上次勉强看完了第一本关于关联分析的书
今天来看下一本真正讲到SIEM当中有关概念以及实现的书
PART I Introduction to SIEM: Threat Intelligence for IT Systems
CHAPTER 1 Business Models
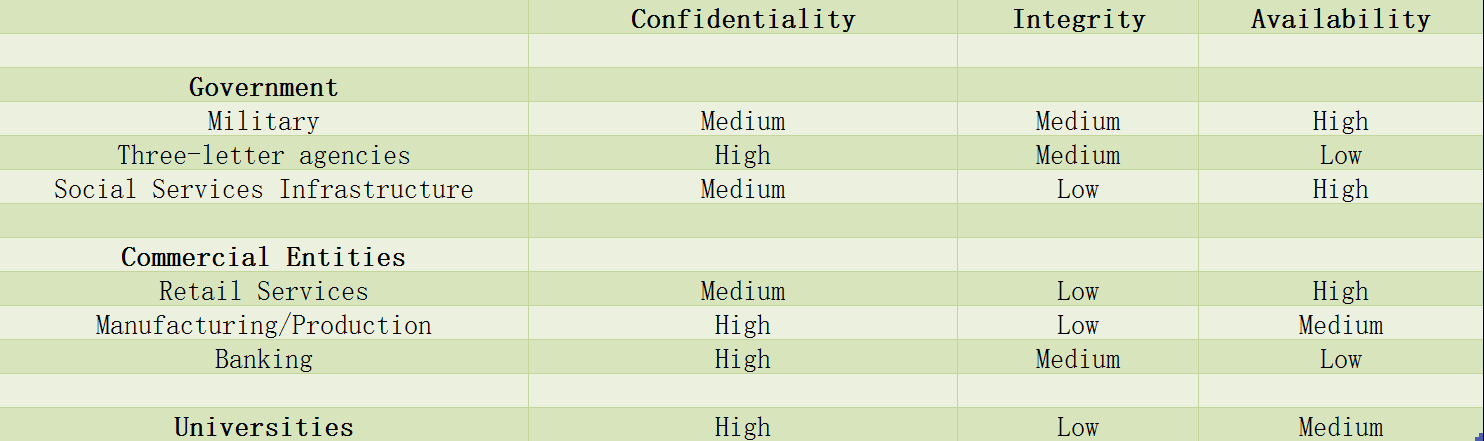
商业模式分为三种: Government Commercial Universities
首先是一个概念,学过安全的人都知道:CIA -> Confidentiality、Integrity、Availability
Three-Letter Agencies
Central Intelligence Agency (CIA)
Federal Bureau of Investigations (FBI)
National Security Agency (NSA)
Britain’s MI5
Iran’s Ministry of Security (MOIS/VEVAK)
Germany’s Federal Intelligence Service(Bundesnachrichtendienst)
principles of system security:categorization of data、need to know、the principle of least privilege
接下来就对这三种模式当中的这三个属性进行评估
CHAPTER 2 Threat Models
The Bad Things That Could Happen:
- Vulnerabilities:存在安全上的漏洞
- Vulnerable Protocols:有漏洞与缺陷的协议
- Misconfiguration:配置出错
- User Awareness and Mistakes:用户操作不当
Malicious Intent:
1.Internal Threats:其实这是最关键的一环,当然也没什么好讨论的,有几个措施可以预防:
- Separation of duties
- Job rotation Security awareness training
- Strict permissions on all resources
- Implement auditing on critical data,applications, and system configuration and logs
2.External Threats:human attack
Recognizing Attacks on the IT Systems:
Scanning or Reconnaissance(footprint and fingerprint)
Exploits:
- Viruses
- Worms
- IP Spoofing from the Outside
- IP Spoofing from the Inside
- Distributed Denial-of-Service (DDoS)
- Buffer Overflow and SQL Injection Attacks
- Password Attacks
- Attacks on IDS/IPS Systems
- Other Systems Under Attack
Entrenchment(留后门等一系列动作,用于进一步控制系统同时避开各种监测):
- Disable operating system and application updates
- Disable antivirus and antispyware updates
- Disable forwarding logs to syslog or the SIEM system
- Make system configuration changes
- Install new service(s) and/or stop service(s)
Phoning Home(进一步安装各种恶意软件及工具等等等等):
- Reset the browser’s default home page
- Use known bad or blacklist IP addresses
- Use of dark IP address space
- Use of a good destination IP address, but with unusual behavior
Control:IRC protocol等
CHAPTER 3 Regulatory Compliance(法规遵从性)
Regulatory Compliance:
- Sarbanes-Oxley Act (2002) - SOX
- Gramm-Leach-Bliley Act (1999) - GLBA
- Healthcare Insurance Portability and Accountability Act (1996) - HIPAA
- Payment Card Industry Data Security Standard - PCI DSS
- California Senate Bill 1386 (2003) - CA SB1386
- Federal Information Security Management Act (2002) - FISMA
- Cyber Security Act of 2009 (SB 773) - not yet ratified
Prudent Security:
- Assign a Specific Individual or Group Responsible for Security/Compliance
- Implement Environmental (Physical) and Operational Security
- Identify, Categorize, and Protect Sensitive IT Assets (Systems and Data)
- Define Policies and Procedures Regarding IT Security
- Follow Vendor, Industry, and Government Security and Configuration “Best Practices”
- Provide Ongoing Security Awareness Training to All Employees
- Design Systems and Applications with Security Built In
- Separate Development, Quality Assurance, and Production Systems and Processes
- Secure Sensitive Data in Transit and at Rest (Encryption)
- Implement Unique User IDs per User and per User’s Role
- Implement Strong Authentication Techniques
- Implement a Strong Password Policy
- Provide Access Using the Principle of Least Privilege
- Implement Access Controls on All IT Assets
- Configure Systems Securely Before Implementing Them in Production
- Patch Operating Systems, Devices (Firmware), and Applications in a Timely Manner
- Implement Antivirus and Antispyware Applications on All Nodes, and on IDS and IPS Systems and Update Definitions Frequently
- Implement Properly Configured Perimeter/Boundary Security Systems (IP Tables, Firewalls,Proxy Servers)
- Monitor All IT System Access (Auditing)
- Provide Automatic Alerting Systems on Violations of IT System Assets
- Implement Incident Response to All Breaches of Security
- Test Security Systems and Processes Regularly
好长啊~- -这里看的我都要吐了 大致都是一些规则,如果要设计安全的系统必须要参考的,摆在这里镇着吧。






















 895
895











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








