⋯ , m q ) (m_1,\cdots,m_q) (m1,⋯,mq) such that m i = i m_i=i mi=i,则输出 1 1 1,否则输出 0 0 0。
-
qSCom p k _{pk} pk():为probabilistic 算法用于生成soft commitment和辅助信息 a u x aux aux。Such a commitment is not associated with a specific sequence of messages。
-
qSOpen p k _{pk} pk( m , i , f l a g , a u x m,i,flag,aux m,i,flag,aux):生成一个soft de-commitment τ \tau τ of C C C to the message m m m at position i i i。 f l a g ∈ { H , S } flag\in \{\mathbb{H},\mathbb{S}\} flag∈{H,S} 变量代表辅助state信息 a u x aux aux对应为hard commitment ( C , a u x ) = (C,aux)= (C,aux)=qHCom p k _{pk} pk( m 1 , ⋯ , m q m_1,\cdots,m_q m1,⋯,mq) 还是 soft commitment ( C , a u x ) = (C, aux)= (C,aux)=qSCom p k _{pk} pk()。若 f l a g = H 且 m ≠ m i flag=\mathbb{H}且m\neq m_i flag=H且m=mi,则该算法返回错误信息 ⊥ \perp ⊥。
-
qSVer p k _{pk} pk( m , i , C , τ m,i,C,\tau m,i,C,τ):returns 1 1 1 if τ \tau τ is a valid soft de-commitment of C C C to m m m at position i i i and 0 0 0 otherwise. If τ \tau τ is valid and C C C is a hard commitment, its hard opening must be to m m m at index i i i。
-
qFake p k , t k _{pk,tk} pk,tk():为随机算法,将trapdoor t k tk tk 作为输入,输出为a q q q-fake commitment C C C 和辅助信息 a u x aux aux。 C C C不与任何消息绑定。The q q q-fake commitment C C C is similar to a soft de-commitment with the difference that it can be hard-opened using the trapdoor t k tk tk。
-
qHEquiv p k , t k _{pk,tk} pk,tk( m 1 , ⋯ , m q , i , a u x m_1,\cdots,m_q,i,aux m1,⋯,mq,i,aux):为 non-adaptive hard equivocation algorithm. Given ( C , a u x ) = (C,aux)= (C,aux)=qFake p k , t k _{pk,tk} pk,tk(),生成a hard de-commitment π \pi π for C C C at the i i i-th position of the sequence ( m 1 , ⋯ , m q ) (m_1,\cdots,m_q) (m1,⋯,mq)。 该算法为non-adaptive是因其要求the sequence of messages必须是确定的 be determined once-and-for-all before the execution of qHEquiv。
-
qSEquiv p k , t k _{pk,tk} pk,tk( m , i , a u x m,i,aux m,i,aux):为soft equivocation algorithm。Given ( C , a u x ) = (C,aux)= (C,aux)=qFake p k , t k _{pk,tk} pk,tk()中的辅助信息 a u x aux aux,it creates a soft de-commitment τ \tau τ to m m m at position i i i。
Standard trapdoor mercurial commitment可认为是
q
=
1
q=1
q=1的qTMC特例。



Equivocation含糊其辞:
使得adversary无法区分真实的commitment/de-commitment和基于trapdoor
t
k
tk
tk伪造的commitment/de-commitment。

1.3 Zero-Knowledge Sets and Databases
An elementary database
D
D
D (EDB) is a set of pairs
(
x
,
y
)
⊂
{
0
,
1
}
∗
×
{
0
,
1
}
∗
(x,y) \subset \{0,1\}^{*}\times\{0,1\}^{*}
(x,y)⊂{0,1}∗×{0,1}∗,其中
x
x
x为key,
y
y
y为相应的value。
A zero-knowledge EDB要求可提供“
x
∈
[
D
]
a
n
d
y
=
D
(
x
)
x\in [D]\ and\ y=D(x)
x∈[D] and y=D(x) is the associated value”或“x\notin [D]”的相应证明 without revealing any further information on
D
D
D (not even the cardinality of [
D
D
D])。
Zero-knowledge sets可认为是所有value值均为 1 1 1的ZK-EDB的特例。
EDB scheme由(CRS-Gen,P1,P2,V)算法组成:

2. Concise qTMC Scheme
本文构建的concise qTMC scheme是基于Camenisch等人2009年论文《An Accumulator Based on Bilinear Maps and Efficient Revocation for Anonymous Credentials》的accumulator累加器思路(该思路又是受Boneh等人2005年论文《Collusion Resistant Broadcast Encryption with Short Ciphertexts and Private Keys》启发)。
Camenisch等人2009年论文《An Accumulator Based on Bilinear Maps and Efficient Revocation for Anonymous Credentials》中的思路为:
public key:
(
g
,
g
1
,
⋯
,
g
q
,
g
q
+
2
,
⋯
,
g
2
q
)
(g,g_1,\cdots,g_q,g_{q+2},\cdots,g_{2q})
(g,g1,⋯,gq,gq+2,⋯,g2q),其中
g
i
=
g
α
i
g_i=g^{\alpha^i}
gi=gαi
待累加元素:
ν
⊆
{
1
,
⋯
,
q
}
\nu \subseteq \{1,\cdots,q\}
ν⊆{1,⋯,q}
累加算法:
V
=
∏
j
∈
ν
g
q
+
1
−
j
=
g
1
g
2
⋯
g
q
=
g
α
+
α
2
+
⋯
+
α
q
V=\prod_{j\in\nu}g_{q+1-j}=g_1g_2\cdots g_q=g^{\alpha+\alpha^2+\cdots +\alpha^q}
V=∏j∈νgq+1−j=g1g2⋯gq=gα+α2+⋯+αq
待证明:
i
∈
ν
i \in \nu
i∈ν
Prover提供的证明可为:
W
i
=
∏
j
∈
ν
∖
i
g
q
+
1
−
j
+
i
=
V
α
i
/
g
q
+
1
W_i=\prod_{j\in\nu\setminus i}g_{q+1-j+i}=V^{\alpha^i}/{g_{q+1}}
Wi=∏j∈ν∖igq+1−j+i=Vαi/gq+1
Verifier验证:
e
(
g
i
,
V
)
=
e
(
g
,
W
i
)
⋅
e
(
g
1
,
g
q
)
e(g_i,V)=e(g,W_i)\cdot e(g_1,g_q)
e(gi,V)=e(g,Wi)⋅e(g1,gq)即可。
本论文中,为hiding属性,增加了随机数 γ ∈ Z p \gamma \in \mathbb{Z}_p γ∈Zp,同时为使累加的消息 m i ∈ Z p ∗ m_i\in \mathbb{Z}_p^{*} mi∈Zp∗ 对位置敏感(in a position-sensitive manner) Benoît Libert做了如下改进:
- commit to ( m 1 , ⋯ , m q ) (m_1,\cdots,m_q) (m1,⋯,mq)表示为 V = g γ ⋅ ∏ j = 1 q g q + 1 − j m j V=g^{\gamma}\cdot\prod_{j=1}^{q}g_{q+1-j}^{m_j} V=gγ⋅∏j=1qgq+1−jmj 【该commitment在q-DHE assumption下具有binding属性,若q-DHE assumption不成立,则adversary可produce two distinct openings of V V V at position i i i。同时,也可将该commitment看成是trapdoor commitment,其trapdoor key为 g q + 1 = g α q + 1 g_{q+1}=g^{\alpha^{q+1}} gq+1=gαq+1,拥有该trapdoor key 的人可open 该commitment为任意值。】
- 为证明 m i m_i mi为 the i i i-th committed message,Prover提供: W i = g i γ ⋅ ∏ j = 1 , j ≠ i q g q + 1 − j + i m j W_i=g_i^{\gamma}\cdot \prod_{j=1,j\neq i}^{q}g_{q+1-j+i}^{m_j} Wi=giγ⋅∏j=1,j=iqgq+1−j+imj
- Verifier验证: e ( g i , V ) = e ( g , W i ) ⋅ e ( g 1 , g q ) m i e(g_i,V)=e(g,W_i)\cdot e(g_1,g_q)^{m_i} e(gi,V)=e(g,Wi)⋅e(g1,gq)mi即可。
- 为实现mercurial commitment 具有更灵活的binding属性,若调整Verifier的验证公式为 e ( g i , V ) = e ( g 1 , W i ) ⋅ e ( g 1 , g q ) m i e(g_i,V)=e(g_1,W_i)\cdot e(g_1,g_q)^{m_i} e(gi,V)=e(g1,Wi)⋅e(g1,gq)mi则相应的binding属性将消失。基本思路为,Prover 的commitment不再只是 V V V,而是 ( C , V ) (C,V) (C,V),其中 θ ∈ Z p \theta \in\mathbb{Z}_p θ∈Zp,当 C = g θ C=g^{\theta} C=gθ时,为hard commitment;当 C = g 1 θ C=g_1^{\theta} C=g1θ时,为soft commitment。Verifier验证的公式为: e ( g i , V ) = e ( C , W i ) ⋅ e ( g 1 , g q ) m i e(g_i,V)=e(C,W_i)\cdot e(g_1,g_q)^{m_i} e(gi,V)=e(C,Wi)⋅e(g1,gq)mi
详细的mercurial commitment流程如下:

以上使用的是对称pairing,若使用非对称pairing,相应的细节调整为:
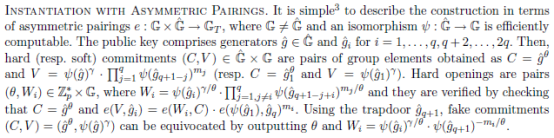
3. 基于qTMC构建ZK-EDB
2008年Catalano等人[CFM]论文《Zero-Knowledge Sets with Short Proofs》中构建ZK-EDB的思路可参见Camenisch等人2009年论文《An Accumulator Based on Bilinear Maps and Efficient Revocation for Anonymous Credentials》的附录B。
基本的思路为:对于
q
q
q-ary tree of height
h
h
h,将每个key
x
x
x赋值给tree的leaf,理论上,该EBD的size 上限为
q
h
q^h
qh。
本论文在次基础上增加了independent zero-knowledge的要求,即 adversaries be unable to correlate their database to those created by honest provers.






















 1809
1809











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








