Preface
In today’s world, where computer viruses and security threats are common themes in
anything from Hollywood movies and TV advertisements to political discussions, it seems
unthinkable to ignore security considerations in the design and implementation of any
network. However, it is only in the past 4–5 years that talkative security experts have been
invited to the design table from the start. The common thinking only 5 years ago was either:
this is somebody else’s problem or let us design the major functionalities first, then bring in a
cryptographer to secure it! This treatment of security as an add-on feature typically led either
to design delays, overheads and extra costs when the “feature” had to be included, or to
ignored security provisioning when the “feature” was not a must. The problem, of course,
stemmed from the fact that security “features” have rarely been revenue-makers. As we all
know, many political, social and economic events in the last half decade have forced the
designers, regulators and businessmen to adjust their attitudes towards security consider-
ations. People realized that although security measures are not revenue-makers, their lack is
indeed a deal breaker, to say the least, or has catastrophic aftermaths, at worst.
The Internet Engineering Task Force (IETF) has also played an important role in estab-
lishing the aforementioned trend by making a few bold moves. The rejection of some very
high profile specifications due to the lack of proper security considerations was a message to
the industry that security is not to be taken lightly. This was done in a dot.com era where the
Internet and its applications seemed to have no boundaries and security provisioning seemed
to be only a barrier rather than an enabler.
As a result of this trend, the field of network security gained a lot of attention. A profession
that seemed to belong only to a few mathematically blessed brains opened up to a community
of practitioners dealing with a variety of networking and computing applications. Many stan-
dards, such as 802.1X, IPsec and TLS, were developed to apply cryptographic concepts and
algorithms to networking problems. Many books were written on the topics of security and
cryptography, bringing the dark and difficult secrets of fields such as public key crypto-
graphy to a public that typically was far less mathematically savvy than the original inventors.
Many protocols and procedures were designed to realize infrastructures such as PKIs to bring
these difficult concepts to life. Still, cryptographic algorithms or security protocols such as
IPsec are not enough alone to operate a network that needs to generate services and revenues
or to protect its constituency. Access to the network needs to be controlled. Users and devices
need to be authorized for a variety of services and functions and often must pay for their
usage. This is where the AAA protocols came in. In its simpler form a AAA protocol such as
fpref.fm Page xvii Wednesday, August 3, 2005 8:03 PM
xviii
Preface
a base RADIUS protocol only provides authentication-based access control. A few service
types are also included in the authorization signaling. RADIUS was later augmented with
accounting procedures. Diameter as a newer protocol was only standardized less than 2 years ago.
Both RADIUS and Diameter are still evolving at the time of writing. This evolution is to
enable AAA mechanisms and protocols to provide powerful functions to manage many
complicated tasks ranging from what is described above to managing resources and mobility
functions based on a variety of policies. In the near future the networks need to allow the
user through a variety of interfaces, devices and technologies to gain access to the network.
The user will require to be mobile and yet connected. The provision of the connection may
at times have to be aided by third parties. The interaction between AAA and security proce-
dures with entities providing mobility and roaming capabilities is a very complicated one and
is still not completely understood. Despite this complexity, there seem to be very few books
on the market that discuss more than a single topic (either security, or mobility or wireless
technology). The topic of AAA is largely untouched. Very little text in the way of published
literature is available on AAA protocols, let alone describing the interaction of these
protocols with security, mobility and key management protocols.
The idea for writing this book started from an innocent joke by the IETF operation and
management area director during an IETF lunch break a few years ago. When we asked
about the relations between the use of EAP for authentication and Mobile IP-AAA signaling,
the answer was “Maybe you should write a book about the subject”. Even though this was
considered a joke at a time, as we started to work on deploying AAA infrastructure for
Mobile IP and EAP support, the need for easy-to-understand overview material was felt so
strongly that the joke now sounded like black humor. We had to write a book on AAA as a
community service!
The book is geared towards people who have a basic understanding of Internet Protocol
(IP) and TCP/IP stack layering concepts. Except for the above, most of the other IP-related
concepts are explained in the text. Thus, the book is suitable for managers, engineers,
researchers and students who are interested in the topic of network security and AAA but do
not possess in-depth IP routing and security knowledge. We aimed at providing an overview
of IP mobility (Mobile IP) and security (IPsec) to help the reader who is not familiar with
these concepts so that the rest of the material in the book can be understood. However, the
reader may feel that the material quickly jumps from a simple overview of Mobile IP or IPsec
to sophisticated topics such as bootstrapping for IP mobility or key exchange for IP security.
Our reasoning here was that we felt that there are a number of excellently written books on
the topics of Mobile IP and IPsec, to which the reader may refer, so it would not be fair to fill
this book with redundant information. Instead, the book provides just enough material on
those topics to quickly guide the reader into the topics that are more relevant to the rest of the
material in this book. The book may also serve as a reference or introduction depending on the
reader’s need and background, but it is not intended as a complete implementation reference
book. The tables listing the protocol attributes are intentionally not exhaustive to avoid
distractions. Most of the time, only subsets that pertain to the discussions within the related
text are provided to enable the reader to understand the principles behind the design of these
attributes. At the same time, references to full standards specifications are provided for
readers interested in implementation of the complete feature sets.
Chapter 1 of this book provides an overview of what AAA is and stands for. It provides
thorough descriptions of both authorization and accounting mechanisms. Unfortunately the
field and standardization on authorization mechanisms is in the infancy stage at this point and
fpref.fm Page xviii Wednesday, August 3, 2005 8:03 PM
Preface
xix
accounting, compared to authentication, has received far less attention in the research and
standards community due to its operator-specific nature. Due to the enormous amount of
research done on authentication, we devote Chapter 2 entirely to authentication concepts and
mechanisms and also provide a rather unique classification (from IAB) of authentication
mechanisms in that chapter. We will come back to the topic of authentication and describe
more sophisticated EAP-based authentications in Chapter 10, but after Chapter 2, we go
through the concepts of key management in Chapter 3 to lay the groundwork for most of the
security and key management discussions in Chapter 4 and the rest of the book. Chapter 4
discusses IPsec and TLS briefly, but provides a thorough discussion on IKE as an important
example of a key management and security association negotiation protocol. As mentioned
earlier, the aim of that chapter is not to describe IPsec or TLS thoroughly. Both these proto-
cols are provided for completeness and to provide the background for the later discussion of
security topics. Chapter 5 discusses mobility protocols for IP networks. It describes basic
Mobile IP procedures and quickly goes through the latest complementary work in IETF, such
as bootstrapping. This chapter also describes two IETF seamless mobility protocols, context
transfer and candidate access router discovery, which may be required to achieve seamless
handovers. This chapter also describes the security procedures for Mobile IPv4 and lays the
groundwork for Mobile IP-AAA discussions in Chapter 8. Chapters 6 and 7 describe the two
most important AAA protocols, namely RADIUS and Diameter and their applications for
authentication and accounting. Many of the specifications that are considered work in
progress in IETF are covered here.
Chapter 8 finally covers the topic discussed in the IETF joke we mentioned earlier: Mobile
IP-AAA signaling to provide authentication and key management for Mobile IP signaling.
Chapter 9 goes on to provide a description of public key infrastructures (PKI) and the
issues and concerns with management of PKIs, certificates and their revocation.
Chapter 10 describes the EAP authentication framework, EAP signaling transport and the
structure for a generic EAP-XXX mechanism. It also provides overviews of a variety of EAP
authentication methods, such as EAP-TLS, EAP-TTLS, EAP-SIM, and so on.
Finally, Chapter 11 makes a humble attempt at describing the overall problem of AAA and
identity management in a multi-operator environment and discusses various architectural
models to tackle the problem. This chapter also provides an overview of the Liberty Alliance.
We wish the readers a joyful read.
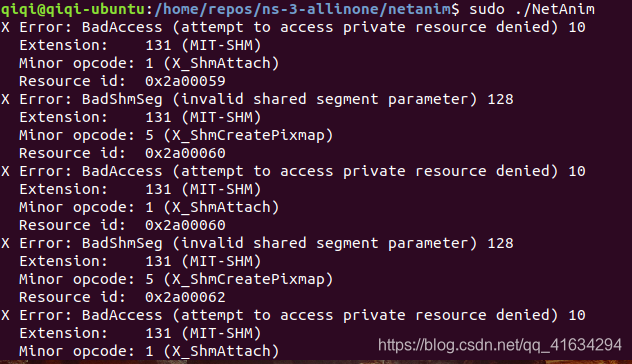
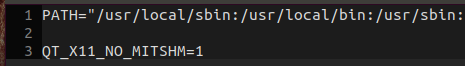
 打开时是灰色的,提示错误如本文第一张图,搜索错误提示时发现是qt有关错误,经过以上方案已成功解决。
打开时是灰色的,提示错误如本文第一张图,搜索错误提示时发现是qt有关错误,经过以上方案已成功解决。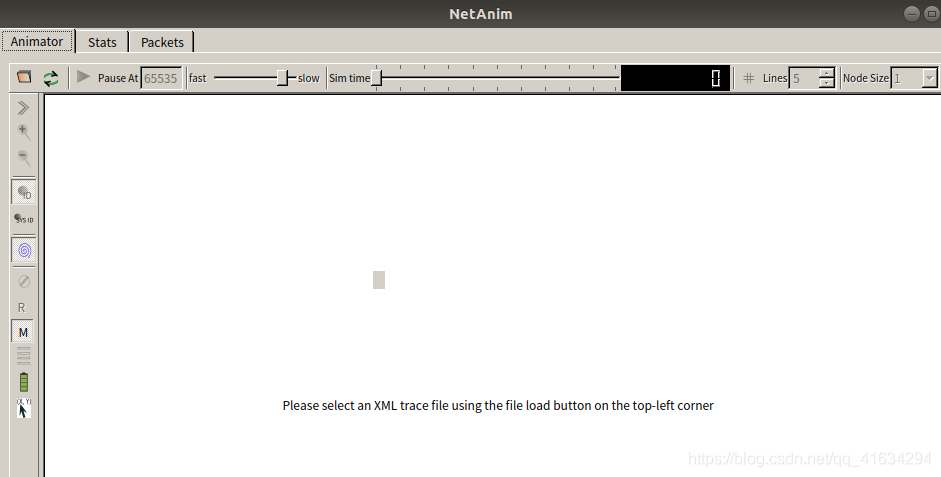


 打开时是灰色的,提示错误如本文第一张图,搜索错误提示时发现是qt有关错误,经过以上方案已成功解决。
打开时是灰色的,提示错误如本文第一张图,搜索错误提示时发现是qt有关错误,经过以上方案已成功解决。
 1427
1427











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?


