1.1 概述
一般情况下,不同单位地业务对接需配备安全设备(例如防火墙、网闸)进行限制性地相互访问,从而满足双方单位的网络安全要求。常规的技术方案有:
1、打通三层路由+安全访问控制策略
2、源地址转换+目标地址转化+安全访问控制策略
3、双向地址转换+安全访问控制策略
本期文章结合实际案例向各位小伙伴总结分享方案2和方案3。
1.2 组网实现的目标
Firewall_1配置两条双地址转换策略,Firewall_2配置一条目的地址转换策略和一条源地址转化策略;
Ser_1设备可telnet访问Ser_2设备;
Ser_2设备可telnet访问Ser_1设备。
1.3 组网拓扑图及地址规划
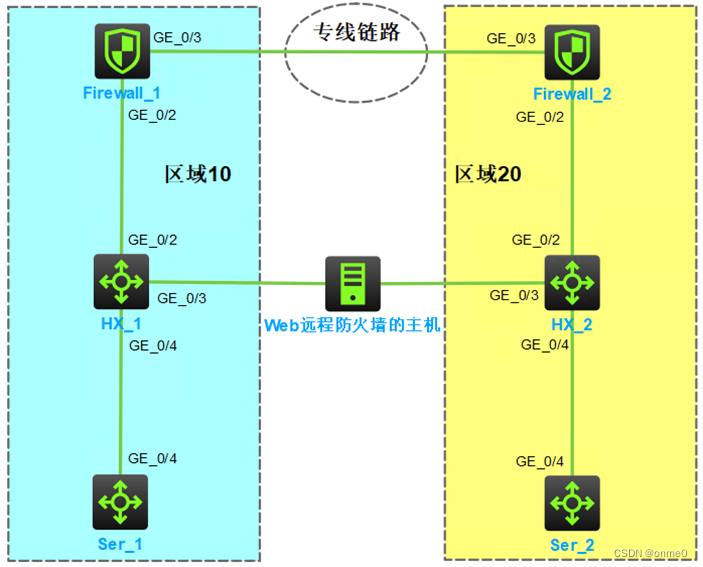
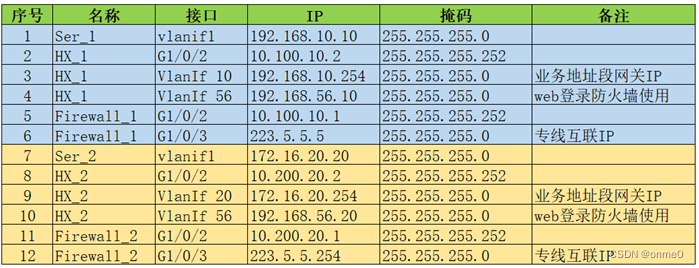
1.4 组网设备配置
1.4.1 Ser_1设备配置
[H3C]sysname Ser_1
[Ser_1]interface Vlan-interface1
[Ser_1-Vlan-interface1] ip address 192.168.10.10 255.255.255.0
[Ser_1-Vlan-interface1]quit
[Ser_1]#
[Ser_1]telnet server enable
#自定义telnet服务的端口为11223
[Ser_1]telnet server port 11223
#添加设备的用户名和密码
[Ser_1]local-user admin
[Ser_1-luser-manage-admin]password simple admin
[Ser_1-luser-manage-admin]service-type telnet
[Ser_1-luser-manage-admin]authorization-attribute user-role level-15
[Ser_1-luser-manage-admin]quit
[Ser_1]line console 0
#console登陆设备,设置永不超时退出
[Ser_1-line-console0]idle-timeout 0
[Ser_1-line-console0]quit
[Ser_1]line vty 0 4
[Ser_1-line-vty0-4] authentication-mode scheme
[Ser_1-line-vty0-4]quit
[Ser_1]ip route-static 0.0.0.0 0 192.168.10.254
[Ser_1]
1.4.2 HX_1设备配置
[H3C]sysname HX_1
####################web登录防火墙使用####################
[HX_1]vlan 56
[HX_1-vlan56]interface Vlan-interface56
[HX_1-Vlan-interface56] ip address 192.168.56.10 255.255.255.0
[HX_1-Vlan-interface56]interface GigabitEthernet1/0/3
[HX_1-GigabitEthernet1/0/3] port access vlan 56
[HX_1-GigabitEthernet1/0/3]quit
####################web登录防火墙使用####################
[HX_1]vlan 10
[HX_1-vlan10]interface Vlan-interface10
[HX_1-Vlan-interface10] ip address 192.168.10.254 255.255.255.0
[HX_1-Vlan-interface10]quit
[HX_1]interface GigabitEthernet1/0/2
[HX_1-GigabitEthernet1/0/2] port link-mode route
[HX_1-GigabitEthernet1/0/2] ip address 10.100.10.2 255.255.255.252
[HX_1-GigabitEthernet1/0/2]quit
[HX_1]#
[HX_1]interface GigabitEthernet1/0/4
[HX_1-GigabitEthernet1/0/4] port access vlan 10
[HX_1-GigabitEthernet1/0/4]quit
[HX_1]line console 0
[HX_1-line-console0]idle-timeout 0
[HX_1-line-console0]quit
[HX_1]
1.4.3 Firewall_1设备配置
[H3C]sysname Firewall_1
#修改admin账户的登录密码
[Firewall_1]local-user admin
[Firewall_1-luser-manage-admin]password simple telnet12345
[Firewall_1-luser-manage-admin]quit
[Firewall_1]line console 0
#去除console登陆验证的配置
[Firewall_1-line-console0]undo authentication-mode
[Firewall_1-line-console0]idle-timeout 0
[Firewall_1-line-console0]quit
[Firewall_1]#
#配置回执给HX_1设备的静态路由——回执路由
[Firewall_1]ip route-static 192.168.10.0 24 10.100.10.2
#web登录防火墙的作用——回执路由
[Firewall_1]ip route-static 192.168.56.0 24 10.100.10.2
[Firewall_1]
[Firewall_1]interface GigabitEthernet1/0/2
[Firewall_1-GigabitEthernet1/0/2] ip address 10.100.10.1 255.255.255.252
[Firewall_1-GigabitEthernet1/0/2]quit
[Firewall_1]#
[Firewall_1]interface GigabitEthernet1/0/3
[Firewall_1-GigabitEthernet1/0/3] ip address 223.5.5.5 255.255.255.0
[Firewall_1-GigabitEthernet1/0/3]quit
[Firewall_1]#
[Firewall_1]security-zone name Trust
[Firewall_1-security-zone-Trust] import interface GigabitEthernet1/0/2
[Firewall_1-security-zone-Trust]quit
[Firewall_1]#
[Firewall_1]security-zone name Untrust
[Firewall_1-security-zone-Untrust] import interface GigabitEthernet1/0/3
[Firewall_1-security-zone-Untrust]quit
[Firewall_1]
#自定义服务,添加TCP 11223端口服务
[Firewall_1]object-group service telnet11223
[Firewall_1-obj-grp-service-telnet11223] service tcp destination eq 11223
#自定义服务,添加TCP 21223端口服务
[Firewall_1-obj-grp-service-telnet11223]object-group service telnet21223
[Firewall_1-obj-grp-service-telnet21223] service tcp destination eq 21223
[Firewall_1-obj-grp-service-telnet21223]#
#配置nat地址转换策略
[Firewall_1] nat global-policy
#配置双向地址转换nat策略sx_telnet21223,允许源地址段192.168.10.0/24访问目标10.100.10.1的tcp 21223,源地址转换成223.5.5.5(easy-ip技术),目标转换成223.5.5.5的TCP 21223
[Firewall_1-nat-global-policy] rule name sx_telnet21223
[Firewall_1-nat-global-policy-rule-sx_telnet21223]service telnet21223
[Firewall_1-nat-global-policy-rule-sx_telnet21223]source-zone Trust
[Firewall_1-nat-global-policy-rule-sx_telnet21223]destination-ip host 10.100.10.1
[Firewall_1-nat-global-policy-rule-sx_telnet21223]source-ip subnet 192.168.10.0 24
[Firewall_1-nat-global-policy-rule-sx_telnet21223]action snat easy-ip
[Firewall_1-nat-global-policy-rule-sx_telnet21223]action dnat ip-address 223.5.5.254 local-port 21223
[Firewall_1-nat-global-policy-rule-sx_telnet21223]counting enable
[Firewall_1-nat-global-policy-rule-sx_telnet21223]quit
#配置双向地址转换nat策略sx_telnet11223,允许源地址223.5.5.254访问目标223.5.5.5的tcp 11223,源地址转换成10.100.10.1 (easy-ip技术),目标转换成192.168.10.10的TCP 11223。
[Firewall_1-nat-global-policy] rule name sx_telnet11223
[Firewall_1-nat-global-policy-rule-sx_telnet11223]service telnet11223
[Firewall_1-nat-global-policy-rule-sx_telnet11223]source-zone Untrust
[Firewall_1-nat-global-policy-rule-sx_telnet11223]source-ip host 223.5.5.254
[Firewall_1-nat-global-policy-rule-sx_telnet11223]destination-ip host 223.5.5.5
[Firewall_1-nat-global-policy-rule-sx_telnet11223]action snat easy-ip
[Firewall_1-nat-global-policy-rule-sx_telnet11223] action dnat ip-address 192.168.10.10 local-port 11223
[Firewall_1-nat-global-policy-rule-sx_telnet11223]counting enable
[Firewall_1-nat-global-policy-rule-sx_telnet11223]quit
[Firewall_1-nat-global-policy]
#配置全域默认放通的应用安全策略
[Firewall_1]security-policy ip
[Firewall_1-security-policy-ip] rule 3 name any-all
[Firewall_1-security-policy-ip-3-any-all] action pass
[Firewall_1-security-policy-ip-3-any-all] logging enable
[Firewall_1-security-policy-ip-3-any-all] counting enable
[Firewall_1-security-policy-ip-3-any-all]quit
[Firewall_1-security-policy-ip]quit
[Firewall_1]
1.4.4 Ser_2设备配置
[H3C]sysname Ser_2
[Ser_2]interface Vlan-interface1
[Ser_2-Vlan-interface1] ip address 172.16.20.20 255.255.255.0
[Ser_2-Vlan-interface1]quit
[Ser_2]
[Ser_2]telnet server enable
[Ser_2]#自定义telnet服务的端口为21223
[Ser_2]telnet server port 21223
[Ser_2]#添加设备的用户名和密码
[Ser_2]local-user admin
[Ser_2-luser-manage-admin]password simple admin
[Ser_2-luser-manage-admin]service-type telnet
[Ser_2-luser-manage-admin]authorization-attribute user-role level-15
[Ser_2-luser-manage-admin]quit
[Ser_2]line console 0
[Ser_2-line-console0]idle-timeout 0
[Ser_2-line-console0]quit
[Ser_2]line vty 0 4
[Ser_2-line-vty0-4] authentication-mode scheme
[Ser_2-line-vty0-4]quit
[Ser_2] ip route-static 0.0.0.0 0 172.16.20.254
[Ser_2]#
1.4.5 HX_2设备配置
[H3C]sysname HX_2
####################web登录防火墙使用####################
[HX_2]vlan 56
[HX_2-vlan56]interface Vlan-interface56
[HX_2-Vlan-interface56] ip address 192.168.56.20 255.255.255.0
[HX_2-Vlan-interface56]quit
[HX_2]interface GigabitEthernet1/0/3
[HX_2-GigabitEthernet1/0/3] port access vlan 56
[HX_2-GigabitEthernet1/0/3]quit
####################web登录防火墙使用####################
[HX_2]vlan 20
[HX_2-vlan20]interface Vlan-interface20
[HX_2-Vlan-interface20] ip address 172.16.20.254 255.255.255.0
[HX_2-Vlan-interface20]quit
[HX_2]interface GigabitEthernet1/0/2
[HX_2-GigabitEthernet1/0/2] port link-mode route
[HX_2-GigabitEthernet1/0/2] ip address 10.200.20.2 255.255.255.252
[HX_2-GigabitEthernet1/0/2]quit
[HX_2]interface GigabitEthernet1/0/4
[HX_2-GigabitEthernet1/0/4] port access vlan 20
[HX_2-GigabitEthernet1/0/4]quit
[HX_2]line console 0
[HX_2-line-console0]idle-timeout 0
[HX_2-line-console0]quit
[HX_2] ip route-static 0.0.0.0 0 10.200.20.1
[HX_2]
1.4.6 Firewall_2设备配置
[H3C]sysname Firewall_2
[Firewall_2]interface GigabitEthernet1/0/2
[Firewall_2-GigabitEthernet1/0/2] ip address 10.200.20.1 255.255.255.252
[Firewall_2-GigabitEthernet1/0/2]quit
[Firewall_2]#
[Firewall_2]interface GigabitEthernet1/0/3
[Firewall_2-GigabitEthernet1/0/3] ip address 223.5.5.254 255.255.255.0
[Firewall_2-GigabitEthernet1/0/3]quit
[Firewall_2]security-zone name Trust
[Firewall_2-security-zone-Trust] import interface GigabitEthernet1/0/2
[Firewall_2-security-zone-Trust]security-zone name Untrust
[Firewall_2-security-zone-Untrust] import interface GigabitEthernet1/0/3
[Firewall_2-security-zone-Untrust]quit
[Firewall_2]
#配置回执给HX_2设备的静态路由——回执路由
[Firewall_2]ip route-static 172.16.20.0 24 10.200.20.2
#web登录防火墙的作用——回执路由
[Firewall_2]ip route-static 192.168.56.0 24 10.200.20.2
[Firewall_2]
#修改admin账户的登录密码
[Firewall_2]local-user admin
[Firewall_2-luser-manage-admin]password simple telnet12345
[Firewall_2-luser-manage-admin]quit
[Firewall_2]#
[Firewall_2]line console 0
[Firewall_2-line-console0]undo authentication-mode
[Firewall_2-line-console0]idle-timeout 0
[Firewall_2-line-console0]quit
[Firewall_2]#
#自定义服务,添加TCP 21223端口服务
[Firewall_2]object-group service telnet21223
[Firewall_2-obj-grp-service-telnet21223] service tcp destination eq 21223
[Firewall_2-obj-grp-service-telnet21223]quit
#配置nat地址转换策略
[Firewall_2]nat global-policy
[Firewall_2-obj-grp-service-telnet21223]nat global-policy
#配置目的地址转换策略d_telnet21223,内网IP的172.16.20.20 tcp端口21223映射给223.5.5.254的21223并允许源区域Untrust的所有主机访问
[Firewall_2-nat-global-policy] rule name d_telnet21223
[Firewall_2-nat-global-policy-rule-d_telnet21223]service telnet21223
[Firewall_2-nat-global-policy-rule-d_telnet21223]source-zone Untrust
[Firewall_2-nat-global-policy-rule-d_telnet21223]destination-ip host 223.5.5.254
[Firewall_2-nat-global-policy-rule-d_telnet21223] action dnat ip-address 172.16.20.20 local-port 21223
[Firewall_2-nat-global-policy-rule-d_telnet21223]counting enable
[Firewall_2-nat-global-policy-rule-d_telnet21223]quit
#配置源地址转换策略s,允许内网172.16.20.0/24访问223.5.5.5
[Firewall_2-nat-global-policy] rule name s
[Firewall_2-nat-global-policy-rule-s]source-zone Trust
[Firewall_2-nat-global-policy-rule-s]source-ip subnet 172.16.20.0 24
[Firewall_2-nat-global-policy-rule-s]action snat easy-ip
[Firewall_2-nat-global-policy-rule-s]counting enable
[Firewall_2-nat-global-policy-rule-s]quit
#配置全域默认方通的应用安全策略
[Firewall_2-nat-global-policy]security-policy ip
[Firewall_2-security-policy-ip] rule 20 name any-all
[Firewall_2-security-policy-ip-20-any-all] action pass
[Firewall_2-security-policy-ip-20-any-all] logging enable
[Firewall_2-security-policy-ip-20-any-all] counting enable
[Firewall_2-security-policy-ip-20-any-all]quit
[Firewall_2-security-policy-ip]quit
[Firewall_2]
1.4.7 Windows主机路由配置
在安装HCL软件的Windows系统主机上,以管理员权限打开命令提示符(CMD),输入以下命令添加相关静态明细路由。
#Web远程Firewall_1的路由配置
route add 10.100.10.0 mask 255.255.255.0 192.168.56.10
#Web远程Firewall_2的路由配置
route add 10.200.20.0 mask 255.255.255.0 192.168.56.20
1.5 测试验证组网的目标
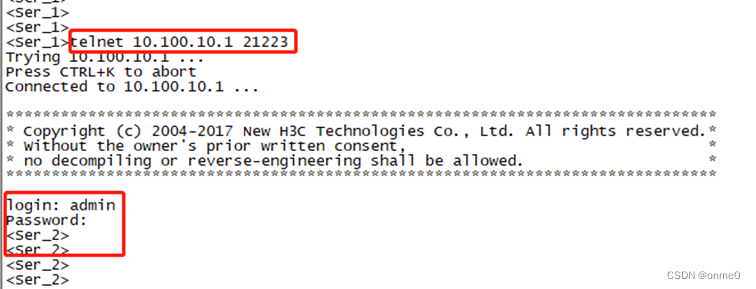
1.5.1 Ser_1设备telnet访问Ser_2
Ser_1设备telnet访问Ser_2,访问方式:telnet 10.100.10.1 21223,访问测试结果如下图所示;
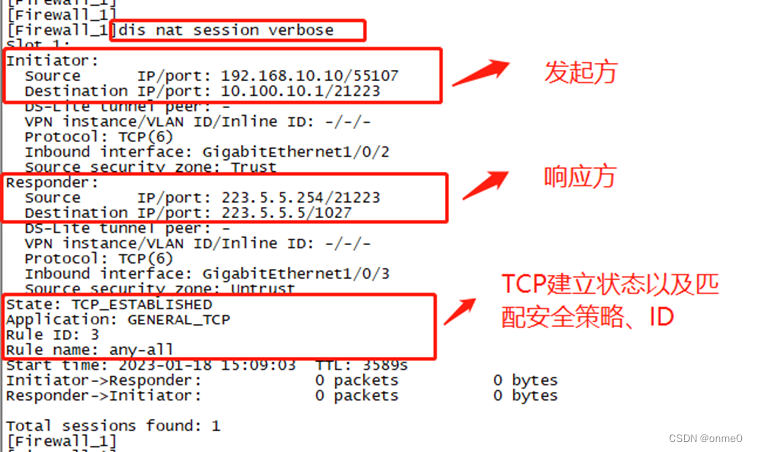
#通过命令“dis nat session verbose”查看Firewall_1设备nat会话表(对应双向地址转换),如下图所示;
从发起方来看:源IP是192.168.10.10,目标IP是10.100.10.1;
从响应方来看:源IP是223.5.5.254,目标IP是223.5.5.5;
对比来看:当Ser_1设备telnet 10.100.10.1 21223时,在Firewall_1上,源IP192.168.10.10转换成223.5.5.5,目标IP10.100.10.1转换成223.5.5.254,即双向地址转换。
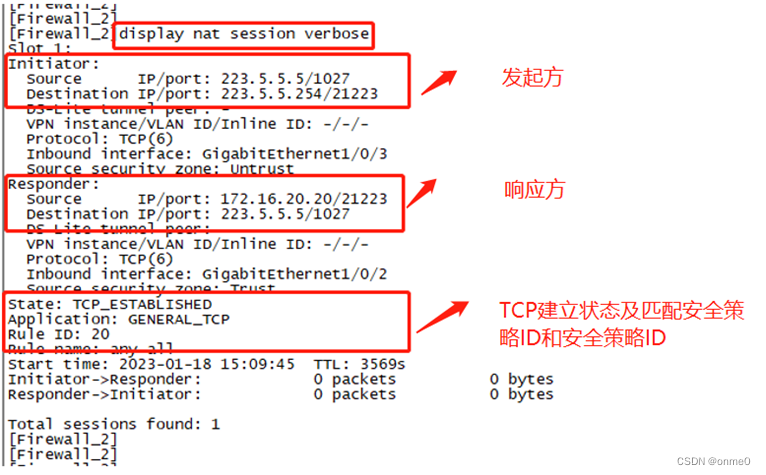
#通过命令“dis nat session verbose”查看Firewall_2设备nat会话表(对应目的地址转换),如下图所示;
从发起方来看:源IP是223.5.5.5,目标IP是223.5.5.254;
从响应方来看:源IP是172.16.20.20,目标IP是223.5.5.5;
对比来看:当Ser_1设备telnet 10.100.10.1 21223时,在Firewall_2上,目标IP223.5.5.254转换成172.16.20.20,即目标地址转换。
1.5.2 Ser_2设备telnet访问Ser_1
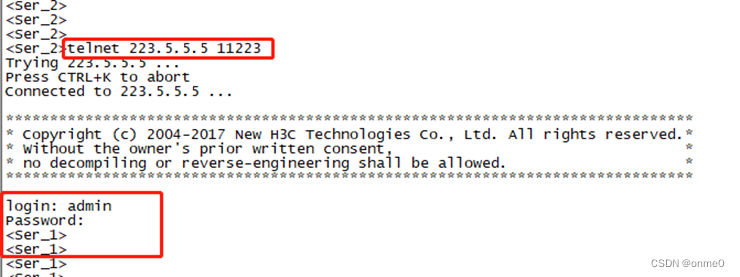
Ser_2设备telnet访问Ser_1,访问方式:telnet 223.5.5.5 11223,访问测试结果如下图所示;
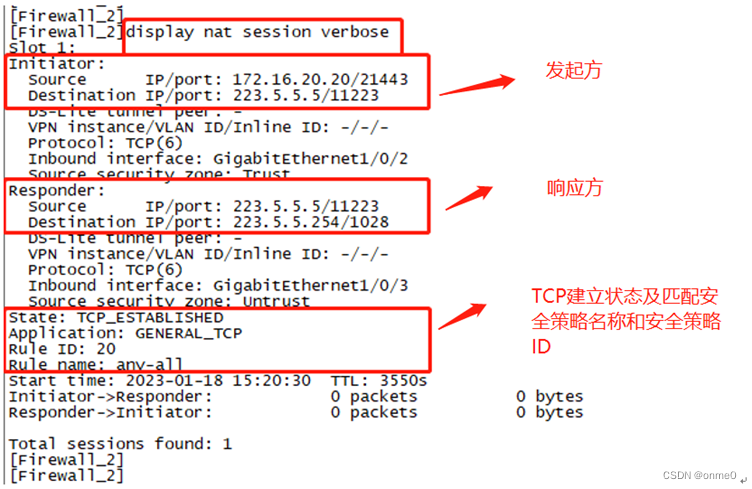
#通过命令“dis nat session verbose”查看Firewall_2设备nat会话表(对应源地址转换),如下图所示;
从发起方来看:源IP是172.16.20.20,目标IP是223.5.5.5;
从响应方来看:源IP是223.5.5.5,目标IP是223.5.5.254;
对比来看:当Ser_2设备telnet 223.5.5.5 11223时,在Firewall_2上,源IP172.16.20.20转换成223.5.5.254,即源地址转换。
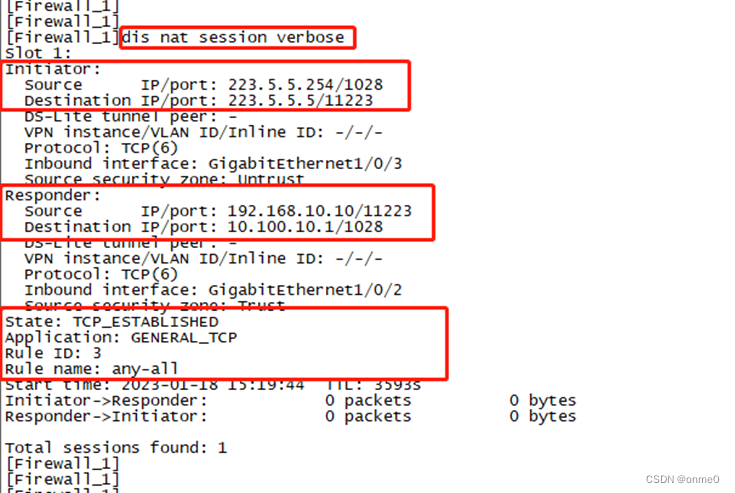
#通过命令“dis nat session verbose”查看Firewall_1设备nat会话表(对应双向地址转换),如下图所示;
1.6 总结
Ser_1设备telnet访问Ser_2,HX_1未配置默认路由指向指向Firewall_1,访问方式是:telnet 10.100.10.1 21223,而10.100.10.1是区域10的内网IP;
Ser_2设备telnet访问Ser_1,HX_2必须配置默认路由指向Firewall_2,访问方式:telnet 223.5.5.5 11223,而223.5.5.5是区域10 Firewall_1设备专线链路接口的IP。
























 1122
1122











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










