依赖jar
<!-- 加密工具jar -->
<dependency>
<groupId>com.github.ulisesbocchio</groupId>
<artifactId>jasypt-spring-boot-starter</artifactId>
<version>2.1.0</version>
</dependency>
工具类
package com.ll.cc.test.msgtest.util;
import java.security.NoSuchAlgorithmException;
import java.security.SecureRandom;
import javax.crypto.Cipher;
import javax.crypto.KeyGenerator;
import javax.crypto.SecretKey;
import javax.crypto.spec.SecretKeySpec;
/**
* @Author: lc
* @Date: 2019/12/3 13:58
*/
public class AESUtils {
private static final int AES_KEY_SIZE = 128;
private static final String PASS_AES_SEED = "1da2ce17fccDSUNr4c9JnbdfJNm3a0f79af5c3f3";
private static final String PASS_AES_PREFIX = "{AES}";
/**
* 加密
*
* @param content
* @param keyseed
* @return
* @throws Exception
*/
public static String encrypt(String content, String keyseed) throws Exception {
KeyGenerator kgen = KeyGenerator.getInstance("AES");
SecureRandom random = SecureRandom.getInstance("SHA1PRNG");
random.setSeed(keyseed.getBytes());
kgen.init(AES_KEY_SIZE, random);
SecretKey secretKey = kgen.generateKey();
byte[] enCodeFormat = secretKey.getEncoded();
SecretKeySpec key = new SecretKeySpec(enCodeFormat, "AES");
Cipher cipher = Cipher.getInstance("AES");// 创建密码器
byte[] byteContent = content.getBytes("utf-8");
cipher.init(Cipher.ENCRYPT_MODE, key);// 初始化
byte[] result = cipher.doFinal(byteContent);// 加密
// 加密后的byte数组是不能强制转换成字符串,因此将二进制数据转换成十六进制表示
return parseByte2HexStr(result);
}
public static byte[] decrypt(byte[] content, String keyseed) throws Exception {
KeyGenerator kgen = KeyGenerator.getInstance("AES");
kgen.init(AES_KEY_SIZE, new SecureRandom(keyseed.getBytes()));
SecretKey secretKey = kgen.generateKey();
byte[] enCodeFormat = secretKey.getEncoded();
SecretKeySpec key = new SecretKeySpec(enCodeFormat, "AES");
Cipher cipher = Cipher.getInstance("AES");// 创建密码器
cipher.init(Cipher.DECRYPT_MODE, key);
byte[] result = cipher.doFinal(hex2byte(content));
return result;
}
public static String decryptToString(String content, String keyseed) throws Exception {
KeyGenerator kgen = KeyGenerator.getInstance("AES");
SecureRandom random = SecureRandom.getInstance("SHA1PRNG");
random.setSeed(keyseed.getBytes());
kgen.init(AES_KEY_SIZE, random);
SecretKey secretKey = kgen.generateKey();
byte[] enCodeFormat = secretKey.getEncoded();
SecretKeySpec key = new SecretKeySpec(enCodeFormat, "AES");
Cipher cipher = Cipher.getInstance("AES");
cipher.init(Cipher.DECRYPT_MODE, key);
byte[] result = cipher.doFinal(parseHexStr2Byte(content));
return new String(result, "UTF-8");
}
public static String encryptForJS(String content, String keyseed) throws Exception {
SecretKeySpec key = getKeySpecFromBytes(keyseed.toUpperCase());
Cipher cipher = Cipher.getInstance("AES");
cipher.init(1, key);
byte[] byteEnc = cipher.doFinal(content.getBytes("UTF-8"));
return parseByte2HexStr(byteEnc);
}
public static String decryptForJS(String content, String keyseed) throws Exception {
SecretKeySpec key = getKeySpecFromBytes(keyseed.toUpperCase());
Cipher cipher = Cipher.getInstance("AES/ECB/NoPadding");
cipher.init(2, key);
String result = new String(cipher.doFinal(hex2byte(content.getBytes("UTF-8"))));
return result.trim();
}
/**
* 将二进制转换成16进制
*
* @param buf
* @return
*/
public static String parseByte2HexStr(byte[] buf) {
StringBuffer sb = new StringBuffer();
for (int i = 0; i < buf.length; i++) {
String hex = Integer.toHexString(buf[i] & 0xFF);
if (hex.length() == 1) {
hex = '0' + hex;
}
sb.append(hex.toUpperCase());
}
return sb.toString();
}
/**
* 将16进制字符转换成二进制
*
* @param hexStr
* @return
*/
public static byte[] parseHexStr2Byte(String hexStr) {
if (hexStr == null || hexStr.length() < 1) {
return null;
}
byte[] result = new byte[hexStr.length() / 2];
for (int i = 0; i < hexStr.length() / 2; i++) {
int high = Integer.parseInt(hexStr.substring(i * 2, i * 2 + 1), 16);
int low = Integer.parseInt(hexStr.substring(i * 2 + 1, i * 2 + 2), 16);
result[i] = (byte) (high * 16 + low);
}
return result;
}
/**
* 将16进制转换为二进制
*
* @param b
* @return
*/
public static byte[] hex2byte(byte[] b) {
if (b.length % 2 != 0) {
throw new IllegalArgumentException("长度不是偶数!");
}
byte[] b2 = new byte[b.length / 2];
for (int n = 0; n < b.length; n += 2) {
String item = new String(b, n, 2);
b2[(n / 2)] = (byte) Integer.parseInt(item, 16);
}
return b2;
}
public static SecretKeySpec getKeySpecFromBytes(String strBytes) throws NoSuchAlgorithmException {
SecretKeySpec spec = new SecretKeySpec(hex2byte(strBytes.getBytes()), "AES");
return spec;
}
/**
* 获取加密后的密码
*
* @param passWord
* @return
*/
public static String getPassEncrypt(String passWord) {
if (passWord != null && passWord.trim().length() > 0) {
try {
String enPass = encrypt(passWord, PASS_AES_SEED);
return PASS_AES_PREFIX + enPass;
} catch (Exception e) {
return null;
}
}
return passWord;
}
/**
* 获取解密的pass
*
* @param epassWord
* @return
*/
public static String getPassDecrypt(String epassWord) {
if (epassWord != null && epassWord.trim().length() > 0 && epassWord.startsWith(PASS_AES_PREFIX)) {
try {
epassWord = epassWord.substring(PASS_AES_PREFIX.length());
String enPass = decryptToString(epassWord, PASS_AES_SEED);
return enPass;
} catch (Exception e) {
return epassWord;
}
}
return epassWord;
}
public static void main(String[] args) {
String s = AESUtils.getPassEncrypt("coral2018");
System.out.println(s);
System.out.println(AESUtils.getPassDecrypt(s));
}
}
注册解密Bean
package com.ll.cc.test.msgtest.config.jasypt;
import org.jasypt.encryption.StringEncryptor;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.core.Ordered;
import org.springframework.core.annotation.Order;
/**
* 加密配置
* @author lc
* @date 2019/12/3 3:19 PM
*/
@Configuration
public class JasyptConfig {
/**
* 自定义的加密解密处理Bean (替换jasypt的默认组件)
* @return
*/
@Bean("jasyptStringEncryptor")
@Order(Ordered.HIGHEST_PRECEDENCE)
public StringEncryptor stringEncryptor() {
return new CustomStringEncryptor();
}
}
package com.ll.cc.test.msgtest.config.jasypt;
import com.ll.cc.test.msgtest.util.AESUtils;
import org.jasypt.encryption.StringEncryptor;
import org.slf4j.Logger;
import org.slf4j.LoggerFactory;
/**
* jasypt自定义加密工具类
* @author lc
* @date 2019/12/3 2:30 PM
*/
public class CustomStringEncryptor implements StringEncryptor {
private Logger logger = LoggerFactory.getLogger(CustomStringEncryptor.class);
public CustomStringEncryptor(){
if (logger.isDebugEnabled()){
logger.debug("customer StringEncrypt inited, use {}", AESUtils.class.getCanonicalName());
}
}
@Override
public String encrypt(String message) {
if (logger.isDebugEnabled()){
logger.debug("加密前: {}", message);
logger.debug("加密后: {}", AESUtils.getPassEncrypt(message));
}
return AESUtils.getPassEncrypt(message);
}
@Override
public String decrypt(String encryptedMessage) {
if (logger.isDebugEnabled()){
logger.debug("解密前: {}", encryptedMessage);
logger.debug("解密后: {}", AESUtils.getPassDecrypt(encryptedMessage));
}
return AESUtils.getPassDecrypt(encryptedMessage);
}
}
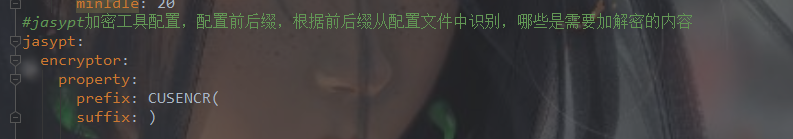
配置文件



























 5578
5578











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










