1. Discrete logarithm problem
Let g g g为 a known element of prime order r r r in a group (with group operation written multiplicatively). Let G = < g > G=<g> G=<g> be the group generated by g g g.
常用的group选择有:
- multiplicative group of a finite field;
- algebraic torus over a finite field;
- elliptic curve over a finite field;
- divisor class group of a curve over a finite field。
Discrete logarithm problem常用假设有:
-
DLP: discrete logarithm problem。常用于Schnorr signatures, DSA signatures。
已知 h ∈ G h\in G h∈G,找到 x x x使得 h = g x h=g^x h=gx。 -
CDH: computational Diffie-Hellman problem。常用于 Diffie-Hellman key exchange and variants, Elgamal encryption and variants, BLS signatures and variants。
已知 g a , g b ∈ G g^a,g^b\in G ga,gb∈G,计算 g a b g^{ab} gab。 -
SDH: static Diffie-Hellman problem。
Fix g , g a ∈ G g,g^a\in G g,ga∈G. Given h ∈ G h\in G h∈G,计算 h a h^a ha。 -
gap-CDH: Gap Diffie-Hellman problem。常用于 ECIES proof in the Random Oracle Model, Chaum undeniable signature。
已知 g a , g b ∈ G g^a,g^b\in G ga,gb∈G,计算 g a b g^{ab} gab,when the algorithm has access to an oracle which solves the DDH problem。 -
DDH: decision Diffie-Hellman problem。常用于 Diffie-Hellman key exchange and variants, Elgamal encryption and variants.
已知 g a , g b , h ∈ G g^a,g^b,h\in G ga,gb,h∈G,判断 h = g a b h=g^{ab} h=gab是否成立? -
Strong-DDH: strong decision Diffie-Hellman problem
已知 g , g a , g b , g b − 1 , h ∈ G g,g^a,g^b,g^{b^{-1}},h\in G g,ga,gb,gb−1,h∈G,判断 h = g a b h=g^{ab} h=gab是否成立? -
sDDH: skewed decision Diffie-Hellman problem。
Let f f f 为任意的uninvertible function with domain Z r \mathbb{Z}_r Zr。已知 f ( a ) , g b , h ∈ G f(a),g^b,h\in G f(a),gb,h∈G,判断 h = g a b h=g^{ab} h=gab是否成立? -
PDDH: parallel decision Diffie-Hellman problem。
已知 g x 1 , ⋯ , g x n , h 1 , ⋯ , h n ∈ G g^{x_1},\cdots,g^{x_n},h_1,\cdots,h_n\in G gx1,⋯,gxn,h1,⋯,hn∈G,判断 h 1 = g x 1 x 2 , ⋯ , h n − 1 = g x n − 1 x n , h n = g x n x 1 h_1=g^{x_1x_2},\cdots,h_{n-1}=g^{x_{n-1}x_n},h_n=g^{x_nx_1} h1=gx1x2,⋯,hn−1=gxn−1xn,hn=gxnx1是否成立? -
Square-DH: Square Diffie-Hellman problem. The best known algorithm for Square-DH is to actually solve the DLP.
已知 g a ∈ G g^a\in G ga∈G,计算 g a 2 g^{a^2} ga2。 -
l-DHI: l-Diffie-Hellman inversion problem. The best known algorithm for l-DHI is to actually solve the DHP.
已知 g a , g a 2 , ⋯ , g a l ∈ G g^a,g^{a^2},\cdots,g^{a^l}\in G ga,ga2,⋯,gal∈G,计算 g 1 / a g^{1/a} g1/a。 -
l-DDHI: l-Decisional Diffie-Hellman inversion problem
已知 g a , g a 2 , ⋯ , g a l , v ∈ G g^a,g^{a^2},\cdots,g^{a^l},v\in G ga,ga2,⋯,gal,v∈G,判断 v = g 1 / a v=g^{1/a} v=g1/a是否成立? -
REPRESENTATION: Representation problem. The best known algorithm for REPRESENTATION is to solve the DLP.
已知 g 1 , ⋯ , g k , h ∈ G g_1,\cdots,g_k,h\in G g1,⋯,gk,h∈G,找到 a 1 , ⋯ , a k a_1,\cdots,a_k a1,⋯,ak使得 h = g 1 a 1 ⋯ g k a k h=g_1^{a_1}\cdots g_k^{a_k} h=g1a1⋯gkak成立。 -
LRSW: LRSW Problem. The best known algorithm for LRSW is to solve the DLP.
已知 g , g x , g y g,g^x,g^y g,gx,gy,已知 oracle O O O(输入为 s s s,其选择一个随机值 a = g z a=g^z a=gz,然后其输出为 ( a , a s y , a x + s x y ) (a,a^{sy},a^{x+sxy}) (a,asy,ax+sxy)),对于任意的 t t t(not one of the 输入 s s s)和 b ≠ 1 b\neq 1 b=1值 计算 ( t , b , b t y , b x + t x y ) (t,b,b^{ty},b^{x+txy}) (t,b,bty,bx+txy)。 -
Linear: Linear problem。The best known algorithm for Linear is to solve the DLP。
已知 g a , g b , g a c , g b d ∈ G g^a,g^{b},g^{ac},g^{bd}\in G ga,gb,gac,gbd∈G,计算 g c + d g^{c+d} gc+d。 -
D-Linear1: Decision Linear problem (version 1)
已知 g a , g b , g a c , g b d , v ∈ G g^a,g^{b},g^{ac},g^{bd},v\in G ga,gb,gac,gbd,v∈G,判断 v = g c + d v=g^{c+d} v=gc+d是否成立? -
l-SDH: l-Strong Diffie-Hellman problem
已知 g a , g a 2 , ⋯ , g a l ∈ G g^a,g^{a^2},\cdots,g^{a^l}\in G ga,ga2,⋯,gal∈G,找到 w ∈ F q w\in F_q w∈Fq并计算 g 1 / ( a + w ) g^{1/(a+w)} g1/(a+w)。 -
c-DLSE: Discrete Logarithm with Short Exponents。The best known algorithm for the c-DLSE is to use the baby-step-giant-step or Pollard kangaroo algorithms for solving the DLP in a short interval. 常用于
Gennaro pseudorandom generator。
Let G = Z p ∗ G=\mathbb{Z}_p^* G=Zp∗ 其中 p − 1 = 2 q p-1=2q p−1=2q, p , q p,q p,q均为primes,let c c c为integer。已知 g x m o d p g^x \mod p gxmodp 且 0 ≤ x ≤ 2 c 0\leq x\leq 2^c 0≤x≤2c,求解相应的 x x x值。 -
CONF: (conference-key sharing scheme)。常用于Okamoto’s conference-key sharing scheme。
已知 g a , g b , g a b ∈ G g^a,g^b,g^{ab}\in G ga,gb,gab∈G,计算 g b g^{b} gb。 -
3PASS: 3-Pass Message Transmission Scheme。常用于Shamir’s 3-pass message transmission scheme。
已知 A , B , C ∈ G A,B,C\in G A,B,C∈G,找到相应的 s s s使得 A = s a , B = s b , C = s a b A=s^a,B=s^b,C=s^{ab} A=sa,B=sb,C=sab成立。 -
LUCAS: Lucas Problem。
已知 p , z ∈ < V t ( m ) > p,z\in<V_t(m)> p,z∈<Vt(m)>,找到相应的 x x x,使得 V x ( m ) = z V_x(m)=z Vx(m)=z成立。其中 V t ( m ) V_t(m) Vt(m)的定义为: V 0 ( m ) = 2 , V 1 ( m ) = m , V t ( m ) = m V t − 1 ( m ) − V t − 2 ( m ) 。 V_0(m)=2,V_1(m)=m,V_t(m)=mV_{t-1}(m)-V_{t-2}(m)。 V0(m)=2,V1(m)=m,Vt(m)=mVt−1(m)−Vt−2(m)。 -
XLP: x-Logarithm Problem。
对于Elliptic curve E ( F q ) E(\mathbb{F}_q) E(Fq)上的任意一点 P = ( x , y ) ∈ F q 2 P=(x,y)\in\mathbb{F}_q^2 P=(x,y)∈Fq2,将 x ( P ) = x ˉ x(P)=\bar{x} x(P)=xˉ 表示为 P P P点$ X坐标的二进制表示。对任意的group element g a g^a ga, x = x ( g a ) x=x(g^a) x=x(ga),是否能区分 g a g^a ga和 g x g^x gx? -
MDHP: Matching Diffie-Hellman Problem。常用于E-Cash。
Let g g g be a generator of group G G G having order q q q,let a 0 , b 0 , a 1 , b 1 ∈ Z q a_0,b_0,a_1,b_1\in\mathbb{Z}_q a0,b0,a1,b1∈Zq and r ∈ R { 0 , 1 } r\in_R\{0,1\} r∈R{0,1}。已知 ( g a 0 , g a 0 b 0 , g a 1 , g a 1 b 1 ) (g^{a_0},g^{a_0b_0},g^{a_1},g^{a_1b_1}) (ga0,ga0b0,ga1,ga1b1)和 ( g b r , g b 1 − r ) (g^{b_r},g^{b_{1-r}}) (gbr,gb1−r),找到相应的 r r r。 -
DDLP: Double Discrete Logarithm Problem。常用于Public verifiable secret sharing。
Let p , q p,q p,q 为素数且 q = ( p − 1 ) / 2 q=(p-1)/2 q=(p−1)/2,设置 G G G为group of order p p p with generator g g g, h ∈ Z p ∗ h\in\mathbb{Z}_p^* h∈Zp∗为an element of order q q q。已知 g , h , a = g ( h x ) g,h,a=g^{(h^x)} g,h,a=g(hx),求解 x x x。 -
rootDLP: Root of Discrete Logarithm Problem。常用于Camenisch and Stadler group signature scheme。
已知group generator g g g, positive integer e e e 和 a ∈ G a\in G a∈G,计算 x x x使得 a = g ( x e ) a=g^{(x^e)} a=g(xe)成立。 -
n-M-DDH: Multiple Decision Diffie-Hellman Problem。常用于 Group key exchange。
Let n ≥ 2 n\geq 2 n≥2, D = ( g x 1 , ⋯ , g x n , { g x i x j } 1 ≤ i < j ≤ n ) D=(g^{x_1},\cdots,g^{x_n},\{g^{x_ix_j}\}_{1\leq i< j\leq n}) D=(gx1,⋯,gxn,{gxixj}1≤i<j≤n) 其中 x 1 , ⋯ , x n ∈ Z r x_1,\cdots,x_n\in\mathbb{Z}_r x1,⋯,xn∈Zr为随机值; D r a n d o m = ( g 1 , ⋯ , g n , { g i j } 1 ≤ i < j ≤ n ) D_{random}=(g_1,\cdots,g_n,\{g_{ij}\}_{1\leq i<j\leq n}) Drandom=(g1,⋯,gn,{gij}1≤i<j≤n)为a random tuple in G G G。很难区分 D D D和 D r a n d o m D_{random} Drandom。 -
l-HENSEL-DLP: l-Hensel Discrete Logarithm Problem。
Let G G G为a subgroup or prime order r r r in Z p ∗ \mathbb{Z}_p^* Zp∗,其中 p p p为a prime with polynomial binary length;Let 1 < g < p 1<g<p 1<g<p be an integer满足 g r ≡ 1 ( m o d p l − 1 ) , g r ≢ 1 m o d p l ) g^r\equiv 1(\mod p^{l-1}),g^r\not\equiv 1\mod p^l) gr≡1(modpl−1),gr≡1modpl),其中 l > 1 且 为 整 数 l>1且为整数 l>1且为整数。已知 g x m o d p g^x \mod p gxmodp, x x x为 [ 1 , r − 1 ] [1,r-1] [1,r−1]范围内的随机数,计算 g x m o d p l g^x \mod p^l gxmodpl。 -
DLP(Inn(G)): Discrete Logarithm Problem over Inner Automorphism Group。常用于MOR Public Key Cryptosystem。
已知 ϕ , ϕ s ∈ I n n ( G ) \phi,\phi^s\in Inn(G) ϕ,ϕs∈Inn(G) for s ∈ Z s\in\mathbb{Z} s∈Z,求解 s ( m o d ∣ ϕ ∣ ) s(\mod |\phi|) s(mod∣ϕ∣)。 -
IE: Inverse Exponent。
为l-DHI (l-Diffie-Hellman inversion problem) l = 1 l=1 l=1的特例情况。 -
TDH: The Twin Diffie-Hellman Assumption。
Let G G G 为 a cyclic group with generator g g g,and of prime order q q q。定义 d h ( X , Y ) = Z dh(X,Y)=Z dh(X,Y)=Z,其中 X = g x , Y = g y , Z = g x y X=g^x,Y=g^y,Z=g^{xy} X=gx,Y=gy,Z=gxy。定义twin DH function 2 d h : G 3 → G 2 ( X 1 , X 2 , Y ) → ( d h ( X 1 , Y ) , d h ( X 2 , Y ) ) 2dh: G^3\rightarrow G^2\ (X_1,X_2,Y)\rightarrow (dh(X_1,Y),dh(X_2,Y)) 2dh:G3→G2 (X1,X2,Y)→(dh(X1,Y),dh(X2,Y))。定义相应的twin DH predicate为: 2 d h p ( X 1 , X 2 , Y ^ , Z ^ 1 , Z ^ 2 ) = 1 i f f 2 d h ( X 1 , X 2 , Y ^ ) = ( Z ^ 1 , Z ^ 2 ) 2dhp(X_1,X_2,\hat{Y},\hat{Z}_1,\hat{Z}_2)=1\ iff\ 2dh(X_1,X_2,\hat{Y})=(\hat{Z}_1,\hat{Z}_2) 2dhp(X1,X2,Y^,Z^1,Z^2)=1 iff 2dh(X1,X2,Y^)=(Z^1,Z^2)。
twin DH assumption是指:已知random X 1 , X 2 , Y ∈ G X_1,X_2,Y\in G X1,X2,Y∈G,计算 2 d h ( X 1 , X 2 , Y ) 2dh(X_1,X_2,Y) 2dh(X1,X2,Y)很难。
strong twin DH assumption是指:已知 X 1 , X 2 , Y ∈ G X_1,X_2,Y\in G X1,X2,Y∈G along with access to a decision oracle for the predicate 2 d h p ( X 1 , X 2 , ⋅ , ⋅ , ⋅ ) 2dhp(X_1,X_2,\cdot,\cdot,\cdot) 2dhp(X1,X2,⋅,⋅,⋅) which on input ( Y ^ , Z ^ 1 , Z ^ 2 ) (\hat{Y},\hat{Z}_1,\hat{Z}_2) (Y^,Z^1,Z^2) returns 2 d h p ( X 1 , X 2 , Y ^ , Z ^ 1 , Z ^ 2 ) 2dhp(X_1,X_2,\hat{Y},\hat{Z}_1,\hat{Z}_2) 2dhp(X1,X2,Y^,Z^1,Z^2),计算 2 d h ( X 1 , X 2 , Y ) 2dh(X_1,X_2,Y) 2dh(X1,X2,Y)很难。 -
XTR-DL: XTR discrete logarithm problem。Most protocols based on DLP can be used with XTR.
Let T r ( g ) Tr(g) Tr(g) 为an XTR representation of an element of the XTR subgroup of F p 6 ∗ \mathbb{F}_{p^6}^* Fp6∗,已知 t t t,求解 x x x使得 t = T r ( g x ) t=Tr(g^x) t=Tr(gx)成立。 -
XTR-DH: XTR Diffie-Hellman problem。Most protocols based on DLP can be used with XTR.
Let T r ( g ) Tr(g) Tr(g) 为an XTR representation of an element of the XTR subgroup of F p 6 ∗ \mathbb{F}_{p^6}^* Fp6∗,已知 t 1 , t 2 t_1,t_2 t1,t2,求解 t 3 t_3 t3使得 t 1 = T r ( g x ) , t 2 = T r ( g y ) , t 3 = T r ( g x y ) t_1=Tr(g^x),t_2=Tr(g^y),t_3=Tr(g^{xy}) t1=Tr(gx),t2=Tr(gy),t3=Tr(gxy)成立。 -
XTR-DHD: XTR decision Diffie-Hellman problem.Most protocols based on DLP can be used with XTR.
Let T r ( g ) Tr(g) Tr(g) 为an XTR representation of an element of the XTR subgroup of F p 6 ∗ \mathbb{F}_{p^6}^* Fp6∗,已知 t 1 = T r ( g x ) , t 2 = T r ( g y ) , t 3 t_1=Tr(g^x),t_2=Tr(g^y),t_3 t1=Tr(gx),t2=Tr(gy),t3,判断 t 3 = T r ( g x y ) t_3=Tr(g^{xy}) t3=Tr(gxy)是否成立? -
CL-DLP: discrete logarithms in class groups of imaginary quadratic orders。常用于key exchange。
为standard discrete logarithm problems in a class group of imaginary quadratic orders。 -
TV-DDH: Tzeng Variant Decision Diffie-Hellman problem。常用于Conference key agreement.
Let p , q = 2 p + 1 p,q=2p+1 p,q=2p+1均为素数,let G ⊆ F p ∗ G\subseteq \mathbb{F}_p^* G⊆Fp∗ 为subgroup of order q q q。 h ∈ G h\in G h∈G为 [ 1 , p − 1 ] [1,p-1] [1,p−1]内的整数, h m o d q h\mod q hmodq为 [ 0 , q − 1 ] [0,q-1] [0,q−1]内整数。已知 g 1 , g 2 ∈ G g_1,g_2\in G g1,g2∈G 且 0 ≤ u 1 , u 2 < q 0\leq u_1,u_2<q 0≤u1,u2<q,取任意整数 a a a,判断 u 1 = g 1 a m o d q , u 2 = g 2 a m o d q u_1=g_1^a\mod q,u_2=g_2^a\mod q u1=g1amodq,u2=g2amodq是否成立? -
n-DHE: n-Diffie-Hellman Exponent problem。常用于 Broadcast encryption, accumulators.
对于a group G G G of prime order q q q,let g i = g λ i , λ ← Z q g_i=g^{\lambda^i},\lambda\leftarrow \mathbb{Z}_q gi=gλi,λ←Zq,已知 { g , g 1 , g 2 , ⋯ , g n , g n + 2 , ⋯ , g 2 n } ∈ G 2 n \{g,g_1,g_2,\cdots,g_n,g_{n+2},\cdots,g_{2n}\}\in G^{2n} {g,g1,g2,⋯,gn,gn+2,⋯,g2n}∈G2n,计算 g n + 1 。 g_{n+1}。 gn+1。
2. Factoring
Factoring problems通常针对的是products of two random primes。如
n
=
p
q
,
n
∈
N
n=pq,n\in\mathbb{N}
n=pq,n∈N,其中
p
,
q
p,q
p,q均为素数。
通常基于安全考虑,定义强素数的形式为
p
=
2
p
′
+
1
p=2p'+1
p=2p′+1,其中
p
p
p和
p
′
p'
p′均为素数。
-
FACTORING: integer factorisation problem
已知正整数 n ∈ N n\in\mathbb{N} n∈N,寻找其素数因式分解 n = p 1 e 1 p 2 e 2 ⋯ p k e k n=p_1^{e_1}p_2^{e_2}\cdots p_k^{e_k} n=p1e1p2e2⋯pkek,其中 p i p_i pi为pairwise distinct 素数, e i > 0 e_i>0 ei>0。 -
SQRT: square roots modulo a composite
已知复合正整数 n ∈ N n\in\mathbb{N} n∈N 和 a square a a a modulo n n n,求 a a a modulo n n n的平方根,即求解integer x x x 使得 x 2 ≡ a ( m o d n ) x^2\equiv a\ (mod\ n) x2≡a (mod n)。
常用于Rabin encryption。 -
C H A R A C T E R d CHARACTER^d CHARACTERd: character problem
Let n n n和 d d d为正整数,已知 x ∈ Z n ∗ x\in\mathbb{Z}_n^* x∈Zn∗,设计算法 χ ( x ) \chi(x) χ(x),其中 χ \chi χ为a non-trivial character of Z n ∗ \mathbb{Z}_n^* Zn∗ of order d d d。
常用于Undeniable Signautres。
可看成是quadratic residuosity problem的generalisation。 -
M O V A d MOVA^d MOVAd: character problem
Let n ∈ Z , s ∈ Z + n\in\mathbb{Z},s\in\mathbb{Z}^+ n∈Z,s∈Z+, χ \chi χ为a character of order d d d on Z n ∗ \mathbb{Z}_n^* Zn∗。已知 s s s个pairs ( α i , χ ( α i ) ) (\alpha_i,\chi(\alpha_i)) (αi,χ(αi)),其中 α i ∈ Z n ∗ \alpha_i\in\mathbb{Z}_n^* αi∈Zn∗ for all i ∈ [ 1 , ⋯ , s ] i\in[1,\cdots,s] i∈[1,⋯,s], x ∈ Z n ∗ x\in\mathbb{Z}_n^* x∈Zn∗,计算 χ ( x ) \chi(x) χ(x)。
常用于Undeniable Signautres。 -
C Y C L O F A C T d CYCLOFACT^d CYCLOFACTd: factorisation in Z[θ]
Let θ \theta θ 为 d t h d^{th} dth root of unity, σ \sigma σ 为 an element of Z [ θ ] \mathbb{Z}[\theta] Z[θ],求 σ \sigma σ的因式分解。 -
F E R M A T d FERMAT^d FERMATd: factorisation in Z[θ]
Let θ \theta θ 为 d t h d^{th} dth root of unity, n ∈ Z n\in\mathbb{Z} n∈Z 使得 n = π π ˉ n=\pi\bar{\pi} n=ππˉ for some π ∈ Z [ θ ] \pi\in\mathbb{Z}[\theta] π∈Z[θ]。已知 n n n,求 π \pi π。 -
RSAP: RSA problem
已知正整数 n n n为至少2个素数的乘积,已知整数 e e e (coprime with φ ( n ) \varphi(n) φ(n)) 和整数 c c c,求整数 m m m使得 m e ≡ c ( m o d n ) m^e\equiv c\ (mod\ n) me≡c (mod n)成立。 -
Strong-RSAP: strong RSA problem
已知正整数 n n n为至少2个素数的乘积,已知整数 c c c,求奇数 e ≥ 3 e\geq 3 e≥3和整数 m m m,使得 m e ≡ c ( m o d n ) m^e\equiv c\ (mod\ n) me≡c (mod n)成立。 -
Difference-RSAP: Difference RSA problem
已知正整数 n n n为至少2个素数的乘积,已知an element D ∈ Z n ∗ D\in\mathbb{Z}_n^* D∈Zn∗ 和 m − 1 m-1 m−1 个pairs ( x i , y i ) (x_i,y_i) (xi,yi) 使得 x i e − y i e = D ( m o d n ) x_i^e-y_i^e=D\ (mod\ n) xie−yie=D (mod n),求解新的pair x m e − y m e = D ( m o d n ) x_m^e-y_m^e=D\ (mod\ n) xme−yme=D (mod n) 成立。 -
Partial-DL-ZN2P: Partial Discrete Logarithm problem in Z n 2 ∗ \mathbb{Z}_{n^2}^* Zn2∗
已知正整数 n = p q n=pq n=pq,其中 p = 2 p ′ + 1 , q = 2 q ′ + 1 p=2p'+1,q=2q'+1 p=2p′+1,q=2q′+1, p , p ′ , q , q ′ p,p',q,q' p,p′,q,q′均为素数,已知an element g ∈ Z n 2 ∗ g\in\mathbb{Z}_{n^2}^* g∈Zn2∗ of maximal order in G = Q R n 2 G=QR_{n^2} G=QRn2 和 h = g a m o d n 2 h=g^a\ mod\ n^2 h=ga mod n2 for some a ∈ { 1 , ⋯ , o r d ( G ) } a\in\{1,\cdots,ord(G)\} a∈{1,⋯,ord(G)},求解整数 x x x使得 x = a ( m o d n ) x=a\ (mod\ n) x=a (mod n)。
常用于homomorphic public key encryption, public key encryption with double trapdoor decryption mechanism。 -
DDH-ZN2P: Decision Diffie-Hellman problem over Z n 2 ∗ \mathbb{Z}_{n^2}^* Zn2∗
已知正整数 n = p q n=pq n=pq,其中 p = 2 p ′ + 1 , q = 2 q ′ + 1 p=2p'+1,q=2q'+1 p=2p′+1,q=2q′+1, p , p ′ , q , q ′ p,p',q,q' p,p′,q,q′均为素数,已知an element g ∈ Z n 2 ∗ g\in\mathbb{Z}_{n^2}^* g∈Zn2∗ of maximal order in G = Q R n 2 G=QR_{n^2} G=QRn2 和 elements X = g x m o d n 2 , Y = g y m o d n 2 X=g^x\ mod\ n^2, Y=g^y\ mod\ n^2 X=gx mod n2,Y=gy mod n2 for some x , y ∈ { 1 , ⋯ , o r d ( G ) } x,y\in\{1,\cdots,ord(G)\} x,y∈{1,⋯,ord(G)} 以及 Z ∈ G Z\in G Z∈G,判断 Z = g x y m o d n 2 Z=g^{xy}\ mod\ n^2 Z=gxy mod n2是否成立。
常用于public key encryption with double trapdoor decryption mechanism。 -
Lift-DH-ZN2P: Lift Diffie-Hellman problem over Z n 2 ∗ \mathbb{Z}_{n^2}^* Zn2∗
已知正整数 n = p q n=pq n=pq,其中 p = 2 p ′ + 1 , q = 2 q ′ + 1 p=2p'+1,q=2q'+1 p=2p′+1,q=2q′+1, p , p ′ , q , q ′ p,p',q,q' p,p′,q,q′均为素数,已知an element g ∈ Z n 2 ∗ g\in\mathbb{Z}_{n^2}^* g∈Zn2∗ of maximal order in G = Q R n 2 G=QR_{n^2} G=QRn2 和 elements X = g x m o d n 2 , Y = g y m o d n 2 X=g^x\ mod\ n^2, Y=g^y\ mod\ n^2 X=gx mod n2,Y=gy mod n2 for some x , y ∈ { 1 , ⋯ , o r d ( G ) } x,y\in\{1,\cdots,ord(G)\} x,y∈{1,⋯,ord(G)} 以及 Z = g x y m o d n Z=g^{xy}\ mod\ n Z=gxy mod n,求 Z ′ = g x y m o d n 2 Z'=g^{xy}\ mod\ n^2 Z′=gxy mod n2。
常用于public key encryption with double trapdoor decryption mechanism。 -
EPHP: Election Privacy Homomorphism problem
已知固定的小素数 e e e、素数 p p p 使得 e ∣ ( p − 1 ) e|(p-1) e∣(p−1)、素数 q q q使得 e ∤ ( q − 1 ) e\nmid (q-1) e∤(q−1),有 n = p q n=pq n=pq、 g ∈ Z n g\in\mathbb{Z}_n g∈Zn 且 e e e divides the order of g g g。由 g g g作为generator生成的group表示为 G G G。
EPHP是指:已知 w ∈ G w\in G w∈G、 v ∈ [ 0 , e ] v\in [0,e] v∈[0,e],是否存在 r ∈ N r\in N r∈N,使得 w = g v + e r w=g^{v+er} w=gv+er成立。存在的概率应高于 ( e − 1 ) / e (e-1)/e (e−1)/e。
常用于homomorphic public key encryption 和 electronic voting protocols。 -
AERP: Approximate e-th root problem
已知正整数 n = p 2 q n=p^2q n=p2q,其中 p , q p,q p,q为素数且 ∣ n ∣ = 3 k |n|=3k ∣n∣=3k,已知整数 e ≥ 4 e\geq 4 e≥4、 y ∈ Z n y\in\mathbb{Z}_n y∈Zn,求整数 x x x,使得 ( x e m o d n ) ∈ I k ( y ) (x^e\ mod\ n)\in I_k(y) (xe mod n)∈Ik(y)成立,其中 I k ( y ) = { u ∣ y ≤ u < y + 2 2 k − 1 } I_k(y)=\{u|y\leq u< y+2^{2k-1}\} Ik(y)={u∣y≤u<y+22k−1}。
常用于ESIGN signature scheme。 -
l l l-HENSEL-RSAP: l l l-Hensel RSA
已知 N = p q N=pq N=pq, e e e coprime with ϕ ( N ) \phi(N) ϕ(N), x e ( m o d N ) x^e\ (mod\ N) xe (mod N) for a random integer 1 < x < N 1<x<N 1<x<N,求 x e ( m o d N l ) x^e\ (mod\ N^l) xe (mod Nl)。
常用于public-key encryption。 -
DSeRP: Decisional Small e-Residues in Z n 2 ∗ \mathbb{Z}_{n^2}^* Zn2∗
已知正整数 n = p q n=pq n=pq,其中 p , q p,q p,q为素数,已知整数 e > 2 e>2 e>2 使得 g c d ( e , n ( p − 1 ) ( q − 1 ) ) = 1 gcd(e,n(p-1)(q-1))=1 gcd(e,n(p−1)(q−1))=1,是否能区分 D 0 = { c = r e m o d n 2 ∣ r ∈ R Z n } D_0=\{c=r^e\ mod\ n^2|r\in_R\mathbb{Z}_n\} D0={c=re mod n2∣r∈RZn} distribution 和 D 1 = { c ∈ R Z n 2 } D_1=\{c\in_R\mathbb{Z}_{n^2}\} D1={c∈RZn2} distribution。
常用于Semantically secure public key encryption from Paillier-related assumptions。 -
DS2eRP: Decisional Small 2e-Residues in Z n 2 ∗ \mathbb{Z}_{n^2}^* Zn2∗
已知正整数 n = p q n=pq n=pq,其中 p , q p,q p,q为素数, p = q = 3 m o d 4 p=q=3\ mod\ 4 p=q=3 mod 4,已知整数 e e e 使得 g c d ( e , n ( p − 1 ) ( q − 1 ) ) = 1 gcd(e,n(p-1)(q-1))=1 gcd(e,n(p−1)(q−1))=1且 ∣ n ∣ / 2 < 3 < ∣ n ∣ |n|/2<3<|n| ∣n∣/2<3<∣n∣,是否能区分 D 0 = { c = r 2 e m o d n 2 ∣ r ∈ R Q R n } D_0=\{c=r^{2e}\ mod\ n^2|r\in_R QR_n\} D0={c=r2e mod n2∣r∈RQRn} distribution 和 D 1 = { c ∈ R Q R n 2 } D_1=\{c\in_R QR_{n^2}\} D1={c∈RQRn2} distribution。
常用于Semantically secure public key encryption mixing Paillier and Rabin functions。 -
DSmallRSAKP: Decisional Reciprocal RSA-Paillier in Z n 2 ∗ \mathbb{Z}_{n^2}^* Zn2∗
已知正整数 n = p q n=pq n=pq,其中 p , q p,q p,q为素数,已知an element α \alpha α使得 ( α / p ) = ( α / q ) = − 1 (\alpha/p)=(\alpha/q)=-1 (α/p)=(α/q)=−1,已知整数 e e e使得 ∣ n ∣ / 2 < e < ∣ n ∣ |n|/2<e<|n| ∣n∣/2<e<∣n∣,是否能区分 D 0 = { ( n , e , α , c ) ∣ c = ( r + α r ) e m o d n 2 , r ∈ R Z n s . t . ( r / n ) = 1 , ( α / r m o d n ) > r } D_0=\{(n,e,\alpha,c)|c=(r+\frac{\alpha}{r})^e\ mod\ n^2,r\in_R\mathbb{Z}_n\ s.t.\ (r/n)=1, (\alpha/r\ mod\ n)>r\} D0={(n,e,α,c)∣c=(r+rα)e mod n2,r∈RZn s.t. (r/n)=1,(α/r mod n)>r} distribution 和 D 1 = { ( n , e , α , c ) ∣ c = ( r + α r ) e m o d n 2 , r ∈ R Z n 2 } D_1=\{(n,e,\alpha,c)|c=(r+\frac{\alpha}{r})^e\ mod\ n^2,r\in_R\mathbb{Z}_{n^2}\} D1={(n,e,α,c)∣c=(r+rα)e mod n2,r∈RZn2} distribution。
常用于Semantically secure public key encryption from Paillier-related assumptions。 -
HRP: Higher Residuosity Problem
已知 n n n和 a a a为正整数,且 a ∣ ϕ ( n ) a|\phi(n) a∣ϕ(n),已知 x ∈ Z n ∗ x\in\mathbb{Z}_n^* x∈Zn∗,判断是否存在 y y y,使得 y a = x y^a=x ya=x。
常用于:convertible group signature,public key encrytpion。 -
ECSQRT: Square roots in elliptic curve groups over Z / n Z \mathbb{Z}/n\mathbb{Z} Z/nZ
已知 E ( Z / n Z ) E(\mathbb{Z}/n\mathbb{Z}) E(Z/nZ) 为 elliptic curve group over Z / n Z \mathbb{Z}/n\mathbb{Z} Z/nZ,已知a point Q ∈ E ( Z / n Z ) Q\in E(\mathbb{Z}/n\mathbb{Z}) Q∈E(Z/nZ),计算所有points P ∈ E ( Z / n Z ) P\in E(\mathbb{Z}/n\mathbb{Z}) P∈E(Z/nZ) 使得 2 P = Q 2P=Q 2P=Q。 -
RFP: Root Finding Problem
计算多项式 f ( x ) f(x) f(x) over the ring Z n \mathbb{Z}_n Zn的所有roots,其中 n = p q n=pq n=pq, p , q p,q p,q为2个大素数。 -
phiA: PHI-Assumption
设 P R I M E S a PRIMES_a PRIMESa 为the set of all primes of length a a a, H a H_a Ha为the set of the composite integers that are product of two primes of length a a a。
若 p ∣ ϕ ( m ) p|\phi(m) p∣ϕ(m),则称composite integer m m m ϕ \phi ϕ-hides a prime p p p。
H b ( m ) H^b(m) Hb(m)表示the set of b b b-bit primes p p p that are ϕ \phi ϕ-hidden by m m m; H ˉ b ( m ) \bar{H}^b(m) Hˉb(m)表示the set P R I M E S b − H b ( m ) PRIMES_b-H^b(m) PRIMESb−Hb(m)。
ϕ \phi ϕ-Hidding假设:存在 e , f , g , h > 0 e,f,g,h>0 e,f,g,h>0,使得对于 ∀ k > h \forall k>h ∀k>h和 ∀ 2 e k \forall 2^{ek} ∀2ek-gate circuits C C C, P r [ m ← H k ; p 0 ← H k ( m ) ; p 1 ← H ˉ k ( m ) ; b ← 0 , 1 : C ( m , p b ) = b ] > 1 / 2 + 2 − g k Pr[m\leftarrow H^k;p_0\leftarrow H^k(m);p_1\leftarrow \bar{H}^k(m);b\leftarrow 0,1: C(m,p_b)=b]>1/2+2^{-gk} Pr[m←Hk;p0←Hk(m);p1←Hˉk(m);b←0,1:C(m,pb)=b]>1/2+2−gk。
ϕ \phi ϕ-Sampling假设:存在 e , f , g , h > 0 e,f,g,h>0 e,f,g,h>0,使得对于 ∀ k > h \forall k>h ∀k>h,存在a sampling algorithm S ( ) S() S() 使得for all k k k-bit primes p p p, S ( p ) S(p) S(p) 输出a random k f k^f kf-bit number m ∈ H k f k m\in H_{k^f}^k m∈Hkfk that ϕ \phi ϕ-hides p p p together with m m m's integer factorization。 -
C-DRSA: Computational Dependent-RSA problem
已知 ( N , e ) (N,e) (N,e)和 α ∈ Z n ∗ \alpha\in\mathbb{Z}_n^* α∈Zn∗,求 ( a + 1 ) e ( m o d n ) (a+1)^e(\mod n) (a+1)e(modn) 其中 α = a e ( m o d n ) \alpha=a^e(\mod n) α=ae(modn)。 -
D-DRSA: Decisional Dependent-RSA problem
已知 ( N , e ) (N,e) (N,e)、 α = a e ( m o d n ) \alpha=a^e(\mod n) α=ae(modn)和 γ ∈ Z n ∗ \gamma\in\mathbb{Z}_n^* γ∈Zn∗,是否能区分 γ = ( a + 1 ) e ( m o d n ) \gamma=(a+1)^e(\mod n) γ=(a+1)e(modn)和 γ = c e ( m o d n ) \gamma=c^e(\mod n) γ=ce(modn),其中 a , c a,c a,c为 Z n ∗ \mathbb{Z}_n^* Zn∗中的随机数。 -
E-DRSA: Extraction Dependent-RSA problem
已知 ( N , e ) (N,e) (N,e)、 α = a e ( m o d n ) \alpha=a^e(\mod n) α=ae(modn)和 γ = ( a + 1 ) e ( m o d n ) \gamma=(a+1)^e(\mod n) γ=(a+1)e(modn),求 a ( m o d n ) a(\mod n) a(modn)。 -
DCR: Decisional Composite Residuosity problem
已知composite n n n和integer z z z,判断 z z z是否为 n n n-residue modulo n 2 n^2 n2。 -
CRC: Composite Residuosity Class problem
B α ⊂ Z n 2 ∗ B_{\alpha}\subset\mathbb{Z}_{n^2}^* Bα⊂Zn2∗ 表示:the set of elements of order n α n\alpha nα。
B B B表示: B α B_{\alpha} Bα的disjoint union for α = 1 , ⋯ , λ \alpha=1,\cdots,\lambda α=1,⋯,λ,其中 λ = λ ( n ) \lambda=\lambda(n) λ=λ(n)为the Carmichael’s function taken on n n n。
已知a composite n , w ∈ Z n 2 ∗ , g ∈ B n,w\in\mathbb{Z}_{n^2}^*, g\in B n,w∈Zn2∗,g∈B,计算the n n n-residuosity class of w w w with respect to g : [ w ] g g:[w]_g g:[w]g。 -
DCRC: Decisional Composite Residuosity Class problem
B α ⊂ Z n 2 ∗ B_{\alpha}\subset\mathbb{Z}_{n^2}^* Bα⊂Zn2∗ 表示:the set of elements of order n α n\alpha nα。
B B B表示: B α B_{\alpha} Bα的disjoint union for α = 1 , ⋯ , λ \alpha=1,\cdots,\lambda α=1,⋯,λ,其中 λ = λ ( n ) \lambda=\lambda(n) λ=λ(n)为the Carmichael’s function taken on n n n。
已知a composite n , w ∈ Z n 2 ∗ , g ∈ B , x ∈ Z n n,w\in\mathbb{Z}_{n^2}^*, g\in B,x\in\mathbb{Z}_n n,w∈Zn2∗,g∈B,x∈Zn,判断 x = [ w ] g x=[w]_g x=[w]g是否成立。 -
GenBBS: generalised Blum-Blum-Shub assumption
已知a composite positive integer n ∈ N n\in\mathbb{N} n∈N 和 一系列 g , g 2 ( m o d n ) , g 4 ( m o d n ) , g 8 ( m o d n ) , ⋯ , g 2 2 k ( m o d n ) g,g^2(\mod n), g^4(\mod n), g^8(\mod n),\cdots,g^{2^{2^{k}}}(\mod n) g,g2(modn),g4(modn),g8(modn),⋯,g22k(modn),是否能区分 g 2 2 k + 1 ( m o d n ) g^{2^{2^{k+1}}}(\mod n) g22k+1(modn) 和 r 2 ( m o d n ) r^2(\mod n) r2(modn)。
3. Product groups
本节主要关注的是products of two groups of known prime order,常用于pairing based cryptography,但是在本节讨论的是 pairing之外的安全假设。
主要有3种分类:
1)Type 1:
G
1
=
G
2
G_1=G_2
G1=G2,均为group of prime order
q
q
q;
2)Type 2:
G
1
≠
G
2
G_1\neq G_2
G1=G2,均为group of prime order
q
q
q,但是存在efficiently computable homomorphism
ψ
:
G
2
→
G
1
\psi:G_2\rightarrow G_1
ψ:G2→G1;
3)Type3:
G
1
≠
G
2
G_1\neq G_2
G1=G2,均为group of prime order
q
q
q,且不存在efficiently computable homomorphism
ψ
:
G
2
→
G
1
\psi:G_2\rightarrow G_1
ψ:G2→G1。
以
g
i
g_i
gi表示a generator of
G
i
G_i
Gi,则对于Type 1有
g
1
=
g
2
g_1=g_2
g1=g2。
对于
a
∈
G
i
,
b
∈
G
j
a\in G_i,b\in G_j
a∈Gi,b∈Gj,若
log
g
i
a
=
log
g
j
b
\log_{g_i}a=\log_{g_j}b
loggia=loggjb,则表示为
a
∼
b
a\sim b
a∼b
-
co-CDH: co-Computational Diffie-Hellman Problem
已知 g i a g_i^a gia,求 g 3 − i a g_{3-i}^a g3−ia。 -
PG-CDH: Computational Diffie-Hellman Problem for Product Groups
已知 g i , g i x , g i y , g 3 − i , g 3 − i x , g 3 − i y g_i,g_i^x,g_i^y,g_{3-i},g_{3-i}^x,g_{3-i}^y gi,gix,giy,g3−i,g3−ix,g3−iy,求 g i x y g_i^{xy} gixy。 -
XDDH: External Decision Diffie-Hellman Problem
已知 g i a , g j b g_i^a,g_j^b gia,gjb和 v ∈ G k v\in G_k v∈Gk,判断 v = g k a b v=g_k^{ab} v=gkab是否成立。 -
D-Linear2: Decision Linear Problem (version 2)
已知 g ∈ G 1 , g a , g b , g a c , g b d g\in G_1,g^a,g^b,g^{ac},g^{bd} g∈G1,ga,gb,gac,gbd 和 g 2 ∈ G 2 , g 2 a , g 2 b , v ∈ G 1 g_2\in G_2,g_2^a,g_2^b,v\in G_1 g2∈G2,g2a,g2b,v∈G1,判断 v = g c + d v=g^{c+d} v=gc+d是否成立。 -
PG-DLIN: Decision Linear Problem for Product Groups
已知 g i 1 , g i 2 , g i 3 ∈ G i , g i 1 x , g i 2 y g_{i1},g_{i2},g_{i3}\in G_i, g_{i1}^x,g_{i2}^y gi1,gi2,gi3∈Gi,gi1x,gi2y 和 g j 1 , g j 2 , g j 3 ∈ G j , g k 1 x , g k 2 x g_{j1},g_{j2},g_{j3}\in G_j, g_{k1}^x,g_{k2}^x gj1,gj2,gj3∈Gj,gk1x,gk2x,使得 g i 1 ∼ g j 1 , g i 2 ∼ g j 2 , g i 3 ∼ g j 3 g_{i1}\sim g_{j1},g_{i2}\sim g_{j2}, g_{i3}\sim g_{j3} gi1∼gj1,gi2∼gj2,gi3∼gj3,判断 v = g l 1 x + y v=g_{l1}^{x+y} v=gl1x+y是否成立。 -
FSDH: Flexible Square Diffie-Hellman Problem
已知 g 2 a ∈ G 2 g_2^a\in G_2 g2a∈G2,对于任意选择的 h ∈ G 1 h\in G_1 h∈G1,求 ( h , h a , h a 2 ) (h,h^a,h^{a^2}) (h,ha,ha2)。 -
KSW1: Assumption 1 of Katz-Sahai-Waters
对于所有的p.p.t. adversaray A A A,security parameter 为 n n n的情况下,以下情况成立的概率可忽略:
运行 G ( 1 n ) G(1^n) G(1n) 获取 ( p , q , r , G , G T , t ^ ) (p,q,r,G,G_T,\hat{t}) (p,q,r,G,GT,t^)。
设置 N = p q r N=pqr N=pqr,并令 g p , g q , g r g_p,g_q,g_r gp,gq,gr分别为generators of G p , G q , G r G_p,G_q,G_r Gp,Gq,Gr。
选择随机的 Q 1 , Q 2 , Q 3 ∈ G q Q_1,Q_2,Q_3\in G_q Q1,Q2,Q3∈Gq,随机的 R 1 , R 2 , R 3 ∈ G r R_1,R_2,R_3\in G_r R1,R2,R3∈Gr,随机的 a , b , s ∈ Z p a,b,s\in \mathbb{Z}_p a,b,s∈Zp以及随机的bit v v v.
A A A 已知 ( N , G , G T , t ^ ) (N,G,G_T,\hat{t}) (N,G,GT,t^) 和 g p , g r , g q R 1 , g p b , g p b 2 , g p a g q , g p a b Q 1 , g p s , g p b s Q + 2 R 2 g_p,g_r,g_qR_1,g_p^b,g_p^{b^2},g_p^ag_q,g_p^{ab}Q_1,g_p^s,g_p^{bs}Q+2R_2 gp,gr,gqR1,gpb,gpb2,gpagq,gpabQ1,gps,gpbsQ+2R2,若 v = 0 v=0 v=0,则告知 A A A T = g p b 2 s Q 3 R 3 T=g_p^{b^2s}Q_3R_3 T=gpb2sQ3R3值。
A A A输出 v ′ v' v′使得 v ′ = v v'=v v′=v的概率可忽略。
4. Pairings
2008年《Pairings for cryptographers》中指出,pairings over groups of known prime order 表示为:
t
^
:
G
1
×
G
2
→
G
T
\hat{t}:G_1\times G_2\rightarrow G_T
t^:G1×G2→GT
若其中
G
1
,
G
2
,
G
T
G_1,G_2,G_T
G1,G2,GT都具有相同的prime order
l
l
l,则可分为以下三大类:
1)Type 1:
G
1
=
G
2
G_1=G_2
G1=G2;【通常使用supersingular curves,这些supersingular curves又分为两类:一类是over fields of characteristic 2 or 3 (with embedding degree 4 or 6 respectively);另一类是over fields of large prime characteristic (with embedding degree 2)。】
2)Type 2:
G
1
≠
G
2
G_1\neq G_2
G1=G2,但是存在efficiently computable homomorphism
ϕ
:
G
2
→
G
1
\phi:G_2\rightarrow G_1
ϕ:G2→G1;【通常使用ordinary curves,且the homomorphism from
G
2
G_2
G2 to
G
1
G_1
G1 is the trace map。】
3)Type3:
G
1
≠
G
2
G_1\neq G_2
G1=G2,且不存在efficiently computable homomorphism
ϕ
:
G
2
→
G
1
\phi:G_2\rightarrow G_1
ϕ:G2→G1。【通常使用ordinary curves,且
G
2
G_2
G2为the kernel of the trace map。】
若 G 2 G_2 G2 为non-cyclic group of order l 2 l^2 l2,则可称为Type 4。




具体举例为:
- Type 1:

- Type 2:

- Type 3:

若
log
g
1
a
=
log
g
2
b
\log_{g_1}a=\log_{g_2}b
logg1a=logg2b,则表示为
a
∼
b
a\sim b
a∼b。
Pairing 相关假设有:【注意,有的assumption并不适于所有的pairing type。Certain assumptions are provably false w.r.t. certain group types.】
-
BDHP: Bilinear Diffie-Hellman Problem。
已知 g i a , g j b 和 g k c g_i^a,g_j^b和g_k^c gia,gjb和gkc,计算 t ^ ( g 1 , g 2 ) a b c \hat{t}(g_1,g_2)^{abc} t^(g1,g2)abc。
其中 i , j , k ∈ { 1 , 2 } i,j,k\in\{1,2\} i,j,k∈{1,2},对应有四种可能的组合 ( i , j , k ) ∈ { ( 1 , 1 , 1 ) , ( 1 , 1 , 2 ) , ( 1 , 2 , 2 ) , ( 2 , 2 , 2 ) } (i,j,k)\in\{(1,1,1),(1,1,2),(1,2,2),(2,2,2)\} (i,j,k)∈{(1,1,1),(1,1,2),(1,2,2),(2,2,2)},也可称为 B D H P i , j , k BDHP_{i,j,k} BDHPi,j,k。
– 对于Type 1 pairing,以上四种组合是等价的。
– 对于Type 2 pairing,具有 B D H P 2 , 2 , 2 ≤ P B D H P 1 , 2 , 2 ≤ P B D H P 1 , 1 , 2 ≤ P B D H P 1 , 1 , 1 BDHP_{2,2,2}\leq_P BDHP_{1,2,2}\leq_P BDHP_{1,1,2}\leq_P BDHP_{1,1,1} BDHP2,2,2≤PBDHP1,2,2≤PBDHP1,1,2≤PBDHP1,1,1。
– 对于Type 3 pairing,这四种组合have no known reductions between them。 -
DBDH: Decision Bilinear Diffie-Hellman Problem。常用于 Boneh-Franklin ID-based encryption scheme。
已知 g i a , g j b , g k c 和 t ^ ( g 1 , g 2 ) z g_i^a,g_j^b,g_k^c和\hat{t}(g_1,g_2)^{z} gia,gjb,gkc和t^(g1,g2)z,判断 t ^ ( g 1 , g 2 ) a b c = t ^ ( g 1 , g 2 ) z \hat{t}(g_1,g_2)^{abc}=\hat{t}(g_1,g_2)^{z} t^(g1,g2)abc=t^(g1,g2)z是否成立。 -
B-DLIN: Bilinear Decision-Linear Problem
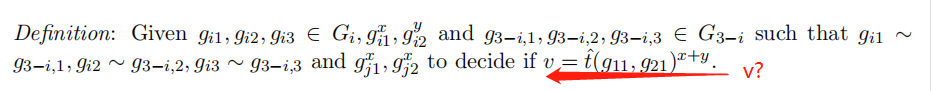
-
l-BDHI: l-Bilinear Diffie-Hellman Inversion Problem
已知 g i a , g i a 2 , g i a 3 , ⋯ , g i a l g_i^{a},g_i^{a^2},g_i^{a^3},\cdots,g_i^{a^l} gia,gia2,gia3,⋯,gial,计算 t ^ ( g 1 , g 2 ) 1 / a \hat{t}(g_1,g_2)^{1/a} t^(g1,g2)1/a。其中 i ∈ { 1 , 2 } i\in\{1,2\} i∈{1,2}。 -
l-DBDHI: l-Bilinear Decision Diffie-Hellman Inversion Problem
已知 g i a , g i a 2 , g i a 3 , ⋯ , g i a l g_i^{a},g_i^{a^2},g_i^{a^3},\cdots,g_i^{a^l} gia,gia2,gia3,⋯,gial和 v ∈ G T v\in G_T v∈GT,判断 v = t ^ ( g 1 , g 2 ) 1 / a v=\hat{t}(g_1,g_2)^{1/a} v=t^(g1,g2)1/a是否成立?其中 i ∈ { 1 , 2 } i\in\{1,2\} i∈{1,2}。 -
l-wBDHI: l-weak Bilinear Diffie-Hellman Inversion Problem。
已知 g i a , g i a 2 , g i a 3 , ⋯ , g i a l g_i^{a},g_i^{a^2},g_i^{a^3},\cdots,g_i^{a^l} gia,gia2,gia3,⋯,gial和 g j b g_j^b gjb,计算 t ^ ( g 1 , g 2 ) a l + 1 b \hat{t}(g_1,g_2)^{a^{l+1}b} t^(g1,g2)al+1b。其中 i ∈ { 1 , 2 } i\in\{1,2\} i∈{1,2}。 -
l-wDBDHI: l-weak Decisional Bilinear Diffie-Hellman Inversion Problem
已知 g i a , g i a 2 , g i a 3 , ⋯ , g i a l , g j b g_i^{a},g_i^{a^2},g_i^{a^3},\cdots,g_i^{a^l},g_j^b gia,gia2,gia3,⋯,gial,gjb和 v ∈ G T v\in G_T v∈GT,判断 v = t ^ ( g 1 , g 2 ) a l + 1 b v=\hat{t}(g_1,g_2)^{a^{l+1}b} v=t^(g1,g2)al+1b是否成立?其中 i ∈ { 1 , 2 } i\in\{1,2\} i∈{1,2}。 -
KSW2: Assumption 2 of Katz-Sahai-Waters。首次用于 the construction of a predicate encryption scheme supporting the inner product。(KATZ等人2008年论文《Predicate Encryption Supporting Disjunctions, Polynomial Equations, and Inner Products》)
– 运行 G ( 1 n ) G(1^n) G(1n)来获取 ( p , q , r , G , G T , t ^ ) (p,q,r,G,G_T,\hat{t}) (p,q,r,G,GT,t^);
– 设置 N = p q r N=pqr N=pqr,let g p , g q , g r g_p,g_q,g_r gp,gq,gr分别为 G p , G q , G r G_p,G_q,G_r Gp,Gq,Gr的generators;
– 选择随机数 h ∈ G p ; Q 1 , Q 2 ∈ G q ; s , γ ∈ Z q h\in G_p;Q_1,Q_2\in G_q;s,\gamma\in\mathbb{Z}_q h∈Gp;Q1,Q2∈Gq;s,γ∈Zq以及random bit v v v;
– p.p.t. adversary A A A 的输入有 ( N , G , G T , t ^ ) (N,G,G_T,\hat{t}) (N,G,GT,t^)和 g p , g q , g r , h , g p s , h s Q 1 , g p γ Q 2 , t ^ ( g p , h ) γ g_p,g_q,g_r,h,g_p^s,h^sQ_1,g_p^{\gamma}Q_2,\hat{t}(g_p,h)^{\gamma} gp,gq,gr,h,gps,hsQ1,gpγQ2,t^(gp,h)γ,当 v = 0 v=0 v=0时,再给 A A A 输入 t ^ ( g p , h ) γ s \hat{t}(g_p,h)^{\gamma s} t^(gp,h)γs;当 v = 1 v=1 v=1时,给 A A A的输入为a random element of G T G_T GT。 A A A的输出为a bit v ′ v' v′,且其succeed if v ′ = v v'=v v′=v。 -
MSEDH: Multi-sequence of Exponents Diffie-Hellman Assumption。用于 Delerabl´ee and Pointcheval dynamic threshold public-key encryption scheme。
– Let B = ( p , G 1 , G 2 , G T , t ^ ( ⋅ , ⋅ ) ) B=(p,G_1,G_2,G_T,\hat{t}(\cdot,\cdot)) B=(p,G1,G2,GT,t^(⋅,⋅))为a bilinear map group system,let l , m , t l,m,t l,m,t为3个整数,let g 0 g_0 g0为 G 1 G_1 G1的generator, h 0 h_0 h0为 G 2 G_2 G2的generator。
– 输入为2个random coprime polynomials f f f和 g g g,分别具有degree l l l和 m m m,分别具有pairwise distinct roots x 1 , ⋯ , x l x_1,\cdots,x_l x1,⋯,xl和 y 1 , ⋯ , y m y_1,\cdots,y_m y1,⋯,ym。同时有 T ∈ G T T\in G_T T∈GT以及如下的exponentiations 序列:
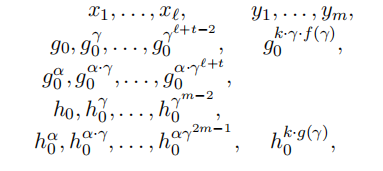
判断 T T T是否与 t ^ ( g 0 , h 0 ) k ⋅ f ( γ ) \hat{t}(g_0,h_0)^{k\cdot f(\gamma)} t^(g0,h0)k⋅f(γ)相等或者与 G T G_T GT中的某随机元素相同? -
SXDH assumption: the SXDH assumption states that there are prime-order groups ( G 1 , G 2 , G T ) (G_1, G_2, G_T ) (G1,G2,GT) that admits a bilinear map e : G 1 × G 2 → G T e : G_1 \times G_2 \rightarrow G_T e:G1×G2→GT such that the Decisional Diffie-Hellman (DDH) assumption holds in both G 1 G_1 G1 and G 2 G_2 G2. 首次在2005年论文《Correlation-Resistant Storage via Keyword-Searchable Encryption》中提出:


而在 2019年论文《Proofs for Inner Pairing Products and Applications》中指出,SXDH assumption仅在Type 3 pairings 下成立,因此任何基于SXDH assumption的设计均对应应采用Type 3 pairing。 -
DBP: double pairing assumption。在2016年论文《Structure-Preserving Signatures and Commitments to Group Elements》中提出。

5. Lattices
基础可参看博客 如何保护今日加密数据以抵抗量子攻击?。
A lattice
Λ
\Lambda
Λ of dimension
n
n
n 为 a discrete subgroup of
R
d
\mathbb{R}^d
Rd,其中
d
≥
n
d\geq n
d≥n。
密码学中的实际应用,通常使用的为lattices in
Z
d
\mathbb{Z}^d
Zd。
A lattice is specified by a
d
×
n
d\times n
d×n basis matrix
B
B
B, consisting of
n
n
n linearly indepedent basis vectors
b
⃗
i
∈
R
d
\vec{b}_i\in\mathbb{R}^d
bi∈Rd。
以
Λ
(
B
)
\Lambda(B)
Λ(B)来表示the lattice spanned by the basis
B
B
B。
5.1 Main Lattice Problems
-
SVP γ p _{\gamma}^p γp: (Approximate) Shortest vector problem
已知a basis B ∈ Z m × n B\in\mathbb{Z}^{m\times n} B∈Zm×n 和 γ > 0 \gamma>0 γ>0,求 a nonzero lattice vector v ∈ B Z n ∖ { 0 } v\in B\mathbb{Z}^n\setminus \{0\} v∈BZn∖{0},使得 ∥ v ∥ p ≤ γ λ 1 p ( B ) \parallel v\parallel _p\leq \gamma\lambda_1^p(B) ∥v∥p≤γλ1p(B)。 -
CVP γ p _{\gamma}^p γp: (Approximate) Closest vector problem
已知a basis B ∈ Z m × n B\in\mathbb{Z}^{m\times n} B∈Zm×n 、 γ > 0 \gamma>0 γ>0 和 t ∈ B R n t\in B\mathbb{R}^n t∈BRn,求 a nonzero lattice vector v ∈ B Z n v\in B\mathbb{Z}^n v∈BZn,使得 ∥ t − v ∥ p ≤ γ λ 1 p ( B ) \parallel t-v\parallel _p\leq \gamma\lambda_1^p(B) ∥t−v∥p≤γλ1p(B)。 -
GapSVP γ p _{\gamma}^p γp: Decisional shortest vector problem
已知a basis B ∈ Z m × n B\in\mathbb{Z}^{m\times n} B∈Zm×n 、 d , γ > 0 d,\gamma>0 d,γ>0 和 lattice vector v ∈ B Z n ∖ { 0 } v\in B\mathbb{Z}^n\setminus \{0\} v∈BZn∖{0},是否能区分 m i n { ∥ v ∥ p : v ∈ B Z n ∖ { 0 } } ≤ d min\{\parallel v\parallel _p:v\in B\mathbb{Z}^n\setminus \{0\}\}\leq d min{∥v∥p:v∈BZn∖{0}}≤d 和 m i n { ∥ v ∥ p : v ∈ B Z n ∖ { 0 } } > γ d min\{\parallel v\parallel _p:v\in B\mathbb{Z}^n\setminus \{0\}\}> \gamma d min{∥v∥p:v∈BZn∖{0}}>γd。 -
GapCVP γ p _{\gamma}^p γp: Decisional closest vector problem
已知a basis B ∈ Z m × n B\in\mathbb{Z}^{m\times n} B∈Zm×n 、 d , γ > 0 d,\gamma>0 d,γ>0 和 lattice vector t ∈ B R n t\in B\mathbb{R}^n t∈BRn,是否能区分 m i n { ∥ t − v ∥ p : v ∈ B Z n } ≤ d min\{\parallel t-v\parallel _p:v\in B\mathbb{Z}^n\}\leq d min{∥t−v∥p:v∈BZn}≤d 和 m i n { ∥ t − v ∥ p : v ∈ B Z n } > γ d min\{\parallel t-v\parallel _p:v\in B\mathbb{Z}^n\}> \gamma d min{∥t−v∥p:v∈BZn}>γd。
5.2 Modular Lattice Problems
Modular lattice problems are typically defined as average-case problems.
-
SIS p ( n , m , q , β ) ^p(n,m,q,\beta) p(n,m,q,β): Short integer solution problem
设 q q q为prime, A ∈ Z q n × m A\in\mathbb{Z}_q^{n\times m} A∈Zqn×m,其中 A A A为chosen from a distribution negligibly close to uniform over Z q n × m \mathbb{Z}_q^{n\times m} Zqn×m,则 Λ q ⊥ ( A ) = { x ⃗ ∈ Z m : A x ⃗ ≡ 0 ⃗ ( m o d q ) } \Lambda_q^{\perp}(A)=\{\vec{x}\in\mathbb{Z}^m:A\vec{x}\equiv \vec{0}(\mod q)\} Λq⊥(A)={x∈Zm:Ax≡0(modq)} 为a m m m-dimensional lattice。
求 a vector v ⃗ ∈ Λ q ⊥ ( A ) \vec{v}\in\Lambda_q^{\perp}(A) v∈Λq⊥(A) 使得 ∥ v ⃗ ∥ ≤ β \parallel \vec{v} \parallel\leq \beta ∥v∥≤β。 -
ISIS p ( n , m , q , β ) ^p(n,m,q,\beta) p(n,m,q,β): Inhomogeneous short integer solution problem
设 q q q为prime, A ∈ Z q n × m A\in\mathbb{Z}_q^{n\times m} A∈Zqn×m, y ⃗ ∈ Z n \vec{y}\in\mathbb{Z}^n y∈Zn,其中 A A A和 y ⃗ \vec{y} y为chosen from a distribution negligibly close to uniform over Z q n × m \mathbb{Z}_q^{n\times m} Zqn×m 和 Z q n \mathbb{Z}_q^{n} Zqn。
求 a vector v ⃗ ∈ { x ⃗ ∈ Z m : A x ⃗ ≡ y ⃗ ( m o d q ) } \vec{v}\in\{\vec{x}\in\mathbb{Z}^m:A\vec{x}\equiv \vec{y}(\mod q)\} v∈{x∈Zm:Ax≡y(modq)} 使得 ∥ v ⃗ ∥ ≤ β \parallel \vec{v} \parallel\leq \beta ∥v∥≤β。 -
LWE ( n , q , ϕ ) (n,q,\phi) (n,q,ϕ): Learning with errors problem
T = R / Z \mathbb{T}=\mathbb{R}/\mathbb{Z} T=R/Z 表示 the additive group on the reals modulo one。
A s , ϕ A_{s,\phi} As,ϕ 表示 the distribution on Z q n × T \mathbb{Z}_q^n\times \mathbb{T} Zqn×T obtained by choosing a vector a ⃗ ∈ Z q n \vec{a}\in\mathbb{Z}_q^n a∈Zqn uniformly at random,choosing e e e according to a probability distribution ϕ \phi ϕ on T \mathbb{T} T,输出 ( a ⃗ , < a ⃗ , s > / q + e ) (\vec{a},<\vec{a},s>/q+e) (a,<a,s>/q+e) for some fixed vector s ⃗ ∈ Z q n \vec{s}\in\mathbb{Z}_q^n s∈Zqn。
The search verion of the learning with errors problem “LWE ( n , q , ϕ ) (n,q,\phi) (n,q,ϕ)” 为:
求the secret s ∈ Z q n s\in\mathbb{Z}_q^n s∈Zqn,given access to polynomially many samples of choice from A s , ϕ A_{s,\phi} As,ϕ。
The decision version为:是否能区分the probability distribution A s , ϕ A_{s,\phi} As,ϕ from the unifrom random distribution。
5.3 Miscellaneous Lattice Problems
-
USVP p ( n , γ ) ^p(n,\gamma) p(n,γ): Approximate unique shortest vector problem
设 Λ \Lambda Λ为an n n n-dimensional lattice,求 v ⃗ ∈ Λ ∖ { 0 ⃗ } \vec{v}\in \Lambda\setminus\{\vec{0}\} v∈Λ∖{0},使得 ∥ p ⃗ ∥ ≤ γ λ 1 ( p ) ( Λ ) \parallel\vec{p}\parallel\leq \gamma\lambda_1^{(p)}(\Lambda) ∥p∥≤γλ1(p)(Λ),其中 λ 1 ( p ) ( Λ ) \lambda_1^{(p)}(\Lambda) λ1(p)(Λ)为the first successive minimum of Λ \Lambda Λ in the p p p-norm and the shortest lattice vector i ⃗ \vec{i} i is γ \gamma γ-unique。
换句话说,for all w ⃗ ∈ Λ \vec{w}\in\Lambda w∈Λ with λ 1 ( p ) ≤ ∥ w ⃗ ∥ ≤ γ λ 1 ( p ) ( Λ ) \lambda_1^{(p)}\leq \parallel \vec{w}\parallel\leq \gamma\lambda_1^{(p)}(\Lambda) λ1(p)≤∥w∥≤γλ1(p)(Λ),有 w ⃗ = z u ⃗ \vec{w}=z\vec{u} w=zu for some z ∈ Z z\in\mathbb{Z} z∈Z。 -
SBP p ( n , γ ) ^p(n,\gamma) p(n,γ): Approximate shortest basis problem
设 Λ ⊆ R d \Lambda\subseteq\mathbb{R}^d Λ⊆Rd为 n n n-dimensional lattice,求a basis B B B of Λ \Lambda Λ 使得 for all B ′ ∈ { B ∈ Q d × n : Λ = Λ ( B ) } m a x i = 1 n { ∥ b ⃗ i ∥ } ≤ γ m a x i = 1 n { ∥ b ⃗ i ′ ∥ p } B'\in\{B\in\mathbb{Q}^{d\times n}:\Lambda=\Lambda(B)\}\ max_{i=1}^n\{\parallel\vec{b}_i\parallel\}\leq\gamma max_{i=1}^n\{\parallel \vec{b}_i'\parallel_p\} B′∈{B∈Qd×n:Λ=Λ(B)} maxi=1n{∥bi∥}≤γmaxi=1n{∥bi′∥p} -
SLP p ( n , γ ) ^p(n,\gamma) p(n,γ): Approximate shortest length problem
设 Λ ⊆ R d \Lambda\subseteq\mathbb{R}^d Λ⊆Rd为 n n n-dimensional lattice,求the approximate length (w.r.t the p p p-norm) λ ( p ) \lambda^{(p)} λ(p) of the shortest vector v ⃗ ∈ Λ ∖ { 0 ⃗ } \vec{v}\in\Lambda\setminus\{\vec{0}\} v∈Λ∖{0} 使得 λ 1 ( p ) ( Λ ) ≤ λ ( p ) ≤ γ λ 1 ( p ) ( Λ ) \lambda_1^{(p)}(\Lambda)\leq\lambda^{(p)}\leq \gamma\lambda_1^{(p)}(\Lambda) λ1(p)(Λ)≤λ(p)≤γλ1(p)(Λ),其中 λ 1 ( p ) \lambda_1^{(p)} λ1(p) 表示 the first successive minimum of Λ \Lambda Λi n the p p p-norm。 -
SIVP p ( n , γ ) ^p(n,\gamma) p(n,γ): Approximate shortest independent vector problem
设 Λ ⊆ R d \Lambda\subseteq\mathbb{R}^d Λ⊆Rd为 n n n-dimensional lattice,求 linearly indepedent vectors v ⃗ 1 , ⋯ , v ⃗ n ∈ Λ \vec{v}_1,\cdots,\vec{v}_n\in\Lambda v1,⋯,vn∈Λ with m a x i = 1 n ∥ v ⃗ i ∥ ≤ γ λ n ( p ) ( Λ ) max_{i=1}^{n}\parallel \vec{v}_i\parallel\leq\gamma\lambda_n^{(p)}(\Lambda) maxi=1n∥vi∥≤γλn(p)(Λ),其中 λ n ( p ) ( Λ ) \lambda_n^{(p)}(\Lambda) λn(p)(Λ) 为the n n n-th successive minimum of Λ \Lambda Λi n the p p p-norm。 -
hermiteSVP: Hermite shortest vector problem
已知a basis matrix B ∈ Z m × n ( m ≥ n ) B\in \mathbb{Z}^{m\times n}(m\geq n) B∈Zm×n(m≥n) 和 γ ≥ 1 \gamma\geq 1 γ≥1,求a nonzero vector v v v of norm ∥ v ∥ ≤ γ d e t ( L ( B ) ) 1 / n \parallel v\parallel\leq \gamma det(L(B))^{1/n} ∥v∥≤γdet(L(B))1/n。 -
CRP: Covering radius problem
已知an approximation factor γ ≥ 1 \gamma\geq 1 γ≥1,the input to CRP is a pair ( B , r ) (B,r) (B,r),其中 B B B为a basis matrix B ∈ Z m × n B\in\mathbb{Z}^{m\times n} B∈Zm×n 以及 r ∈ R r\in\mathbb{R} r∈R。是否能区分 ρ ( L ( B ) ) ≤ r \rho(L(B))\leq r ρ(L(B))≤r 和 ρ ( L ( B ) ) > γ ⋅ r \rho(L(B))>\gamma\cdot r ρ(L(B))>γ⋅r。
5.4 Ideal Lattice Problems
设
R
=
Z
[
x
]
/
<
f
>
R=\mathbb{Z}[x]/<f>
R=Z[x]/<f>为the ring of integer polynomials modulo some monic polynomial
f
f
f of degree
n
n
n。
由于
R
R
R为isomorphic to
Z
n
\mathbb{Z}^n
Zn as an additive group,且 ideals in
R
R
R 为 by definition subgroups,两者都对应为lattices。这种形式的latttice称为 “ideal lattices” with respect to
f
f
f。
-
Ideal-SVP γ f , p _\gamma^{f,p} γf,p: (Approximate) Ideal shortest vector problem / Shortest polynomial problem
已知an ideal I I I in Z [ x ] / < f > \mathbb{Z}[x]/<f> Z[x]/<f>,求a polynomial g ∈ I ∖ { 0 } g\in I\setminus\{0\} g∈I∖{0},使得 ∥ g m o d f ∥ p ≤ γ λ 1 p ( I ) \parallel g\mod f\parallel_p\leq \gamma\lambda_1^p(I) ∥gmodf∥p≤γλ1p(I)。 -
Ideal-SIS q , m , β f , p _{q,m,\beta}^{f,p} q,m,βf,p: Ideal small integer solution problem
已知 n n n和 g 1 , ⋯ , g m g_1,\cdots,g_m g1,⋯,gm chosen uniformly at random from Z q [ x ] / < f > \mathbb{Z}_q[x]/<f> Zq[x]/<f>,求 e 1 , ⋯ , e m e_1,\cdots,e_m e1,⋯,em in Z [ x ] \mathbb{Z}[x] Z[x],使得 ∑ i ≤ m e i g i = 0 ( m o d q ) \sum_{i\leq m}e_ig_i=0(\mod q) ∑i≤meigi=0(modq) 且 ∥ e ∥ p ≤ β \parallel e\parallel _p\leq \beta ∥e∥p≤β,其中 e e e is obtained by concatenating the coefficients of all e i e_i ei's。
6. Miscellaneous Problems
-
KEA1: Knowledge of Exponent assumption。参见2004年论文《The Knowledge-of-Exponent Assumptions and 3-Round Zero-Knowledge Protocols》:
背景知识为:Let q q q be a prime such that 2 q + 1 2q+1 2q+1 is also prime, and let g g g be a generator of the order q q q subgroup of Z 2 q + 1 ∗ Z_{2q+1}^* Z2q+1∗。假设输入有 q , g , g a q,g,g^a q,g,ga,想要输出a pair ( C , Y ) , Y = C a (C,Y), Y=C^a (C,Y),Y=Ca。可实现的方式之一是pick some c ∈ Z q c\in\mathbb{Z}_q c∈Zq,设置 C = g c C=g^c C=gc,则有 Y = ( g a ) c = C a Y=(g^a)^c=C^a Y=(ga)c=Ca成立。直观上来说,KEA1假设是指这是唯一的方式。对于任意的adversary能输出such a pair的,其肯定知道相应的 c c c值使得 g c = C g^c=C gc=C。在以下的正式定义中引入了extractor可返回相应的 c c c值:
KEA1 (Knowledge of Exponent assumption) 的定义为: For any adversary A A A that takes input q , g , g a q,g,g^a q,g,ga,返回 ( C , Y ) (C,Y) (C,Y)其中 Y = C a Y=C^a Y=Ca,即意味着存在an extractor A A A,对于与adversary相同的输入,可返回 c c c值,使得 g c = C g^c=C gc=C。 -
MQ: Multivariable Quadratic equations。多变量二次方程式。
已知a system of m m m quadratic polynomial equations in n n n variables each, { y 1 = p 1 ( x 1 , ⋯ , x n ) , ⋯ , y m = p m ( x 1 , ⋯ , x n ) } \{y_1=p_1(x_1,\cdots,x_n),\cdots,y_m=p_m(x_1,\cdots,x_n)\} {y1=p1(x1,⋯,xn),⋯,ym=pm(x1,⋯,xn)},求解 x ∈ F n x\in\mathbb{F}^n x∈Fn 为 in general an NP-problem。 -
CF: Given-weight codeword finding。常用于: McEliece public key cryptosystem (finding the shortest codeword).
已知 n × k n\times k n×k binary linear code C C C和相应的 n × ( n − k ) n\times (n-k) n×(n−k) parity check matrix H H H,求解vector x ⃗ \vec{x} x使得 x ⃗ H = 0 \vec{x}H=0 xH=0成立且 x x x has weight w w w。 -
ConjSP: Braid group conjugacy search problem。
已知 x , y ∈ B n x,y\in B_n x,y∈Bn,求解 a ∈ B n a\in B_n a∈Bn使得 a − 1 x a = y a^{-1}xa=y a−1xa=y成立。 -
GenConjSP: Generalised braid group conjugacy search problem。用于 Public-key cryptosystem due to Ko, Lee, Cheon, Han, Kang and Park。
已知 x , y ∈ B n x,y\in B_n x,y∈Bn,求解 a ∈ B m , m ≤ n a\in B_m,m\leq n a∈Bm,m≤n使得 a − 1 x a = y a^{-1}xa=y a−1xa=y成立。 -
ConjDecomP: Braid group conjugacy decomposition problem。
已知 x , y ∈ B n x,y\in B_n x,y∈Bn, y = b x b − 1 y=bxb^{-1} y=bxb−1 for some b ∈ B n b\in B_n b∈Bn,求解 a ′ , a ′ ′ ∈ B m , m < n a',a''\in B_m,m<n a′,a′′∈Bm,m<n使得 a ′ x a ′ ′ = y a'xa''=y a′xa′′=y成立。 -
ConjDP: Braid group conjugacy decision problem。
已知 x , y ∈ B n x,y\in B_n x,y∈Bn,判断 x x x和 y y y是否conjugate?即是否存在 a ∈ B n a\in B_n a∈Bn使得 a − 1 x a = y a^{-1}xa=y a−1xa=y成立? -
DHCP: Braid group decisional Diffie-Hellman-type conjugacy problem。常用于 Public-key cryptosystem, pseudorandom number generator, pseudorandom synthesizer。
已知 a , w l − 1 a w l , w u − 1 a w u a,w_l^{-1}aw_l,w_u^{-1}aw_u a,wl−1awl,wu−1awu,判断 x u − 1 x l − 1 a x l x u = w u − 1 w l − 1 a w l w u x_u^{-1}x_l^{-1}ax_lx_u=w_u^{-1}w_l^{-1}aw_lw_u xu−1xl−1axlxu=wu−1wl−1awlwu是否成立?for a ∈ B n , x l , w l ∈ B l a\in B_n,x_l,w_l\in B_l a∈Bn,xl,wl∈Bl and x u , w u ∈ B u x_u,w_u\in B_u xu,wu∈Bu。 -
ConjSearch: (multiple simlutaneous) Braid group conjugacy search problem。
Let B B B be a braid group, g ˉ = ( g 1 , ⋯ , g k ) \bar{g}=(g_1,\cdots,g_k) gˉ=(g1,⋯,gk) and h ˉ = ( h 1 , ⋯ , h k ) \bar{h}=(h_1,\cdots,h_k) hˉ=(h1,⋯,hk) be two tuples of elements of B B B。查找 x ∈ B x\in B x∈B使得 h ˉ = x − 1 g ˉ x \bar{h}=x^{-1}\bar{g}x hˉ=x−1gˉx成立。 -
SubConjSearch: subgroup restricted Braid group conjugacy search problem。常用于Anshel- Anshel- Goldfeld key exchange protocol (AAG)。
Let B B B be a braid group, and A A A a subgroup of B B B generated by some { a 1 , ⋯ , a r } \{a_1,\cdots,a_r\} {a1,⋯,ar} and let g ˉ = ( g 1 , ⋯ , g k ) \bar{g}=(g_1,\cdots,g_k) gˉ=(g1,⋯,gk) and h ˉ = ( h 1 , ⋯ , h k ) \bar{h}=(h_1,\cdots,h_k) hˉ=(h1,⋯,hk) be two tuples of elements of B B B。查找 x ∈ A x\in A x∈A, as a word in { a 1 , ⋯ , a r } \{a_1,\cdots,a_r\} {a1,⋯,ar},使得 h ˉ = x − 1 g ˉ x \bar{h}=x^{-1}\bar{g}x hˉ=x−1gˉx成立。 -
LINPOLY : A linear algebra problem on polynomials。
Let W W W be a linear space of dimension ≤ n \leq n ≤n consisting of quadratic forms in n n n variables X 1 , ⋯ , X n X_1,\cdots,X_n X1,⋯,Xn。已知 V = ∑ 1 ≤ i ≤ n X i W V=\sum_{1\leq i\leq n}X_iW V=∑1≤i≤nXiW,is it possible (and how) to uniquely determine W W W? For any subspace L ′ L' L′ of the linear space L L L generated by X 1 , ⋯ , X n X_1,\cdots,X_n X1,⋯,Xn。Let ( V : L ′ ) ← r ∈ K [ X 1 , ⋯ , X n ] : r L ′ ⊆ V (V:L')\leftarrow r\in K[X_1,\cdots,X_n]:rL'\subseteq V (V:L′)←r∈K[X1,⋯,Xn]:rL′⊆V where K K K is a finite field。
猜想:For randomly chosen W W W, the probability ρ \rho ρ that ( V : L ) = W (V:L)=W (V:L)=W are very close to 1 1 1, when n > 2 n>2 n>2。 -
HFE-DP: Hidden Field Equations Decomposition Problem。 It is the basis of the HFE crypto system.
Let F F F be a finite field of order q q q and S , T ∈ A f f − 1 S,T\in Aff^{-1} S,T∈Aff−1 be two invertible, affine transformations over the vector space F n F^n Fn。Denote E : = G F ( q n ) E:=GF(q^n) E:=GF(qn) an extension field over F F F and ϕ : F n → E \phi:F^n\rightarrow E ϕ:Fn→E the bijection between this extension field and the corresponding vector space. We have ϕ − 1 ( ϕ ( a ) ) = a , ∀ a ∈ F n \phi^{-1}(\phi(a))=a,\forall a \in F^n ϕ−1(ϕ(a))=a,∀a∈Fn。
Now let P ( X ) : = ∑ i , j < D , q i + q j < D C i , j X q i + q j + ∑ q i < D B i X q i + A P(X):=\sum_{i,j<D,q^i+q^j<D}C_{i,j}X^{q^i+q^j}+\sum_{q^i<D}B_iX^{q^i}+A P(X):=∑i,j<D,qi+qj<DCi,jXqi+qj+∑qi<DBiXqi+A for finite field elements C i , j , B i , A ∈ E C_{i,j},B_i,A\in E Ci,j,Bi,A∈E the inner polynomial. This gives the public key:
P ( x ) : = T ∘ P ∘ S ( x ) \mathcal{P}(x):=T\circ P\circ S(x) P(x):=T∘P∘S(x)
or more precisely:
P ( x ) : = T ∘ ϕ − 1 ∘ P ∘ ϕ ∘ S ( x ) \mathcal{P}(x):=T\circ \phi^{-1}\circ P\circ \phi \circ S(x) P(x):=T∘ϕ−1∘P∘ϕ∘S(x)
HFE Decomposition problem是指:已知公钥 P \mathcal{P} P,找到对应的私钥 ( S , P , T ) (S,P,T) (S,P,T)。 -
HFE-SP: Hidden Field Equations Solving Problem。
Let F F F be a finite field of order q q q and S , T ∈ A f f − 1 S,T\in Aff^{-1} S,T∈Aff−1 be two invertible, affine transformations over the vector space F n F^n Fn。Denote E : = G F ( q n ) E:=GF(q^n) E:=GF(qn) an extension field over F F F and ϕ : F n → E \phi:F^n\rightarrow E ϕ:Fn→E the bijection between this extension field and the corresponding vector space. We have ϕ − 1 ( ϕ ( a ) ) = a , ∀ a ∈ F n \phi^{-1}(\phi(a))=a,\forall a \in F^n ϕ−1(ϕ(a))=a,∀a∈Fn。
Now let P ( X ) : = ∑ i , j < D , q i + q j < D C i , j X q i + q j + ∑ q i < D B i X q i + A P(X):=\sum_{i,j<D,q^i+q^j<D}C_{i,j}X^{q^i+q^j}+\sum_{q^i<D}B_iX^{q^i}+A P(X):=∑i,j<D,qi+qj<DCi,jXqi+qj+∑qi<DBiXqi+A for finite field elements C i , j , B i , A ∈ E C_{i,j},B_i,A\in E Ci,j,Bi,A∈E the inner polynomial. This gives the public key:
P ( x ) : = T ∘ P ∘ S ( x ) \mathcal{P}(x):=T\circ P\circ S(x) P(x):=T∘P∘S(x)
or more precisely:
P ( x ) : = T ∘ ϕ − 1 ∘ P ∘ ϕ ∘ S ( x ) \mathcal{P}(x):=T\circ \phi^{-1}\circ P\circ \phi \circ S(x) P(x):=T∘ϕ−1∘P∘ϕ∘S(x)
Hidden Field Equations Solving Problem是指:已知 y ∈ F n y\in F^n y∈Fn,找到 x ∈ F n x\in F^n x∈Fn使得 y = P ( x ) y=\mathcal{P}(x) y=P(x)成立。 -
MKS: Multiplicative Knapsack。Naccache and Stern 用于构建 trapdoor one-way permutation。
已知正整数 p , c , n p,c,n p,c,n以及a set { v i } ∈ { 1 , ⋯ , p − 1 } n \{v_i\}\in\{1,\cdots,p-1\}^n {vi}∈{1,⋯,p−1}n,找到a binary vector x x x使得 c = ∏ i = 1 n v i x i c=\prod_{i=1}^{n}v_i^{x_i} c=∏i=1nvixi成立。 -
BP: Balance Problem。常用于Incremental hashing。
已知a group G G G和 a set { v i } ∈ G n \{v_i\}\in G^n {vi}∈Gn,找到disjoint subsets I , J I,J I,J, not both empty,使得 ⨀ i ∈ I v i = ⨀ j ∈ J v j \bigodot_{i\in I}v_i=\bigodot_{j\in J}v_j ⨀i∈Ivi=⨀j∈Jvj成立。 -
AHA: Adaptive Hardness Assumptions.
We consider adaptive strengthenings of standard general hardness assumptions, such as the existence of one-way functions and pseudorandom generators.
– A collection of adaptive 1 − 1 1-1 1−1 one-way functions is a family of 1 − 1 1-1 1−1 functions F n = { f s : { 0 , 1 } n → { 0 , 1 } n } F_n=\{f_s:\{0,1\}^n\rightarrow \{0,1\}^n\} Fn={fs:{0,1}n→{0,1}n} such that for every s s s, it is hard to invert f s ( r ) f_s(r) fs(r) for a random r r r, even for an adversary that is granted access to an “inversion oracle” for f s ′ f_{s'} fs′ for ever s ′ ≠ s s'\neq s s′=s. In other words, the function f s f_s fs is one-way, even with access to an oracle that invert all the functions in the family。
– A sf collection of adaptive pseudo-random generators is a family of 1 − 1 1-1 1−1 functions G n = { G s : { 0 , 1 } n → { 0 , 1 } n } G_n=\{G_s:\{0,1\}^n\rightarrow \{0,1\}^n\} Gn={Gs:{0,1}n→{0,1}n} such that for every s s s, it is hard to invert G s G_s Gs is pseudo-random, even for an adversary that is granted access to an oracle whether given y y y is in the range of G s ′ G_{s'} Gs′ for s ′ ≠ s s'\neq s s′=s. -
SPI: Sparse Polynomial Interpolation。常用于Identification scheme。参见2000年论文《AN IDENTIFICATION SCHEME BASED ON SPARSE POLYNOMIALS》
已知 A , a 0 , ⋯ , a k , C 1 , ⋯ , C k ∈ F q A,a_0,\cdots,a_k,C_1,\cdots,C_k\in \mathbb{F}_q A,a0,⋯,ak,C1,⋯,Ck∈Fq,找到 a polynomial f ( x ) ∈ F [ x ] f(x)\in\mathbb{F}[x] f(x)∈F[x] of degree at most q − 1 q-1 q−1 使得 f ( 0 ) = A , f ( a 0 ) = 0 , f ( a i ) = C i f(0)=A,f(a_0)=0,f(a_i)=C_i f(0)=A,f(a0)=0,f(ai)=Ci for 1 ≤ i ≤ k 1\leq i\leq k 1≤i≤k and f ( x ) − A f(x)-A f(x)−A has coefficients in { 0 , 1 } \{0,1\} {0,1}。 -
SPP: Self-Power Problem。若该问题可破解,在可伪造EIGamal signature scheme中类型2和4的签名。
已知prime p p p和 c ≡ x x m o d p c\equiv x^x\mod p c≡xxmodp,求解 x x x。 -
VDP: Vector Decomposition Problem。常用于AN IDENTIFICATION SCHEME BASED ON SPARSE POLYNOMIALS,AN IDENTIFICATION SCHEME BASED ON SPARSE POLYNOMIALS。
已知a two-dimensional vector space V V V over a finite field, with basis e 1 , e 2 e_1,e_2 e1,e2,和 a vector v v v in V V V。找到 a multiple u u u of e 1 e_1 e1 使得 v − u v-u v−u is a multiple of e 2 e_2 e2。 -
2-DL: 2-generalized Discrete Logarithm Problem。
已知a group G G G of exponent r r r and order r 2 r^2 r2, with generators P 1 , P 2 P_1,P_2 P1,P2, and an element Q Q Q in G G G。找到 a pair of integers ( a , b ) (a,b) (a,b) 使得 Q = a P 1 + b P 2 Q=aP_1+bP_2 Q=aP1+bP2成立。
参考资料
[1] Can you give me a summary of cryptographic hardness assumptions?
[2] 2013年报告《Final Report on Main Computational Assumptions in Cryptography》
[3] European Network of Excellence in Cryptology II
[4] 2012年 Cryptographic Primitives and Hard Problems in Cryptography wiki
[5] 2015年论文《Cryptographic Assumptions: A Position Paper》
























 4198
4198

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








