基于跳表的云存储隐私保护TPA审计方案
摘要
Recently, researchers have proposed several privacy preserving public auditing schemes to remotely check the integrity of outsourced data based on homomorphic authenticators, random block sampling and random masking techniques. However, almost all these schemes require users to maintain tables related to the block index. These tables are difficult to maintain, especially when the outsourced data is frequently updated. In this paper, we propose a privacy-preserving public auditing scheme with the support of dynamics using rank-based authenticated skip list for the integrity of the data in cloud storage, of which users do not need to maintain the relevant table. And we give a formal security proof for data integrity guarantee and analysis for privacy-preserving property of the audit protocol. The performance analysis demonstrates that our scheme is highly efficient.
最近,研究人员提出了几种保护隐私的公共审计方案,以基于同态身份验证器,随机块采样和随机掩盖技术来远程检查外包数据的完整性。但是,几乎所有这些方案都要求用户维护与块索引相关的表。这些表很难维护,尤其是在经常更新外包数据时。在本文中,我们提出了一种保护隐私的公共审计方案,该方案使用基于秩的身份验证跳表来动态支持云存储中数据的完整性,而用户无需维护相关表。并且我们为数据完整性保证提供了形式化安全证明,并分析了审计协议的隐私保护特性。性能分析表明,我们的方案是高效的。
Keywords: Audit Protocol; Cloud Storage; Privacypreserving; Public Auditing; Rank-based Authenticated Skip List
关键字:审计协议;云储存;隐私保护;公共审计;基于秩验证跳表
1 Introduction
Cloud computing has many advantages; this has led to an increasing number of individuals and companies choosing to store their data and conduct their business using cloud-based services [22]. Unlike traditional systems, users lose their physical control over their data. Although the cloud infrastructure is significantly more reliable than personal computing devices, data security/privacy is still one of the core considerations for users when adopting cloud services because of the internal and external threats associated with cloud services [1,35,38]. Therefore, researchers have proposed various security models and schemes to overcome the issue of data integrity auditing [3,12–15,18,20,27,29–31,33,34,36,37].
云计算有许多优点;这导致了越来越多的个人和公司选择使用云服务来存储数据和开展业务[22]。与传统系统不同,用户失去了对数据的物理控制。尽管云基础设施比个人计算设备更加可靠,但由于与云服务相关的内部和外部威胁,数据安全/隐私仍然是用户采用云服务时的核心考虑因素之一[1,35,38]。因此,研究人员提出了各种安全模型和方案来解决数据完整性审计问题[3,12-15,18,20,27,29-31,33,34,36,37]。
The public auditable schemes allow external parties, in addition to the user, to audit the integrity of outsourced data; however, this could potentially leak the user’s data to auditors. Hence, researchers have proposed privacy-preserving public auditing schemes to avoid auditors learning user’s data in the auditing phase. The construction of the signatures in some of these schemes involve the block index information i, such as H(name||i) or H(Bi || Vi || Ri)[30,36,37]。 Users need to maintain a table in the local storage for each file, such as mapversion Table [5] or index-hash table [36,37]. The table is also sent to the third-party auditor (TPA) before the data is audited. If the table is corrupted, effective audits or dynamic operations cannot be conducted on the outsourced data. In addition, if a large file is stored in cloud storage server (CSS) and undergoes frequent insert and delete operations, the block index will continue to increase and become very large. This is because the block index cannot be reused. Consequently, it becomes increasingly difficult for users to maintain the table. To address the problem, the index i is removed, and H(mi) is used in constructing the signature for block mi to prevent replay attack on the same hash values.
公共可审计方案允许除了用户之外的外部各方,来审计外包数据的完整性。但是,这可能会将用户的数据泄漏给审计员。因此,研究者提出了保护隐私的公共审计方案,以避免审计人员在审计阶段获取用户数据。在这其中一些方案中,签名的构造包含了块索引信息 i,例如H(name||i)或者H(Bi || Vi || Ri)[30,36,37]。用户需要为每个文件在本地存储中维护一个表,例如mapversion table[5]或index hash table[36,37]。在审计数据之前,该表也会发送给第三方审计师(TPA)。如果表已损坏,则无法对外包数据执行有效的审核或动态操作。此外,如果一个大文件存储在云存储服务器(CSS)中,并且经常进行插入和删除操作,则块索引将继续增加并变得非常大。这是因为块索引不能重用。因此,用户越来越难以维护表。为了解决这个问题,删除索引 i,并使用H(mi)构造块mi的签名,以防止对相同散列值的重放攻击。为了支持保护隐私的TPA审计,在签名构造中使用(H(mi))^α/β,并将其分配给跳表的叶节点的数据项值[9]。
In this paper, a secure public auditing algorithm is proposed with the support of dynamics using a rank-based authenticated skip list [9] for the outsourced data. The contributions of this paper can be summarized as follows:
1)A privacy-preserving public auditing scheme which fully supports dynamics by employing rank-based authenticated skip list is proposed. (H(mi))^α/β is used as the data item of the bottom node of the skip list to realize privacy-preserving.
2) Based on the cryptography reduction theory [16,21] and CPoR’s model [27] a formal security proof is given for the integrity guarantee of outsourced data and privacy-preserving property of the auditing phase for the scheme.
The remainder of the paper is organized as follows. Section 2 contains the related work. Section 3 introduces the system model and our design goals. In Section 4, we elaborate our proposed scheme. Section 5 analyzes the security and performance of our scheme. The conclusion is given in Section 6.
本文提出了一种完全支持动态的对外包数据的安全公共审计算法,它使用基于秩的认证跳表[9]。本文的贡献概括如下:
1)提出了一个具有隐私保护性的完全支持动态修改的公共审计方法,其中 (H(mi))^α/β作为跳转列表底部节点的数据项,实现隐私保护。
2)基于密码学简化理论[16,21]和CPoR模型[27],给出了该方案审计阶段外包数据完整性保证和隐私保护特性的形式化安全证明。
论文的其余部分安排如下。第二节是相关工作。第三部分介绍了系统模型和我们的设计目标。在第四节中,我们详细阐述了我们提出的方案。第五节分析了本方案的安全性和性能。结论见第6节。
2 Related Work
Ateniese et al. proposed the provable data possession (PDP) model, which can be used for remotely checking data integrity [2,3]. This model can generate probabilistic proofs of possession by randomly sampling data blocks from the server, in which the tags of the sampled blocks can be aggregated into a single value using homomorphic verifiable tags(HVTs). It is believed to be the first scheme to provide blockless verification and public verifiability at the same time. Erway et al. proposed dynamic PDP (DPDP), which applies the structure of rank-based authenticated skip list to ensures the integrity of the tags using the skip list structure and the integrity of the blocks by their tags. This scheme effectively supports provable secure updates to the remotely stored data [9]. Juels and Kaliski presented the proof of retrievability (PoR) model. This model ensures both the possession and the retrievability of outsourced data by using spot-checking and error-correcting codes. However, the number of audit challenges a user can perform is predetermined and public auditability is not supported in [15].
Ateniese等人。提出了可证明的数据占有(PDP)模型,可用于远程数据完整性检查[2,3]。该模型可以通过从服务器随机抽取数据块来生成其拥有的概率证明,其中,可以使用同态可验证标记(HVTs)将被采样块的标记聚合为单个值。这被认为是第一个同时提供无阻塞验证和公共验证的方案。Erway等人。提出了一种动态PDP(DPDP),它采用基于秩的认证跳表结构,来保证使用跳表结构的标签的完整性,并通过标签保证块的完整性。该方案有效地支持对远程存储数据进行可验证的安全更新[9]。Juels和Kaliski提出了可检索性验证(PoR)模型。该模型通过使用抽样检查和纠错码,保证了外包数据的拥有和可检索性。然而,用户可以执行的审计挑战的数量是预先确定的,并且在[15]中不支持公共审计性。
Shacham et al. designed a compact version of PoR (CPoR) [27] and proved the security of their scheme against arbitrary adversaries in the Juel-Kaliski model. The construction of the publicly verifiable CPoR scheme is based on Boneh-Lynn-Shacham (BLS) signatures [8]. Wang et al. proposed a public auditing scheme that supports dynamic data operations in [31]. The authentication information of the scheme is managed using the Merkle hash tree (MHT) [23], in which the leaf nodes are the values of H(mi)(mi is the i-th block of the file). To prevent TPA extracting data content from the collected information, they designed a privacy-preserving public auditing scheme using a random mask technique to blind the response information in the follow-up work [30]. But its description for the dynamics is ambiguous. Zhu et al. proposed another privacy-preserving public auditing scheme which supported dynamic data updates employing an index-hash table [36]. However, in these two privacypreserving schemes, block index related information is involved in the signature construction. Users are required to maintain a relevant table. To guarantee the integrity of the multiple replicas in cloud, Curtmola et al. proposed the replication-based remote data auditing scheme, called Multiple-Replica PDP (MR-PDP), which extends the (single-copy) PDP scheme for overcoming the collusion attack in a multi-server environment. However, MRPDP only supports private verification [7].
Shacham等人。在Juel-Kaliski模型中设计了PoR(CPoR)[27]的一个紧凑版本,并证明了其方案对任意对手的安全性。可公开验证的CPoR方案的构建基于Boneh Lynn Shacham(BLS)签名[8]。Wang等人。文[31]提出了一种支持动态数据操作的公共审计方案。该方案的认证信息使用Merkle哈希树(MHT)[23]来管理,其中叶节点是H(mi)的值(mi是文件的第i个块)。为了防止TPA从收集到的信息中提取数据内容,他们设计了一个隐私保护的公共审计方案,使用随机掩码技术来屏蔽重复任务的响应信息[30]。但它对动态的描述很模糊。朱等人。提出了另一种保护隐私的公共审计方案,该方案支持使用索引哈希表的动态数据更新[36]。然而,在这两个方案中,与块索引相关的信息参与了签名的构造。用户需要维护一个相关的表。为了保证云中多个副本的完整性,Curtmola等人。提出了一种基于副本的远程数据审计方案,称为多副本PDP(MR-PDP),该方案扩展了单副本PDP(single-copy)方案以克服多服务器环境下的合谋攻击。然而,MRPDP只支持私有验证[7]。
Barsoum et al. proposed two multi-copy DPDP public auditing schemes, supporting data dynamics based on the MHT and map-version table, respectively. Different copies are generated through encrypting the concatenation of the copy number and file blocks [5]. In the latter, the map-version table must be stored in the local storage of the user and is managed by the user during the various update operations performed on the file. In [34], Yang et al. propose a public auditing scheme for shared cloud data in which a group manager is introduced to help members generate authenticators to protect the identity privacy. This method uses two lists to record the members who performed the most-recent modification on each block to achieve the identity traceability. This scheme also achieves data privacy during authenticator generation by employing a blind signature technique. To overcome the issue of resource-constrained users dealing with heavy burdens, Shen et al. proposed a cloud storage auditing scheme for group users by introducing a third party medium (TPM) to perform time-consuming operations on behalf of users [29]. Utilizing proxy re-signatures and homomorphic linear authenticators, Li et al. propose a privacy-preserving cloud data audit scheme that can support key-updating and authenticator-evolving [18]. Researchers have proposed a number of cloud storage auditing schemes in the recent past. All these schemes primarily focus on several different aspects of cloud storage auditing. However, almost none of these schemes address the issue that users need to maintain a block index related table in the local storage for the privacy-preserving public auditing schemes. Users should be “stateless” and must not be required to store and update the table between different dynamic operations, since such table is difficult to maintain.
Barsoum等人。提出了两种多备份DPDP公共审计方案,分别支持基于MHT和映射表的数据动态性。通过对拷贝号和文件块相关内容的编码,生成不同的拷贝[5]。在后者中,映射表必须存储在用户的本地存储中,并由用户在文件上执行的各种更新操作期间进行管理。在[34]中,Yang等人。提出了一种共享云数据的公共审计方案,该方案引入分组管理者,帮助成员生成身份验证器以保护身份隐私。此方法使用两个列表记录对每个块执行最新修改的成员,以实现身份跟踪。该方案还利用盲签名技术实现了认证器生成过程中的数据保密。为了克服资源受限的用户处理繁重负担的问题,沈等人。通过引入第三方介质(TPM)来代表用户执行耗时的操作,提出了一种面向组用户的云存储审计方案[29]。Li等人利用代理重签名和同态线性认证器。提出了一种隐私保护的云数据审计方案,该方案能够支持密钥更新和认证器进化[18]。最近,研究人员提出了许多云存储审计方案。所有这些方案主要关注云存储审计的几个不同方面。然而,这些方案中几乎没有一个解决了这样一个问题:用户需要在本地存储中维护一个块索引相关表,以用于隐私保护的公共审计方案。用户应该是“无状态的”,不需要在不同的动态操作之间存储和更新表,因为这样的表很难维护。
3 Problem Statements
3.1 System Model
The auditing system for cloud storage involves cloud users, CSS and TPA as shown in Figure 1. The cloud user is the data owner, who has large amount of data to be stored in the CSS. The users can access and dynamically update their data in the CSS by interacting with the CSS. The CSS, which is managed by the cloud service provider (CSP), has significant storage space and massive amount of computational resources. The users’ data is stored in the cloud storage and is managed and maintained by the CSP. The TPA has expertise and capabilities that users do not have and can audit the users’ outsourced data in the CSS on behalf of users at the users’ request.
To ensure the integrity and correctness of the users’ outsourced data, users need to make periodic checks. To save computation resources and network bandwidth, users can delegate the TPA to perform the periodic data integrity verification. However, users do not want information from their data to be learned by the TPA during the auditing process. In this model, it is assumed that the cloud server does not have the incentive to reveal their hosted data to any external entity. It is also assumed that the TPA has no incentive to collude with either the CSP or the user during the auditing process. However, it is interested in the users’ data.

图1:云存储架构包括CSS、云用户和TPA
云存储审计系统涉及云用户、CSS和TPA,如图1所示。云用户是数据所有者,它有大量数据要存储在CSS中。用户可以通过与CSS交互来访问和动态更新CSS中的数据。**CSS由云服务提供商(CSP)管理,拥有巨大的存储空间和大量的计算资源。**用户的数据存储在云存储中,由CSP管理和维护。TPA拥有用户不具备的专业知识和能力,可以应用户要求代表用户在CSS中审计用户的外包数据。
为了保证用户外包数据的完整性和正确性,用户需要定期进行检查。为了节省计算资源和网络带宽,用户可以委托TPA执行定期的数据完整性验证。但是,用户不希望TPA在审计过程中从其数据中获取信息。在此模型中,假设云服务器没有向任何外部实体显示其托管数据的动机。还假设在审计过程中,TPA没有与CSP或用户串通的动机。然而,而它对用户的数据感兴趣。
3.2 Design Goals
In the aforementioned model, a scheme is proposed in which the design goals can be summarized as follows [19]:
- Public auditability: To allow any authorized TPA to verify the integrity of the cloud data without retrieving a copy of the whole data;
- Storage correctness: To ensure that there no CSP exists that can pass the audit of the TPA without storing cloud users’ data intact;
- Privacy preserving: To ensure that it is infeasible for the TPA to recover the user’s data from the information collected during the auditing phase;
- High performance: The TPA can perform data auditing with minimum communication and computation overhead;
- Dynamic data: To allow the data owners to modify, insert and delete data blocks in the cloud storage when they want to update their data at any time;
- Batch auditing: The TPA can audit the data of different users at the same time.
3.2设计目标
在上述模型中,提出了一种方案,其中设计目标可概括如下[19]:
1) 公共可审计性:允许任何授权的TPA在不检索整个数据副本的情况下验证云数据的完整性;
2) 存储正确性:确保不存在任何完整存储云用户数据却能通过TPA审计的CSP
3) 隐私保护:确保TPA无法从审计阶段收集的信息中恢复用户数据;
4) 高性能:TPA能够以最小的通信和计算开销进行数据审计; 5) 动态数据:允许数据所有者在需要随时更新数据时,修改、插入和删除云存储中的数据块;
6) 批量审核:TPA可以同时审核不同用户的数据。
4 The Proposed Construction
4.1 Preliminaries
Relevant functions. A pseudo-random function (PRF) f and a pseudo-random permutation (PRP) π are used with the following parameters [3]:
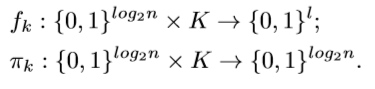
Bilinear maps. Suppose a group G is a Gap DiffieHellman (GDH) group with prime order p. GT is another multiplicative cyclic group with prime order p. Then, the bilinear map is a map e : G ×G → GT with the following properties [8]:
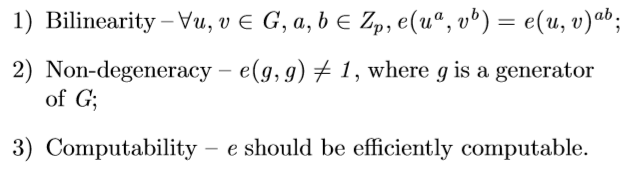
4提出贡献
4.1预备工作
相关职能。伪随机函数(PRF)f和伪随机置换(PRP)π与以下参数一起使用[3]:
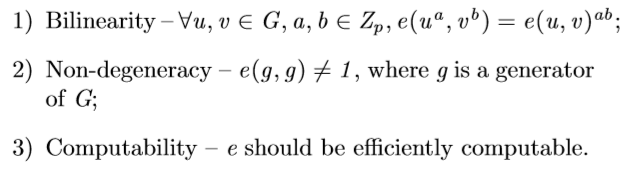
双线性映射。假设一个组G是一个具有素数阶p的Gap Diefellman(GDH)群。GT是另一个具有素数阶p的乘法循环组。然后,双线性映射是一个具有以下性质的映射e:G×G→GT[8]:
1) 双线性-任意u,v∈G,a,b∈Zp,e(ua,vb)=e(u,v)ab;
2)非简并性-e(g,g)!=1,其中g是G的一个生成器;
3) 可计算性——e应该是高效可计算的。
为了简单起见,下面的方案描述使用对称双线性映射。不对称双线性映射为e:G1×G2→GT。

基于秩的跳表[9,11,24]。在0级(底层)上,与第i个节点v相关的主要信息包括:第i个节点l(v)的级别、第i个节点r(v)的秩、第i个节点的数据项T(mi)和第i个节点f(v)的标签;在非底层包括:节点l(v)的级别、节点r(v)的秩、节点f(v)的标签;除此之外,每个节点包含一些与跳表结构相关的信息,例如右指针和下指针。
节点的秩值指示从该节点出发的可到达的底部节点(或叶节点)的数目。空节点的秩等于0。每个底部节点的位置可以根据相关节点的秩值来计算。底层节点的标签值为 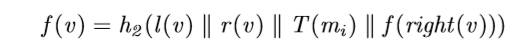
在底层节点中为:
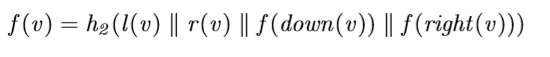
where the symbol “||” denotes concatenation, f (down(v)) and f (right(v)) are the label of the down and right node of v, respectively. The label value of a Null node is 0. The function h2(·) is a collision-resistant cryptographic hash function. Users hold the label f (s) of the top leftmost node (or start node) of the skip list. The f (s) is called the basis (or root). It is equivalent to the user’s verification metadata. To obtain the proof information of some block i, the skip list needs traversing from the start node vk to the node v1 associated with block i through the rank of the nodes. The reverse path v1,··· ,vk is called verification path of the block i, as shown in Figure 2. The information of the nodes x0,y0 −y3 and v1 −v2 is used as auxiliary authentication information (AAI) for calculating each rank and label value from v1 to vk on the verification path.
其中符号“| |”表示连接,f(向下(v))和f(向右(v))分别是v的向下和向右节点的标签。空节点的标签值为0。函数h2(·)是一个抗冲突的加密哈希函数。用户持有跳表最左上角节点(或开始节点)的标签f(s)。f(s)称为基(或根)。它相当于用户的验证元数据。为了获得某个块i的证明信息,跳表需要通过节点的秩从开始节点vk遍历到与块i相关联的节点v1。反向路径v1,····,vk称为块i的验证路径,如图2所示。节点x0、y0-y3和v1-v2的信息用作辅助认证信息(AAI),用于计算验证路径上从v1到vk的每个秩和标签值。

The proof of a block is composed of a sequence of tuples made of the relevant information of each node on the verification path. That is, the proof for block i with data T(mi) is a sequence Πi = (A(v1),··· ,A(vk)) where A(vj) = (l(vj),q(vj),d(vj),g(vj)),1 ≤ j ≤ k, from which we can get the AAI. The l(vj) is the level of the node and Boolean d(vj) indicates whether vj−1 is to the right or below vj. The value of g(vj) is used to calculate the label of the corresponding node along the verification path. For the non-bottom level nodes, if d(vj) = rgt, then g(vj) = f (dwn(vj)), else if d(vj) = dwn, then g(vj) = f (rgt(vj)). For bottom-level nodes vj(j > 1) on the verification path, the value of g(vj) is the data item of the node. The value of g(v1) is the label of the right node of v1. For nodes at the bottom-level, q(v1) is the sum of the rank of the right node of v1 and 1, this 1 means that the node v1 itself is also a reachable node on the bottom-level. The value of q(vj) of each node on the left side of the node v1 at bottom-level is 1. For non-bottom level nodes, if the node vj−1 is the right (or down) node of vj, then q(vj) = r(dwn(vj)) (or q(vj) = r(rgt(vj))).
块的证明由验证路径上每个节点的相关信息构成的元组序列组成。也就是说,对于数据T(mi)的块i的证明是一个序列∏i=(a(v1),··,a(vk)),其中a(vj)=(l(vj),q(vj),d(vj),g(vj)),1≤j≤k,从中我们可以得到AAI。l(vj)是节点的级别,布尔值d(vj)指示vj-1是在vj的右侧还是下方。g(vj)的值用于计算沿着验证路径的相应节点的标签。对于非底层节点,如果d(vj)=rgt,则g(vj)=f(dwn(vj)),否则,如果d(vj)=dwn,则g(vj)=f(rgt(vj))。对于验证路径上的底层节点vj(j>1),g(vj)的值是节点的数据项。例如g(v1)的值是v1的右节点的标签。对于底层节点,q(v1)是v1和1的右节点的秩的和,这个1表示节点v1本身也是底层的可到达节点。底层节点v1左侧每个节点的q(vj)值为1。对于非底层节点,如果节点vj-1是vj的右(或下)节点,则q(vj)=r(dwn(vj))(或q(vj)=r(rgt(vj)))。

4.2隐私保护方案
本研究遵循文献[3,15,27,28,30,31,36]提出的概念。该方案基于CPoR模型[27]和[25]中的相关方法。
该方案包括两个算法KeyGen(1k)、St(sk,F)以及一个交互式审计协议审计(CSP,TPA)。设S=(p,G,GT,e)是一个双线性映射分组系统,随机选择生成器g,h∈rG,其中G,GT是两组大素数阶p.,h(·)是一个安全的映射到点的散列函数:{0,1}∗→G,它将字符串统一映射到G。另一个散列函数h1(·):GT→Zp将GT的分组元素统一映射到Zp。
KeyGen(1^k) :这个随机算法生成公共和私有参数。云用户选择一个随机签名密钥对(spk,ssk)和两个随机α,β∈R Zp。私有参数是sk=(α,β,ssk)公共参数pk=(g,h,X,Y),其中X=hα,Y=hβ∈g。
St(sk,F):将数据文件F分成n×s个扇区F={mi j}n×s,mi={mij}1≤j≤s,mij∈Zp。云用户选择s随机τ1、···、τs∈Zp作为文件的秘密,计算uj=gτj∈g,1≤j≤s和认证器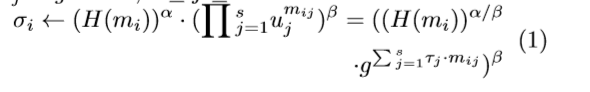
对于每个块i,云用户构造一个基于秩的认证跳表,其中第i个底部节点的数据项为(H(mi))α/β,1≤i≤n。设Φ=(σ1,··,σn)且t0为“fn k n k u1 k···k us k Mc”,fn由用户从Zp中均匀随机选择,作为F的标识符,Mc是跳表的根。云用户计算t=t0 k ssigsk(t0)作为私钥ssk下F的文件标记。然后,用户将{F,Φ,t}和跳表发送到云服务器,并从其本地存储中删除{F,Φ}和跳表。然后用户持有t作为元数据。
审计(CSP,TPA):这是TPA和CSP之间的三步转移协议,如下:
•承诺(CSP→TPA):CSP选择s随机λj∈R Zp,(1≤j≤s),然后计算Tj=uλjj,(1≤j≤s),并将其承诺{Tj}j∈[1,s]发送给TPA。
•质询(TPA→CSP):授权TPA首先检索文件标签t。TPA通过spk检查t的有效性,如果验证失败,则通过输出拒绝退出。否则,TPA将恢复t0中的值。然后TPA生成一组质询信息Chal={c,k1,k2}[3],其中c是要被审计的数据块的数目,k1,k2分别是伪随机置换πk和伪随机函数fk的随机选择键。利用πk和fk生成被挑战数据块的c指标sj(1≤j≤c,1≤sj≤n)和c相关系数vi(i∈{sj | 1≤j≤c},vi∈R Zp)。让我表示c随机指数sj的集合。设Q是指数对和系数对的{(i,vi)}i∈i的集合。然后TPA将Chal发送到校准CSP。
•响应(TPA——>CSP):CSP在接收到挑战Chal时,选择一个随机r∈r Zp并计算:


并将每个块i和{(H(mi))α/β)}i∈i的证明集{∏i}i和{(H(mi))α/β)}i的响应θ=(σ,{μj}j∈[1,s],Ψ)发送到TPA。验证:TPA根据{(H(mi))α/β,∏i}i∈i计算根Rt并检查Rt?=Mc。如果不是真的,TPA输出拒绝,否则TPA可以检查
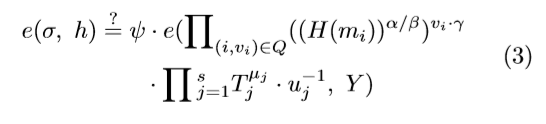
如果相等,TPA输出接受,否则拒绝。





















 2462
2462











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








